SUMMUS (ERTL) - 2025


Table of Contents
Introduction
On the 10th of May 2025, I successfully completed the SUMMUS: Extreme Red Teamer Lab. Hence, as I have done with previous certs, in today's post, I will give my opinions on what you are going to encounter and what you need to do before purchasing the course and provide you with some tips for the lab.
What you should expect from the lab
At first glance, you will encounter that the lab is pretty similar to the OSEP exam, where you are going to receive an OpenVPN file, a Kali machine and a target to access the internal network. Also, as in the OSEP exam, to pass the lab, you need to encounter a file that is hidden really deep in the network with the final flag that rotates every hour; so be quick to send it to the admin when you encounter.
Skills & Topics You’ll Need to Master
To successfully complete the lab, you’ll need to demonstrate solid offensive security knowledge across multiple domains:
- Active Directory: Extensive AD recon is essential; be thorough and methodical. Take advantage of famous tools; they are good for a reason.
- Cloud Platform Exploitation: Expect to pivot across environments like Amazon Web Services (AWS), Google Cloud Platform (GCP) and Microsoft Azure. Understanding how to attack or exploit misconfiguration in these environments is going to be key to advancing in the lab.
- Pivoting and Tunnelling Techniques: Multi-layered pivoting is required to access segmented networks and hidden domains.
- EDR Evasion & OpSec: Avoid disk writes and look for stealthy lateral movement techniques.
Tips
I can not give many tips, because it will make the lab a lot easier. However, here you have some tips that will make it easier for you.
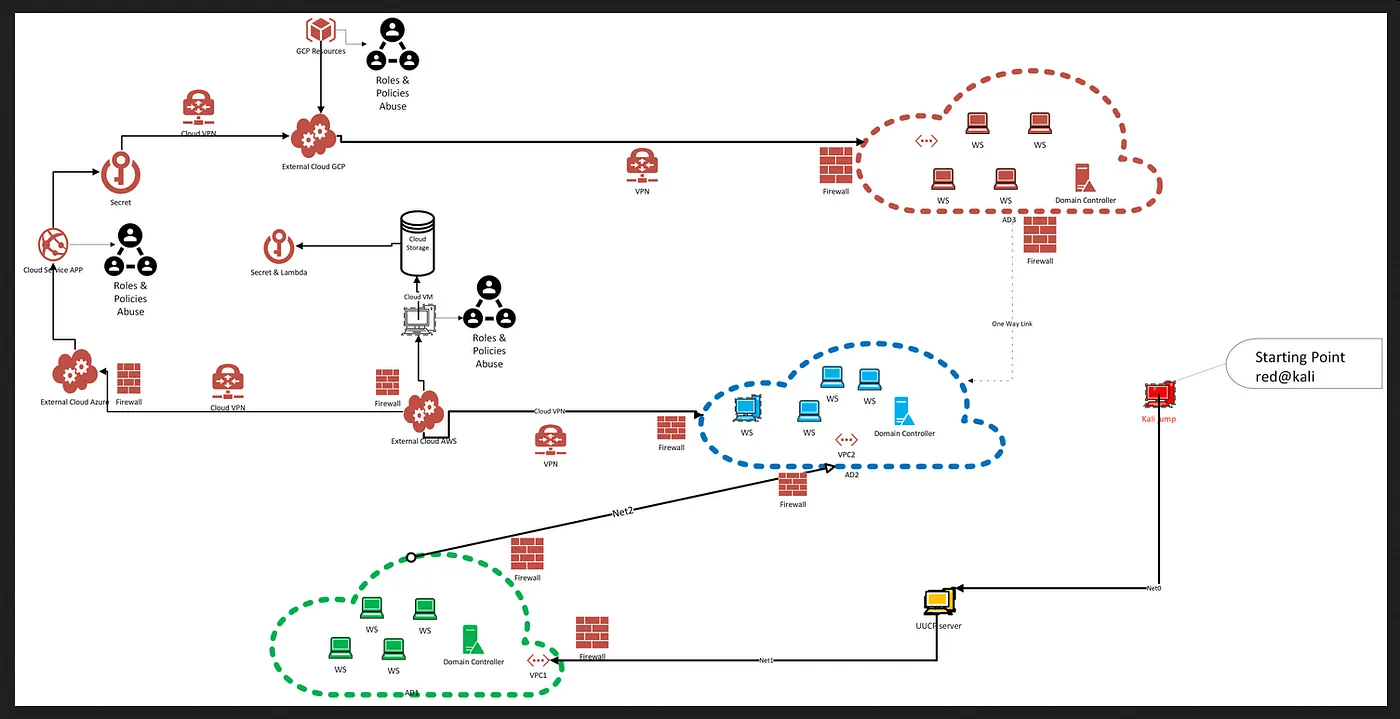
- One of the most helpful resources I can share is this mind map created by @kariarce2377. It offers a clear overview to help you navigate and understand the structure of a network.
- Install KeePass2 on your machine so you can deal with OTPs, credentials and commands that you are going to execute over and over while
- For the cloud part, Cloud HackTricks is going to be your best friend. Once you have access to your AWS credentials, pay special attention to the enumeration part.
- Regarding the Google Cloud part, use this new tool made by 3v4Si0N GCPermissioner.
Conclusion
This lab is a comprehensive and challenging environment designed to test your ability to operate like a real adversary stealthily, methodically, and across diverse platforms.
From on-prem Active Directory exploitation to cloud-native abuse in AWS, GCP, and Azure, success depends on your ability to pivot, adapt, and recognise patterns in seemingly unrelated pieces of information. Take notes, stay organised, and don’t rush.