Pineapple Modules - [Hak5]
![Cover Image for Pineapple Modules - [Hak5]](/assets/images/blog/pinneapleModules-hak5/PineappleModules.png)

Table of Contents
Introduction
Hello everyone! It is been a long time from my last post. because I have sitting a lot of exams, so I couldn't get involved in any project. Today, I bring you with several if not all modules that you can use in the 2019 summer in a pineapple nano.
Maybe, You might be asking, Why did you bought A Pineapple Nano? I didn’t, my gf bought the basic hak5 pack for my birthday.

https://shop.hak5.org/collections/hak5-field-kits/products/hak5-essentials-field-kit
Just because I wanted it to mess a little more in the world of cybersecurity. (Maybe someday, I will bring you with reviews/tutorials of the Bash Bunny and the Turtle). Let's get start. (By default I’m installing everything on the DS Card)
STATUS
In my opinion, this module should be the first one you should install. Because it gathers a lot of information in real time about performances in your pineapple.
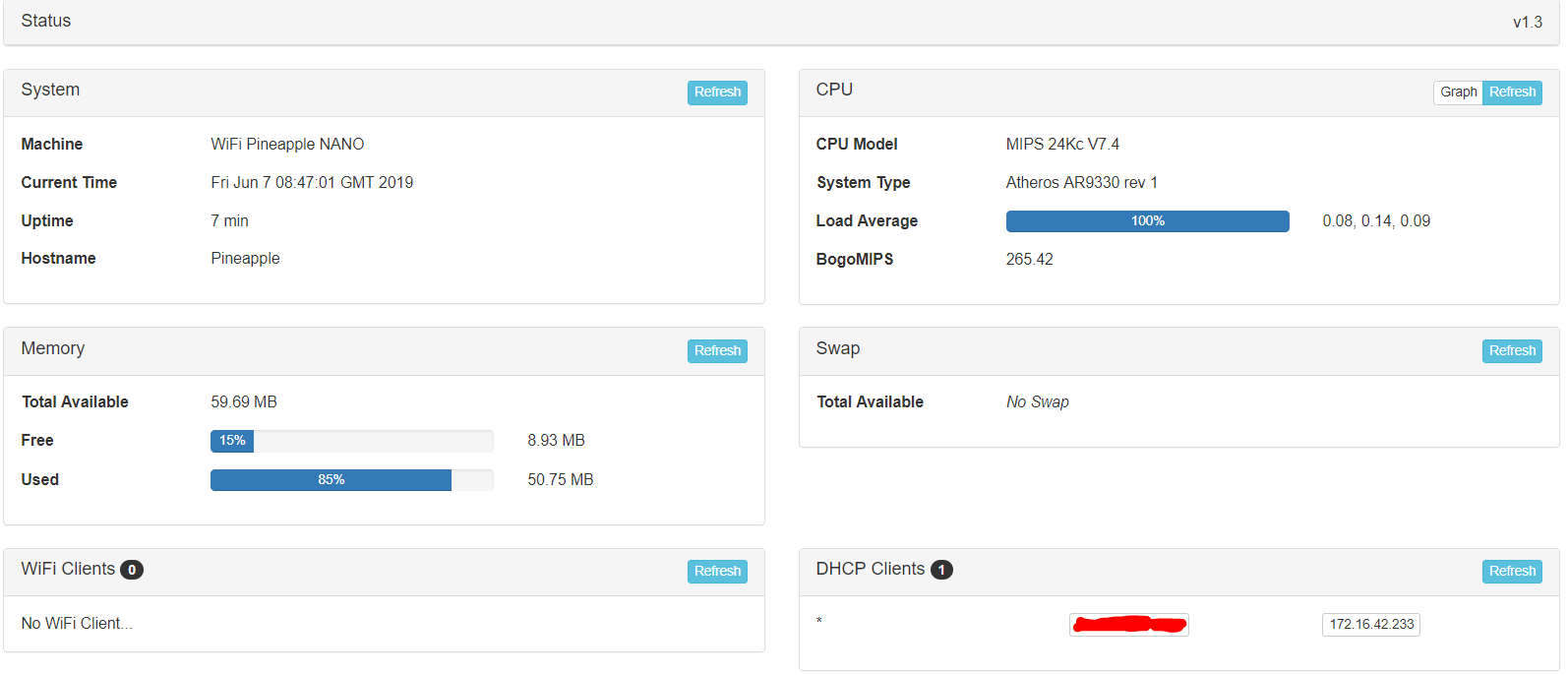
As you can see, the CPU is always bussy and the pineapple has very low capacity. Furthermore, you can see all clients connected to it with its MAC, in my case is my smartphone .
Regarding to its low capacity I put an 8 GB SD card, which I think more than enough for installing a lot of modules and saving its logs.
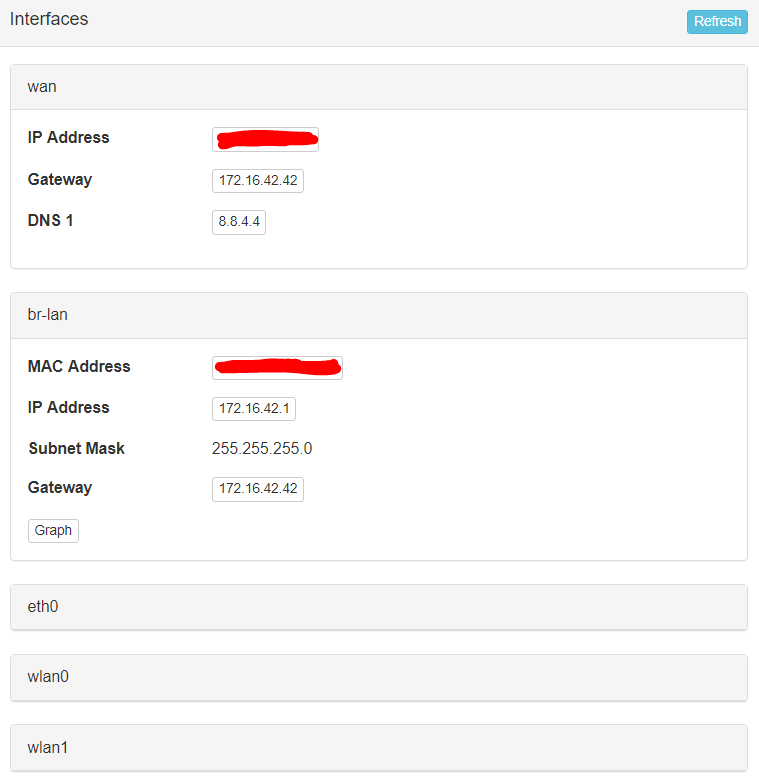
Finally, status provides you with important information about pineapple’s network interfaces.
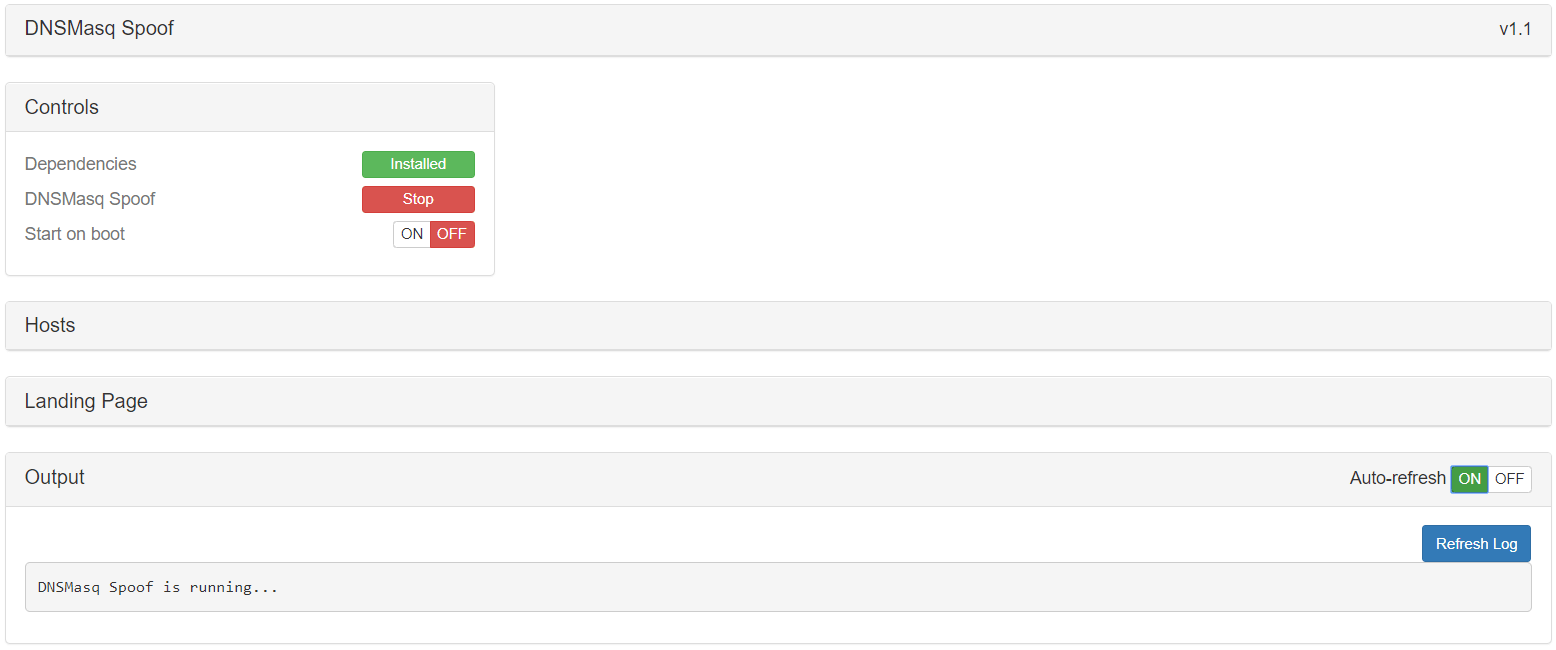
DNSMasq Spoof (v1.1) & RandomRoll
Killing 2 birds with one stone, I’m going to show how DNSMasq & RandomRoll works with a small demo which you will have fun doing it by yourself. Before going further I have to say, that I0m not using DNSMasq due to a lot of troubles which I had to deal with for nothing.
First of all I’m going to start with RandomRoll which is a module which creates random webpages as you can see below and you can check which ones, you just one to see.
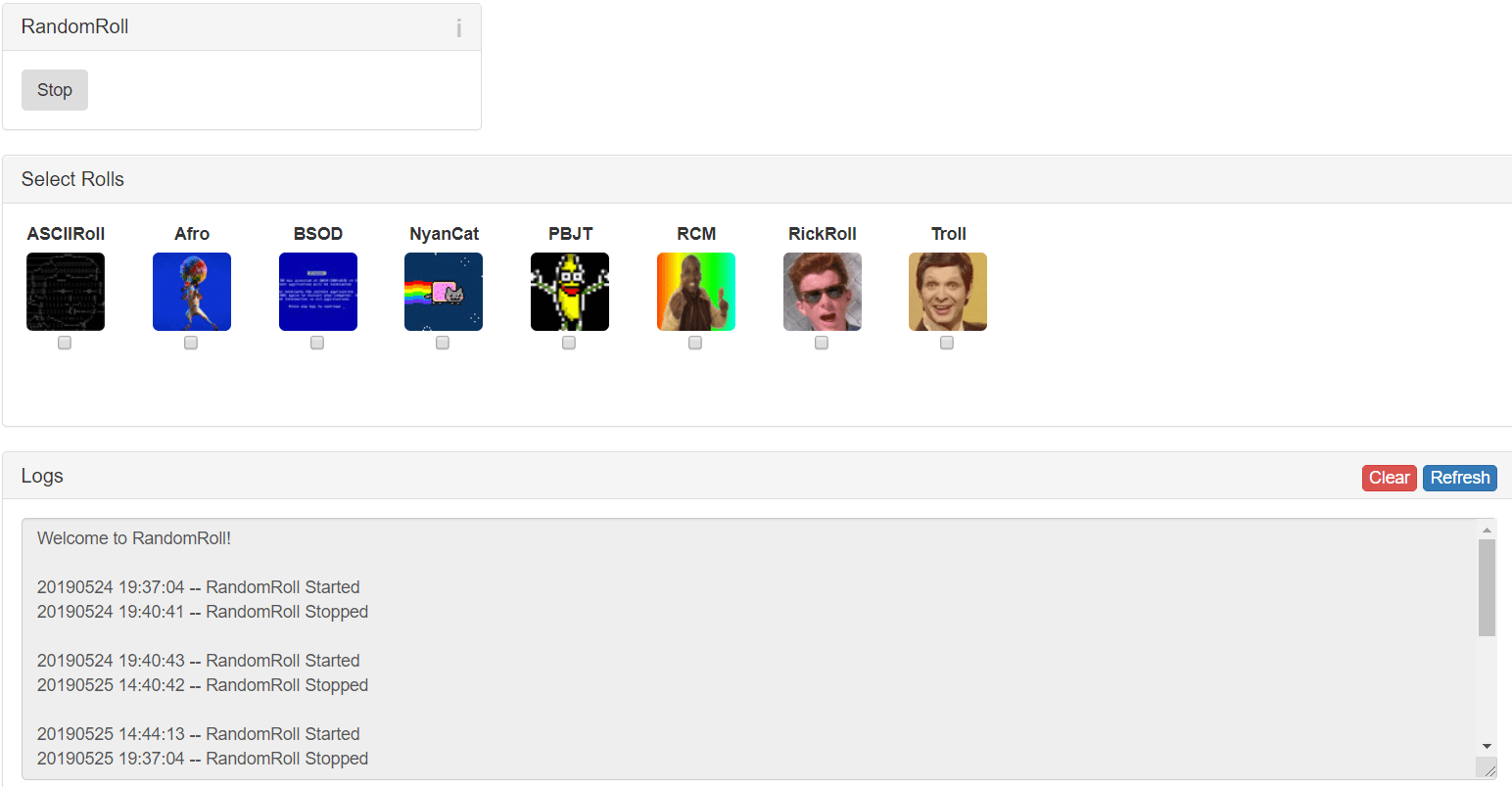
This module is super simple to use, you just need to check with pages do you want to see (If you don’t check anyone, they will appear randomly) and press start.
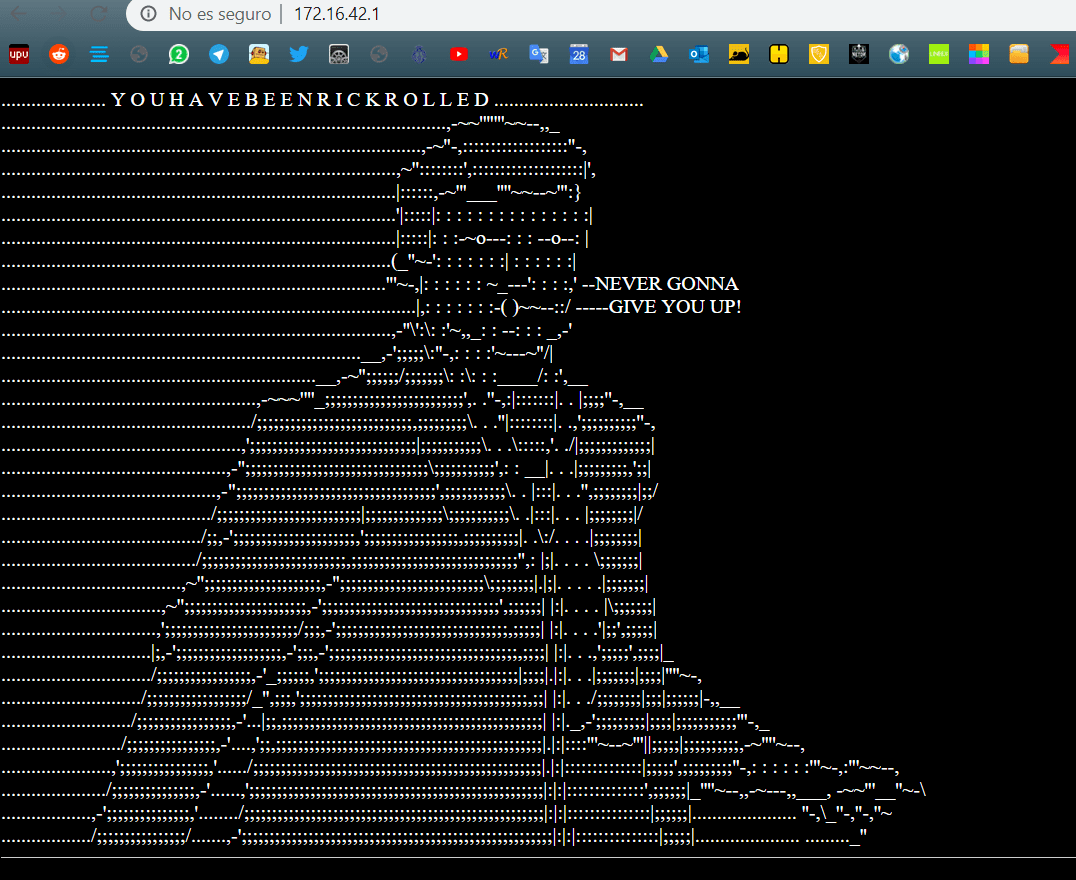
Secondly, as you can see the GUI isn’t very explanatory, but there isn’t any need.
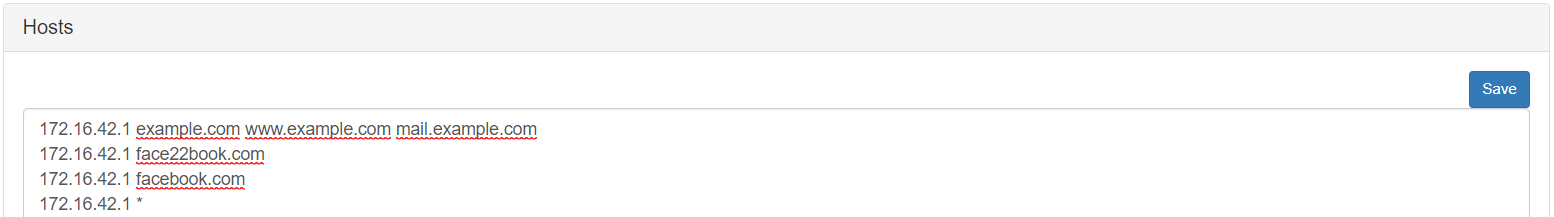
The only thing that you have to use is “Hosts” field. In which you will write the IP which will be redirect the user who has written one of the domains in that list. In this demo I’m going to use “facebook.com” and “facebook.com” in order to be redirect to the pineapple webpage (Where is the RandomRoll installed)
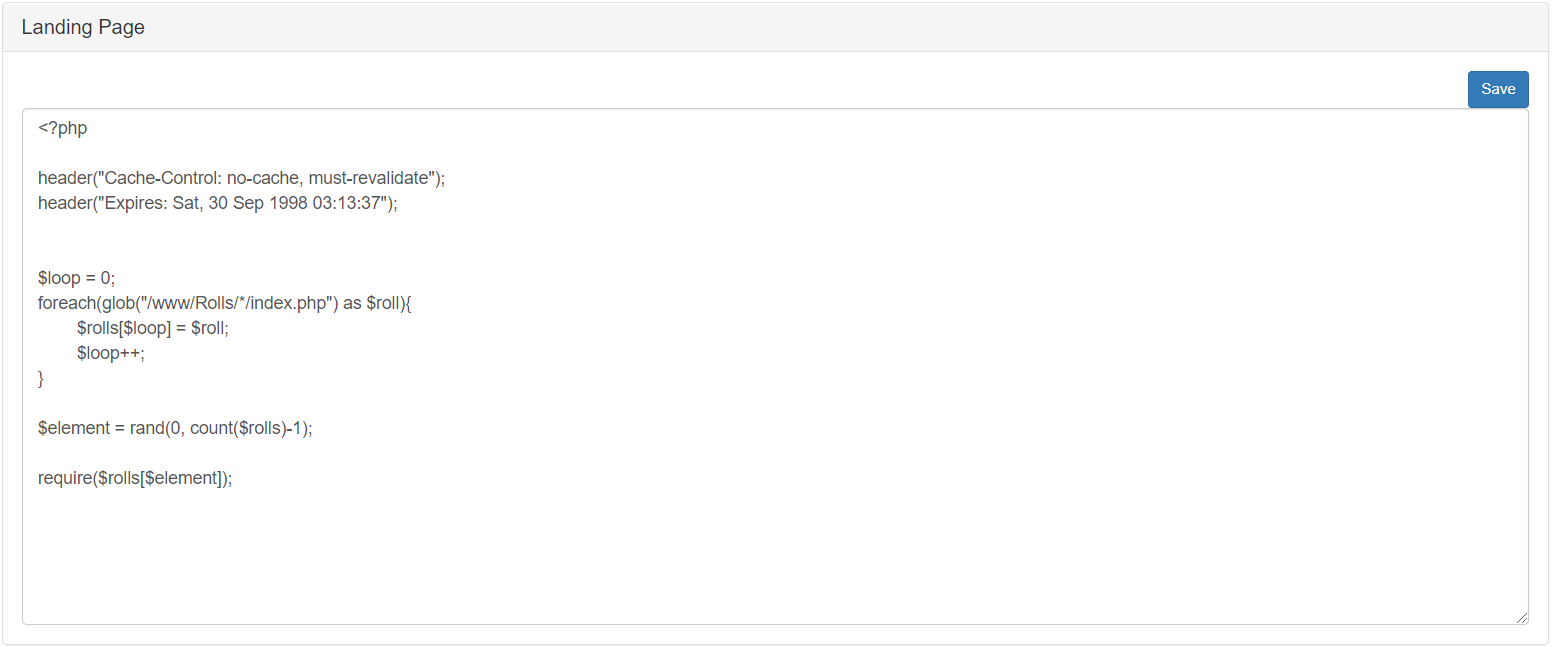
The second field that you will use if you aren’t using a module like RandomRoll, where you will write your webpage code which wil be executed once victims are redirected to the pineapple.
Finally, the only thing that you have to configure is the routing table to forward each DNS request through the pineapple. Just write the Default Route, in my case 172.16.42.42 with br-lan interface.
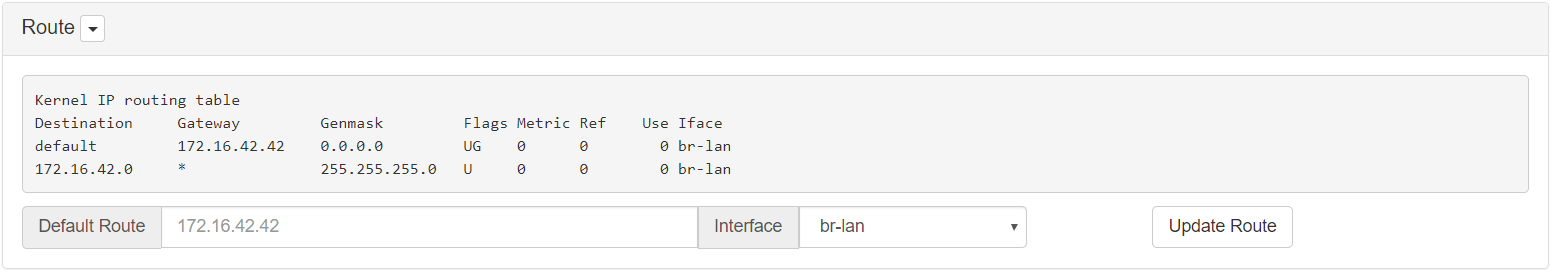
Before seeing the results, I have to say that I’m connecting my cell phone in order to get screenshots and checking although I have Internet in my pineapple the DNS isn’t getting affected.
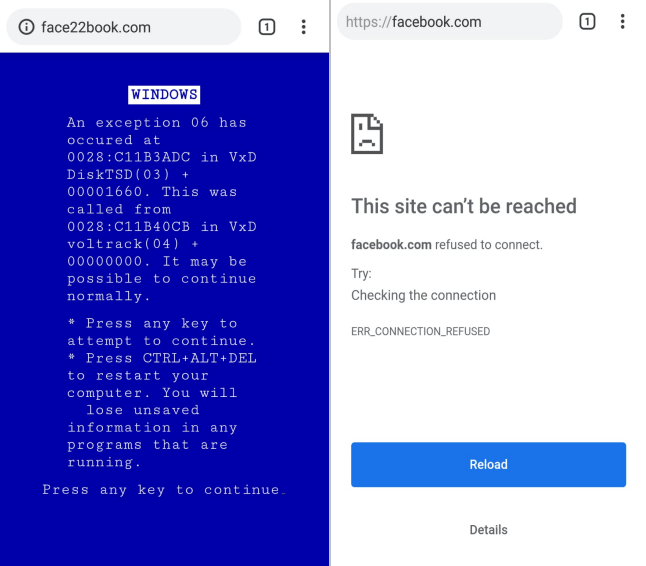
As you can see in the first picture it worst perfectly. However as you can see there is a Connection Error, and that because is using https, and https works in port 443 which is closed in the pineapple right now. Finally, If we stop the DNS Spoofing module, everything will work properly.
DEAUTH
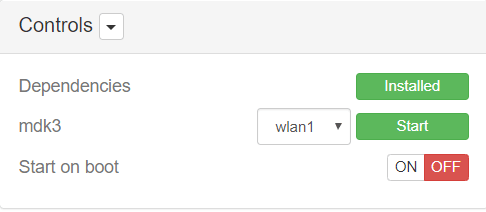
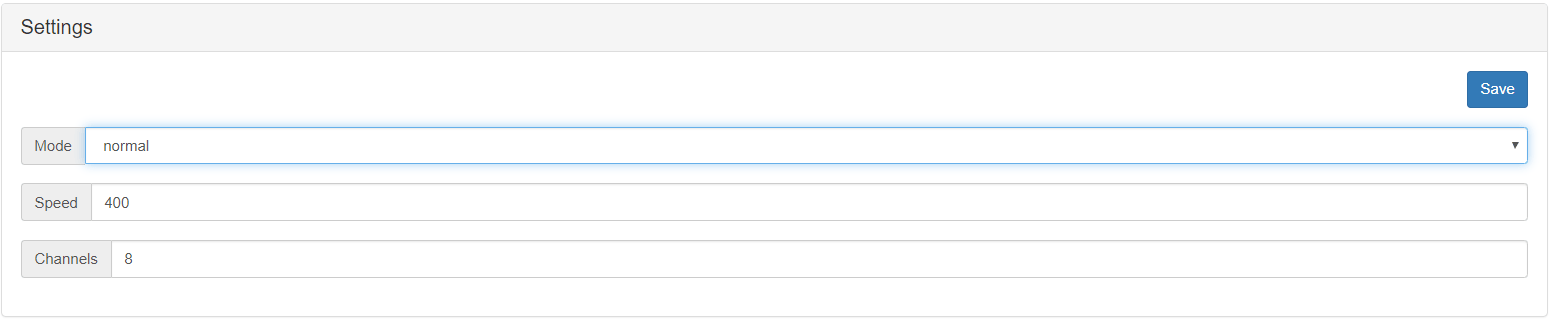
The deauth module is like the aireplay-ng command, which is used to deauthenticate users of a network. As you can see, there is a Settings menu where you need to write the speed (Number of packets send per second), channels ( You can write several channels separated by comma) and mode:
- Normal: Deauthenticates Everybody
- Whitelist: Doesn’t deauthenticate anyone which MAC address has been written in that list.
- Blacklist: Just deathenticate those devices, whose MAC appears in that list.
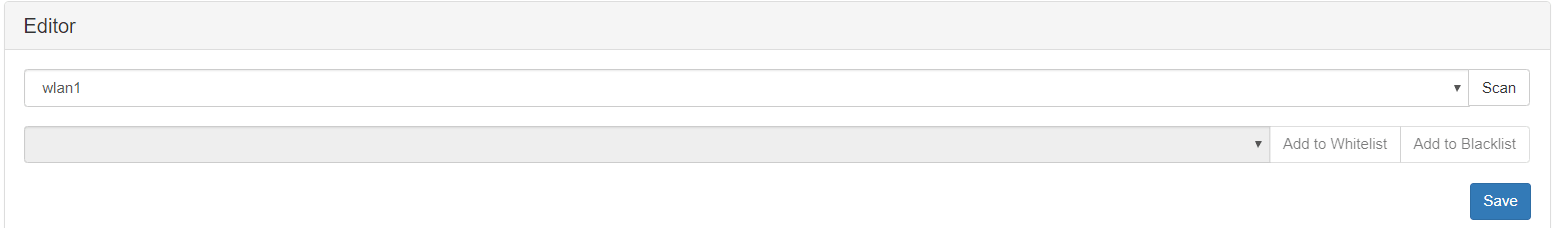
The editor is a menu, which helps you to add Networks BSSID to one or other list. Just choose an interface and press “scan”, then select those MAC that you want to filtrer and finally press “save”.
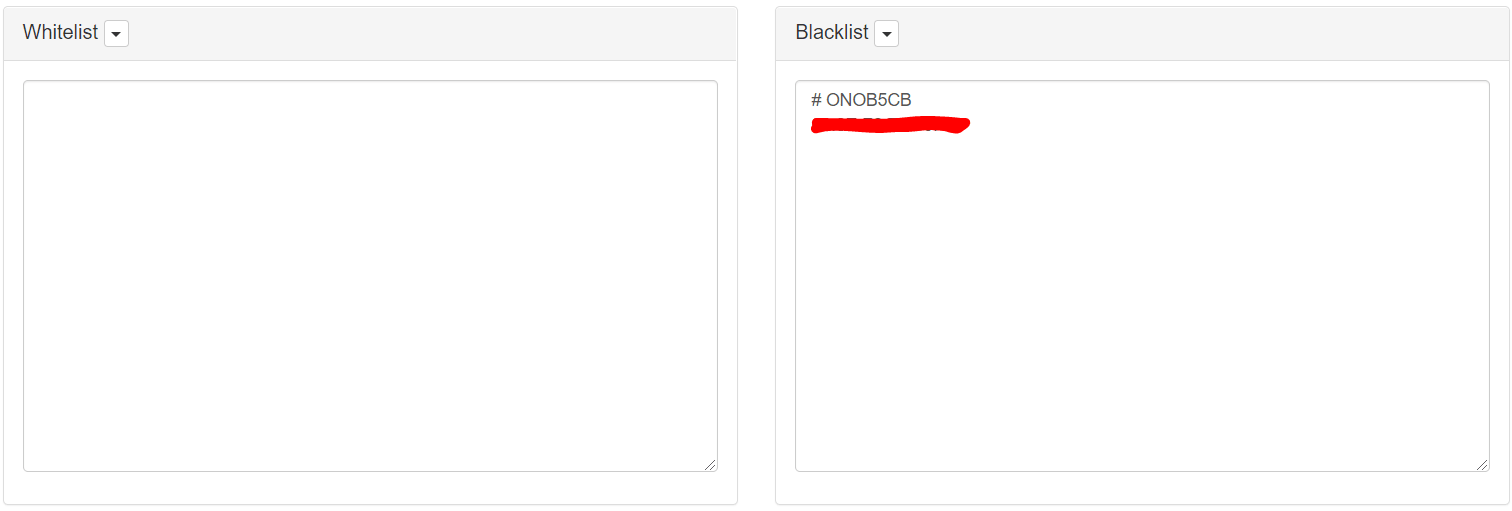
Here you can add manually those MACs that you want to filter.
The log menu shows you, packets which have been send and to whom.
In order to make this thin to work, You have to choose interface wlan1 and press start once. Then check the menu and you will find another interface.
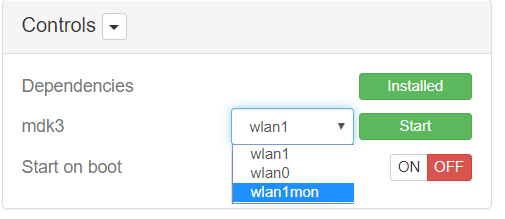
Select the new interface, and press start again. In my case I chose** blacklist mode**.
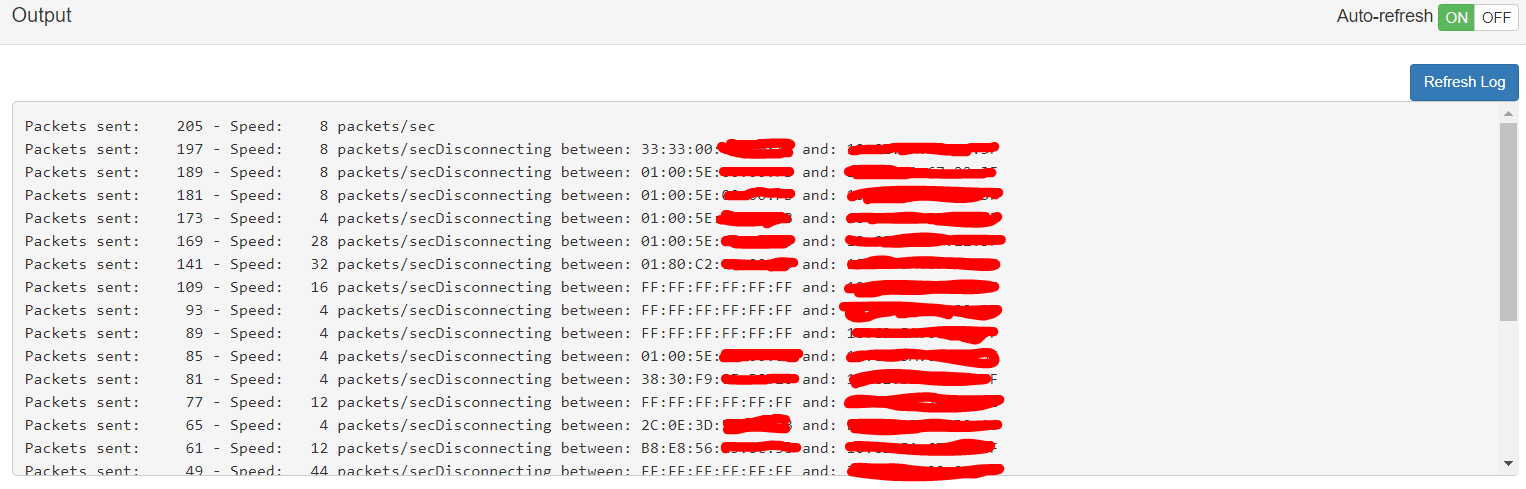
As you can see below deauthetication packets are been send against my network.
Although my PC didn’t disconnect from my AP, my Cell Phone did it.
LOCATE
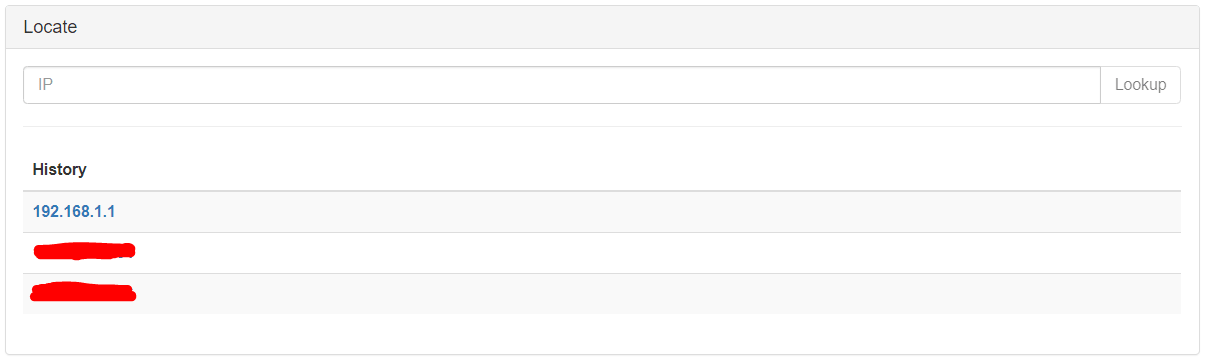
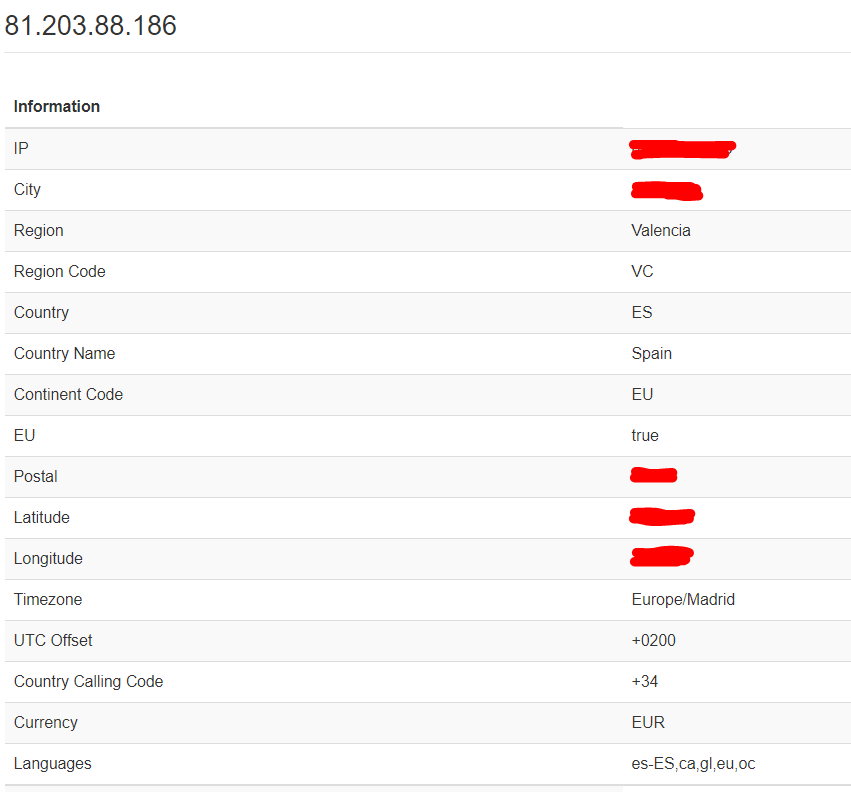
Locate, is a simple module which provides you a lot information about a provided public IP.
As you can see the only thing that you have to write is the IP. (Needs Internet) Furthermore, It records a history of written IPs.
As you will see once, you clicked on Lookup. It will provide a lot of information. Because I’m using my public IP I have found, that in \\City\\ and \\Postal\\ fields are giving my residential location (The one which is written in the contract of my ISP), not my current location :$
Occupineapple / Wi-Fi Jammer
Occupineapple or Wi-Fi jammer is a module which sends a lot of beacons simulating a lot of access points, whom you cant associate with.
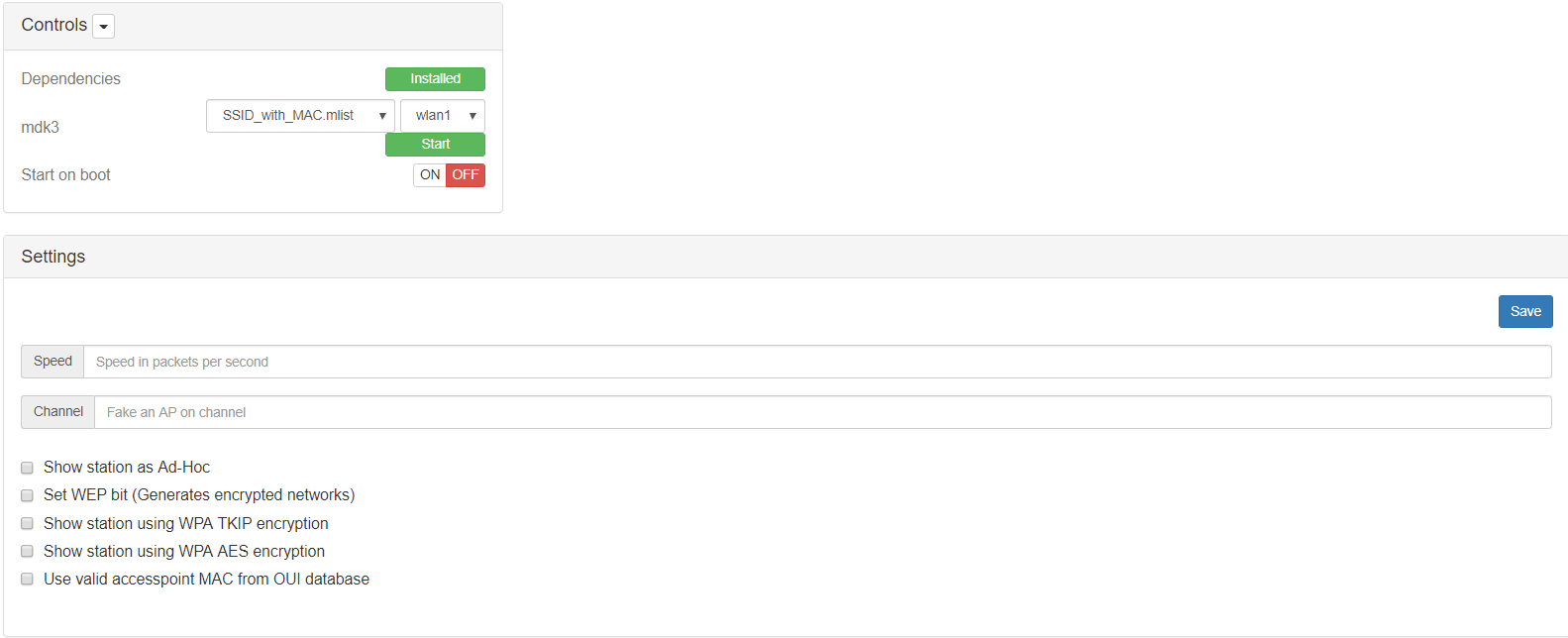
The first field to use is the mdk3, in which you will choose a list filled with SSID and like in the image above BSSID. The other ones, I think are self explanatory. For this demo, I’m going to use the default values (no one) ;)
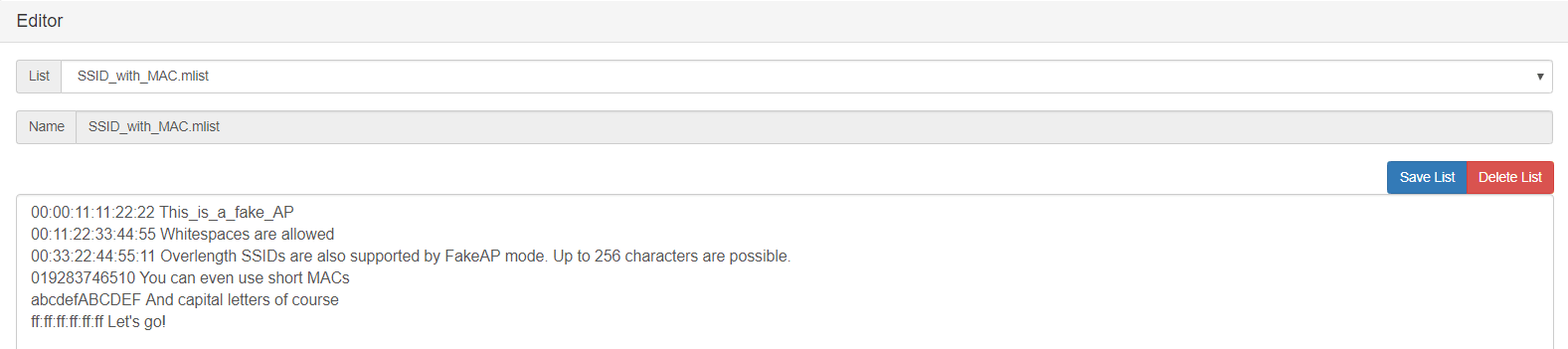
Furthermore, this module provides you a list editor for editing or adding new list to jam the network media.
As the previous module, you have to click on start several times. In order to use the card interface in monitor mode.
DWALL
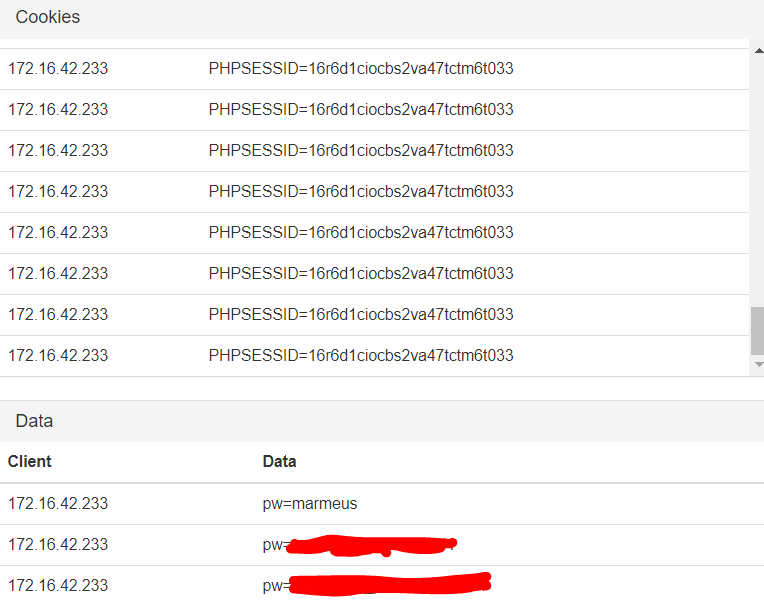
DWALL module is a mitm module which will provide you URLS, IMAGES, COOKIES and even PASSWORDS!!! of the clients connected to the pineapple.
In order to make this module work, you only have to click on “Enable” and then “Start Listening”
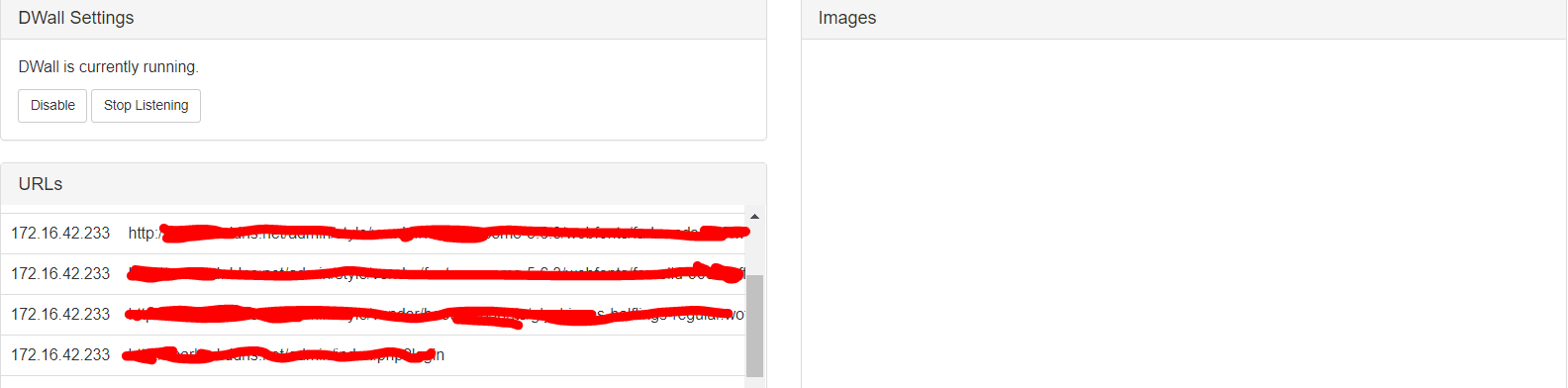
I was connected with my smartphone client (172.16.42.233) and even though, I was surfing the Internet I couldn't find a web page in which I couldn’t get any image. However, I got some cookies and for some http webpages I could get the password of that site as I show you below.
SignalStrength
This module as can can image, shows you the strength of networks nearby you.
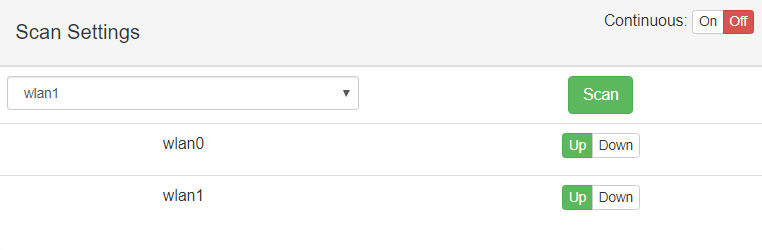
In order to start you only have to select a wireless interface and press Scan. However, if you only press scan, in my case, it will just detect the pineapple AP (Access Point). So, I encourage you to to turn on the “Continuous” mode. Once, Clicked scan the Scan results table will be start to filling in.
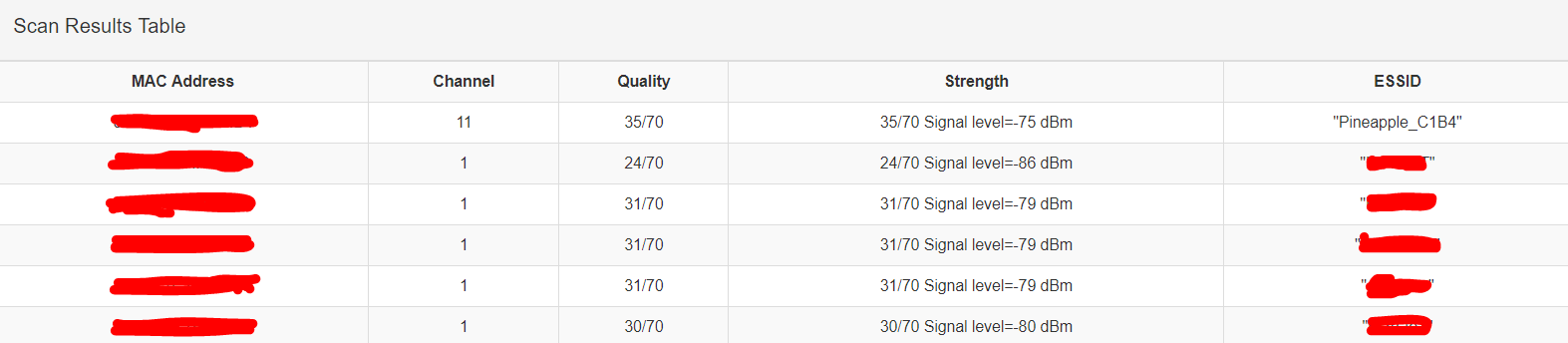
For the ones who aren’t familiar with dBm, the ideal strength would be 0. Hence, SignalStrength provides you with a column ranking the quality of the signal.
Finally, it shows you a pie chart all the networks aforementioned.
The numbers in the graph are therefore based on the signal strength dBm plus 100 to produce a positive number.
ConnectedClients
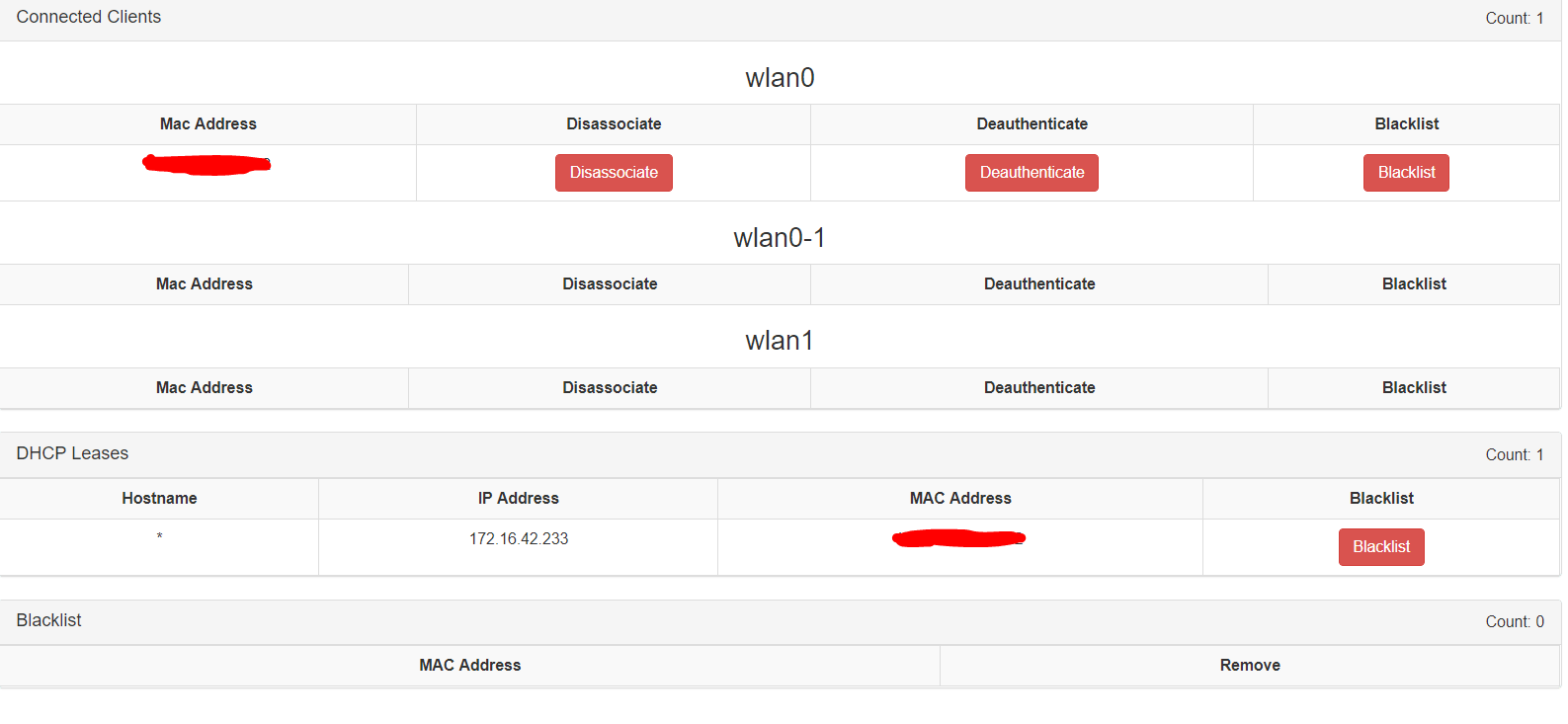
This module is a better option instead of the pre-installed clients module. Due to it provides, actions for each client such as: Disassociate, Deauthenticate or even blacklist a client. Moreover, you can see the IPs assigned by the DHCP server for a MAC address and a table which will show you black listed clients.
URLSNARF
urlsnarf is a simple module which allow you to sniff http url request.
I tried with my mobile phone and using chrome I couldn't get any one, just junk petitions that my mobile phone was doing through other apps. However, when I connected my laptop I could get the http urls (The last 3 lines in the log field below)
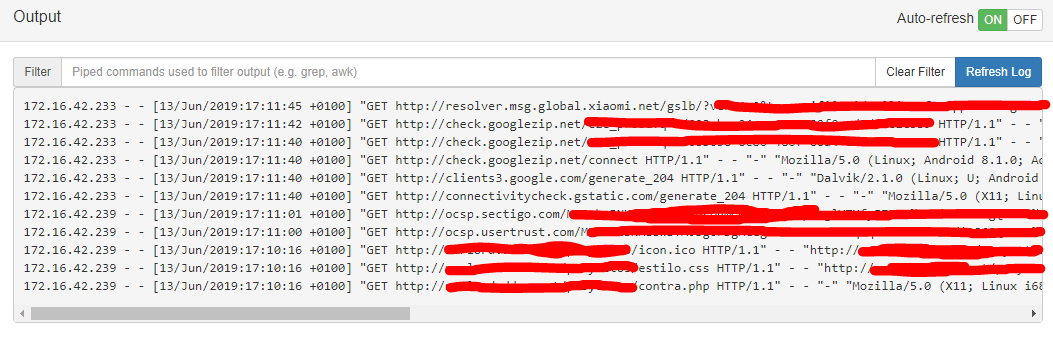
CABINET
Cabinet is a file manager module, which allows you to browse through folders search files and create, edit and delete files and folders. Because, I’m accessing as root to the pineapple, I can create any file wherever I want.
Create a file:
Create a folder:
GET
https://forums.hak5.org/topic/37397-official-get/
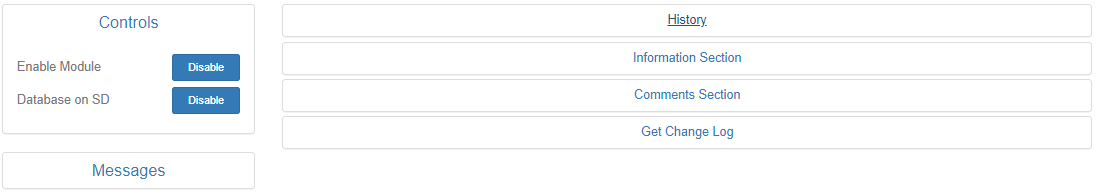
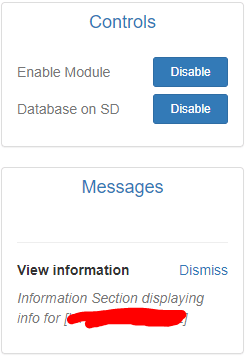
Get is a module which provides to the attacker information about victim’s web browser. However, it is a little bit tricky to get that information. First of all, enable the module and if you are running out of internal memory, enable “Database on SD”.
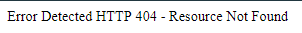
Once done this, you must use your imagination, through dnspoffing, to redirect to the victim at the webpage http://172.16.42.1/ or http://172.16.42.1/redirect.php. If it worked properly you will see in the victim’s browser something like this.
Now, its time to go back to the pineapple’s module and have a look to the history field.
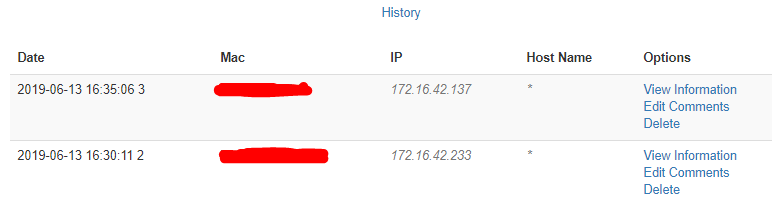
I used my laptop and mobile phone for doing some tests. (PCs provides more information than obile phones due to some browser don’t allow you to install plugins)
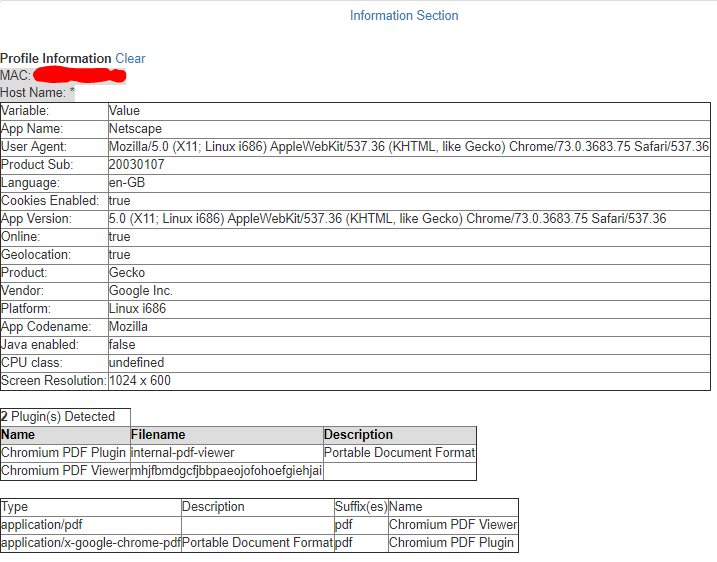
As you can see in the screenshot below, it shows you some of the Plugins that I have installed on my web browser. Furthermore, you can see the type of browser, language, cookies enabled, SO, Screen Resolution….
SITE SURVEY
https://forums.hak5.org/topic/38284-official-site-survey-module/
Site survey is a module which allows yo to:
- View APs around with information such as SSID, MAC, Encryption, Cipher, Auth, Channel, Frequency, Signal Quality.
- View connected Clients
- Vendor information on AP's MAC
- Start capture on AP
- Start deauth on AP
- Capture history with information such as number of IVS or 4-Way Handshake
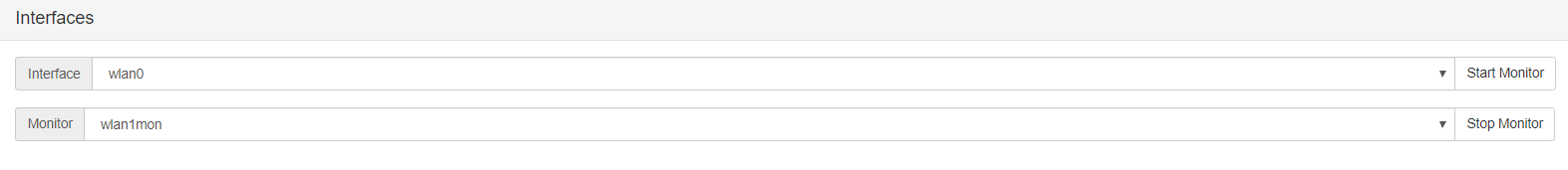
In order to start playing with this module you must choose an interface to put it on monitor mode.
Once, you have one interface in monitor mode, you can choose if detect just APs only or APs & their clients (My advice is to select a time higher than a minute). I’m going to use the second option, but if you want to choose the first one, active the Auto-refresh mode in order to take detect more APs, because sometimes with just a scan the pineapple doesn’t detect everything.
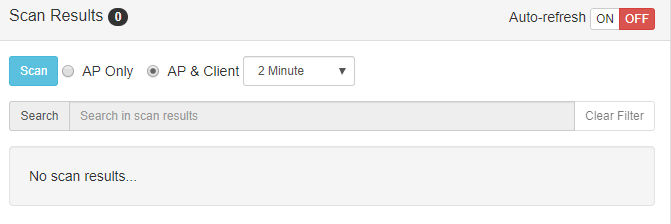
Once, clicked “Scan” button, wait until it ends.

Finally, you will see all the APs and their clients. Select one and press capture.
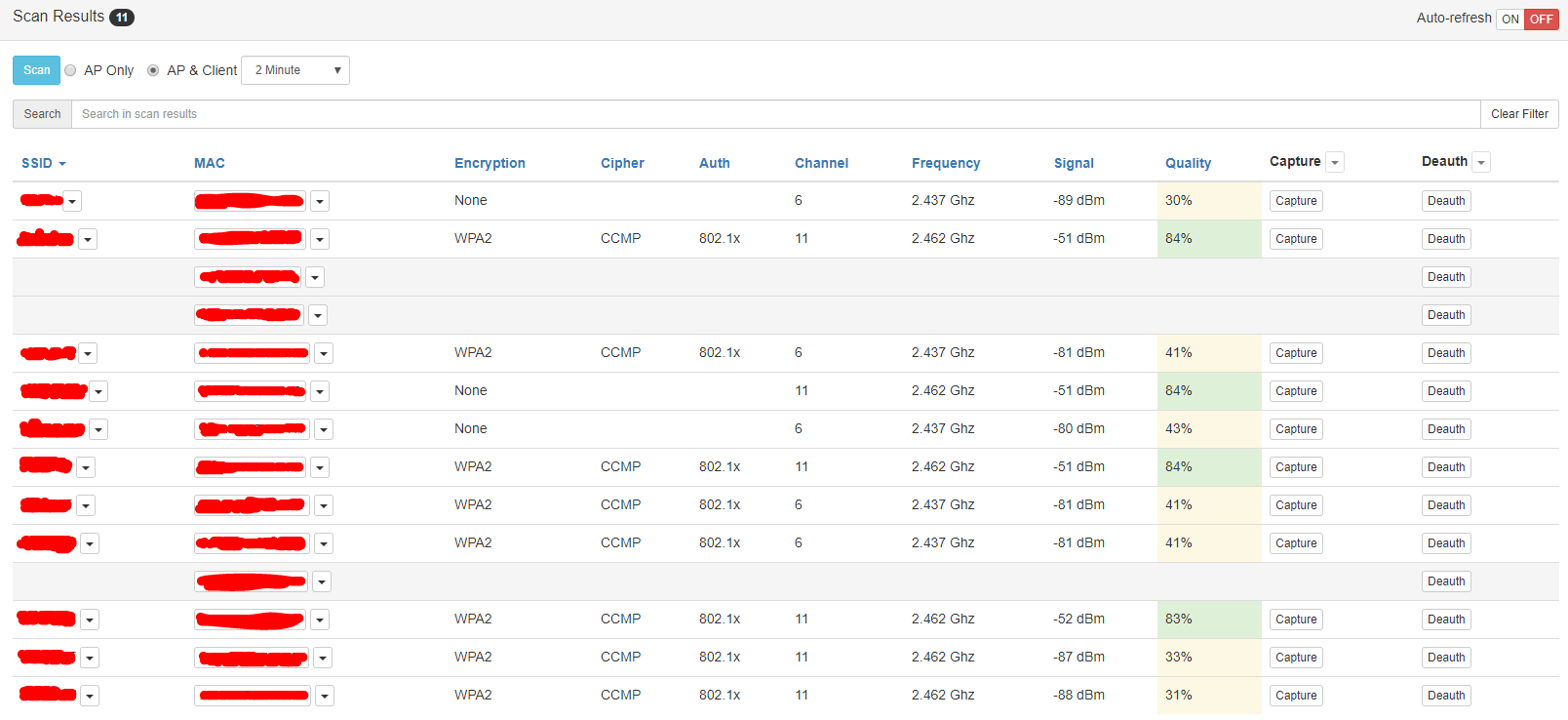
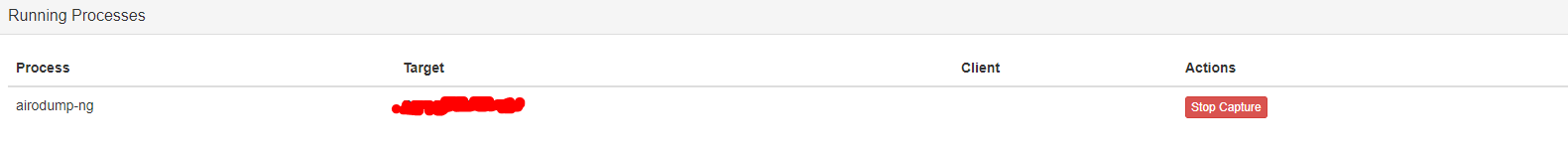
Whenever you want, press stop or if you want to get the handshake realize a deauth attack.
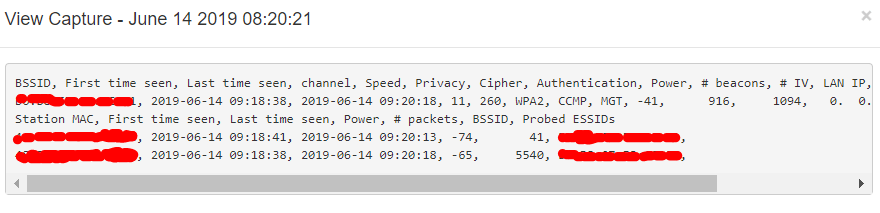
THEMES
I think the default theme is perfect if you are in a light room you aren’t going to be watching pineapple screen for a long period of time. However, that isn’t my case, so I decided to take a look at this module and It gave just want I need it.
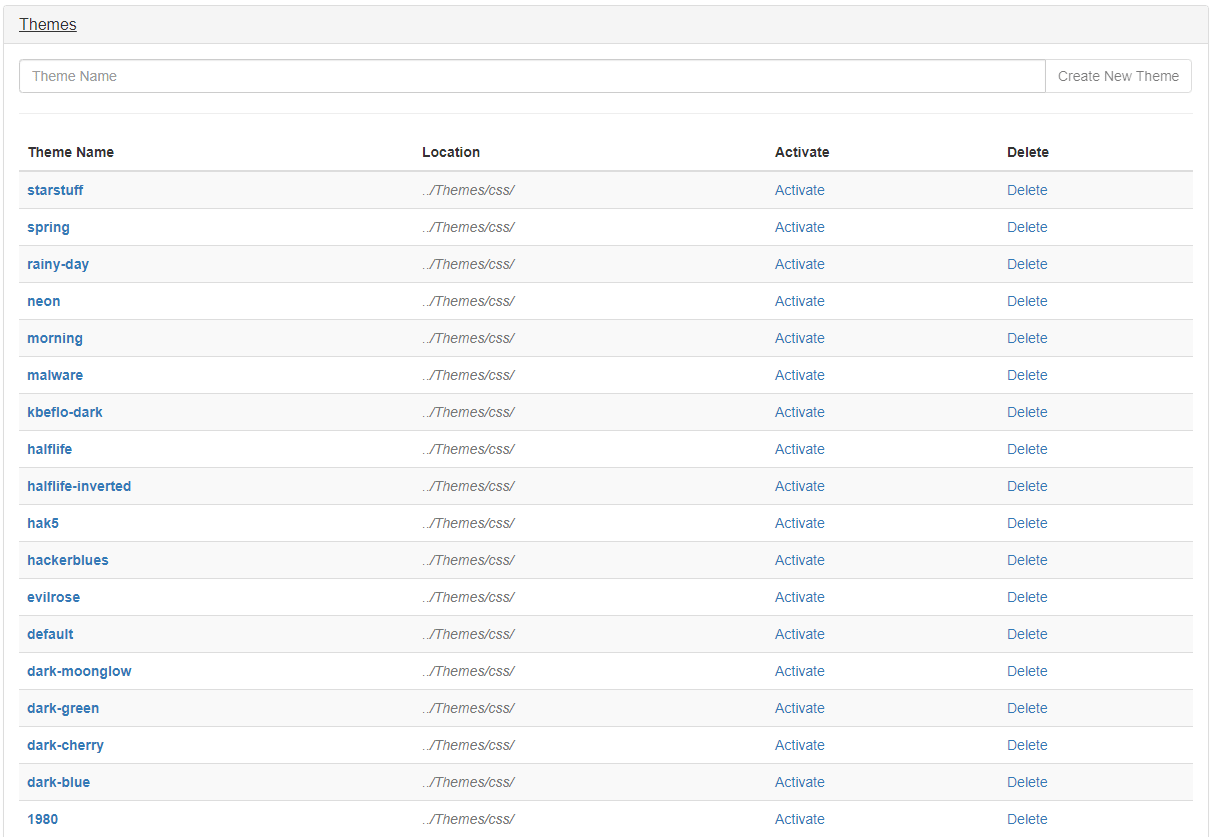
As you can see there a plenty of theme, but my favourite is “dark-blue” (Image below)
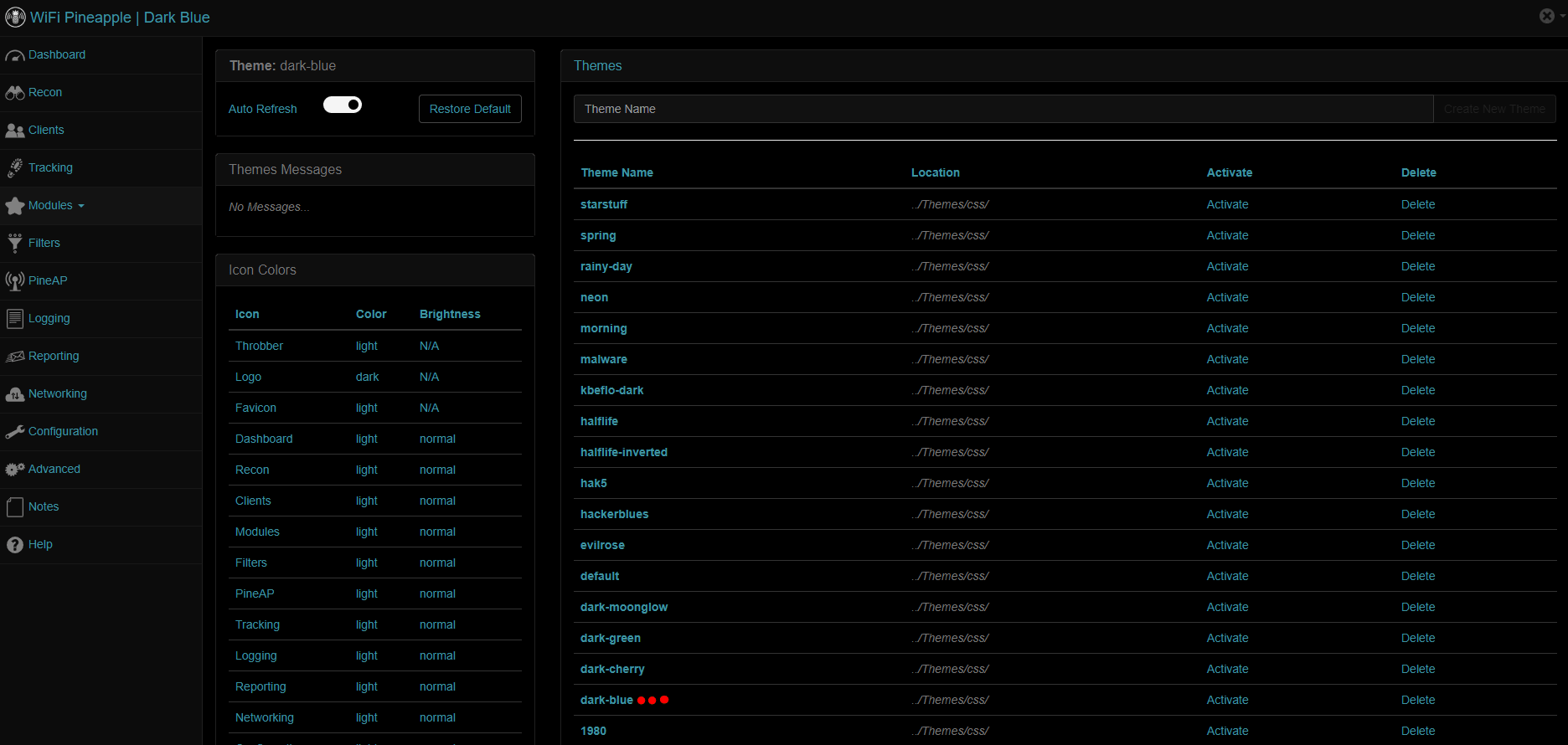
Furthermore, it allows you to change the default pineapple icons.
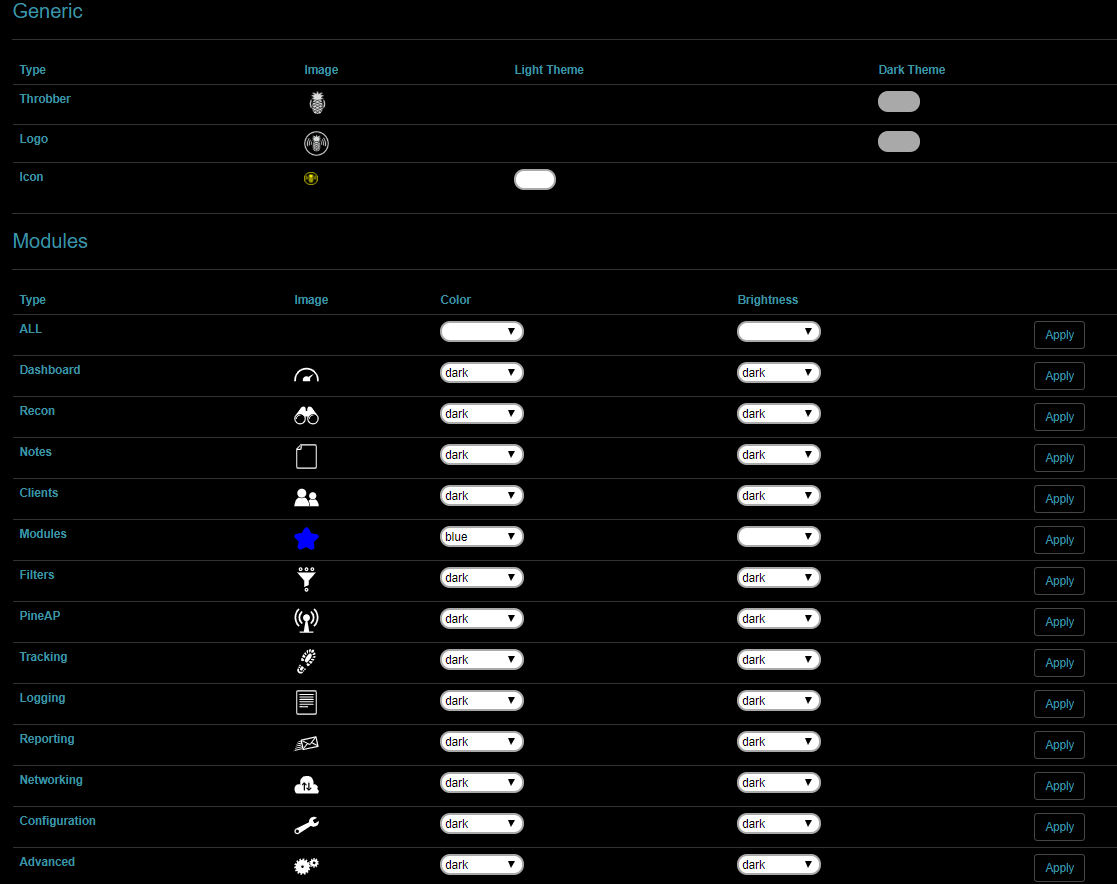
Those aren’t the default settings, I just customized it to get everything as I like.
MODULE MAKER
https://forums.hak5.org/topic/37313-official-module-maker/
Module Maker isn’t a module to make new modules, it just creates the template for you.

Once, you just have to fill the gaps and it will create the template module.
More
https://forums.hak5.org/topic/37448-official-portal-auth
https://forums.hak5.org/topic/37759-official-cursedscreech/
I’m not going to make a tutorial about these modules because I think these youtube videos, shows it better that I could ever explain it better than me.
- Portal Auth: https://www.youtube.com/watch?v=Bvo43JvmeW0
- Cursed Screech: https://www.youtube.com/watch?v=PIrHQz9o4cQ