OSEP Review - 2024


Table of Contents
Introduction
On the 23rd of January 2024, I successfully became an OffSec Experienced Penetration Tester (OSEP). Hence, as I did with the OSCP, in today's post, I will give my opinions on what you are going to encounter and what you need to do before purchasing the course and provide you with some tips for the exam.
What you should expect from the course
The PEN-300 course covers topics like Active Directory, PowerShell Constrained Language and antivirus evasion, phishing and some Linux Lateral Movement techniques as main topics.
However, these topics are covered just a bit, giving you enough knowledge to start doing your own malware programs or bypasses but not enough information about how to evade an EDR. Furthermore, Active Directory vulnerabilities are not as well covered as they are in the CRTO; which I recommend obtaining before facing the OSEP so you can tackle the course's Active Directory part without much of a hassle.
Before purchasing the course
The central aspect of the course to highlight is the 700 pages of information you must learn in less than 3 months, so you can have time to practice the knowledge on the challenge labs. Maybe it was just me, but I couldn't handle working, living independently, and spending time with my life partner, with reading the documentation, doing the exercise and completing the lab challenges in less than three months.
Nonetheless, there are two alternatives if you are in the same situation. The easiest one is to buy the Learn One Offsec Training on Black Friday, so you have a whole year to complete the course and sit the exam.
The other alternative is to get familiar with the sylabus. To do so, you can create your own lab and practice there the certification topics. Then, you can buy the three-month course, focusing only on practising what you have already learned in your lab and completing the challenge labs as many times as you think necessary.
Another aspect is the infrastructure you must have to store the notes, scripts and programs you will develop during the course. This is seen in the section "Introduction to Visual Studio".
Because your code and notes will be triggered by antivirus, you must have a Windows (with Windows Defender disabled) and a Kali virtual machine.
- The Windows machine develops and compiles your programs and PowerShell Scripts.
- The Kali machine stores everything that is developed on the Windows machine (create a SAMBA share), plus your notes and tools, and it will also be used to download your tools from your victim machines.
To mount the infrastructure, install Apache and Samba.
sudo apt install apache2 samba -yThen, modify the Samba configuration.
kali@kali:~$ sudo mv /etc/samba/smb.conf /etc/samba/smb.conf.bkp
kali@kali:~$ sudo cat /etc/samba/smb.conf
[global]
client min protocol = LANMAN1
workgroup = WORKGROUP
log file = /var/log/samba/log.%m
max log size = 1000
logging = file
map to guest = bad user
usershare allow guests = yes
[visualstudio]
path = /var/www/html
browseable = yes
read only = no
writeable = yes
guest ok = yes
public = yes
force user = auditorAfter that, create a Samba user that can access the share. To access the share
sudo smbpasswd -a auditor
sudo chmod -R 777 /var/www/html
sudo systemctl stop smbd
sudo systemctl start smbdFinally, you can access the share with the following command.
net use \\<KALI_IP>\visualstudio <PASSWORD> /USER:auditorIn this way, everything you develop can be easily downloaded into the victim's machine. Plus, I encourage you to create Git repository so you can keep track of your malware changes.
After purchasing the course
For your information, if you have bought the Learn One Annual Subscription, as the name says, it is a SUBSCRIPTION, so if you do not cancel it after a year, you will receive a new charge on your account :D

Moreover, the Offsec platform can be overwhelming with the number of courses that appear despite not being enrolled. To save you time browsing the web every time you are logged out, I suggest you add a link to the theory modules and another to the lab's dashboard to your browser's bookmarks bar.
Regarding the latter, when you are reading the theory, they expect you to use a certain machine to perform certain exercises, but sometimes you won't know which machine is which.
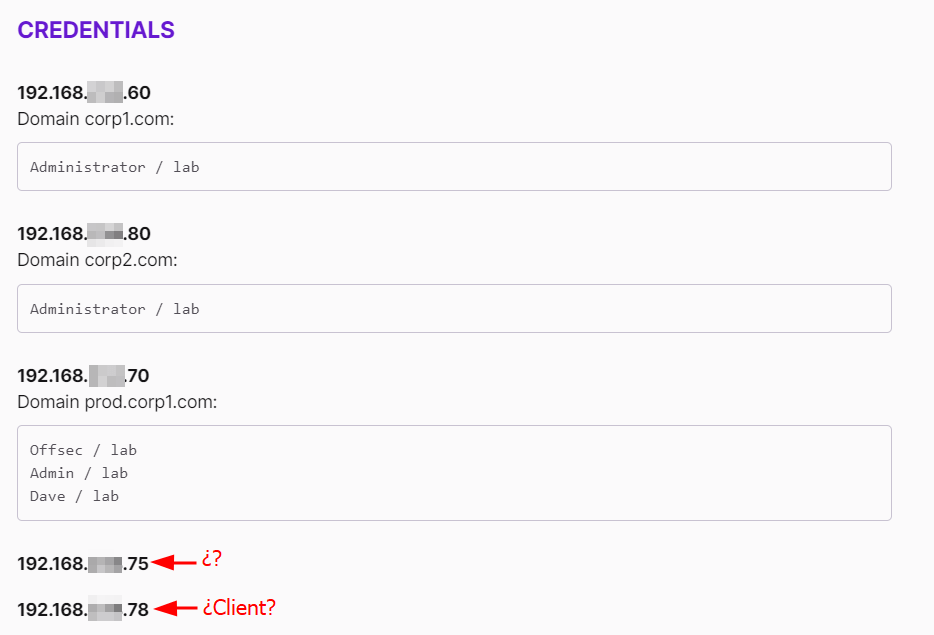
Also, once you have your Offsec account, you must create an account at the Offsec's forum, where you will find most of your doubts. However, you might need more exact details about solving specific exercises, or you are hardly stuck on a challenge. In those cases, Offsec's Discord comes in really handy; you must link your Offsec account to your Discord account to access the PEN-300 challenges. Then, before asking anything, look at those channels because it is quite probable that your doubt has already been solved.
in:#pen-300-general in:#pen-300-exercises in:#pen-300-labs <YOUR_DOUBT>The challenge labs
The challenge labs are an excellent opportunity to explore achieving the same goal in different ways, like using PsExec.exe or impacket-psexec or exploiting the same vulnerability with different tools, which means always having a plan B.
Furthermore, complete the labs several times, enumerating as much as possible because sometimes you will encounter two different attack vectors that will lead to the same result. Again, exploit both paths because you might face them in the future.
The exam
The exam is like an external pentest where you are given X amounts of external IPs, and your objective is to get inside the company's internal network to access the machine that contains secret.txt. If you do not find the secret.txt, another alternative, is to obtain 10 flags; it doesn't matter if they are local.txt or proof.txt; the sum of both must be 10.
The external machines are vulnerable, so you can get access to the internal network in one way or another. This is important to know because each of them consists of a different path to achieve the secret.txt. Thus, the second alternative to passing the exam is to access those paths and exploit as many machines as you can in order to obtain 10 flags.
Finally, the reason you came here; these are some tips to tackle the exam.
Organise your notes before the exam so everything is well located to avoid wasting time looking for commands or techniques.
Create your own
met.exethat isn't detected by the AVs on the challenge labs.Instead of starting with the most complicated technique, you know, start with the simplest.
Prepare several alternatives to perform certain actions.
Ligolo-ng and Metasploit autoroute are your friends for accessing the internal network.
This is the continuation of the OSCP, so you might encounter vulnerabilities that aren't related to the OSEP but could have appeared on the OSCP.
Use DynWin32-ShellcodeProcessHollowing.ps1 to obtain a stable reverse shell.
In order to bypass CLM, you can use bypass-clm, but it requires you to remove the AV evasion to avoid being detected in the lab.
Metasploit is more than enough; do not waste your time learning how to use an Open Source C2.
Take breaks during the exam; it will help you clear your main so you can find your way when you are stuck.
The
secret.txtis achievable but requires a lot of enumeration of even the simplest things.If you get stuck you can have a look at my guide to help you.
Conclusion
To sum up, the OSEP is a little bit more advanced certification for students who want to learn the basics of AV bypasses, Active Directory and phishing techniques, and it is paid for by the company.
If you have passed the OSCP and the CRTO, you can definitively face the OSEP ;)